今天再给大家分享一下如何使用wireshark对wpa2、wpa3加密数据进行解密~
本文目录:
How To Decrypt802.11
如何基于wpa_supplicant获取key
如何进行解密
如何通过TK解密wpa2、wpa3空口
解密方法落地
How To Decrypt802.11
Wireshark可以解密WEP、WPA、WPA2、WPA3预共享(或者个人)模式的加密数据,在Wireshark 2.0之后的版本,WPA/WPA2企业模式也可以解密,但是有一些限制;
如何基于wpa_supplicant获取key
//在wpa_supplicant当中添加如下patch
src/drivers/driver_nl80211.c b/src/drivers/driver_nl80211.c
3726 static int wpa_driver_nl80211_set_key(struct i802_bss *bss,
3727 struct wpa_driver_set_key_params *params)
+ for (size_t i = 0; i < key_len; i++) {
+ wpa_printf(MSG_DEBUG, "get debug key %02x ", key[i]);
+ }
+ wpa_hexdump(MSG_ERROR, "DEBUG print dump", key, key_len);
ifindex = if_nametoindex(ifname);
wpa_printf(MSG_DEBUG, "%s: ifindex=%d (%s) alg=%d addr=%p key_idx=%d "
- "set_tx=%d seq_len=%lu key_len=%lu key_flag=0x%x link_id=%d",
+ "set_tx=%d seq_len=%lu key_len=%lu key_flag=0x%x link_id=%d key=%02x",
__func__, ifindex, ifname, alg, addr, key_idx, set_tx,
(unsigned long) seq_len, (unsigned long) key_len, key_flag,
- link_id);
+ link_id), *key;如何进行解密
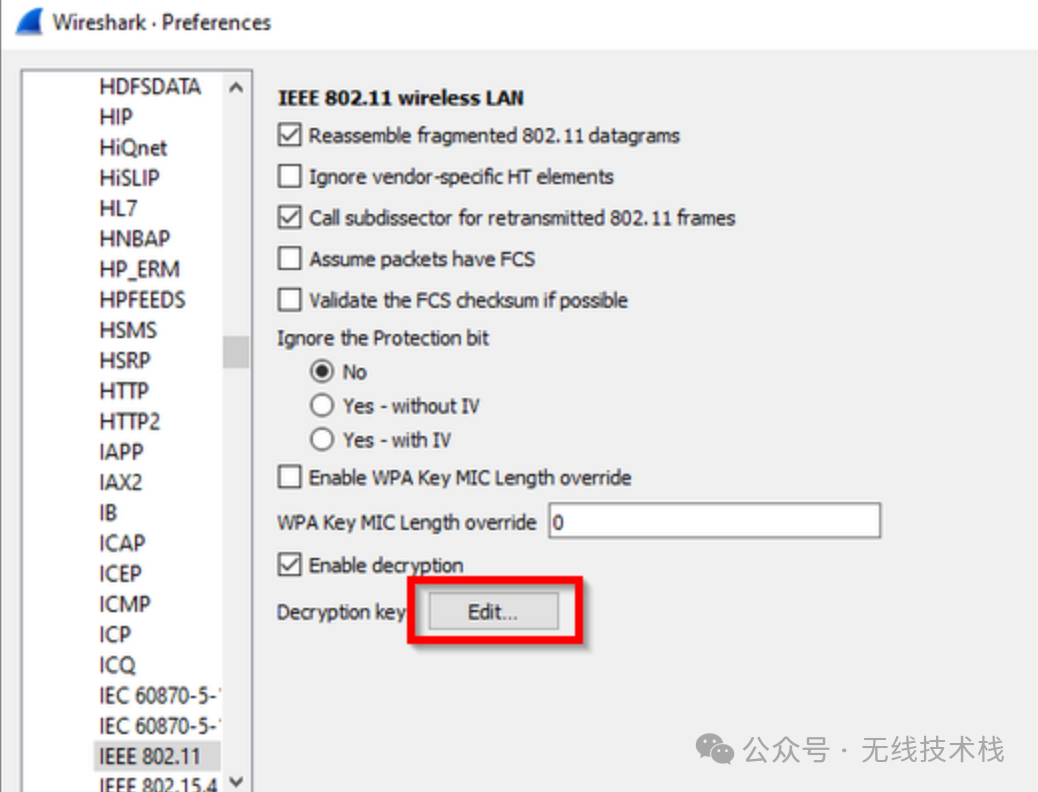
(1)Go to Edit->Preferences->Protocols->IEEE 802.11. You should see a window that looks like this:
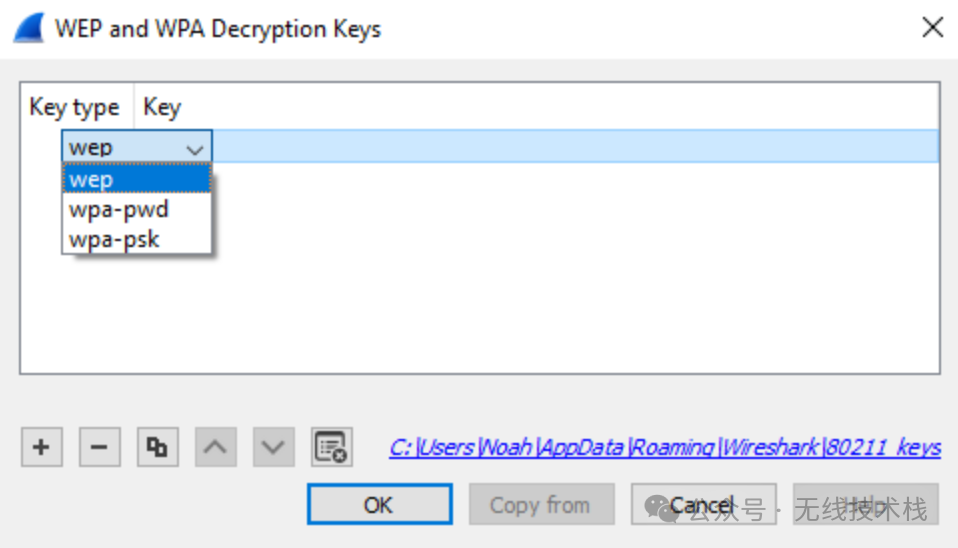
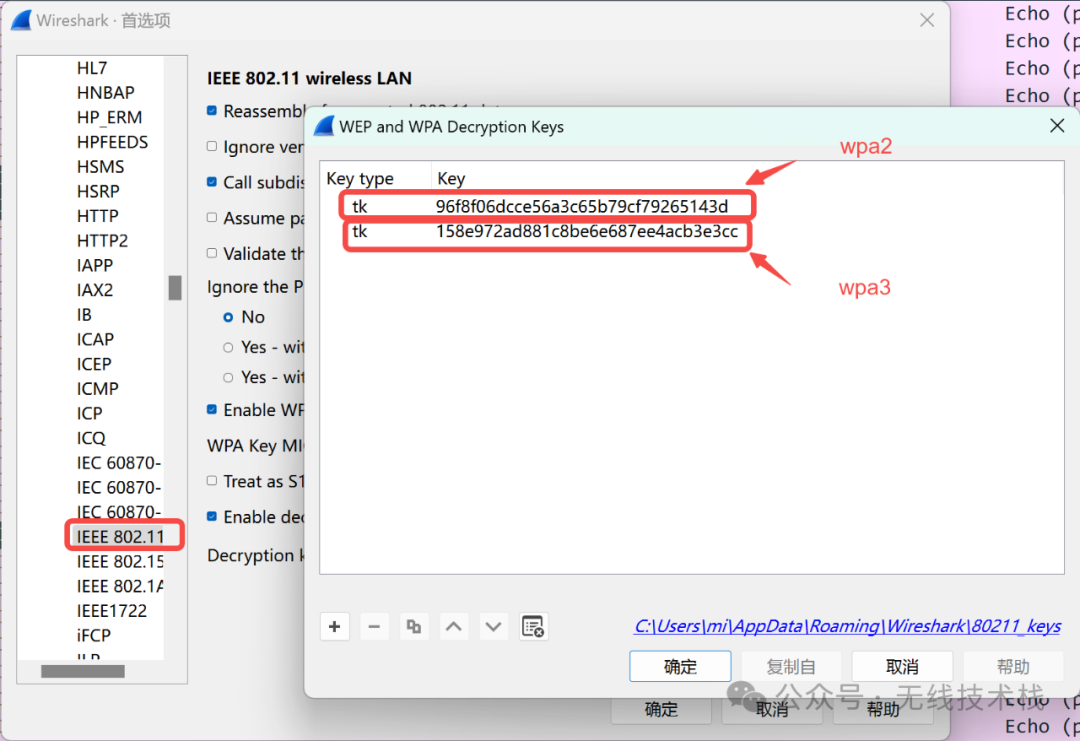
(2)Click on the "Edit..." button next to "Decryption Keys" to add keys. You should see a window that looks like this:
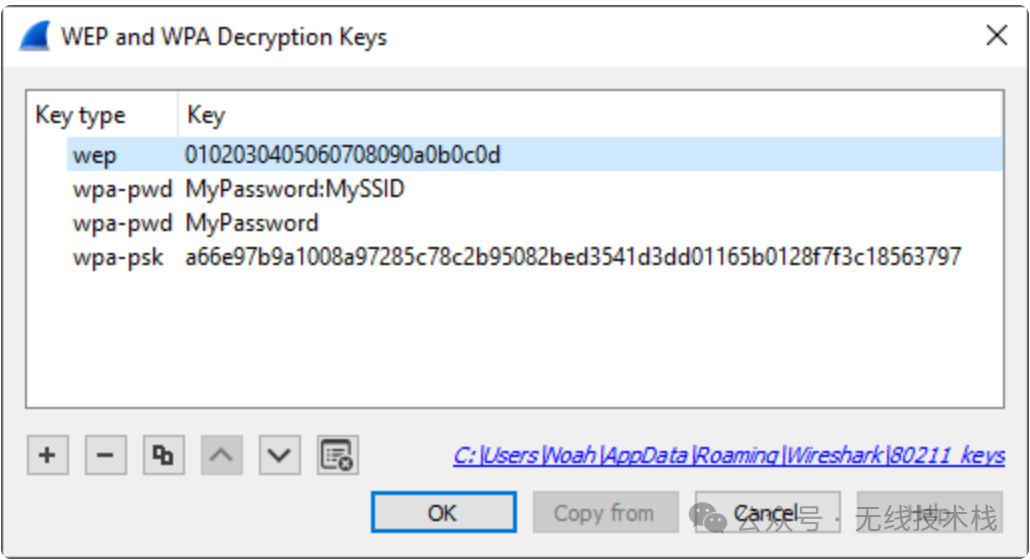
如上图,我们可以点击"+"添加新的key,这里有三种选择:wep、wpa-pwd、wpa-psk;
WEP:key必须是带或者不带冒号的十六进制字符串被解析
a1:b2:c3:d4:e50102030405060708090a0b0c0d
wpa-pwd:wpa key使用密码和SSID创建
MyPassword:MySSIDwpa-psk:
0102030405060708091011...6061626364如何通过TK解密wpa2、wpa3空口
可以使用PTK/GTK的key信息进行解密,wpa2/wpa3通用;
wpa2:
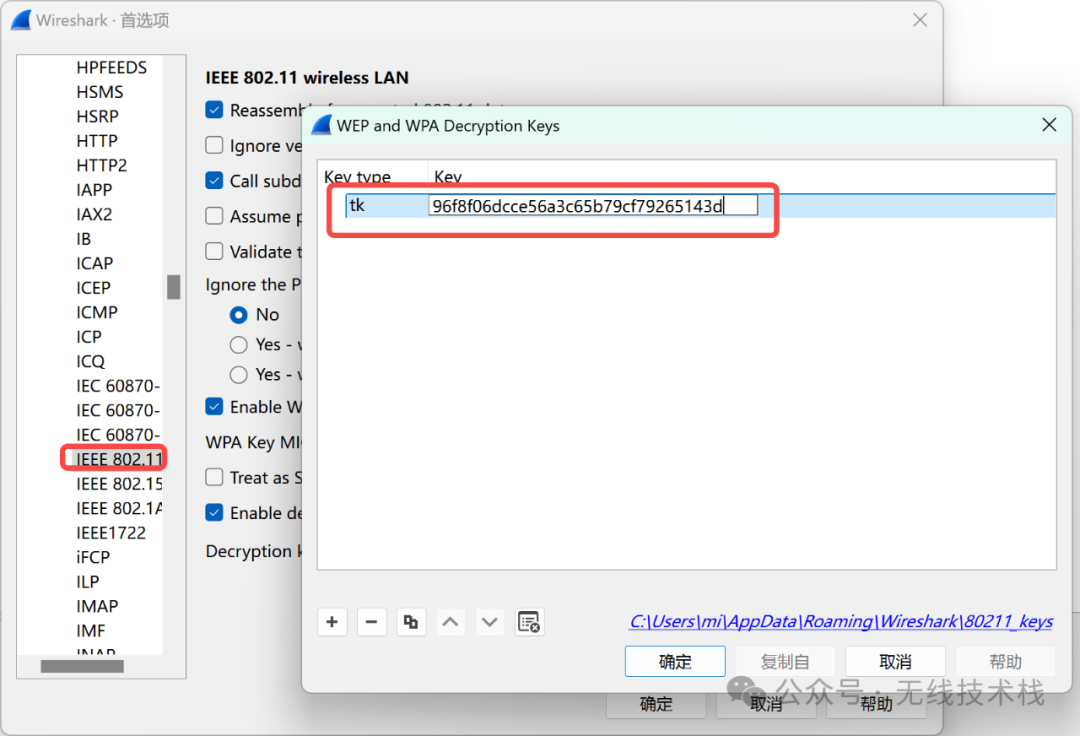
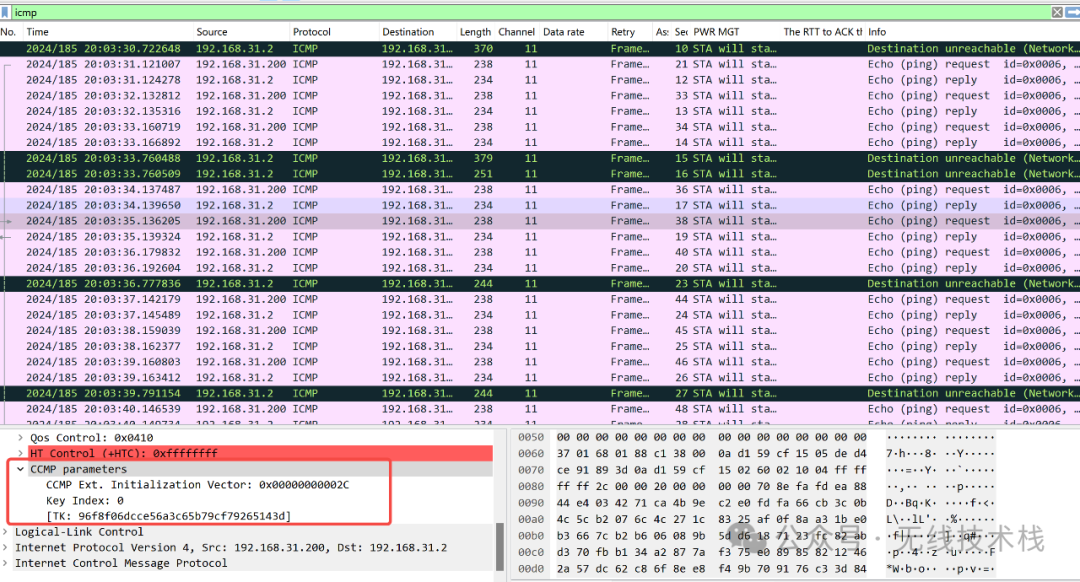
key:96f8f06dcce56a3c65b79cf79265143d
//加了patch之后wpa_supplicant的打印35632:07-03 20:11:44.219 30968 30968 D wpa_supplicant: wlan0: WPA: Installing PTK to the driver35650:07-03 20:11:44.219 30968 30968 E wpa_supplicant: DEBUG print dump - hexdump(len=16): 96 f8 f0 6d cc e5 6a 3c 65 b7 9c f7 92 65 14 3d35651:07-03 20:11:44.219 30968 30968 D wpa_supplicant: wpa_driver_nl80211_set_key: ifindex=24 (wlan0) alg=3 addr=0xb40000757b1a6d20 key_idx=0 set_tx=1 seq_len=6 key_len=16 key_flag=0x2c link_id=-1 anjss key=ffffffd835737:07-03 20:11:44.224 30968 30968 D wpa_supplicant: wlan0: WPA: Installing GTK to the driver (keyidx=1 tx=0 len=16)35755:07-03 20:11:44.224 30968 30968 E wpa_supplicant: DEBUG print dump - hexdump(len=16): 2a 46 c6 c9 b6 47 21 4f dc ef 9f 26 3f ac 5d c035756:07-03 20:11:44.224 30968 30968 D wpa_supplicant: wpa_driver_nl80211_set_key: ifindex=24 (wlan0) alg=3 addr=0x58dc253e4e key_idx=1 set_tx=0 seq_len=6 key_len=16 key_flag=0x14 link_id=-1 anjss key=9de2a59a
在wireshark中添加tk信息:
解密之后的效果:
wpa3:
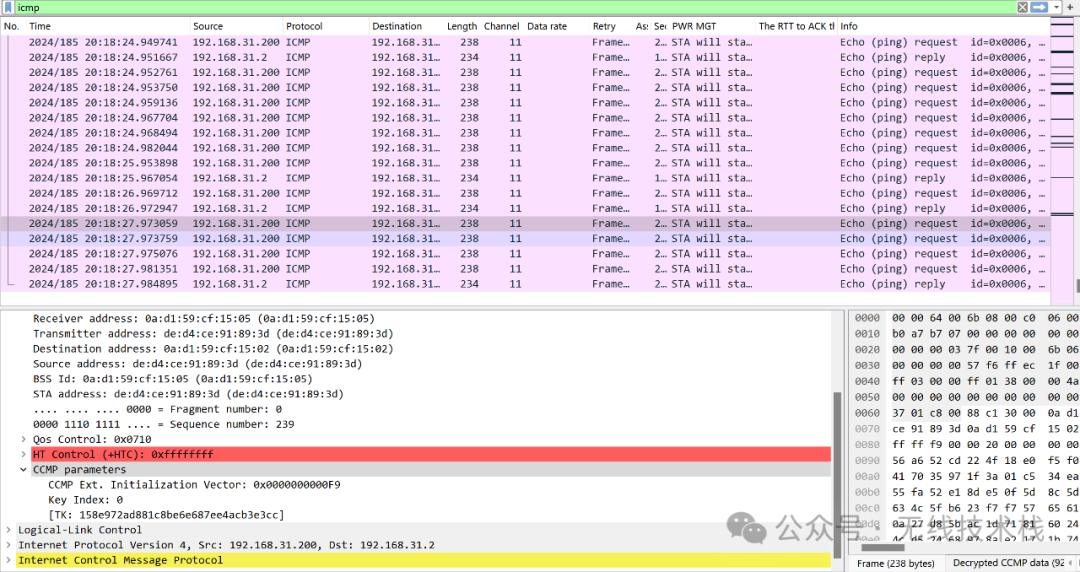
key:158e972ad881c8be6e687ee4acb3e3cc
//加了patch之后wpa_supplicant的打印579094:07-03 20:16:22.254 30968 30968 D wpa_supplicant: wlan0: WPA: Installing PTK to the driver579113:07-03 20:16:22.254 30968 30968 E wpa_supplicant: DEBUG print dump - hexdump(len=16): 15 8e 97 2a d8 81 c8 be 6e 68 7e e4 ac b3 e3 cc579115:07-03 20:16:22.254 30968 30968 D wpa_supplicant: wpa_driver_nl80211_set_key: ifindex=24 (wlan0) alg=3 addr=0xb40000757b1a6d20 key_idx=0 set_tx=1 seq_len=6 key_len=16 key_flag=0x2c link_id=-1 anjss key=ffffffd8579189:07-03 20:16:22.257 30968 30968 D wpa_supplicant: wlan0: WPA: Installing GTK to the driver (keyidx=1 tx=0 len=16)579207:07-03 20:16:22.257 30968 30968 E wpa_supplicant: DEBUG print dump - hexdump(len=16): b5 26 b4 0b fe 19 e0 f4 6c be 9d d7 fb be 2c 02579209:07-03 20:16:22.257 30968 30968 D wpa_supplicant: wpa_driver_nl80211_set_key: ifindex=24 (wlan0) alg=3 addr=0x58dc253e4e key_idx=1 set_tx=0 seq_len=6 key_len=16 key_flag=0x14 link_id=-1 anjss key=cf1ae989579250:07-03 20:16:22.269 30968 30968 D wpa_supplicant: wlan0: WPA: IGTK keyid 4 pn 000000000000579268:07-03 20:16:22.269 30968 30968 E wpa_supplicant: DEBUG print dump - hexdump(len=16): a1 89 66 71 10 e9 9f 05 74 e8 06 31 f9 95 2c 3a579269:07-03 20:16:22.269 30968 30968 D wpa_supplicant: wpa_driver_nl80211_set_key: ifindex=24 (wlan0) alg=4 addr=0x58dc253e4e key_idx=4 set_tx=0 seq_len=6 key_len=16 key_flag=0x14 link_id=-1 anjss key=ffffffd8
在wireshark中添加tk信息:
解密之后的数据:
解密方法落地
key信息是直接关联到安全的关键信息,一般不能直接打印到日志中,这样会增加wifi数据被破解的风险,可以考虑通过一些公钥私钥对这个key信息进行加密,这样即使不法分子拿到这个信息也不好解密,方便在项目进行debug;
如果读到这里,你觉得有所收获,就关注下小编的公众号,未来一起进步~