Docker
安装Docker
### 通过脚本安装
curl -sSL https://get.daocloud.io/docker | sh
# 或
curl -sSL http://acs-public-mirror.oss-cn-hangzhou.aliyuncs.com/docker-engine/internet | sh
# 查看版本
docker -v
# 启动服务
systemctl start docker
systemctl enable docker
# 验证docker安装成功
docker run hello-world
### 通过yum安装
## 新增源
# 添加Docker软件包源
yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo
# 阿里云国内镜像
yum-config-manager --add-repo https://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
#关闭测试版本list(只显示稳定版)
sudo yum-config-manager --enable docker-ce-edge
sudo yum-config-manager --enable docker-ce-test
# 更新yum包索引
yum makecache fast
# 查看版本
yum list docker-ce --showduplicates | sort -r
# 安装
yum install -y docker-ce-17.09.1.ce-1.el7.centos加速器
curl -sSL https://get.daocloud.io/daotools/set_mirror.sh | sh -s http://8431ce13.m.daocloud.io
# 或
tee /etc/docker/daemon.json <<-'EOF'
{"registry-mirrors": ["http://8431ce13.m.daocloud.io"],"insecure-registries":["118.31.43.252:8088","172.30.0.0/16"]}
EOF
systemctl daemon-reload
systemctl restart docker卸载Docker
# 查看安装的版本
yum list installed | grep docker
# 卸载软件
yum -y remove docker-ce.x86_64Docker命令
容器命令
- 查看命令
# 查看所有容器包括停止的
docker ps -a
# 查看运行容器状态
docker ps
# 查看最后一次运行容器信息
docker ps -l
# 查看容器日志
docker logs <ID|容器名称>
# 进入容器
docker exec -it <ID|容器名称> /bin/bash
# 查看容器详情
docker inspect- 操作命令
# 停止容器
docker stop <ID|容器名称>
# 启动之前已经停止的docker_run镜像
docker start <ID|容器名称>
# 删除容器(需停止容器后再删除)
docker rm -f <ID|容器名称>镜像命令
- 查看命令
# 查看本地所有镜像
docker images- 操作命令
# 运行镜像
# docker run --name yijitomcat --privileged -p 8080:8080 -v $PWD/tomcat/logs:/home/apache-tomcat-8.5.31/logs --mount type=volume,src=$PWD/tomcat/conf,dst=/home/apache-tomcat-8.5.31/conf -d mytomcat
docker run --name <容器名称> --privileged -p <宿主机映射端口>:<容器被映射端口> -v <宿主机映射目录>:<容器被映射目录> -d <镜像名称|镜像ID>
# 删除镜像
docker rmi <imageId>
# 拉取镜像
docker pull <镜像名称:版本>
# 查找镜像
docker search <镜像名称>Volume相关操作
# 新增卷
docker volume create --name volumeName
# 查看卷详情
docker volume inspect myVolume
# 查看卷列表
docker volume list
# 挂载到镜像
docker run -d --name yijitomcat -v volumeName:/home/tomcat mytomcat
# 删除镜像时删除挂载
docker rm -v -f yijitomcat
# 查看孤卷
docker volume ls -qf dangling=true
# 删除孤卷
docker volume rm $(docker volume ls -qf dangling=true)
# 授权一个容器访问另一个容器的Volume
docker run -d --volumes-from <另外一个容器> -t <tag> <镜像名称>Docker的持久化和还原
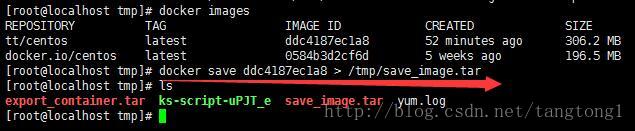
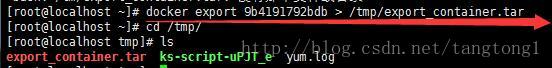
持久化镜像
docker save <imageId>> /tmp/save_image.tar 持久化容器
docker export <containerId> > /tmp/export_container.tar 导入持久化的镜像
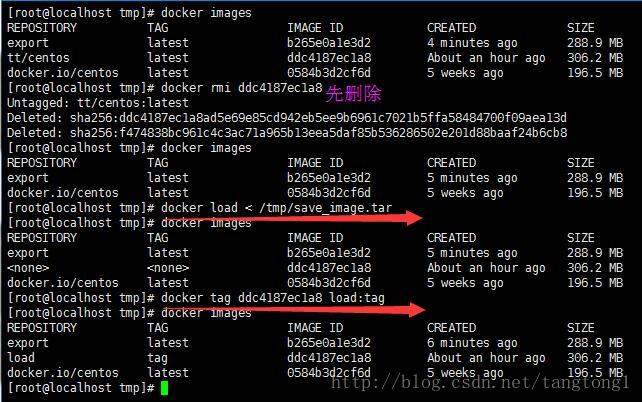
# 加载镜像
docker load < /tmp/save_image.tar
# 为镜像打TAG
docker tag <imageId> load:tag 导入持久化的容器
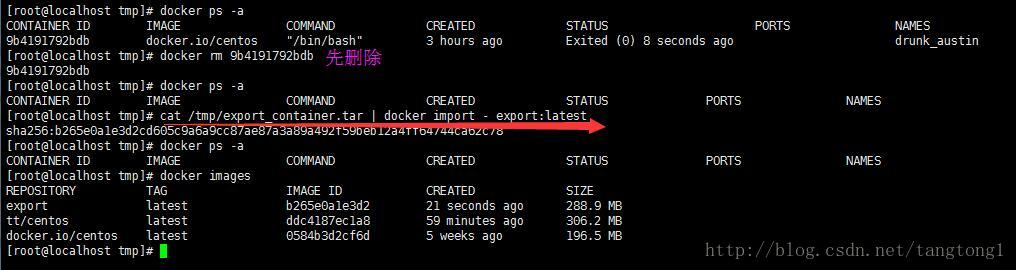
# 注意,导入之后是生成新的镜像而不是容器!
cat /tmp/export_container.tar | docker import - <imageName>:<imageTag> 两种方式的比较
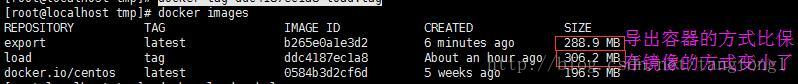
导出容器再导入为镜像的方式会丢失历史信息,而保存镜像再加载为镜像的方式不会丢失历史和层,可以做到层回滚,从下图两者的大小亦可看出些许端倪。
DockerFile
简单例子
docker build -t runoob/centos:6.7 .- -t :指定要创建的目标镜像名
- . :Dockerfile 文件所在目录,可以指定Dockerfile 的绝对路径
搭建Tomcat镜像例子
FROM centos
LABEL maintainer jlcon@qq.com
WORKDIR /home
ENV LANG C.UTF-8
RUN echo "zhun bei zi yuan..."
# ADD可自动解压文件
ADD apache-tomcat-8.5.31.tar.gz /home
ADD jdk-8u171-linux-x64.tar.gz /home
ADD which /usr/bin
ENV CATALINA_HOME /home/apache-tomcat-8.5.31
ENV JAVA_HOME /home/jdk1.8.0_171
ENV PATH $CATALINA_HOME/bin:$PATH
ENV PATH $JAVA_HOME/bin:$PATH
RUN chmod +x /home/apache-tomcat-8.5.31/bin/*.sh
CMD ["/home/apache-tomcat-8.5.31/bin/catalina.sh","run"]自定义镜像服务器
tee /etc/docker/daemon.json <<-'EOF'
{
"registry-mirrors": ["https://nwgq096a.mirror.aliyuncs.com"], #镜像加速地址
"insecure-registries":["192.168.116.148:5000"] # Docker如果需要从非SSL源管理镜像,这里加上。
"max-concurrent-downloads": 10,
"live-restore": true
}
EOF
systemctl daemon-reload
systemctl restart dockerDaemon.json 文件全览
{
"authorization-plugins": [],
"data-root": "",
"dns": [],
"dns-opts": [],
"dns-search": [],
"exec-opts": [],
"exec-root": "",
"experimental": false,
"storage-driver": "",
"storage-opts": [],
"labels": [],
"live-restore": true,
"log-driver": "",
"log-opts": {},
"mtu": 0,
"pidfile": "",
"cluster-store": "",
"cluster-store-opts": {},
"cluster-advertise": "",
"max-concurrent-downloads": 3,
"max-concurrent-uploads": 5,
"default-shm-size": "64M",
"shutdown-timeout": 15,
"debug": true,
"hosts": [],
"log-level": "",
"tls": true,
"tlsverify": true,
"tlscacert": "",
"tlscert": "",
"tlskey": "",
"swarm-default-advertise-addr": "",
"api-cors-header": "",
"selinux-enabled": false,
"userns-remap": "",
"group": "",
"cgroup-parent": "",
"default-ulimits": {},
"init": false,
"init-path": "/usr/libexec/docker-init",
"ipv6": false,
"iptables": false,
"ip-forward": false,
"ip-masq": false,
"userland-proxy": false,
"userland-proxy-path": "/usr/libexec/docker-proxy",
"ip": "0.0.0.0",
"bridge": "",
"bip": "",
"fixed-cidr": "",
"fixed-cidr-v6": "",
"default-gateway": "",
"default-gateway-v6": "",
"icc": false,
"raw-logs": false,
"allow-nondistributable-artifacts": [],
"registry-mirrors": [],
"seccomp-profile": "",
"insecure-registries": [],
"no-new-privileges": false,
"default-runtime": "runc",
"oom-score-adjust": -500,
"node-generic-resources": ["NVIDIA-GPU=UUID1", "NVIDIA-GPU=UUID2"],
"runtimes": {
"cc-runtime": {
"path": "/usr/bin/cc-runtime"
},
"custom": {
"path": "/usr/local/bin/my-runc-replacement",
"runtimeArgs": [
"--debug"
]
}
}
}- debug: it changes the daemon to debug mode when set to true.
- cluster-store: it reloads the discovery store with the new address.
- cluster-store-opts: it uses the new options to reload the discovery store.
- cluster-advertise: it modifies the address advertised after reloading.
- labels: it replaces the daemon labels with a new set of labels.
- live-restore: Enables keeping containers alive during daemon downtime.
- max-concurrent-downloads: it updates the max concurrent downloads for each pull.
- max-concurrent-uploads: it updates the max concurrent uploads for each push.
- default-runtime: it updates the runtime to be used if not is specified at container creation. It defaults to “default” which is the runtime - shipped with the official docker packages.
- runtimes: it updates the list of available OCI runtimes that can be used to run containers
- authorization-plugin: specifies the authorization plugins to use.
- allow-nondistributable-artifacts: Replaces the set of registries to which the daemon will push nondistributable artifacts with a new set of - registries.
- insecure-registries: it replaces the daemon insecure registries with a new set of insecure registries. If some existing insecure registries in - daemon’s configuration are not in newly reloaded insecure resgitries, these existing ones will be removed from daemon’s config.
- registry-mirrors: it replaces the daemon registry mirrors with a new set of registry mirrors. If some existing registry mirrors in daemon’s - configuration are not in newly reloaded registry mirrors, these existing ones will be removed from daemon’s config.
搭建私有仓库
使用REGISTRY创建仓库
拉取registry镜像
docker pull registry打开防火墙
firewall-cmd --zone=public --add-port=5000/tcp --permanent启动
docker run -d -p 5000:5000 --privileged=true -v /opt/registry:/tmp/registry registry - -d 是后台启动容器。
- -p 将容器的 5000 端口映射到 Host 的 5000 端口。5000 是 registry 服务端口。
- -v 将容器 /tmp/registry目录映射到宿主机的/opt/registry,用于存放镜像数据。
- –privileged=true :CentOS7中的安全模块selinux把权限禁掉了,参数给容器加特权,不加上传镜像会报权限错误(OSError: [Errno 13] Permission denied: ‘/tmp/registry/repositories/liibrary’)或者(Received unexpected HTTP status: 500 Internal Server Error)错误
使用NEXUS创建仓库
安装NEXUS
略
新建仓库
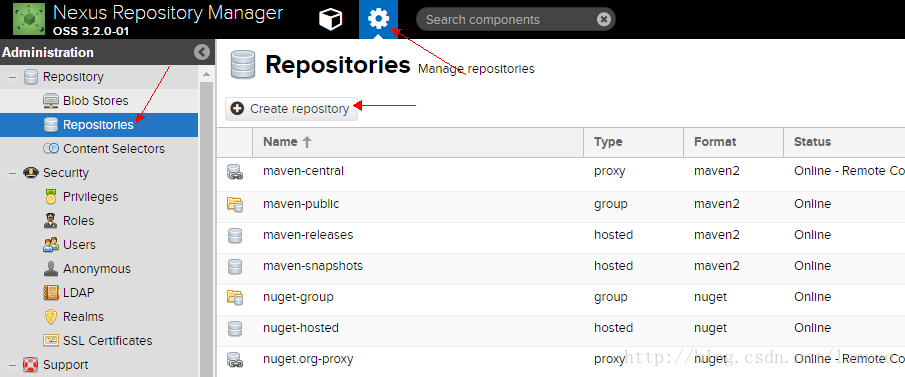
- 点击设置界面,选择Repositories,点击Create repository
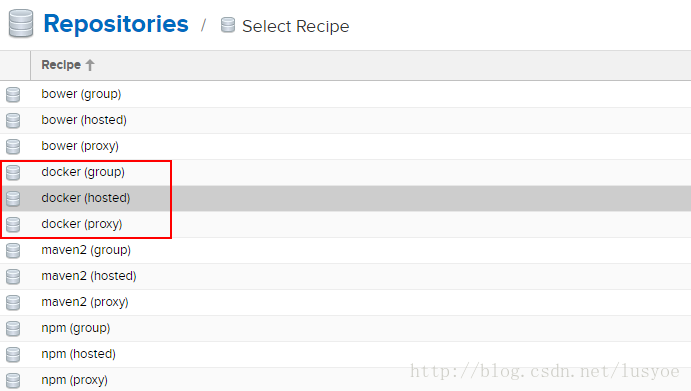
- 选择仓库类型,这里Docker有三种类型,分别是group、hosted、proxy。这里只演示hosted类型,所以选择docker(hosted)
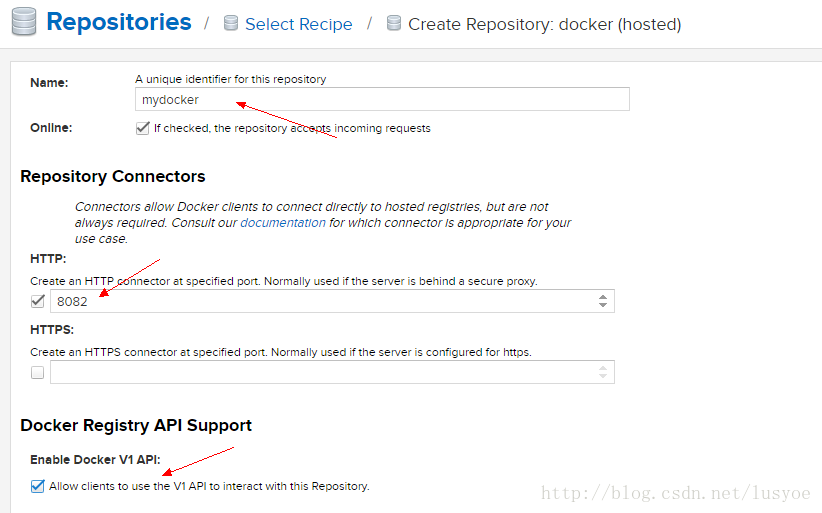
- 配置仓库
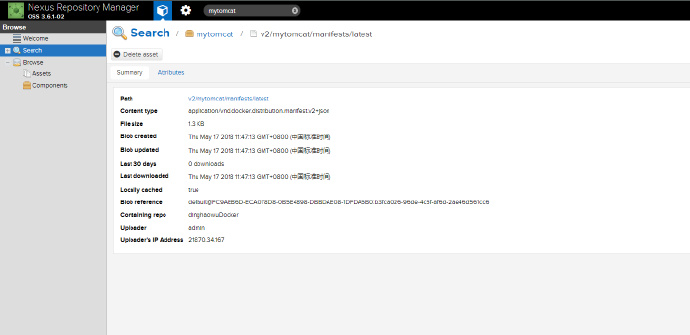
- 上传后查询结果
使用私有仓库
SETTING
# 编辑
vim /etc/docker/daemon.json
# 增加
"insecure-registries":["118.31.43.xxx:8088"]
# 保存重启
systemctl daemon-reload
systemctl restart dockerLOGIN
docker login 118.31.43.xxx:8088 --username admin --password admin123PUSH
# 推送前打个TAG
# docker tag <imageId or imageName> <nexus-hostname>:<repository-port>/<image>:<tag>
docker tag mytomcat 118.31.43.xxx:8088/mytomcat:latest
# 上传镜像
docker push 118.31.43.xxx:8088/mytomcat:latestPULL
docker pull 118.31.43.xxx:8088/mytomcatSEARCH
docker search 118.31.43.xxx:8088/mytomcat上传镜像到私服
# 通过 docker tag重命名镜像,使之与registry匹配。
docker tag <tagName> <ip>:<port:5000>/<name>:<版本号>
# 上传
docker push <ip>:5000/<name>:<版本号>
# 下载
docker pull <ip>:5000/wsf:v1
# 查看Registry中所有镜像信息
curl http://<ip>:5000/v2/_catalog参考资料
- Docker官方手册
- Docker 教程
- docker使用总结
- Dockerfile 官方文档
- Docker实践(二):容器的管理(创建、查看、启动、终止、删除)
- Docker之应用数据管理(volume/bind mount/tmpfs)
- 极简构建docker镜像并push到私有仓库
- sonatype nexus 3搭建Docker私有仓库
Kubernetes
安装Kubernetes
参考资料
- Kubernetes是什么
- Kubernetes(K8S)集群管理Docker容器(部署篇)
- kubernetes(k8s)以及涉及组件简单介绍
- kubernetes Github
- kubernetes reference
- kubernetes官网
OpenShift
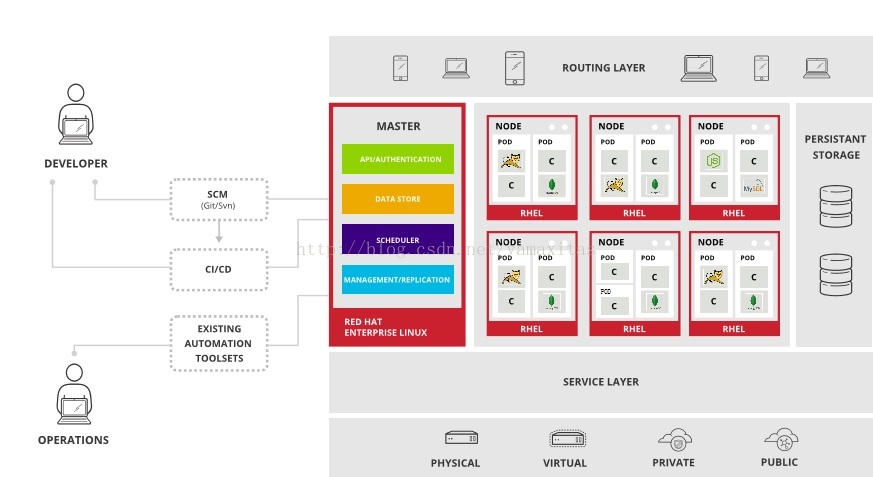
系统架构
- 一个“POD”是一个Docker容器的运行环境(如果需要共享本地的资源, 我们将在单独的POD中部署两种类别的容器)
- 一个“服务”是一个入口,抽象出一个均衡访问负载到一组相同的容器,理论上,最少是一个服务对应一个架构层。
- 一个“服务部署者”或“部署配置”是一个对象,用来描述基于触发器的容器的部署策略。(比如,当Docker注册表中有新版本的映象时,需重新部署)。
- 一个“复制控制器”是一个技术组件,主要负责POD的弹性。
- 一个“路由”是用来显露一个应用的入口(域名解析,主机名或VIP)
控制系统叫做master,运行系统叫做node。 node以pod为单位,以容器的形式运行客户应用。master提供openshift的人机接口,总体管控openshift nodes及pod分配,运行的调配等。
- master: Openshift的控制中心,提供人机接口,负责node的注册,管理,docker 镜像的创建,部署,pod的创建分配,pod集群的管理,openshift运行- 数据的存储。
- etcd: etcd是一个高可用的键值存储系统,主要用于共享配置和服务发现- 。Openshift使用etcd存储运行配置数据。
- pod: Openshift应用的最小单元,它由一个运行客户应用的docker容器和- 一个控制容器组成,通常情况下,一个pod等同于2个docker容器。
- container: 一种预先定义好的可以运行一个多个Linux兼容程序的环境。Containers 从images中启动,并且通称各个contianers之间是隔离的。
- images: 存储了linux文件系统,应用程序,应用程序依赖文件的静态镜像。镜像可以被执行,执行后,程序的内容不会被改变。
- service: Service提供一种对pod 访问模式,为pod提供固定的ip:port地址,使得访问更加的安全和稳定。
- router: Openshift可以对pod进行访问的网络地址。
- build: Openshit 部署客户应用的过程,包括,生成docker images,建立service,启动pod等过程。
- Replicas: Openshift 对应用的HA处理,可以增强可用性,提高并发及响应速度。
- node: 集成docker容器openshift客户应用的运行服务器。其作用等同于kubenate的minions
安装OpenShift
下载
配置
yum install etcd -y
## 新增地址insecure-registries
vim /etc/docker/daemon.json
ln -s /home/openshift/openshift-origin-server-v3.9.0-191fece-linux-64bit/oc /usr/bin
cd /var/lib/origin/openshift.local.config运行
## 创建默认配置文件并启动
## 配置文件位置/var/lib/origin/openshift.local.config/
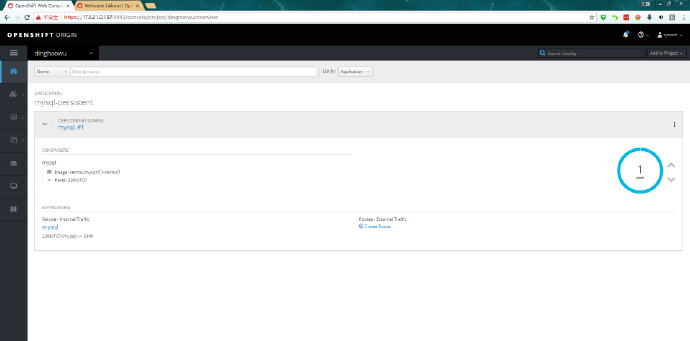
oc cluster up --host-data-dir=/home/openshift/data --use-existing-config --public-hostname=172.21.0.187
## oc启动说明
Starts an OpenShift cluster using Docker containers, provisioning a registry, router, initial
templates, and a default project.
This command will attempt to use an existing connection to a Docker daemon. Before running the
command, ensure that you can execute docker commands successfully (i.e. 'docker ps').
Optionally, the command can create a new Docker machine for OpenShift using the VirtualBox driver
when the --create-machine argument is specified. The machine will be named 'openshift' by default.
To name the machine differently, use the --docker-machine=NAME argument. If the
--docker-machine=NAME argument is specified, but --create-machine is not, the command will attempt
to find an existing docker machine with that name and start it if it's not running.
By default, the OpenShift cluster will be setup to use a routing suffix that ends in nip.io. This is
to allow dynamic host names to be created for routes. An alternate routing suffix can be specified
using the --routing-suffix flag.
A public hostname can also be specified for the server with the --public-hostname flag.
Usage:
oc cluster up [options]
Examples:
# Start OpenShift on a new docker machine named 'openshift'
oc cluster up --create-machine
# Start OpenShift using a specific public host name
oc cluster up --public-hostname=my.address.example.com
# Start OpenShift and preserve data and config between restarts
# 启动OpenShift。指定持久化数据目录,使用已存在配置
oc cluster up --host-data-dir=/mydata --use-existing-config
# Use a different set of images
oc cluster up --image="registry.example.com/origin" --version="v1.1"
# Specify which set of image streams to use
oc cluster up --image-streams=centos7
Options:
--create-machine=false: Create a Docker machine if one doesn't exist#创建一个docker
--docker-machine='': Specify the Docker machine to use#指定一个已存在的docker
-e, --env=[]: Specify a key-value pair for an environment variable to set on OpenShift container
--forward-ports=false: Use Docker port-forwarding to communicate with origin container.
Requires 'socat' locally.
--host-config-dir='/var/lib/origin/openshift.local.config': Directory on Docker host for
OpenShift configuration
--host-data-dir='': Directory on Docker host for OpenShift data. If not specified, etcd data
will not be persisted on the host.
--host-pv-dir='/var/lib/origin/openshift.local.pv': Directory on host for OpenShift persistent
volumes
--host-volumes-dir='/var/lib/origin/openshift.local.volumes': Directory on Docker host for
OpenShift volumes
--http-proxy='': HTTP proxy to use for master and builds
--https-proxy='': HTTPS proxy to use for master and builds
--image='openshift/origin': Specify the images to use for OpenShift
--image-streams='centos7': Specify which image streams to use, centos7|rhel7
--logging=false: Install logging (experimental)
--metrics=false: Install metrics (experimental)
--no-proxy=[]: List of hosts or subnets for which a proxy should not be used
--public-hostname='': Public hostname for OpenShift cluster
--routing-suffix='': Default suffix for server routes
--server-loglevel=0: Log level for OpenShift server
--service-catalog=false: Install service catalog (experimental).
--skip-registry-check=false: Skip Docker daemon registry check
--use-existing-config=false: Use existing configuration if present
--version='': Specify the tag for OpenShift images
Use "oc options" for a list of global command-line options (applies to all commands).创建注册中心secret
- 类型对象Secret旨在保存敏感信息,例如密码、OAuth令牌和ssh密钥。将这些信息放在Secret对象比放入Pod或Docker镜像中更安全和更灵活。
- Secret是一个包含少量敏感数据的对象,例如密码,令牌或密钥。否则,这些信息可能被放入Pod规格或Docker镜像中; 将其放置在Secret对象中可以更好地控制它的使用方式,并降低意外暴露的风险。
- 用户可以创建Secret对象,系统也会创建一些Secret对象。
- 要使用Secret对象,Pod需要引用Secret。Secret可以通过两种方式与Pod一起使用:作为安装在一个或多个容器上的卷中的文件,或者在为Pod拉动镜像时由kubelet使用。
kubectl create secret docker-registry <secret-name> --docker-server=<your-registry-server> --docker-username=<your-name> --docker-password=<your-pword> --docker-email=<your-email>
## 例子
kubectl create secret docker-registry registrykey-m2-1 --docker-server=118.31.43.252:8088 --docker-username=admin --docker-password=admin123 [email protected]
## 查看所有secret
kubectl get secret -a
## 查看指定secret
kubectl get secret <secret-name> --output=yaml
apiVersion: v1
data:
.dockerconfigjson: eyJhdXRocyI6eyIxMTguMzEuNDMuMjUyOjgwODgiOnsidXNlcm5hbWUiOiJhZG1pbiIsInBhc3N3b3JkIjoiYWRtaW4xMjMiLCJlbWFpbCI6ImpsY29uQHFxLmNvbSIsImF1dGgiOiJZV1J0YVc0NllXUnRhVzR4TWpNPSJ9fX0=
kind: Secret
metadata:
creationTimestamp: 2018-05-22T03:29:32Z
name: registrykey-m2-1
namespace: myproject
resourceVersion: "1578"
selfLink: /api/v1/namespaces/myproject/secrets/registrykey-m2-1
uid: 58096acd-5d70-11e8-9c00-08002742a4c7
type: kubernetes.io/dockerconfigjson
## 该.dockerconfigjson字段的值是Docker凭据的base64编码后的展现。
## 要了解.dockerconfigjson原文数据,请将base64编码转换为可读格式:
get secret registrykey-m2-1 --output="jsonpath={.data.\.dockerconfigjson}" | base64 -d
{"auths":{"118.31.43.252:8088":{"username":"admin","password":"admin123","email":"[email protected]","auth":"YWRtaW46YWRtaW4xMjM="}}}
## 将secret添加到openshift
oc secrets add serviceaccount/default secrets/registrykey-m2-1 --for=pull
## 要理解该auth领域的内容,请将base64编码的数据转换为可读格式:
echo "eyJhdXRocyI6eyIxMTguMzEuNDMuMjUyOjgwODgiOnsidXNlcm5hbWUiOiJhZG1pbiIsInBhc3N3b3JkIjoiYWRtaW4xMjMiLCJlbWFpbCI6ImpsY29uQHFxLmN" | base64 -d## 配置ConfigMap
kubectl create configmap my-config --from-file=path/to/bar
oc new-app 118.31.43.252:8088/mytomcat