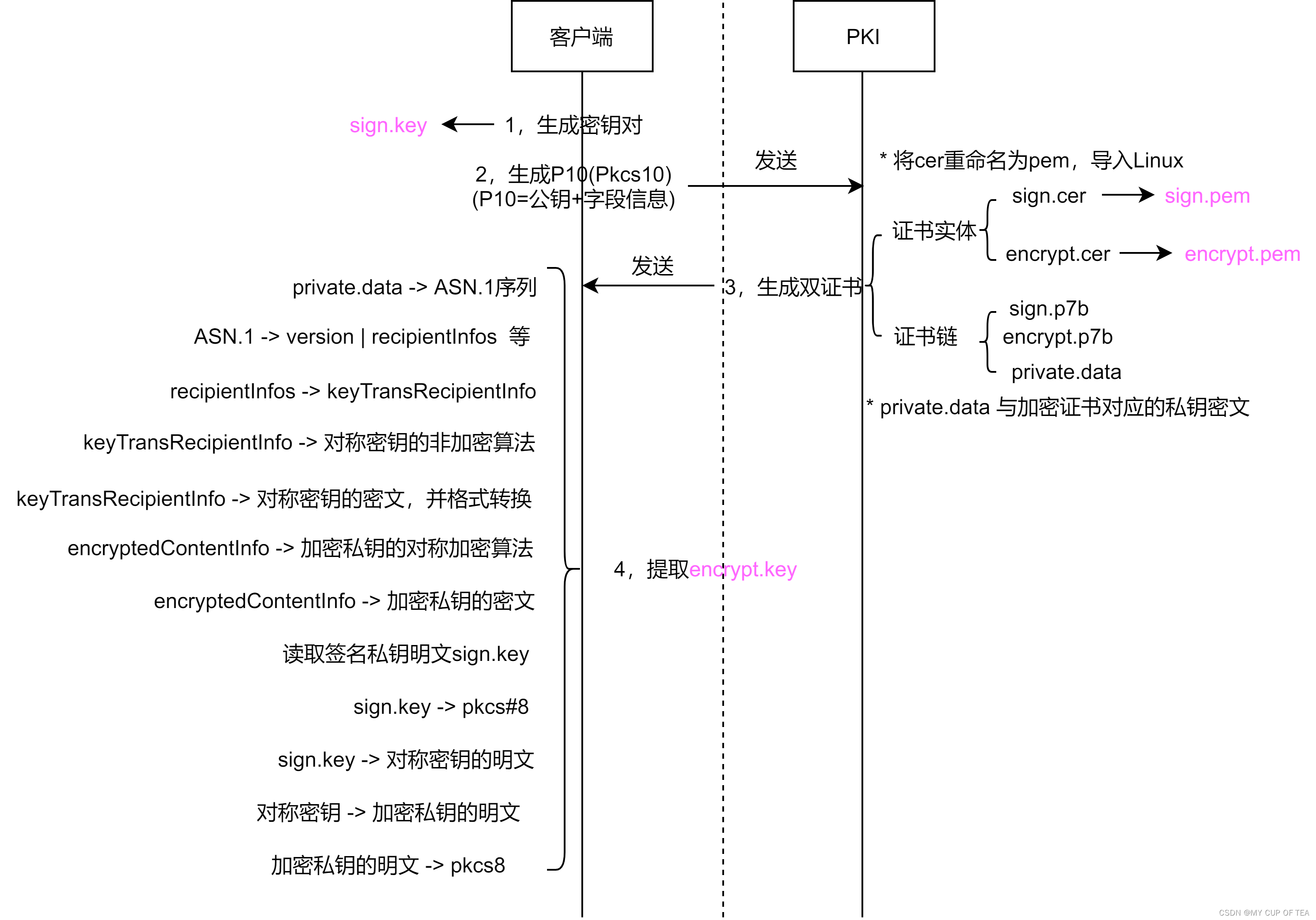
完整流程
生成密钥对
- 1,本地首先使用openssl生成一个256位的SM2私钥
- gmssl ecparam -genkey -name sm2p256v1 -text -out xxxx.key
- 查看私钥内容
- gmssl sm2 -noout -text -in xxxx.key
- 或者
- gmssl pkey -in xxxx.key -text
- gmssl ecparam -genkey -name sm2p256v1 -text -out xxxx.key
gmssl sm2 -noout -text -in xxxx.key
Using configuration from /usr/local/gmssl/openssl.cnf
read SM2 key
Private-Key: (256 bit)
priv:
ae:81:28:c6:00:ba:0f:bc:b8:2d:59:48:0f:a6:b8:
a5:a1:39:b0:b4:09:87:13:04:1f:5c:6d:99:f3:6a:
53:14
pub:
04:e5:e3:11:2f:77:c4:ab:8b:98:e8:4c:ae:c3:0a:
f8:c3:b3:6e:90:b2:59:62:79:af:2e:17:ed:46:e8:
af:6a:70:17:d1:9a:b4:b8:c0:19:07:a9:ef:bc:a2:
ea:c0:38:d2:e7:17:d1:25:1f:28:e0:f0:d9:8b:0c:
bb:d3:60:bd:3a
ASN1 OID: sm2p256v1
NIST CURVE: SM2
生成P10
- 2,基于密钥产生证书申请(P10 = 公钥 + 字段)
- gmssl req -new -sm3 -key xxxx.key -out xxxx.req -subj "/C=Cn/ST=Hubei/L=Wuhan/O=kk/OU=kkk/CN=client/[email protected]"
- 查看申请内容
- gmssl req -nout -in xxxx.req -text
Certificate Request:
Data:
Version: 1 (0x0)
Subject: C = Cn, O = SDT, CN = test
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:e5:e3:11:2f:77:c4:ab:8b:98:e8:4c:ae:c3:0a:
f8:c3:b3:6e:90:b2:59:62:79:af:2e:17:ed:46:e8:
af:6a:70:17:d1:9a:b4:b8:c0:19:07:a9:ef:bc:a2:
ea:c0:38:d2:e7:17:d1:25:1f:28:e0:f0:d9:8b:0c:
bb:d3:60:bd:3a
ASN1 OID: sm2p256v1
NIST CURVE: SM2
Attributes:
a0:00
Signature Algorithm: sm2sign-with-sm3
30:46:02:21:00:ef:aa:5f:08:bb:16:1c:18:7e:c9:dd:44:df:
61:c7:5b:b0:b7:f2:e2:c7:9a:57:e0:c2:67:b9:d7:1e:39:98:
04:02:21:00:8d:9d:d5:45:33:0e:0d:ff:39:b2:f1:d5:93:f9:
3b:5b:17:bd:2a:b6:e1:2d:83:2c:67:56:87:83:60:b4:71:51
-----BEGIN CERTIFICATE REQUEST-----
MIHmMIGMAgEAMCoxCzAJBgNVBAYTAkNuMQwwCgYDVQQKDANTRFQxDTALBgNVBAMM
BHRlc3QwWTATBgcqhkjOPQIBBggqgRzPVQGCLQNCAATl4xEvd8Sri5joTK7DCvjD
s26Qslliea8uF+1G6K9qcBfRmrS4wBkHqe+8ourAONLnF9ElHyjg8NmLDLvTYL06
oAAwCgYIKoEcz1UBg3UDSQAwRgIhAO+qXwi7FhwYfsndRN9hx1uwt/Lix5pX4MJn
udceOZgEAiEAjZ3VRTMODf85svHVk/k7Wxe9KrbhLYMsZ1aHg2C0cVE=
-----END CERTIFICATE REQUEST-----
生成双证书
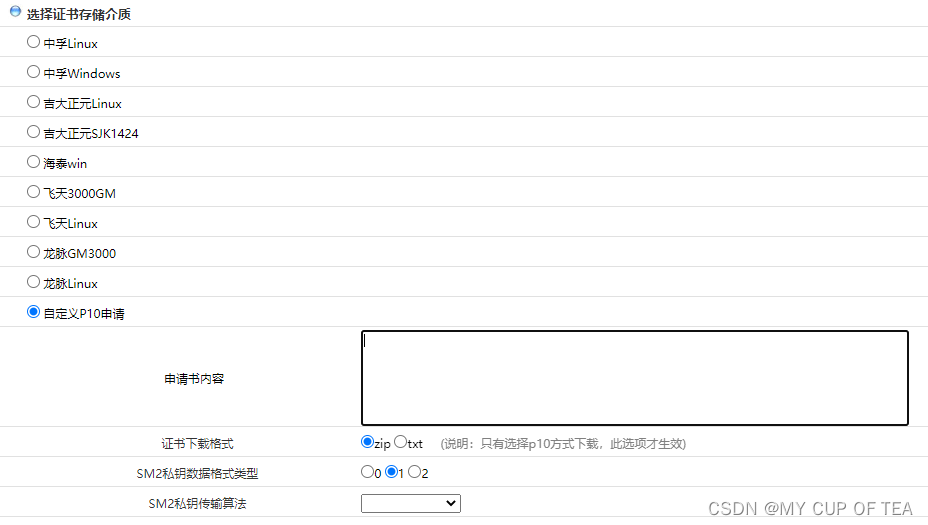
- 3 从吉大正元的PKI进行证书下载,证书的相关字段和请求保持一致,进行证书下载阶段时,上传先前产生的P10数据
- 选择 自定义P10申请
- 申请书内容 填写 xxxx.req,但是需要去掉 -----BEGIN CERTIFICATE REQUEST----- 和 -----END CERTIFICATE REQUEST-----
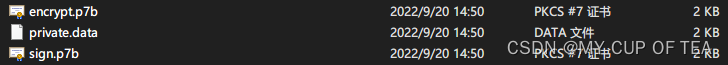
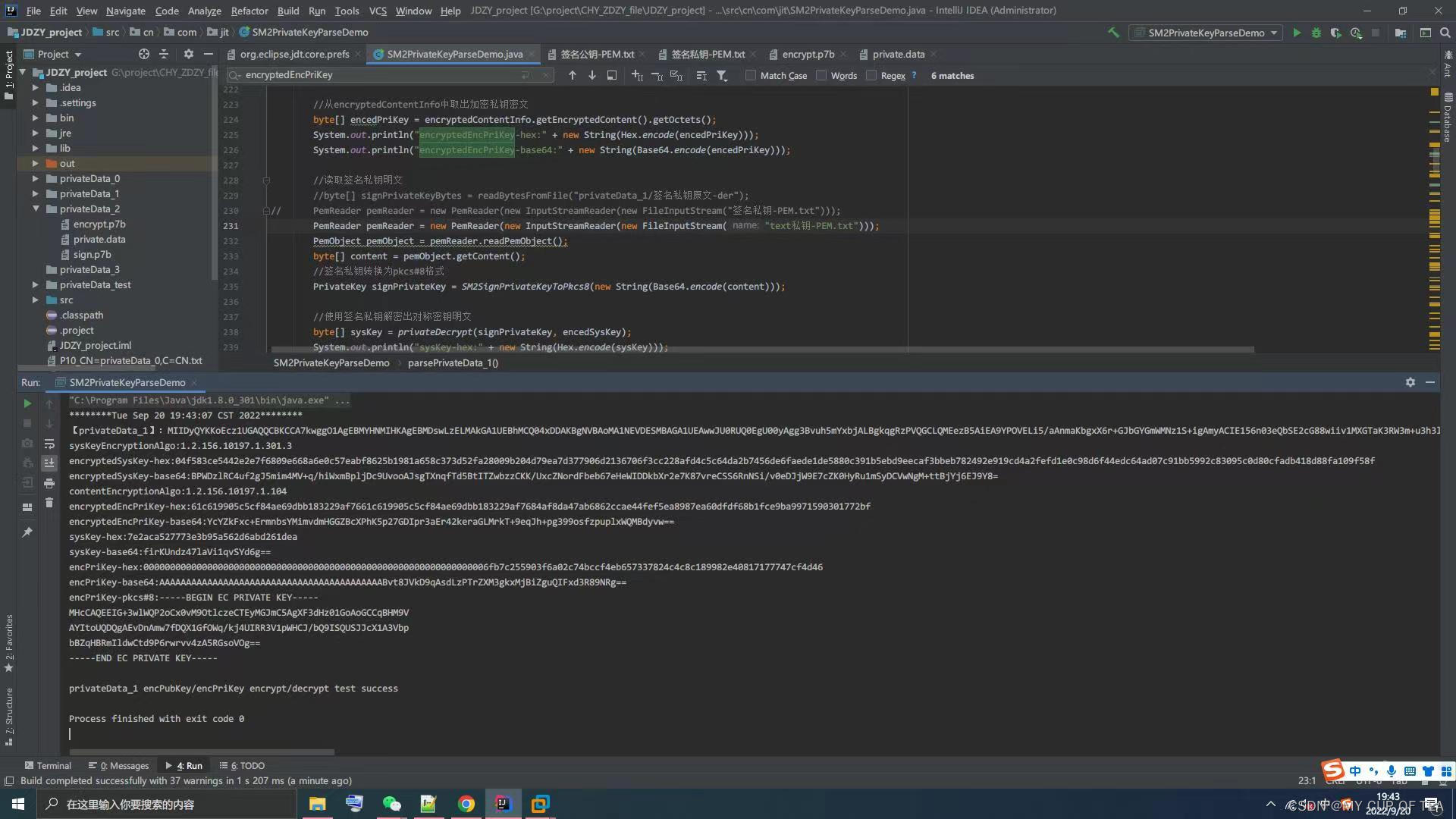
- 证书类型,这里选择zip,但是zip解压得到的以下三个文件,分别是P7b格式的签名和加密证书,private.data 是 加密之后的与加密证书相对应的私钥
- 注意事项:
- 本地产生私钥的时候,同时产生与之对应的公钥
- 公钥+数据字段 --> 获取申请请求
- 私钥和签名证书相对应
- 加密证书是包含公钥的,其对应的私钥被加密保护,也就是private.data
- 注意事项:
- 将cer格式的证书修改后缀名为pem,将其导入到Ubuntu,使用openssl进行读取
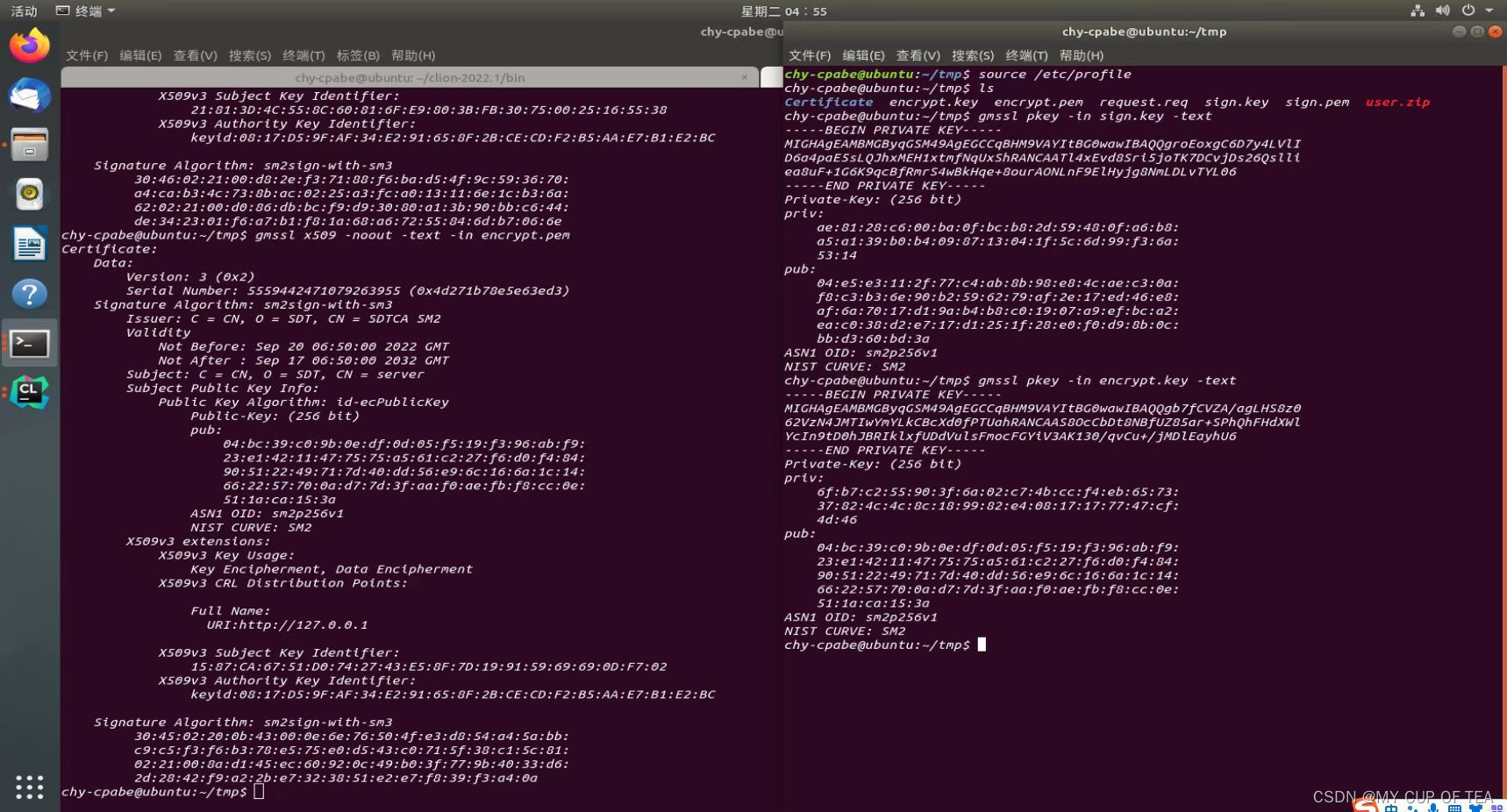
- gmssl x509 -noout -text -in sign.pem
gmssl x509 -noout -text -in sign.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 3965133194720063854 (0x3706fba1e666316e)
Signature Algorithm: sm2sign-with-sm3
Issuer: C = CN, O = SDT, CN = SDTCA SM2
Validity
Not Before: Sep 20 06:50:00 2022 GMT
Not After : Sep 17 06:50:00 2032 GMT
Subject: C = CN, O = SDT, CN = server
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:e5:e3:11:2f:77:c4:ab:8b:98:e8:4c:ae:c3:0a:
f8:c3:b3:6e:90:b2:59:62:79:af:2e:17:ed:46:e8:
af:6a:70:17:d1:9a:b4:b8:c0:19:07:a9:ef:bc:a2:
ea:c0:38:d2:e7:17:d1:25:1f:28:e0:f0:d9:8b:0c:
bb:d3:60:bd:3a
ASN1 OID: sm2p256v1
NIST CURVE: SM2
X509v3 extensions:
X509v3 Key Usage:
Digital Signature, Non Repudiation
X509v3 CRL Distribution Points:
Full Name:
URI:http://127.0.0.1
X509v3 Subject Key Identifier:
21:81:3D:4C:55:8C:60:81:6F:E9:80:3B:FB:30:75:00:25:16:55:38
X509v3 Authority Key Identifier:
keyid:08:17:D5:9F:AF:34:E2:91:65:8F:2B:CE:CD:F2:B5:AA:E7:B1:E2:BC
Signature Algorithm: sm2sign-with-sm3
30:46:02:21:00:d8:2e:f3:71:88:f6:ba:d5:4f:9c:59:36:70:
a4:ca:b3:4c:73:8b:ac:02:25:a3:fc:a0:13:11:6e:1c:b3:6a:
62:02:21:00:d0:86:db:bc:f9:d9:30:80:a1:3b:90:bb:c6:44:
de:34:23:01:f6:a7:b1:f8:1a:68:a6:72:55:84:6d:b7:06:6e
提取crypt.key
- 4 提取与加密证书相对应的key,即encrypt.key