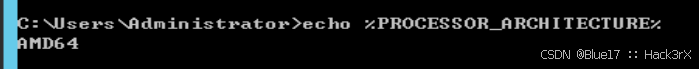关注这个专栏的其他相关笔记:[内网安全] 内网渗透 - 学习手册-CSDN博客
不管是在外网还是在内网中,信息收集都是重要的第一步。对于内网信息收集,我们需要了解到,我们当前控制的机器所处的内网结构是怎么样的,当前机器的角色是什么,使用这台机器的人的角色是什么,以及这台机器上安装了什么杀毒软件,这台机器能否上网,这台机器的型号是啥,使用的操作系统是啥,这些都是我们后面进行进一步攻击的依据,都需要我们通过信息收集来回答。
内网渗透的前提是你已经通过 CS 或者 MSF 拿到了内网一台机器的 Shell,大部分的收集都是通过命令行完成的,笔者这里就不浪费时间专门弄一个 CS 了,这里直接演示针对一台 Windows 电脑,我们应该使用什么样的命令完成信息收集。
0x01:判断当前 Shell 环境
通过下面的命令,我们可以判断我们当前拿到的 Shell 所处的环境,是域还是电脑本地:
whoami # 获取当前用户名称如上,结果为 hack3rx\administrator,这告诉我们,我们当前拥有管理员权限,但具体是域,还是本地管理员,还需要通过下面这个命令判断:
hostname # 获取主机名称如让,hostname 是 DC 不是 hack3rX,证明我们当前是域内管理员,而不是本地管理员。判断规则如下:
-
whoami 的结果:
主机名\用户名=> 本地用户,主机名可以通过hostname获取。 -
whoami 的结果:
域名\用户名=> 域内用户,只要hostname与前半段对不上,就可以判断处于域环境中。
0x02:判断当前 Shell 权限等级
通过下面这条命令,我们可以判断我们当前拿到的 Shell 的权限信息,是管理员还是普通用户:
whoami /groups # 查询当前用户所属组重点关注有没有啥 Administrators 的信息,比如上图中的 BUILTIN\Administrators 组,一旦有这种组,哪怕当前用户不叫 Administrators 那么它也有差不多的权限,你执行命令失败,显示权限不够,一般都是因为没有绕过 UA 验证(这个在前面提权部分讲解了,可以回去看看)。
注意一下 BUILTIN,我们之前在 AD 中分析过了,它里面基本都是本域的,这里又出现了。
0x03:收集当前机器网络配置信息
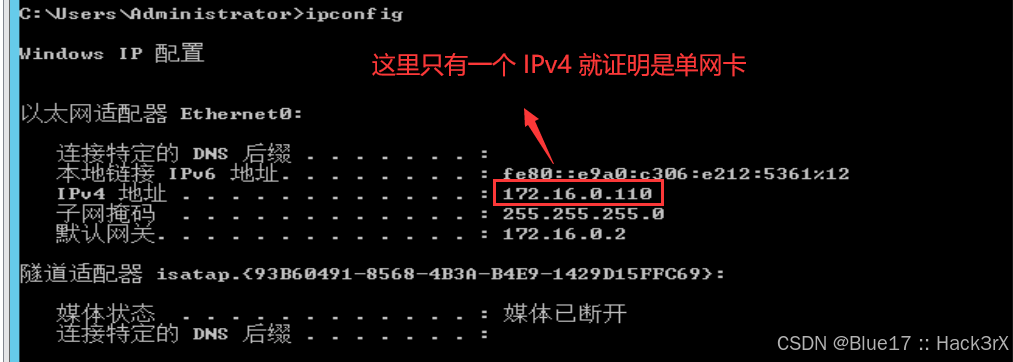
通过下面的命令,我们可以获取到当前机器的网络配置信息,这里主要关注机器有几张网卡,机器网关是啥,IP 是啥,能不能出网:
ipconfig # 显示基本网络信息
ipconfig /all # 显示详细网络信息,可以看到 DNS 信息0x0301:判断网卡数量
判断网卡数量作用:判断当前机器是否连通多网段,可以用来做跨网段攻击。
比如上面的图片,显示就一个 IPv4 地址,就证明是一个单网卡了,如果一个机器有多个 IP,我们就可以假定它能连接多个网段,就可以尝试用这台机器进行网段的横向移动了。
0x0302:收集网关信息
收集网关信息作用:判断有哪些机器可能含有多网卡,能够进行跨网段通信。
在计算机网络实验中,我们划分完 VLAN 后,不同 VLAN 之间的机器想要通信,就是通过网关来实现的,所以如果我们能拿下网关,就可以尝试用网关进行跨网段攻击。
0x0303:收集 DNS 信息
收集 DNS 信息作用:判断域控在哪里。
直接通过 ipconfig 显示不了 DNS 服务器信息,此时可以通过加上 /all 参数,我们前面在模拟普通主机加入域的时,第一步就是将普通主机的 DNS 修改为域控地址,所以通过 DNS 信息,我们可以大致判断域控是哪台机器了。
0x0304:判断机器是否出网
判断机器出网的作用:为权限维持采用的技术做信息支持。
如果能出网我们是不是就可以直接通过反弹 Shell 的方式做权限维持了,如果不出网还得中转机器,十分麻烦。判断出不出网也简单,你尝试 ping baidu.com 就可以了。
0x04:收集当前机器操作系统信息
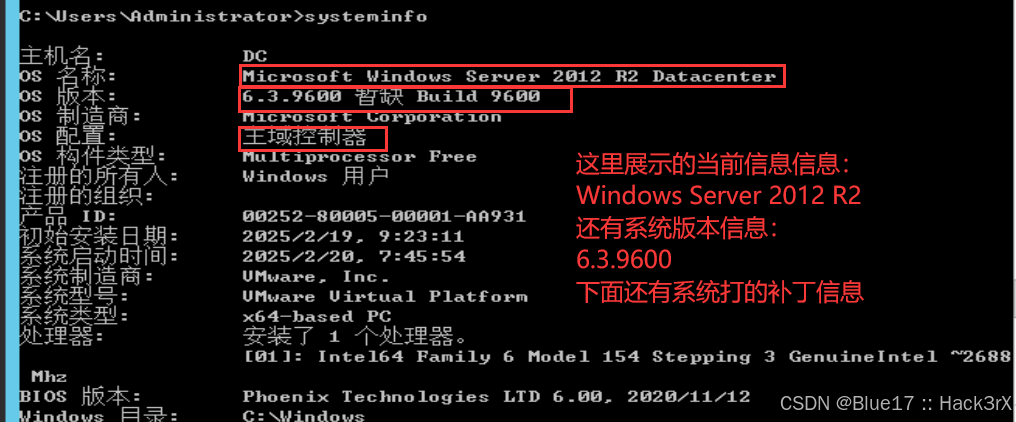
不同的操作系统拥有不同的命令集,不同版本的操作系统拥有的命令也不尽相同。使用下面的命令,可以收集当前操作系统的版本信息,方便我们判断后续应该使用的命令格式:
systeminfo # 可以查看系统信息(Windows Or Linux),系统版本,系统补丁信息
systeminfo | findstr /B /C:"OS Name" /C:"OS Version"
systeminfo | findstr /B /C:"OS 名称" /C:"OS 版本"0x0401:判断系统类型与版本
判断系统类型与版本作用:查找对应系统可能存在的漏洞,为后面使用的命令格式做指导。
这个前面介绍了,不同类型操作系统,同一操作系统的不同版本,命令格式都可能有差别,收集好了,才能对症下药。另外,我们还可以通过系统的版本信息去尝试搜索该系统可能存在的 Nday,进行进一步的攻击。
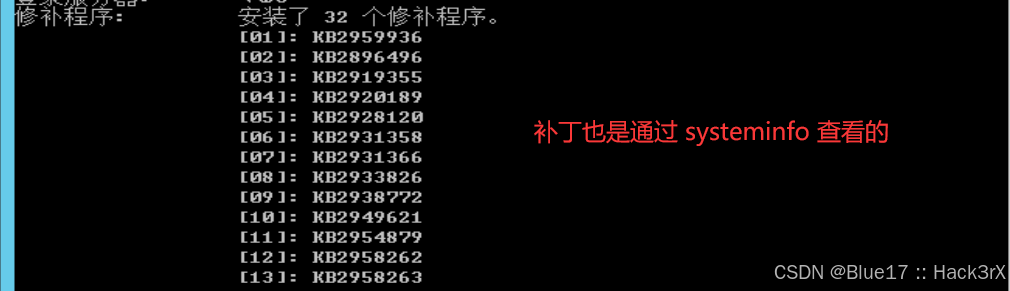
0x0402:收集系统补丁信息
收集系统补丁信息作用:可以查看打的补丁编号与时间,使用未打补丁的漏洞进行攻击。
systeminfo
wmic qfe get Caption,Description,HotFixID,InstalledOn # 推荐用这个查看在前面权限提升的时候我们已经讲过如何根据系统补丁,去反查其可能存在的内核漏洞了,这里就不多说了。
0x0403:收集系统体系结构信息
收集系统体系结构信息作用:我们后面渗透肯定要传软件,使用适合的软件才可以正常运行。
通过下面的命令可以收集到当前操作系统的体系结构信息(多少位,什么操作系统),为我们后面生成木马,或者上传软件做指导:
echo %PROCESSOR_ARCHITECTURE% # 在 cs 与在机器本身中查询的不太一样这里简单介绍一下操作系统的位数:
-
x86:即我们常说的 32 位机器。x86 仅支持 32/16 位代码。 -
AMD64:别名x86-64,即我们常说的 64 位机器。AMD64 向后兼容 x86 的 32/16 位代码。
0x05:收集当前机器软件信息
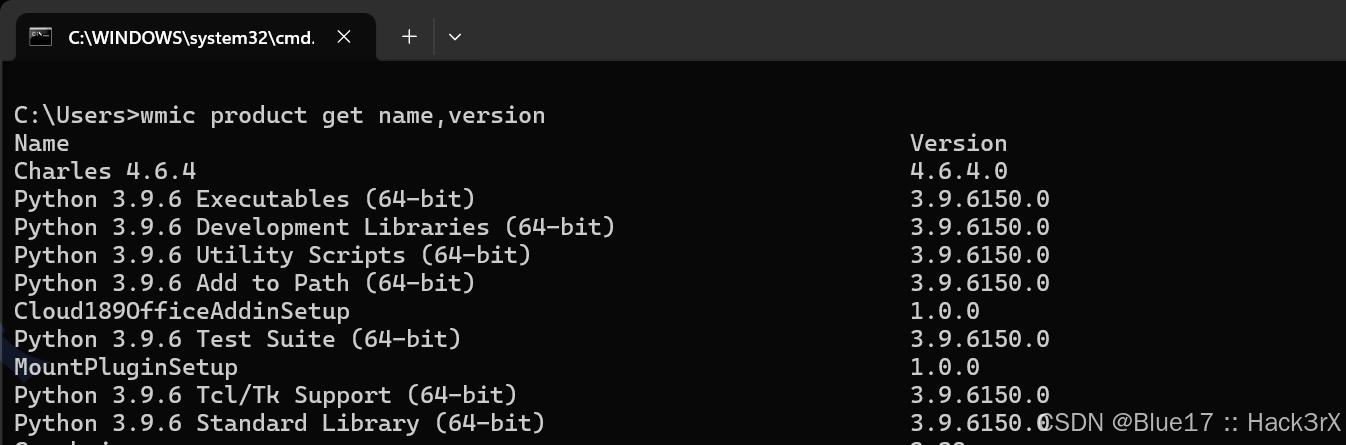
通过下面的命令可以查看当前操作系统中安装的软件及其版本,某些软件自带漏洞,可能造成提权或者给我们后面留后门、横向移动提供便利:
wmic product get name,version
powershell "Get-WmiObject ‐class win32_product | Select‐Object ‐Property name,version"0x06:收集当前机器服务信息
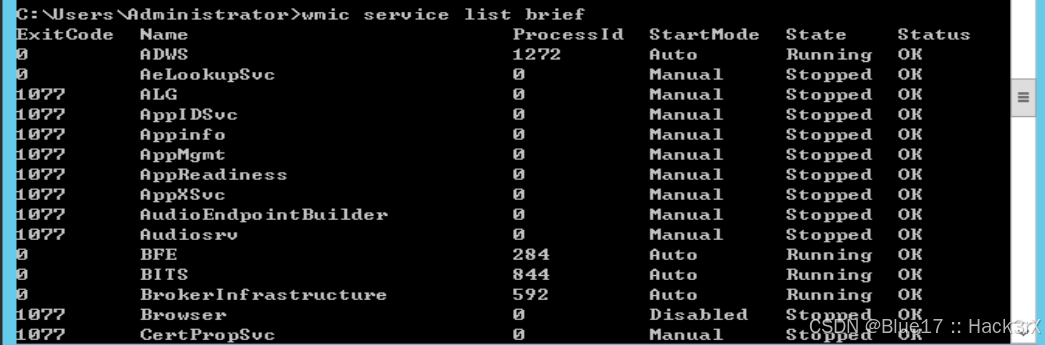
使用下面的命令可以收集当前系统中的服务信息,可以看到各种服务的状态(Windows 利用服务来提权,来留后门了解一下):
wmic service list brief0x07:收集当前机器的进程信息
通过下面的命令可以收集当前系统中的进程信息,我们可以根据进程判断当前机器中运行了哪些软件(具体利用方法未知):
tasklist
wmic process list brief0x08:收集当前机器开机自启程序信息
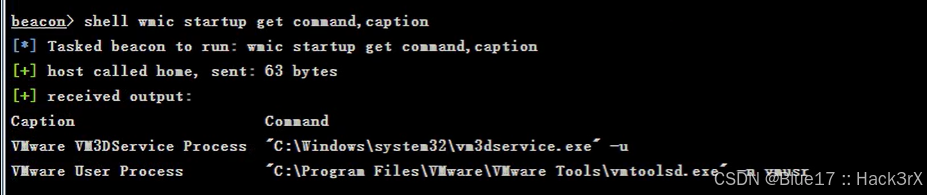
使用下面的命令可以收集到当前机器一开机就会启动的信息(可以方便提权或者留后门哦):
wmic startup get command,caption # 可以展示程序名称与启动命令0x09:收集当前机器计划任务信息
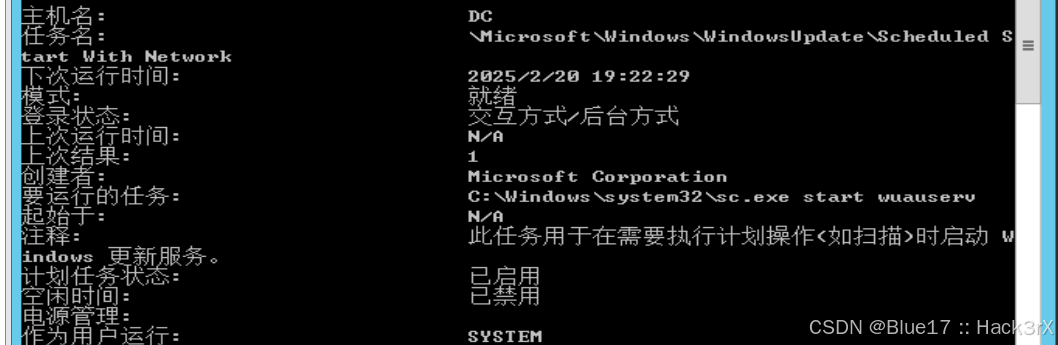
使用下面的命令可以查看当前机器的计划任务信息,若出现无法加载列资源,需要先输入 chcp 437 后再运行查询命令(后面可以用于提权,留后门等操作):
schtasks /query /fo LIST /v0x10:收集当前机器开机时间信息
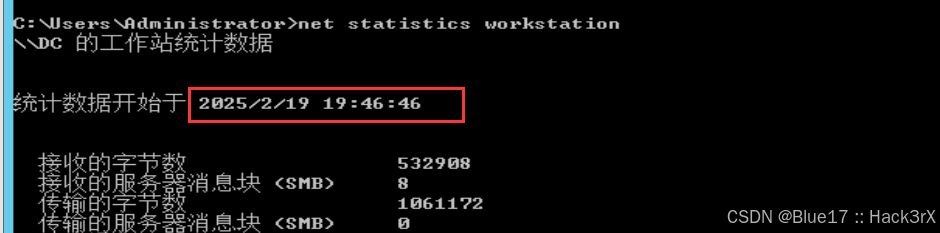
使用下面的命令可以查看当前机器的开机时间(可以用于提权,横向移动):
net statistics workstation0x11:收集当前机器的用户列表信息
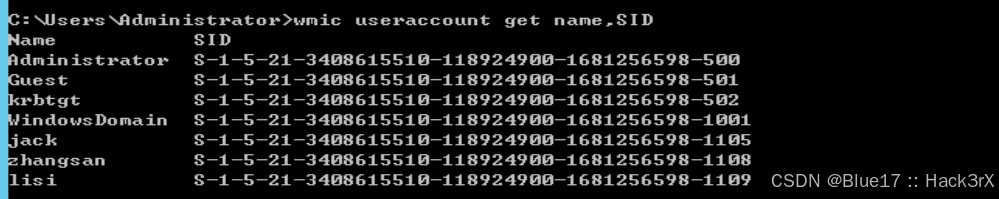
使用下面的命令可以查看当前机器存在的用户信息(除了本地,还有域内的):
net user
wmic useraccount get name,SID # 推荐使用此命令,可以查出克隆账号0x12:收集当前机器的网络连接信息
0x1201:收集网络会话信息
使用下面的命令可以列出当前机器的网络会话:
net session0x1202:收集网络状态信息 — 端口 + 建立的连接
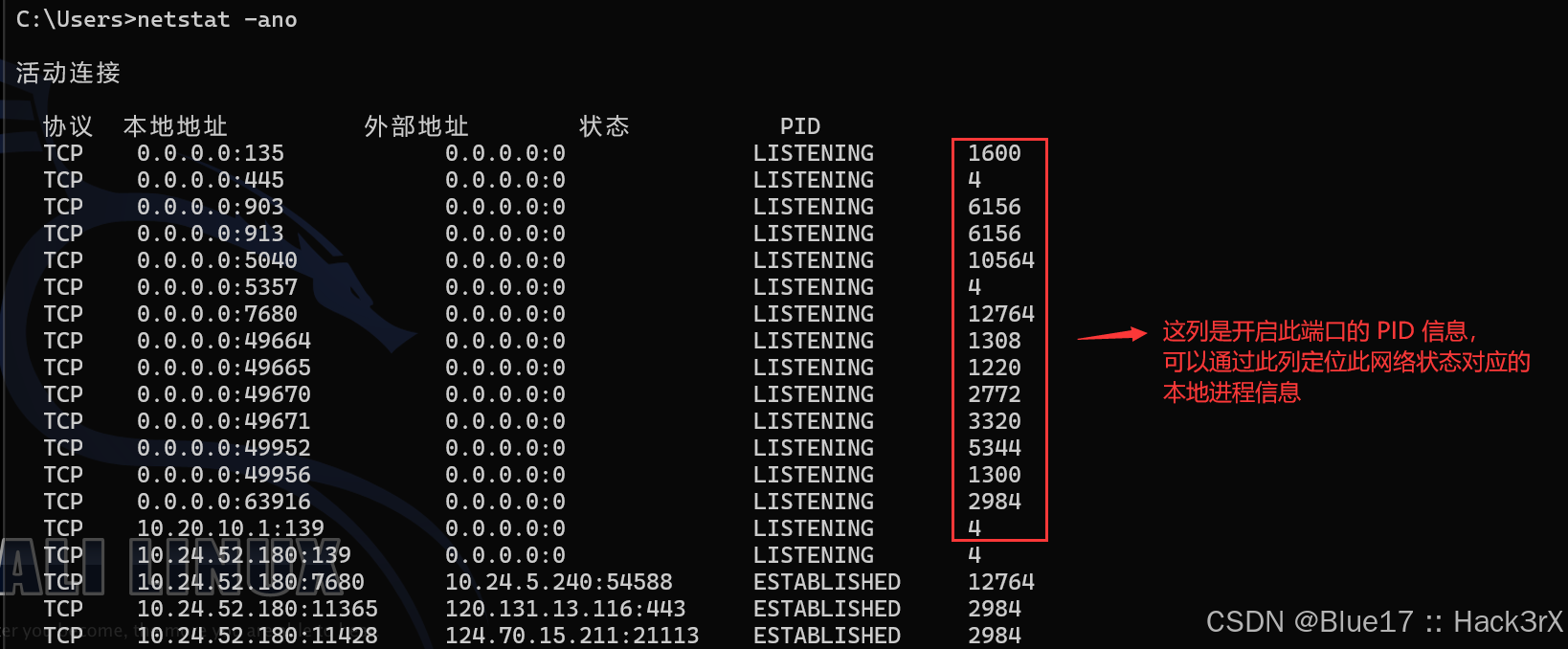
使用下面的命令可以收集到当前机器的网络状态(开放的端口):
netstat -ano # 列出所有的网络连接状态
netstat -ano | findstr <port> # 筛选出对应的端口号
tasklist | findstr <PID> # 根据 PID 号定位进程信息,从而定位软件信息0x13:收集当前机器开放的共享列表
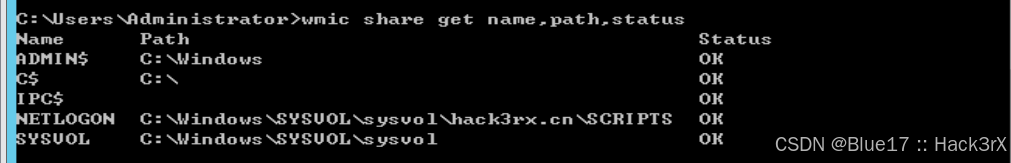
通过下面的命令,可以收集当前机器开放的共享信息,横向移动的时候会讲咋用:
net share
wmic share get name,path,status0x14:收集当前机器路由信息
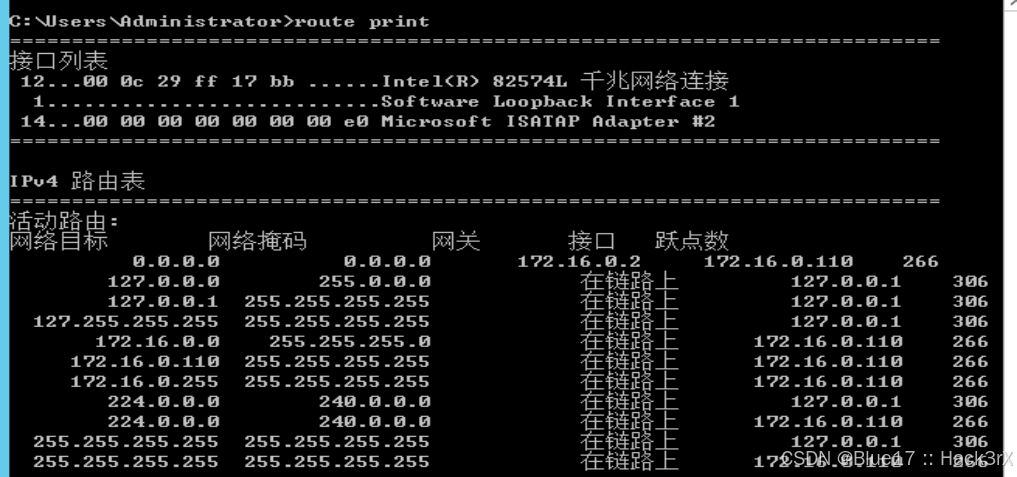
通过下面的命令,我们可以收集到当前机器的路由信息,路由信息可能会泄露内网中的其他网段,为我们后面做内网扫描提供地址依据:
route print0x15:主机防火墙相关操作
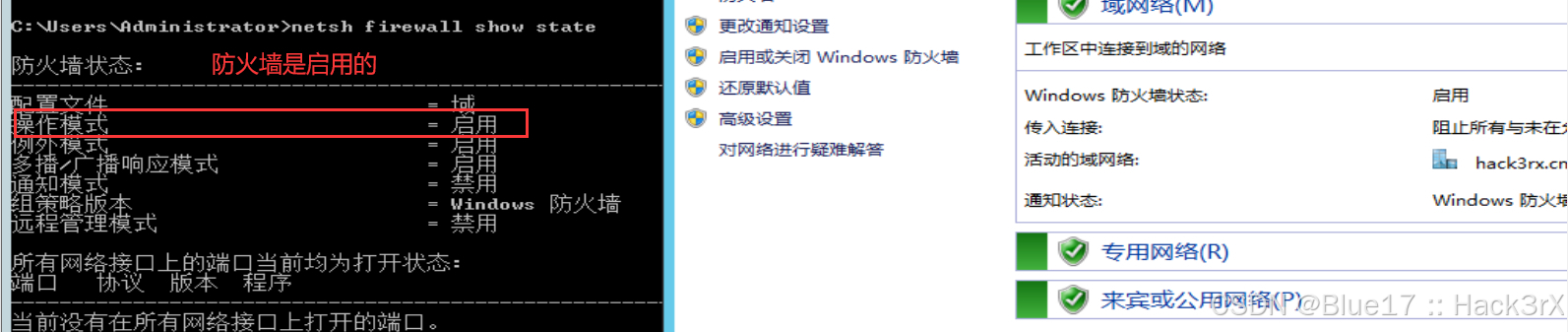
0x1501:查看防火墙是否开启
使用下面的命令可以判断当前机器的防火墙是否开启:
netsh firewall show state # 通过 "操作模式" 判断0x1502:关闭防火墙
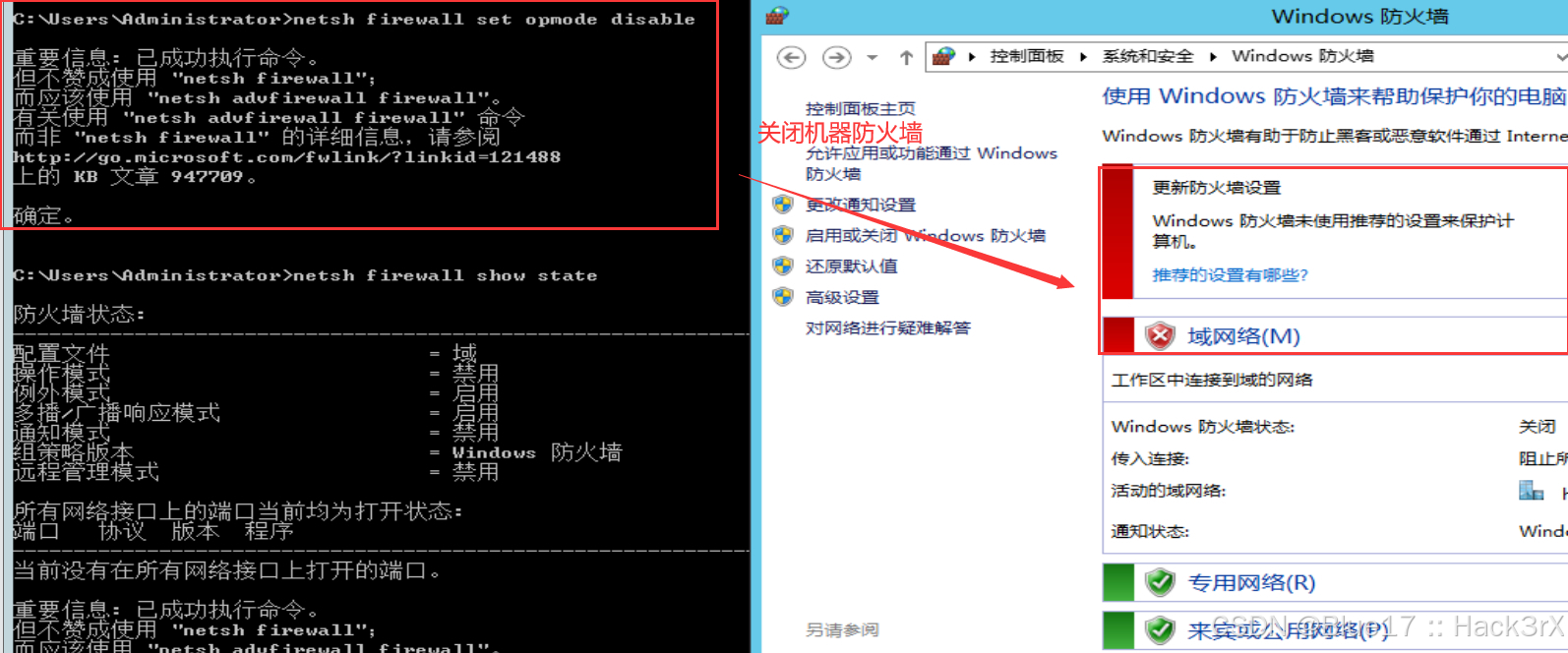
使用下面的命令可以关闭防火墙:
### Windows Server 2003 关闭防火墙:
netsh firewall set opmode disable
### Windows Server 2003 之后关闭防火墙:
netsh firewall set opmode disable # 这个一般只会关掉域的
netsh advfirewall set allprofiles state off # 这个会把所有防火墙都关掉0x1503:查看防火墙配置
使用下面的命令可以查看本机防火墙的配置:
netsh firewall show config0x1504:修改防火墙配置
Windows Server 2003 之前的版本,操作防火墙:
# 允许指定的程序进行全部的连接
netsh firewall add allowedprogram c:\nc.exe "allownc" enableWindows Server 2003 之后的版本,操作防火墙:
# 允许指定程序入网
netsh advfirewall firewall add rule name="pass nc" dir=in action=allow program="C:\nc.exe"
# 允许指定程序出网
netsh advfirewall firewall add rule name="Allownc" dir=out action=allow program="C:\nc.exe"
# 允许指定端口入网
netsh advfirewall firewall add rule name="RemoteDesktop" dir=in action=allow protocol=TCP localport=3389
# 允许指定端口出网
netsh advfirewall firewall add rule name="test" dir=out action=allow protocol=tcp localport=33890x16:主机远程登录(RDP)相关操作
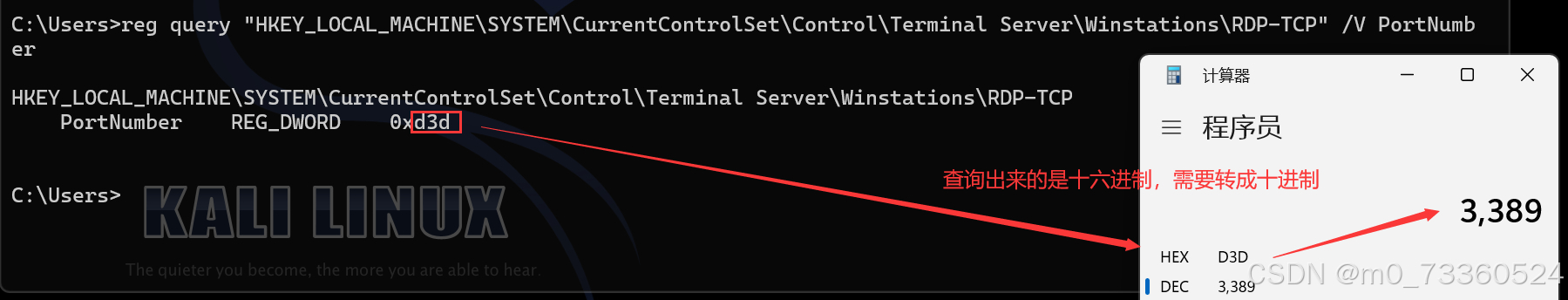
0x1601:查看远程桌面是否开启(查询远程桌面端口)
使用下面的命令,可以从注册表中查询 RDP 远程桌面服务的端口,主要是为了防止管理员修改 RDP 的默认端口,比如改到 5500:
reg query "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\Winstations\RDP-TCP" /V PortNumber查询出来了 RDP 的端口后,可以使用下面的命令查看该端口是否开放,如果开放,则证明开启了该服务,反制,就是没有:
netstat -ano | findstr <PortNumber>
# 示例: netstat -ano | findstr 33890x1602:开启远程桌面服务
Windows Server 2003 机器上,开启远程桌面服务:
# 允许远程桌面服务
wmic path win32_terminalservicesetting where (_CLASS !="") call setallowtsconnections 1Windows Server 2008 和 Windows Server 2021 上,开启远程桌面服务:
# 开启远程桌面服务
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
# 关闭远程桌面服务
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 11111111 /f0x1603:查询本地 RDP 凭证信息
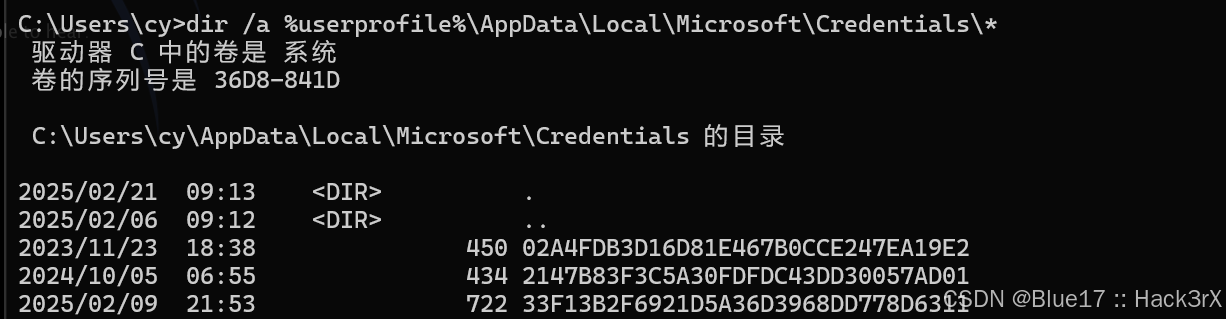
使用如下命令可以查询到本地保存的 RDP 凭证信息,这在后期的横向移动中很有用:
dir /a %userprofile%\AppData\Local\Microsoft\Credentials\*0x17:网络相关 — 查看代理配置信息
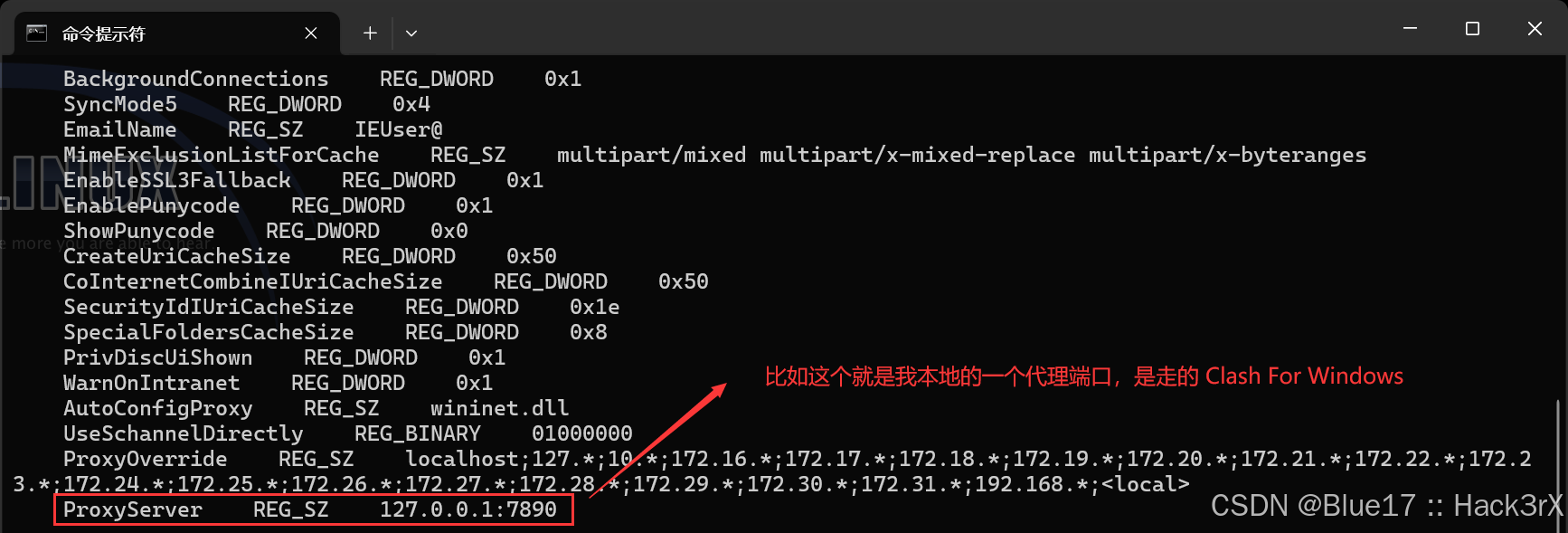
使用下面的命令可以查看当前机器的代理配置信息:
reg query "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings"0x18:网络相关 — 查看本机 ARP 信息
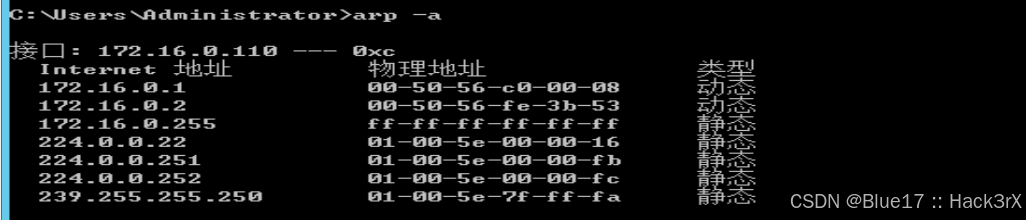
ARP 信息与前面的路由信息一样,可以为我们后面的横向移动提供 IP 地址的指导:
arp -a0x19:查看当前机器保存的登录凭证
使用下面的命令可以查看当前机器保存的登录凭证,这对后期的横向移动很有帮助:
cmdkey /l0x20:查看当前机器本地用户组信息
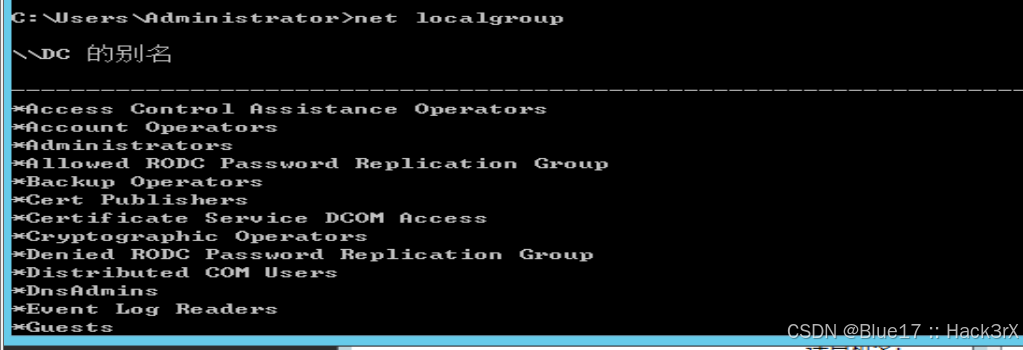
通过以下命令可以查看当前机器的本地用户组,这个主要是针对重要机器的:
net localgroup0x21:查看当前机器管理员组成员列表
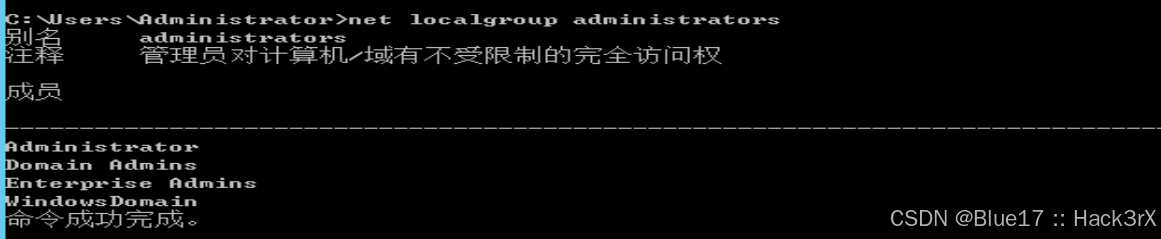
通过以下命令可以查看当前机器的管理员组成员列表(如果你的机器没有加入域,则默认只有一个你当前的用户(伪管理员),和一个 Administrator 用户):
net localgroup administrators如果当前机器加入了域,就会多一个 Domain Admins 组,代表域控里的 Domain Admins 组成员都具有管理权限,上面那个 Enterprise Admins 是企业管理员,也是在域控里配置的。
0x22:查看当前电脑最近打开的文档
使用下面的命令可以查询到当前机器最近打开的文档信息:
dir %APPDATA%\Microsoft\Windows\Recent0x22:密码获取 — WIFI 密码收集
使用下面的命令可以收集当前机器历史连过的 WIFI 的密码信息(如果运行不了,可能得去使用 BAT 脚本的方式进行运行),留意 “关键内容” 字段:
for /f "skip=9 tokens=1,2 delims=:" %i in ('netsh wlan show profiles') do @echo %j | findstr ‐i ‐v echo | netsh wlan show profiles %j key=clear0x23:杀毒软件查询
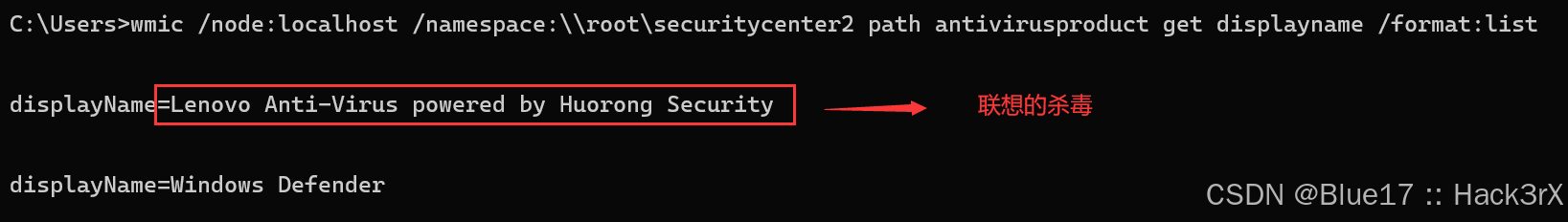
使用下面的命令可以罗列出当前机器中安装的杀毒软件:
wmic /node:localhost /namespace:\\root\securitycenter2 path antivirusproduct get displayname /format:list下面是一些常见的杀毒软件的进程名,如果通过 tasklist 查看到了下面的应用信息,则证明目标安装了对应的杀毒软件:
avList = {
"360tray.exe": "360安全卫士‐实时保护",
"360safe.exe": "360安全卫士‐主程序",
"ZhuDongFangYu.exe": "360安全卫士‐主动防御",
"360sd.exe": "360杀毒",
"a2guard.exe": "a‐squared杀毒",
"ad‐watch.exe": "Lavasoft杀毒",
"cleaner8.exe": "The Cleaner杀毒",
"vba32lder.exe": "vb32杀毒",
"MongoosaGUI.exe": "Mongoosa杀毒",
"CorantiControlCenter32.exe": "Coranti2012杀毒",
"F‐PROT.exe": "F‐Prot AntiVirus",
"CMCTrayIcon.exe": "CMC杀毒",
"K7TSecurity.exe": "K7杀毒",
"UnThreat.exe": "UnThreat杀毒",
"CKSoftShiedAntivirus4.exe": "Shield Antivirus杀毒",
"AVWatchService.exe": "VIRUSfighter杀毒",
"ArcaTasksService.exe": "ArcaVir杀毒",
"iptray.exe": "Immunet杀毒",
"PSafeSysTray.exe": "PSafe杀毒",
"nspupsvc.exe": "nProtect杀毒",
"SpywareTerminatorShield.exe": "SpywareTerminator反间谍软件",
"BKavService.exe": "Bkav杀毒",
"MsMpEng.exe": "Microsoft Security Essentials",
"SBAMSvc.exe": "VIPRE",
"ccSvcHst.exe": "Norton杀毒",
"f‐secure.exe": "冰岛",
"avp.exe": "Kaspersky",
"KvMonXP.exe": "江民杀毒",
"RavMonD.exe": "瑞星杀毒",
"Mcshield.exe": "McAfee",
"Tbmon.exe": "McAfee",
"Frameworkservice.exe": "McAfee",
"egui.exe": "ESET NOD32",
"ekrn.exe": "ESET NOD32",
"eguiProxy.exe": "ESET NOD32",
"kxetray.exe": "金山毒霸",
"knsdtray.exe": "可牛杀毒",
"TMBMSRV.exe": "趋势杀毒",
"avcenter.exe": "Avira(小红伞)",
"avguard.exe": "Avira(小红伞)",
"avgnt.exe": "Avira(小红伞)",
"sched.exe": "Avira(小红伞)",
"ashDisp.exe": "Avast网络安全",
"rtvscan.exe": "诺顿杀毒",
"ccapp.exe": "SymantecNorton",
"NPFMntor.exe": "Norton杀毒软件",
"ccSetMgr.exe": "赛门铁克",
"ccRegVfy.exe": "Norton杀毒软件",
"ksafe.exe": "金山卫士",
"QQPCRTP.exe": "QQ电脑管家",
"avgwdsvc.exe": "AVG杀毒",
"QUHLPSVC.exe": "QUICK HEAL杀毒",
"mssecess.exe": "微软杀毒",
"SavProgress.exe": "Sophos杀毒",
"SophosUI.exe": "Sophos杀毒",
"SophosFS.exe": "Sophos杀毒",
"SophosHealth.exe": "Sophos杀毒",
"SophosSafestore64.exe": "Sophos杀毒",
"SophosCleanM.exe": "Sophos杀毒",
"fsavgui.exe": "F‐Secure杀毒",
"vsserv.exe": "比特梵德",
"remupd.exe": "熊猫卫士",
"FortiTray.exe": "飞塔",
"safedog.exe": "安全狗",
"parmor.exe": "木马克星",
"Iparmor.exe.exe": "木马克星",
"beikesan.exe": "贝壳云安全",
"KSWebShield.exe": "金山网盾",
"TrojanHunter.exe": "木马猎手",
"GG.exe": "巨盾网游安全盾",
"adam.exe": "绿鹰安全精灵",
"AST.exe": "超级巡警",
"ananwidget.exe": "墨者安全专家",
"AVK.exe": "AntiVirusKit",
"avg.exe": "AVG Anti‐Virus",
"spidernt.exe": "Dr.web",
"avgaurd.exe": "Avira Antivir",
"vsmon.exe": "Zone Alarm",
"cpf.exe": "Comodo",
"outpost.exe": "Outpost Firewall",
"rfwmain.exe": "瑞星防火墙",
"kpfwtray.exe": "金山网镖",
"FYFireWall.exe": "风云防火墙",
"MPMon.exe": "微点主动防御",
"pfw.exe": "天网防火墙",
"BaiduSdSvc.exe": "百度杀毒‐服务进程",
"BaiduSdTray.exe": "百度杀毒‐托盘进程",
"BaiduSd.exe": "百度杀毒‐主程序",
"SafeDogGuardCenter.exe": "安全狗",
"safedogupdatecenter.exe": "安全狗",
"safedogguardcenter.exe": "安全狗",
"SafeDogSiteIIS.exe": "安全狗",
"SafeDogTray.exe": "安全狗",
"SafeDogServerUI.exe": "安全狗",
"D_Safe_Manage.exe": "D盾",
"d_manage.exe": "D盾",
"yunsuo_agent_service.exe": "云锁",
"yunsuo_agent_daemon.exe": "云锁",
"HwsPanel.exe": "护卫神",
"hws_ui.exe": "护卫神",
"hws.exe": "护卫神",
"hwsd.exe": "护卫神",
"hipstray.exe": "火绒",
"wsctrl.exe": "火绒",
"usysdiag.exe": "火绒",
"SPHINX.exe": "SPHINX防火墙",
"bddownloader.exe": "百度卫士",
"baiduansvx.exe": "百度卫士‐主进程",
"AvastUI.exe": "Avast!5主程序",
"emet_agent.exe": "EMET",
"emet_service.exe": "EMET",
"firesvc.exe": "McAfee",
"firetray.exe": "McAfee",
"hipsvc.exe": "McAfee",
"mfevtps.exe": "McAfee",
"mcafeefire.exe": "McAfee",
"scan32.exe": "McAfee",
"shstat.exe": "McAfee",
"vstskmgr.exe": "McAfee",
"engineserver.exe": "McAfee",
"mfeann.exe": "McAfee",
"mcscript.exe": "McAfee",
"updaterui.exe": "McAfee",
"udaterui.exe": "McAfee",
"naprdmgr.exe": "McAfee",
"cleanup.exe": "McAfee",
"cmdagent.exe": "McAfee",
"frminst.exe": "McAfee",
"mcscript_inuse.exe": "McAfee",
"mctray.exe": "McAfee",
"_avp32.exe": "卡巴斯基",
"_avpcc.exe": "卡巴斯基",
"_avpm.exe": "卡巴斯基",
"aAvgApi.exe": "AVG",
"ackwin32.exe": "已知杀软进程,名称暂未收录",
"alertsvc.exe": "Norton AntiVirus",
"alogserv.exe": "McAfee VirusScan",
"anti‐trojan.exe": "Anti‐Trojan Elite",
"arr.exe": "Application Request Route",
"atguard.exe": "AntiVir",
"atupdater.exe": "已知杀软进程,名称暂未收录",
"atwatch.exe": "Mustek",
"au.exe": "NSIS",
"aupdate.exe": "Symantec",
"auto‐protect.nav80try.exe": "已知杀软进程,名称暂未收录",
"autodown.exe": "AntiVirus AutoUpdater",
"avconsol.exe": "McAfee",
"avgcc32.exe": "AVG",
"avgctrl.exe": "AVG",
"avgemc.exe": "AVG",
"avgrsx.exe": "AVG",
"avgserv.exe": "AVG",
"avgserv9.exe": "AVG",
"avgw.exe": "AVG",
"avkpop.exe": "G DATA SOFTWARE AG",
"avkserv.exe": "G DATA SOFTWARE AG",
"avkservice.exe": "G DATA SOFTWARE AG",
"avkwctl9.exe": "G DATA SOFTWARE AG",
"avltmain.exe": "Panda Software Aplication",
"avnt.exe": "H+BEDV Datentechnik GmbH",
"avp32.exe": "Kaspersky Anti‐Virus",
"avpcc.exe": " Kaspersky AntiVirus",
"avpdos32.exe": " Kaspersky AntiVirus",
"avpm.exe": " Kaspersky AntiVirus",
"avptc32.exe": " Kaspersky AntiVirus",
"avpupd.exe": " Kaspersky AntiVirus",
"avsynmgr.exe": "McAfee",
"avwin.exe": " H+BEDV",
"bargains.exe": "Exact Advertising SpyWare",
"beagle.exe": "Avast",
"blackd.exe": "BlackICE",
"blackice.exe": "BlackICE",
"blink.exe": "micromedia",
"blss.exe": "CBlaster",
"bootwarn.exe": "Symantec",
"bpc.exe": "Grokster",
"brasil.exe": "Exact Advertising",
"ccevtmgr.exe": "Norton Internet Security",
"cdp.exe": "CyberLink Corp.",
"cfd.exe": "Motive Communications",
"cfgwiz.exe": " Norton AntiVirus",
"claw95.exe": "已知杀软进程,名称暂未收录",
"claw95cf.exe": "已知杀软进程,名称暂未收录",
"clean.exe": "windows流氓软件清理大师",
"cleaner.exe": "windows流氓软件清理大师",
"cleaner3.exe": "windows流氓软件清理大师",
"cleanpc.exe": "windows流氓软件清理大师",
"cpd.exe": "McAfee",
"ctrl.exe": "已知杀软进程,名称暂未收录",
"cv.exe": "已知杀软进程,名称暂未收录",
"defalert.exe": "Symantec",
"defscangui.exe": "Symantec",
"defwatch.exe": "Norton Antivirus",
"doors.exe": "已知杀软进程,名称暂未收录",
"dpf.exe": "已知杀软进程,名称暂未收录",
"dpps2.exe": "PanicWare",
"dssagent.exe": "Broderbund",
"ecengine.exe": "已知杀软进程,名称暂未收录",
"emsw.exe": "Alset Inc",
"ent.exe": "已知杀软进程,名称暂未收录",
"espwatch.exe": "已知杀软进程,名称暂未收录",
"ethereal.exe": "RationalClearCase",
"exe.avxw.exe": "已知杀软进程,名称暂未收录",
"expert.exe": "已知杀软进程,名称暂未收录",
"f‐prot95.exe": "已知杀软进程,名称暂未收录",
"fameh32.exe": "F‐Secure",
"fast.exe": " FastUsr",
"fch32.exe": "F‐Secure",
"fih32.exe": "F‐Secure",
"findviru.exe": "F‐Secure",
"firewall.exe": "AshampooSoftware",
"fnrb32.exe": "F‐Secure",
"fp‐win.exe": " F‐Prot Antivirus OnDemand",
"fsaa.exe": "F‐Secure",
"fsav.exe": "F‐Secure",
"fsav32.exe": "F‐Secure",
"fsav530stbyb.exe": "F‐Secure",
"fsav530wtbyb.exe": "F‐Secure",
"fsav95.exe": "F‐Secure",
"fsgk32.exe": "F‐Secure",
"fsm32.exe": "F‐Secure",
"fsma32.exe": "F‐Secure",
"fsmb32.exe": "F‐Secure",
"gbmenu.exe": "已知杀软进程,名称暂未收录",
"guard.exe": "ewido",
"guarddog.exe": "ewido",
"htlog.exe": "已知杀软进程,名称暂未收录",
"htpatch.exe": "Silicon Integrated Systems Corporation",
"hwpe.exe": "已知杀软进程,名称暂未收录",
"iamapp.exe": "Symantec",
"iamserv.exe": "Symantec",
"iamstats.exe": "Symantec",
"iedriver.exe": " Urlblaze.com",
"iface.exe": "Panda Antivirus Module",
"infus.exe": "Infus Dialer",
"infwin.exe": "Msviewparasite",
"intdel.exe": "Inet Delivery",
"intren.exe": "已知杀软进程,名称暂未收录",
"jammer.exe": "已知杀软进程,名称暂未收录",
"kavpf.exe": "Kapersky",
"kazza.exe": "Kapersky",
"keenvalue.exe": "EUNIVERSE INC",
"launcher.exe": "Intercort Systems",
"ldpro.exe": "已知杀软进程,名称暂未收录",
"ldscan.exe": "Windows Trojans Inspector",
"localnet.exe": "已知杀软进程,名称暂未收录",
"luall.exe": "Symantec",
"luau.exe": "Symantec",
"lucomserver.exe": "Norton",
"mcagent.exe": "McAfee",
"mcmnhdlr.exe": "McAfee",
"mctool.exe": "McAfee",
"mcupdate.exe": "McAfee",
"mcvsrte.exe": "McAfee",
"mcvsshld.exe": "McAfee",
"mfin32.exe": "MyFreeInternetUpdate",
"mfw2en.exe": "MyFreeInternetUpdate",
"mfweng3.02d30.exe": "MyFreeInternetUpdate",
"mgavrtcl.exe": "McAfee",
"mgavrte.exe": "McAfee",
"mghtml.exe": "McAfee",
"mgui.exe": "BullGuard",
"minilog.exe": "Zone Labs Inc",
"mmod.exe": "EzulaInc",
"mostat.exe": "WurldMediaInc",
"mpfagent.exe": "McAfee",
"mpfservice.exe": "McAfee",
"mpftray.exe": "McAfee",
"mscache.exe": "Integrated Search Technologies Spyware",
"mscman.exe": "OdysseusMarketingInc",
"msmgt.exe": "Total Velocity Spyware",
"msvxd.exe": "W32/Datom‐A",
"mwatch.exe": "已知杀软进程,名称暂未收录",
"nav.exe": "Reuters Limited",
"navapsvc.exe": "Norton AntiVirus",
"navapw32.exe": "Norton AntiVirus",
"navw32.exe": "Norton Antivirus",
"ndd32.exe": "诺顿磁盘医生",
"neowatchlog.exe": "已知杀软进程,名称暂未收录",
"netutils.exe": "已知杀软进程,名称暂未收录",
"nisserv.exe": "Norton",
"nisum.exe": "Norton",
"nmain.exe": "Norton",
"nod32.exe": "ESET Smart Security",
"norton_internet_secu_3.0_407.exe": "已知杀软进程,名称暂未收录",
"notstart.exe": "已知杀软进程,名称暂未收录",
"nprotect.exe": "Symantec",
"npscheck.exe": "Norton",
"npssvc.exe": "Norton",
"ntrtscan.exe": "趋势反病毒应用程序",
"nui.exe": "已知杀软进程,名称暂未收录",
"otfix.exe": "已知杀软进程,名称暂未收录",
"outpostinstall.exe": "Outpost",
"patch.exe": "趋势科技",
"pavw.exe": "已知杀软进程,名称暂未收录",
"pcscan.exe": "趋势科技",
"pdsetup.exe": "已知杀软进程,名称暂未收录",
"persfw.exe": "Tiny Personal Firewall",
"pgmonitr.exe": "PromulGate SpyWare",
"pingscan.exe": "已知杀软进程,名称暂未收录",
"platin.exe": "已知杀软进程,名称暂未收录",
"pop3trap.exe": "PC‐cillin",
"poproxy.exe": "NortonAntiVirus",
"popscan.exe": "已知杀软进程,名称暂未收录",
"powerscan.exe": "Integrated Search Technologies",
"ppinupdt.exe": "已知杀软进程,名称暂未收录",
"pptbc.exe": "已知杀软进程,名称暂未收录",
"ppvstop.exe": "已知杀软进程,名称暂未收录",
"prizesurfer.exe": "Prizesurfer",
"prmt.exe": "OpiStat",
"prmvr.exe": "Adtomi",
"processmonitor.exe": "Sysinternals",
"proport.exe": "已知杀软进程,名称暂未收录",
"protectx.exe": "ProtectX",
"pspf.exe": "已知杀软进程,名称暂未收录",
"purge.exe": "已知杀软进程,名称暂未收录",
"qconsole.exe": "Norton AntiVirus Quarantine Console",
"qserver.exe": "Norton Internet Security",
"rapapp.exe": "BlackICE",
"rb32.exe": "RapidBlaster",
"rcsync.exe": "PrizeSurfer",
"realmon.exe": "Realmon ",
"rescue.exe": "已知杀软进程,名称暂未收录",
"rescue32.exe": "卡巴斯基互联网安全套装",
"rshell.exe": "已知杀软进程,名称暂未收录",
"rtvscn95.exe": "Real‐time virus scanner ",
"rulaunch.exe": "McAfee User Interface",
"run32dll.exe": "PAL PC Spy",
"safeweb.exe": "PSafe Tecnologia",
"sbserv.exe": "Norton Antivirus",
"scrscan.exe": "360杀毒",
"sfc.exe": "System file checker",
"sh.exe": "MKS Toolkit for Win3",
"showbehind.exe": "MicroSmarts Enterprise Component ",
"soap.exe": "System Soap Pro",
"sofi.exe": "已知杀软进程,名称暂未收录",
"sperm.exe": "已知杀软进程,名称暂未收录",
"supporter5.exe": "eScorcher反病毒",
"symproxysvc.exe": "Symantec",
"symtray.exe": "Symantec",
"tbscan.exe": "ThunderBYTE",
"tc.exe": "TimeCalende",
"titanin.exe": "TitanHide",
"tvmd.exe": "Total Velocity",
"tvtmd.exe": " Total Velocity",
"vettray.exe": "eTrust",
"vir‐help.exe": "已知杀软进程,名称暂未收录",
"vnpc3000.exe": "已知杀软进程,名称暂未收录",
"vpc32.exe": "Symantec",
"vpc42.exe": "Symantec",
"vshwin32.exe": "McAfee",
"vsmain.exe": "McAfee",
"vsstat.exe": "McAfee",
"wfindv32.exe": "已知杀软进程,名称暂未收录",
"zapro.exe": "Zone Alarm",
"zonealarm.exe": "Zone Alarm",
"AVPM.exe": "Kaspersky",
"A2CMD.exe": "Emsisoft Anti‐Malware",
"A2SERVICE.exe": "a‐squared free",
"A2FREE.exe": "a‐squared Free",
"ADVCHK.exe": "Norton AntiVirus",
"AGB.exe": "安天防线",
"AHPROCMONSERVER.exe": "安天防线",
"AIRDEFENSE.exe": "AirDefense",
"ALERTSVC.exe": "Norton AntiVirus",
"AVIRA.exe": "小红伞杀毒",
"AMON.exe": "Tiny Personal Firewall",
"AVZ.exe": "AVZ",
"ANTIVIR.exe": "已知杀软进程,名称暂未收录",
"APVXDWIN.exe": "熊猫卫士",
"ASHMAISV.exe": "Alwil",
"ASHSERV.exe": "Avast Anti‐virus",
"ASHSIMPL.exe": "AVAST!VirusCleaner",
"ASHWEBSV.exe": "Avast",
"ASWUPDSV.exe": "Avast",
"ASWSCAN.exe": "Avast",
"AVCIMAN.exe": "熊猫卫士",
"AVCONSOL.exe": "McAfee",
"AVENGINE.exe": "熊猫卫士",
"AVESVC.exe": "Avira AntiVir Security Service",
"AVEVL32.exe": "已知杀软进程,名称暂未收录",
"AVGAM.exe": "AVG",
"AVGCC.exe": "AVG",
"AVGCHSVX.exe": "AVG",
"AVGCSRVX": "AVG",
"AVGNSX.exe": "AVG",
"AVGCC32.exe": "AVG",
"AVGCTRL.exe": "AVG",
"AVGEMC.exe": "AVG",
"AVGFWSRV.exe": "AVG",
"AVGNTMGR.exe": "AVG",
"AVGSERV.exe": "AVG",
"AVGTRAY.exe": "AVG",
"AVGUPSVC.exe": "AVG",
"AVINITNT.exe": "Command AntiVirus for NT Server",
"AVPCC.exe": "Kaspersky",
"AVSERVER.exe": "Kerio MailServer",
"AVSCHED32.exe": "H+BEDV",
"AVSYNMGR.exe": "McAfee",
"AVWUPSRV.exe": "H+BEDV",
"BDSWITCH.exe": "BitDefender Module",
"BLACKD.exe": "BlackICE",
"CCEVTMGR.exe": "Symantec",
"CFP.exe": "COMODO",
"CLAMWIN.exe": "ClamWin Portable",
"CUREIT.exe": "DrWeb CureIT",
"DEFWATCH.exe": "Norton Antivirus",
"DRWADINS.exe": "Dr.Web",
"DRWEB.exe": "Dr.Web",
"DEFENDERDAEMON.exe": "ShadowDefender",
"EWIDOCTRL.exe": "Ewido Security Suite",
"EZANTIVIRUSREGISTRATIONCHECK.exe": "e‐Trust Antivirus",
"FIREWALL.exe": "AshampooSoftware",
"FPROTTRAY.exe": "F‐PROT Antivirus",
"FPWIN.exe": "Verizon",
"FRESHCLAM.exe": "ClamAV",
"FSAV32.exe": "F‐Secure",
"FSBWSYS.exe": "F‐secure",
"FSDFWD.exe": "F‐Secure",
"FSGK32.exe": "F‐Secure",
"FSGK32ST.exe": "F‐Secure",
"FSMA32.exe": "F‐Secure",
"FSMB32.exe": "F‐Secure",
"FSSM32.exe": "F‐Secure",
"GUARDGUI.exe": "网游保镖",
"GUARDNT.exe": "IKARUS",
"IAMAPP.exe": "Symantec",
"INOCIT.exe": "eTrust",
"INORPC.exe": "eTrust",
"INORT.exe": "eTrust",
"INOTASK.exe": "eTrust",
"INOUPTNG.exe": "eTrust",
"ISAFE.exe": "eTrust",
"KAV.exe": "Kaspersky",
"KAVMM.exe": "Kaspersky",
"KAVPF.exe": "Kaspersky",
"KAVPFW.exe": "Kaspersky",
"KAVSTART.exe": "Kaspersky",
"KAVSVC.exe": "Kaspersky",
"KAVSVCUI.exe": "Kaspersky",
"KMAILMON.exe": "金山毒霸",
"MCAGENT.exe": "McAfee",
"MCMNHDLR.exe": "McAfee",
"MCREGWIZ.exe": "McAfee",
"MCUPDATE.exe": "McAfee",
"MCVSSHLD.exe": "McAfee",
"MINILOG.exe": "Zone Alarm",
"MYAGTSVC.exe": "McAfee",
"MYAGTTRY.exe": "McAfee",
"NAVAPSVC.exe": "Norton",
"NAVAPW32.exe": "Norton",
"NAVLU32.exe": "Norton",
"NAVW32.exe": "Norton Antivirus",
"NEOWATCHLOG.exe": "NeoWatch",
"NEOWATCHTRAY.exe": "NeoWatch",
"NISSERV.exe": "Norton",
"CFP.exe": "COMODO",
"CLAMWIN.exe": "ClamWin Portable",
"CUREIT.exe": "DrWeb CureIT",
"DEFWATCH.exe": "Norton Antivirus",
"DRWADINS.exe": "Dr.Web",
"DRWEB.exe": "Dr.Web",
"DEFENDERDAEMON.exe": "ShadowDefender",
"EWIDOCTRL.exe": "Ewido Security Suite",
"EZANTIVIRUSREGISTRATIONCHECK.exe": "e‐Trust Antivirus",
"FIREWALL.exe": "AshampooSoftware",
"FPROTTRAY.exe": "F‐PROT Antivirus",
"FPWIN.exe": "Verizon",
"FRESHCLAM.exe": "ClamAV",
"FSAV32.exe": "F‐Secure",
"FSBWSYS.exe": "F‐secure",
"FSDFWD.exe": "F‐Secure",
"FSGK32.exe": "F‐Secure",
"FSGK32ST.exe": "F‐Secure",
"FSMA32.exe": "F‐Secure",
"FSMB32.exe": "F‐Secure",
"FSSM32.exe": "F‐Secure",
"GUARDGUI.exe": "网游保镖",
"GUARDNT.exe": "IKARUS",
"IAMAPP.exe": "Symantec",
"INOCIT.exe": "eTrust",
"INORPC.exe": "eTrust",
"INORT.exe": "eTrust",
"INOTASK.exe": "eTrust",
"INOUPTNG.exe": "eTrust",
"ISAFE.exe": "eTrust",
"KAV.exe": "Kaspersky",
"KAVMM.exe": "Kaspersky",
"KAVPF.exe": "Kaspersky",
"KAVPFW.exe": "Kaspersky",
"KAVSTART.exe": "Kaspersky",
"KAVSVC.exe": "Kaspersky",
"KAVSVCUI.exe": "Kaspersky",
"KMAILMON.exe": "金山毒霸",
"MCAGENT.exe": "McAfee",
"MCMNHDLR.exe": "McAfee",
"MCREGWIZ.exe": "McAfee",
"MCUPDATE.exe": "McAfee",
"MCVSSHLD.exe": "McAfee",
"MINILOG.exe": "Zone Alarm",
"MYAGTSVC.exe": "McAfee",
"MYAGTTRY.exe": "McAfee",
"NAVAPSVC.exe": "Norton",
"NAVAPW32.exe": "Norton",
"NAVLU32.exe": "Norton",
"NAVW32.exe": "Norton Antivirus",
"NEOWATCHLOG.exe": "NeoWatch",
"NEOWATCHTRAY.exe": "NeoWatch",
"NISSERV.exe": "Norton",
"VBA32PP3.exe": "已知杀软进程,名称暂未收录",
"VCRMON.exe": "VirusChaser",
"VRMONNT.exe": "HAURI",
"VRMONSVC.exe": "HAURI",
"VSHWIN32.exe": "McAfee",
"VSSTAT.exe": "McAfee",
"XCOMMSVR.exe": "BitDefender",
"ZONEALARM.exe": "Zone Alarm",
"360rp.exe": "360杀毒",
"afwServ.exe": " Avast Antivirus ",
"safeboxTray.exe": "360杀毒",
"360safebox.exe": "360杀毒",
"QQPCTray.exe": "QQ电脑管家",
"KSafeTray.exe": "金山毒霸",
"KSafeSvc.exe": "金山毒霸",
"KWatch.exe": "金山毒霸",
"gov_defence_service.exe": "云锁",
"gov_defence_daemon.exe": "云锁",
"smartscreen.exe": "Windows Defender"
};