文章目录
secret1
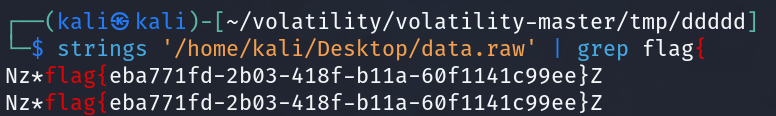
下载附件后直接使用 strings命令搜索flag{
关键字
flag{eba771fd-2b03-418f-b11a-60f1141c99ee}
secret2
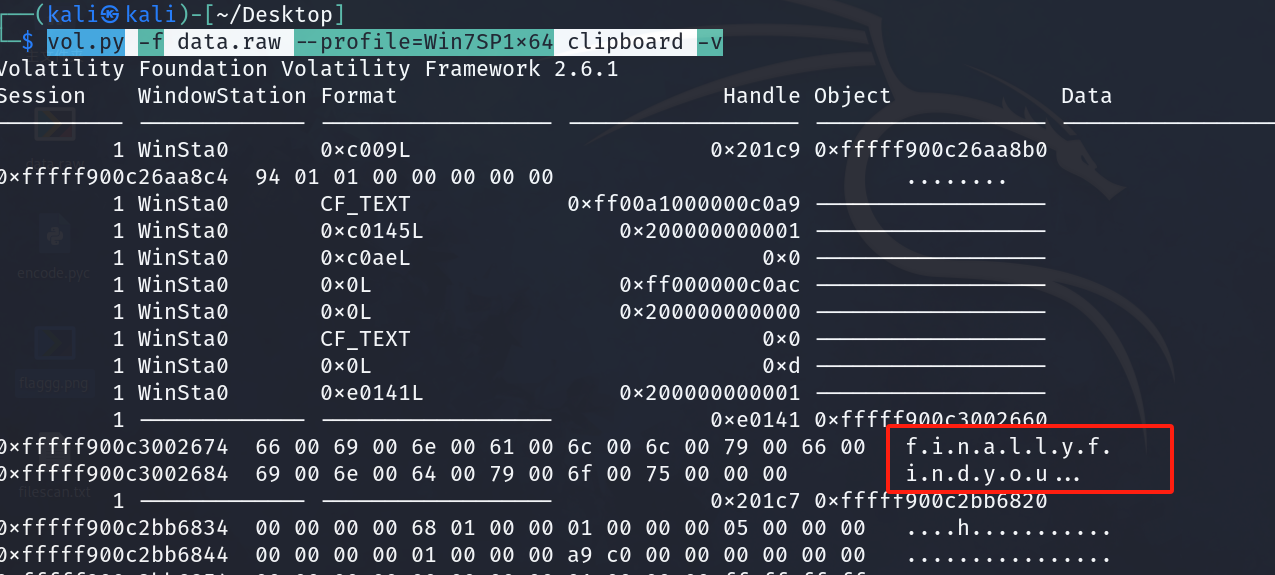
内存查看图片发现可以目标,下载下来
又发现内存文件pyc,
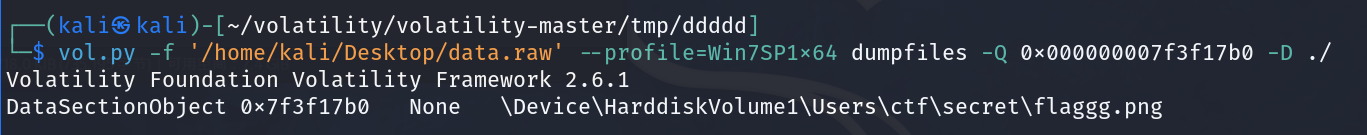
vol.py -f '/home/kali/Desktop/data.raw' --profile=Win7SP1x64 filescan | grep pyc
vol.py -f '/home/kali/Desktop/data.raw' --profile=Win7SP1x64 dumpfiles -Q 0x000000007f3f17b0 -D ./
然后网站恢复pyc文件
本地脚本改写
def decode(png):
flag = "flag{eba771fd-2b03-418f-b11a-60f1141c99ee}"
lens = len(flag)
with open(png, "rb") as f:
pic_bytes = f.read()
output_bytes = bytearray()
for i in range(0, len(pic_bytes)):
output_bytes.append(pic_bytes[i] ^ ord(flag[i * 2 % lens]))
with open("decoded_" + png, "wb") as f:
f.write(output_bytes)
# 使用文件名调用解密函数
decode("flaggg.png")
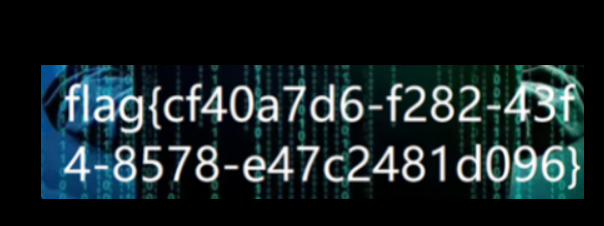
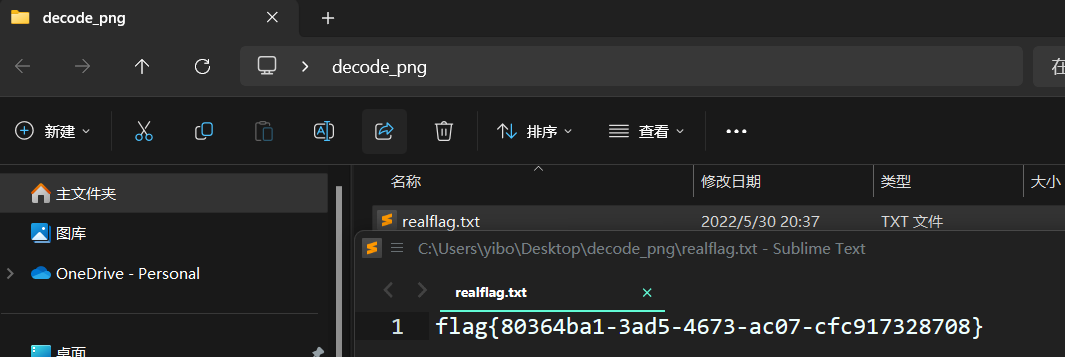
得到新的图片
secret3
题目让找到压缩包获取里面的flag 原始镜像中没有任何压缩包,使用工具010查看上一关解密出来的png图片发现末尾隐藏一个zip压缩包
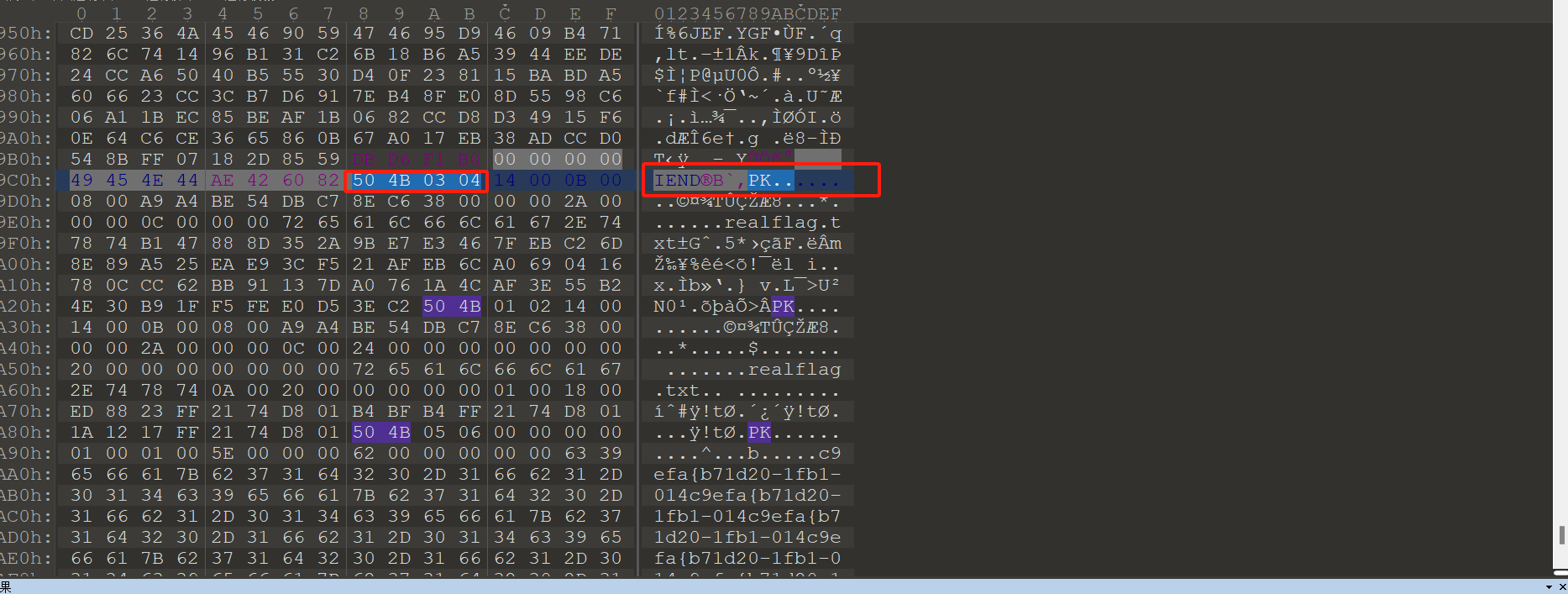
-v
vol.py -f data.raw --profile=Win7SP1x64 clipboard -v
得到解压密码为finallyfindyou解压后得到密码。
flag{80364ba1-3ad5-4673-ac07-cfc917328708}
2024
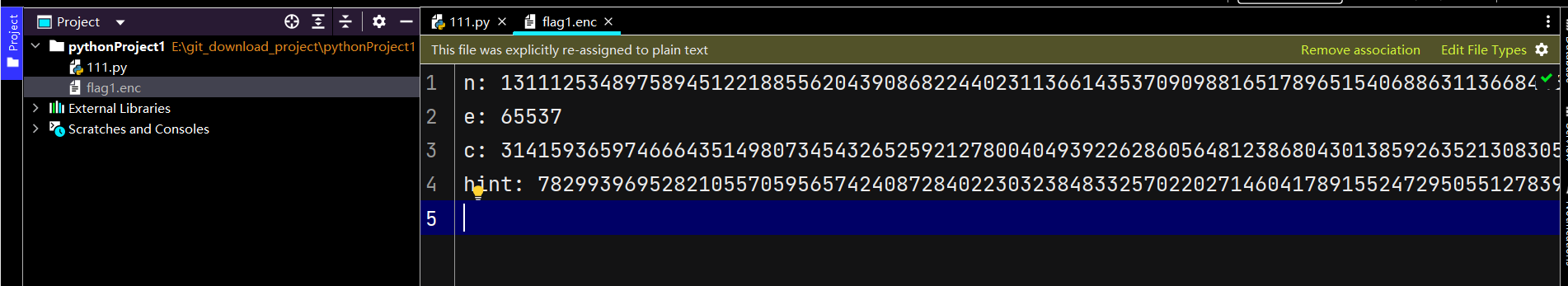
n=13111253489758945122188556204390868224402311366143537090988165178965154068863113668446449296161794818953904845201813996968339175738080442391942643611047671328902660055336047685713304129172682406229372976535096463219284722397386622225405198953493021223679602593847091241061873677679220911618002298935622233065778867002182025189925827061716645121096144074791457524062807482711962935614075745533387992708507241041977555043122850321627021193880102281432259303601748832191559700505221501964668864114901027968209331940369201883937024497451608116803469734003989442454337530585803565044371000913648068275830986927382800781681
e= 65537
c=3141593659746664351498073454326525921278004049392262860564812386804301385926352130830533412578874279777640307188723459000463428867163614026289296879770488846381739604850222680140990612960870712767337498300491425339595560063413241351308224105572360319196544100393979267058845081698258960852205426031225313109530203279690862845089207809897122319874567095069304622924480675948095945621254263622260935871100325009810290118800765403881701575348143626360445449744566574435383154061556825346058028982396103440611104578717448812402689794592513919949144741640447134546309350853929866403202944053915102252929311750864951026513
hint=782993969528210557059565742408728402230323848332570220271460417891552472950551278394818109223963432351812998468748813440403357929589500208607237429933882666987268547344569219725506578724635426286158583723948311951028435419747266085620508643289259244020884007774614053960633170911201106122613673596744042970439226
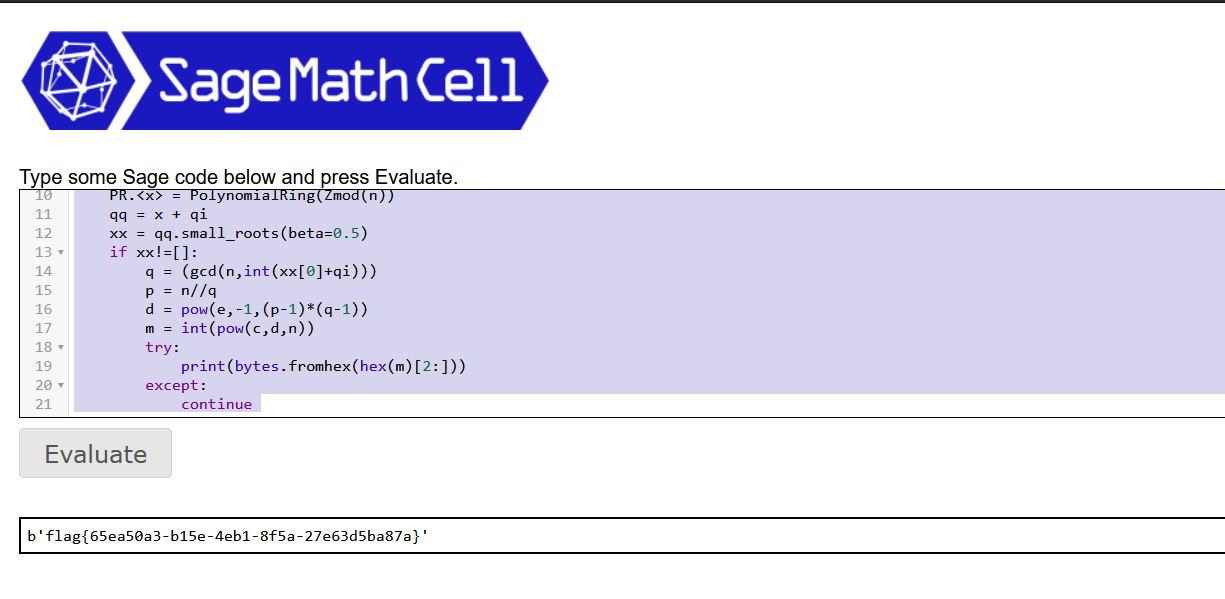
PR.<qq> = PolynomialRing(RealField(1024))
f = 4202*qq**2 - hint*qq + 2024*n
for qi in f.roots():
qi = int(qi[0])
PR.<x> = PolynomialRing(Zmod(n))
qq = x + qi
xx = qq.small_roots(beta=0.5)
if xx!=[]:
q = (gcd(n,int(xx[0]+qi)))
p = n//q
d = pow(e,-1,(p-1)*(q-1))
m = int(pow(c,d,n))
try:
print(bytes.fromhex(hex(m)[2:]))
except:
continue
flag{65ea50a3-b15e-4eb1-8f5a-27e63d5ba87a}
easy-decode
import hashlib
def md5_encrypt(input_string):
# 创建 MD5 哈希对象
md5_hash = hashlib.md5()
# 更新哈希对象
md5_hash.update(input_string)
# 获取 32 字节的⼗六进制表示
full_md5_hex = md5_hash.hexdigest()
# 取前 16 字节(即 16 个⼗六进制字符)
short_md5_hex = full_md5_hex[:32]
return short_md5_hex
if __name__ == "__main__":
input_string =bytes([ 0x40, 0x53, 0x48, 0x83, 0xEC, 0x70, 0x48, 0x8B,
0x05, 0xFB, 0xDF, 0x01, 0x00, 0x48, 0x33, 0xC4,
0x48, 0x89, 0x44, 0x24, 0x68, 0x48, 0x8D, 0x15, 0x74, 0xB2, 0x01, 0x00,
0x48, 0x8D, 0x0D, 0x75,
0xB2, 0x01, 0x00, 0xE8, 0x04, 0x48, 0x00, 0x00, 0x48, 0x8B, 0xD8, 0x48,
0x85, 0xC0, 0x75, 0x22,
0x48, 0x8D, 0x0D, 0x71, 0xB2, 0x01, 0x00, 0xE8, 0xF4, 0x4A, 0x00, 0x00,
0x8D, 0x43, 0x01, 0x48,
0x8B, 0x4C, 0x24, 0x68, 0x48, 0x33, 0xCC, 0xE8, 0x34, 0x02, 0x00, 0x00,
0x48, 0x83, 0xC4, 0x70,
0x5B, 0xC3, 0x33, 0xD2, 0x48, 0x89, 0xAC, 0x24, 0x80, 0x00, 0x00, 0x00,
0x48, 0x89, 0xB4, 0x24,
0x88, 0x00, 0x00, 0x00, 0x48, 0x8B, 0xCB, 0x48, 0x89, 0xBC, 0x24, 0x90,
0x00, 0x00, 0x00, 0x44,
0x8D, 0x42, 0x02, 0xE8, 0xB4, 0x4D, 0x00, 0x00, 0x48, 0x8B, 0xCB, 0xE8,
0x58, 0x46, 0x00, 0x00,
0x45, 0x33, 0xC0, 0x48, 0x63, 0xE8, 0x33, 0xD2, 0x48, 0x8B, 0xCB, 0xE8,
0x9C, 0x4D, 0x00, 0x00,
0x48, 0x8B, 0xCD, 0xE8, 0x80, 0x55, 0x00, 0x00, 0x48, 0x8B, 0xF0, 0x48,
0x85, 0xC0, 0x75, 0x10,
0x48, 0x8B, 0xCB, 0xE8, 0xB4, 0x48, 0x00, 0x00, 0x8D, 0x46, 0x01, 0xE9,
0x86, 0x01, 0x00, 0x00,
0x4C, 0x8B, 0xCB, 0x4C, 0x8B, 0xC5, 0xBA, 0x01, 0x00, 0x00, 0x00, 0x48,
0x8B, 0xCE, 0xE8, 0x8D,
0x54, 0x00, 0x00, 0x48, 0x8B, 0xCB, 0xE8, 0x91, 0x48, 0x00, 0x00, 0xB9,
0xD0, 0x07, 0x00, 0x00,
0xE8, 0x43, 0x55, 0x00, 0x00, 0x48, 0x8D, 0x15, 0x24, 0xFF, 0xFF, 0xFF,
0x48, 0x8B, 0xC8, 0x41,
0xB8, 0xD0, 0x07, 0x00, 0x00, 0x48, 0x8B, 0xD8, 0xE8, 0x53, 0x21, 0x00,
0x00, 0xFF, 0x15, 0x85,
0x31, 0x01, 0x00, 0x48, 0x8B, 0xF8, 0xFF, 0x15, 0x8C, 0x31, 0x01, 0x00,
0x45, 0x33, 0xC0, 0x48,
0x8B, 0xCF, 0x48, 0x8B, 0xD0, 0xFF, 0x15, 0x9D, 0x31, 0x01, 0x00, 0x41,
0xB8, 0xD0, 0x07, 0x00,
0x00, 0x48, 0x8B, 0xD3, 0x48, 0x8B, 0xCF, 0xFF, 0x15, 0x73, 0x31, 0x01,
0x00, 0x45, 0x33, 0xC0,
0x48, 0x8D, 0x54, 0x24, 0x38, 0x48, 0x8B, 0xCF, 0xFF, 0x15, 0x92, 0x31,
0x01, 0x00, 0x48, 0x8B,
0xCF, 0xFF, 0x15, 0x91, 0x31, 0x01, 0x00, 0x0F, 0x57, 0xC0, 0x8D, 0x45,
0x20, 0x99, 0x83, 0xE2,
0x1F, 0x03, 0xC2, 0x83, 0xE0, 0xE0, 0x48, 0x63, 0xC8, 0x0F, 0x11, 0x44,
0x24, 0x48, 0x0F, 0x11,
0x44, 0x24, 0x58, 0xE8, 0xC0, 0x54, 0x00, 0x00, 0x48, 0x8B, 0xF8, 0x48,
0x85, 0xC0, 0x75, 0x10,
0x48, 0x8B, 0xCE, 0xE8, 0x74, 0x51, 0x00, 0x00, 0x8D, 0x47, 0x01, 0xE9,
0xC6, 0x00, 0x00, 0x00,
0xFF, 0x15, 0xFA, 0x30, 0x01, 0x00, 0x48, 0x8B, 0xD8, 0xFF, 0x15, 0x19,
0x31, 0x01, 0x00, 0x4C,
0x8D, 0x4C, 0x24, 0x38, 0x45, 0x33, 0xC0, 0x48, 0x8B, 0xD0, 0x48, 0x8B,
0xCB, 0x48, 0x8D, 0x44,
0x24, 0x48, 0x48, 0x89, 0x44, 0x24, 0x20, 0xFF, 0x15, 0xE3, 0x30, 0x01,
0x00, 0x4C, 0x8B, 0xCE,
0x89, 0x6C, 0x24, 0x20, 0x4C, 0x8D, 0x44, 0x24, 0x30, 0x48, 0x8B, 0xD7,
0x48, 0x8B, 0xCB, 0xFF,
0x15, 0x03, 0x31, 0x01, 0x00, 0x48, 0x63, 0x6C, 0x24, 0x30