DNS
DNS(Domain Name System)服务,可以使用域名代替复杂的IP地址来访问网络服务器,使得网络服务的访问更加简单,而且可以完美地实现与Internet的融合,对于一个网站的推广发布起到极其重要的作用。
而且许多重要网络服务(如E-mail服务)的实现,也需要借助于DNS服务。因此,DNS服务可视为网络服务的基础。
DNS是一种采用客户/服务器机制,实现名称与IP地址转换的系统,是由名字分布数据库组成的,它建立了叫做域名空间的逻辑树结构,是负责分配、改写、查询域名的综合性服务系统,该空间中的每个结点或域都有唯一的名字。
一、BIND DNS 服务器
BIND 是一个功能丰富的 DNS 服务器,它完全符合互联网工程任务 Force (IETF) DNS 标准和草案标准。例如,管理员经常使用 BIND,如下所示:
-
在本地网络中缓存 DNS 服务器
-
区域的权威 DNS 服务器
-
二级服务器来为区域提供高可用性
安装 bind 和 bind-utils 软件包
$ yum install bind bind-utils
# 注:这些软件包提供 BIND 9.11。如果您需要 BIND 9.16,请安装 bind9.16 和 bind9.16-utils 软件包。如果要在 change-root 环境中运行 BIND,请安装 bind-chroot 软件包:
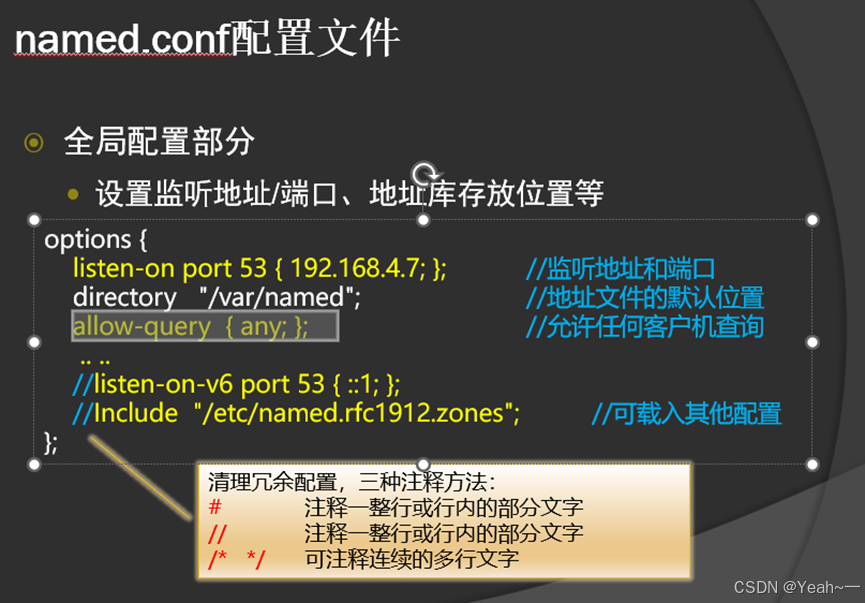
$ yum install bind-chroot主配置文件/etc/named.conf
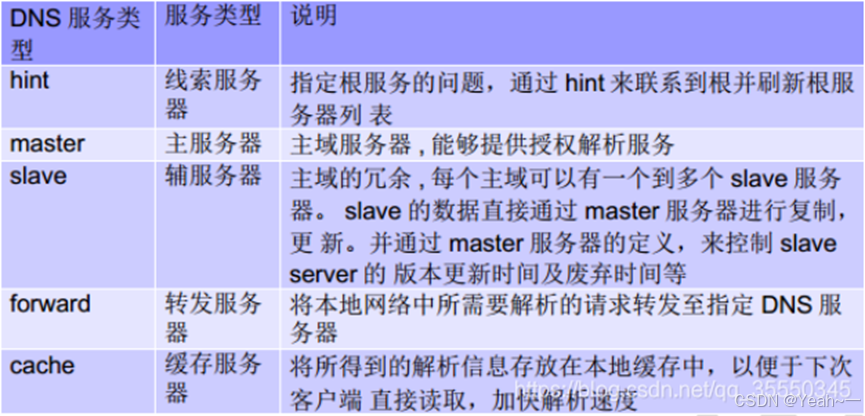
DNS服务类型
地址库文件语法
1.1 配置多区域dns
[root@vm1 ~]# vim /etc/named.conf
[root@vm1 ~]# cat /etc/named.conf
options {
listen-on port 53 { any; };
directory "/var/named";
allow-query { any; };
recursion yes;
};
zone "." IN {
type hint;
file "named.ca";
};
zone "redhat.com" IN {
type master;
file "redhat.com.zone";
};
zone "kunpeng.com" IN {
type master;
file "kunpeng.com.zone";
};
[root@vm1 ~]#
# 配置正向区域文件
[root@vm1 ~]# cp -p /var/named/redhat.com.zone /var/named/kunpeng.com.zone
[root@vm1 ~]# vim /var/named/kunpeng.com.zone
[root@vm1 ~]# cat /var/named/kunpeng.com.zone
$TTL 1D
kunpeng.com. IN SOA vm1.redhat.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
kunpeng.com. NS vm1.redhat.com.
ftp A 2.2.2.2
www A 3.3.3.3
[root@vm1 ~]#检查配置文件有无语法问题
[root@vm1 ~]# named-checkconf /etc/named.conf
[root@vm1 ~]# named-checkzone kunpeng.com /var/named/kunpeng.com.zone
zone kunpeng.com/IN: loaded serial 0
OK
[root@vm1 ~]#重启服务并验证配置
[root@vm1 ~]# systemctl restart named
[root@vm1 ~]# host ftp.kunpeng.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
ftp.kunpeng.com has address 2.2.2.2
[root@vm1 ~]# host www.kunpeng.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
www.kunpeng.com has address 3.3.3.3
[root@vm1 ~]# host www.redhat.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
www.redhat.com has address 1.1.1.1
[root@vm1 ~]#1.2 配置反向域名解析
[root@vm1 ~]# cat /etc/named.conf
options {
listen-on port 53 { any; };
directory "/var/named";
allow-query { any; };
recursion yes;
forwarders { 127.0.0.1; };
forward only;
};
zone "." IN {
type hint;
file "named.ca";
};
zone "redhat.com" IN {
type master;
file "redhat.com.zone";
};
zone "kunpeng.com" IN {
type master;
file "kunpeng.com.zone";
};
zone "1.1.1.in-addr.arpa" {
type master;
file "1.1.1.in-addr.arpa.zone";
};
[root@vm1 ~]# named-checkconf /etc/named.conf配置反向区域文件
[root@vm1 ~]# cp -p /var/named/redhat.com.zone /var/named/1.1.1.in-addr.arpa.zone
[root@vm1 ~]# vim /var/named/1.1.1.in-addr.arpa.zone
[root@vm1 ~]# cat /var/named/1.1.1.in-addr.arpa.zone
$TTL 1D
@ IN SOA vm1.redhat.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
IN NS vm1.redhat.com.
1 IN PTR www.redhat.com.
[root@vm1 ~]#重启服务测试
[root@vm1 ~]# systemctl restart named
[root@vm1 ~]# host 1.1.1.1
1.1.1.1.in-addr.arpa domain name pointer www.redhat.com.
[root@vm1 ~]# 1.3 DNS轮询
一个域名对应多个IP
[root@vm1 ~]# vim /var/named/a.com.zone
[root@vm1 ~]# cat /var/named/a.com.zone
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 192.168.1.1
www A 192.168.1.2
www A 192.168.1.3
[root@vm1 ~]#重启服务验证
[root@vm1 ~]# systemctl restart named
[root@vm1 ~]# host www.a.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
www.a.com has address 192.168.1.3
www.a.com has address 192.168.1.1
www.a.com has address 192.168.1.2
[root@vm1 ~]#
# 需要多ping几次看轮询效果:
[root@vm1 ~]# ping -c 1 www.a.com
PING www.a.com (192.168.1.3) 56(84) bytes of data.
^C
--- www.a.com ping statistics ---
1 packets transmitted, 0 received, 100% packet loss, time 0ms
[root@vm1 ~]#
[root@vm1 ~]# ping -c 1 www.a.com
PING www.a.com (192.168.1.2) 56(84) bytes of data.
^C
--- www.a.com ping statistics ---
1 packets transmitted, 0 received, 100% packet loss, time 0ms
[root@vm1 ~]#
[root@vm1 ~]# ping -c 1 www.a.com
PING www.a.com (192.168.1.1) 56(84) bytes of data.
^C
--- www.a.com ping statistics ---
1 packets transmitted, 0 received, 100% packet loss, time 0ms
[root@vm1 ~]#1.4 泛域名解析
匹配本域内未定义的任何主机地址
直接以*条目匹配,一般用于正向解析
[root@vm1 ~]# cat /var/named/a.com.zone
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 192.168.1.1
ftp A 192.168.1.2
* A 192.168.1.3
[root@vm1 ~]#重启服务验证
[root@vm1 ~]# systemctl restart named
[root@vm1 ~]# host www.a.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
www.a.com has address 192.168.1.1
[root@vm1 ~]# host ftp.a.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
ftp.a.com has address 192.168.1.2
[root@vm1 ~]# host abc.a.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
abc.a.com has address 192.168.1.3
[root@vm1 ~]# host wwww.a.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
wwww.a.com has address 192.168.1.3
[root@vm1 ~]#有规律的泛域名解析:$GENERATE 造数工具
stu1.a.com -------> 192.168.1.1
····················
stu5.a.com -------> 192.168.1.5
[root@vm1 ~]# vim /var/named/a.com.zone
[root@vm1 ~]# cat /var/named/a.com.zone
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
vm1 A 192.168.99.100
$GENERATE 1-5 stu$ A 192.168.1.$
[root@vm1 ~]# 重启服务验证
[root@vm1 ~]# systemctl restart named
[root@vm1 ~]# for i in {1..5}
> do
> host stu${i}.a.com 192.168.99.100
> echo +++++++++++++++++++++++++++++++++
> done
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
stu1.a.com has address 192.168.1.1
+++++++++++++++++++++++++++++++++
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
stu2.a.com has address 192.168.1.2
+++++++++++++++++++++++++++++++++
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
stu3.a.com has address 192.168.1.3
+++++++++++++++++++++++++++++++++
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
stu4.a.com has address 192.168.1.4
+++++++++++++++++++++++++++++++++
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
stu5.a.com has address 192.168.1.5
+++++++++++++++++++++++++++++++++
[root@vm1 ~]#1.5 子域授权
子域授权的作用:
适用于同一个DNS组织
父/子域的解析工作由不同的DNS服务器负责
父DNS服务器应该有为子域迭代的能力
实验:准备两台虚拟机,vm1(192.168.99.100);vm2(192.168.99.129)。并且都安装了bind、bind-chroot。
[root@vm1 ~]# hostname
vm1.a.com
[root@vm1 ~]# yum install -y bind bind-chroot
[root@vm2 ~]# hostname
vm2.tj.a.com
[root@vm2 ~]# yum install -y bind bind-chroot实验效果:客户要解析www.tj.a.com的ip地址,dns服务器设置为vm1,vm1向vm2获取解析记录并返回给客户,此时客户收到的响应为非权威解答。
实验过程
[root@vm1 ~]# cat /etc/resolv.conf # 指定本机为dns服务器
# Generated by NetworkManager
search a.com
nameserver 192.168.99.100
# 修改vm1的主配置文件
[root@vm1 ~]# vim /etc/named.conf
[root@vm1 ~]# cat /etc/named.conf
options {
listen-on port 53 { any; };
directory "/var/named";
allow-query { any; };
recursion yes;
};
zone "." IN {
type hint;
file "named.ca";
};
zone "a.com" IN {
type master;
file "a.com.zone";
};
# 配置vm1的区域文件
[root@vm1 ~]# cat /var/named/a.com.zone
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
tj.a.com. NS vm2.tj.a.com.
vm2.tj.a.com. A 192.168.99.129
vm1 A 192.168.99.100
www A 1.1.1.1
[root@vm1 ~]# systemctl restart named
[root@vm1 ~]# host vm2.tj.a.com
vm2.tj.a.com has address 192.168.99.129
[root@vm1 ~]#
# 修改vm2的主配置文件
[root@vm2 ~]# cat /etc/named.conf
options {
listen-on port 53 { any; };
directory "/var/named";
allow-query { any; };
recursion yes;
};
zone "." IN {
type hint;
file "named.ca";
};
zone "tj.a.com" IN {
type master;
file "tj.a.com.zone";
};
# 配置vm2的区域文件
[root@vm2 ~]# cat /var/named/tj.a.com.zone
$TTL 1D
@ IN SOA vm2.tj.a.com root.localhost.localdomain (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
tj.a.com. NS vm2.tj.a.com.
vm2 A 192.168.99.129
www A 2.2.2.2
[root@vm2 ~]# systemctl restart named
[root@vm2 ~]# host www.tj.a.com 192.168.99.129
Using domain server:
Name: 192.168.99.129
Address: 192.168.99.129#53
Aliases:
www.tj.a.com has address 2.2.2.2
[root@vm2 ~]# host vm2.tj.a.com 192.168.99.129
Using domain server:
Name: 192.168.99.129
Address: 192.168.99.129#53
Aliases:
vm2.tj.a.com has address 192.168.99.129
[root@vm2 ~]#测试子域授权
[root@vm1 ~]# host www.tj.a.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
www.tj.a.com has address 2.2.2.2
[root@vm1 ~]#
[root@vm1 ~]# nslookup www.a.com 192.168.99.100
Server: 192.168.99.100
Address: 192.168.99.100#53
Name: www.a.com
Address: 1.1.1.1
[root@vm1 ~]#
[root@vm1 ~]# nslookup www.tj.a.com 192.168.99.100
Server: 192.168.99.100
Address: 192.168.99.100#53
Non-authoritative answer: 非权威解答
Name: www.tj.a.com
Address: 2.2.2.2
[root@vm1 ~]#1.6 递归与迭代
递归查询是默认开启的,也可以设置 recursion yes; 来明确启用
若要禁止递归,需要设置 recursion no;
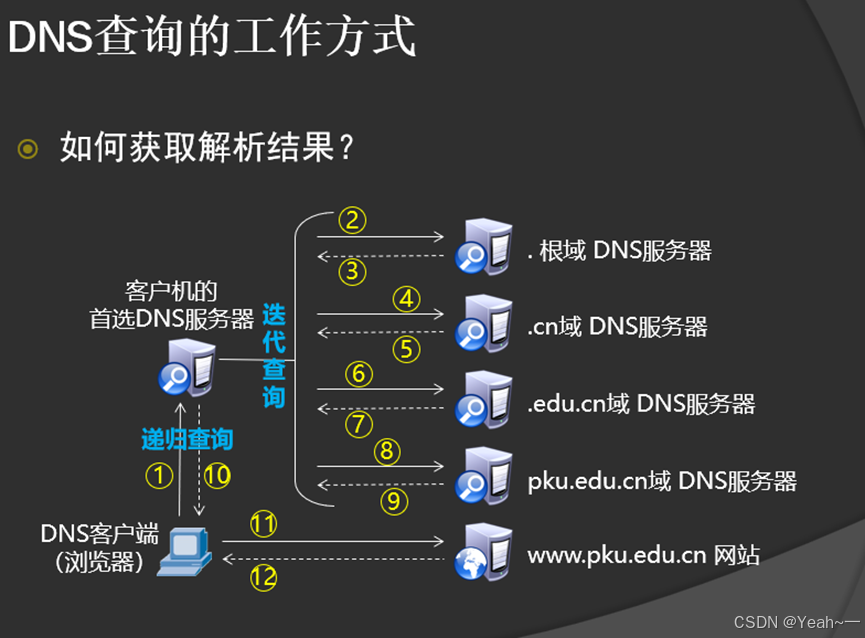
DNS递归解析基本流程:
在这个查询过程中,一直是以本地名称服务器(Local DNS)为中心的,DNS客户端只是发出原始的域名查询请求报文,然后就一直处于等待状态的,直到本地名称服务器发来了最终的查询结果。此时的本地名称服务器就相当于中介代理的作用。如果考虑了本地名称服务器的缓存技术(也就是在DNS服务器上对一定数量的以前查询记录保存一定时间,这样后面查询同样的域名信息时就可直接从缓存中调出来,以加速查询效率)的话,则递归解析的基本流程如下:
-
客户端向本机配置的本地名称服务器(在此仅以首选DNS服务器为例进行介绍,所配置其它备用DNS服务器的解析流程完全一样)发出DNS域名查询请求。
-
本地名称服务器收到请求后,先查询本地的缓存,如果有该域名的记录项,则本地名称服务器就直接把查询的结果返回给客户端;如果本地缓存中没有该域名的记录,则本地名称服务器再以DNS客户端的角色发送与前面一样的DNS域名查询请求发给根名称服务器。
-
根名称服务器收到DNS请求后,把所查询得到的所请求的DNS域名中顶级域名所对应的顶级名称服务器地址返回给本地名称服务器。
-
本地名称服务器根据根名称服务器所返回的顶级名称服务器地址,向对应的顶级名称服务器发送与前面一样的DNS域名查询请求。
-
对应的顶级名称服务器在收到DNS查询请求后,也是先查询自己的缓存,如果有所请求的DNS域名的记录项,则相接把对应的记录项返回给本地名称服务器,然后再由本地名称服务器返回给DNS客户端,否则向本地名称服务器返回所请求的DNS域名中的二级域名所对应的二级名称服务器地址。
-
然后本地名称服务器继续按照前面介绍的方法一次次地向三级、四级名称服务器查询,直到最终的对应域名所在区域的权威名称服务器返回到最终的记录给本地名称服务器。然后再由本地名称服务器返回给DNS客户,同时本地名称服务器会缓存本次查询得到的记录项。
递归查询和迭代查询的区别
-
DNS客户端和本地名称服务器是递归,而本地名称服务器和其他名称服务器之间是迭代。
-
DNS递归名称解析:在DNS递归名称解析中,当所配置的本地名称服务器解析不了时,后面的查询工作是由本地名称服务器替代DNS客户端进行的(以本地名称服务器为中心),只需要本地名称服务器向DNS客户端返回最终的查询结果即可。
-
DNS迭代名称解析:(或者叫迭代查询)的所有查询工作全部是DNS客户端自己进行(以DNS客户端自己为中心)。在条件之一满足时就会采用迭代名称解析方式:
-
在查询本地名称服务器时,如果客户端的请求报文中没有申请使用递归查询,即在DNS请求报头部的RD字段没有置1。相当于说”你都没有主动要求我为你进行递归查询,我当然不会为你工作了”
-
客户端在DNS请求报文中申请使用的是递归查询(也就是RD字段置1了),但在所配置的本地名称服务器上是禁用递归查询(DNS服务器一般默认支持递归查询的),即在应答DNS报文头部的RA字段置0
-
1.7 缓存dns
缓存DNS不需要管理任何DNS区域,但是能够替客户机查询,而且通过缓存、复用查询结果来加快速度。
适用环境:
-
互联网出口带宽较低的企业局域网络
-
ISP服务商的公共DNS服务器
解析记录来源:
-
方式一:全局转发
-
将请求转发给指定的公共DNS(其他缓存DNS),请求递归服务
-
-
方式二:根域迭代
-
依次向根、一级、二级.........域的DNS服务器迭代
-
实验:配置全局转发
[root@vm2 ~]# vim /etc/named.conf
[root@vm2 ~]# cat /etc/named.conf
options {
listen-on port 53 { any; };
directory "/var/named";
allow-query { any; };
recursion yes;
forwarders { 114.114.114.114; 8.8.8.8; };
};
zone "." IN {
type hint;
file "named.ca";
};
#zone "tj.a.com" IN {
# type master;
# file "tj.a.com.zone";
#};
# 重启服务验证
[root@vm2 ~]# systemctl restart named
[root@vm2 ~]# nslookup www.baidu.com 192.168.99.129
Server: 192.168.99.129
Address: 192.168.99.129#53
Non-authoritative answer:
www.baidu.com canonical name = www.a.shifen.com.
Name: www.a.shifen.com
Address: 110.242.68.4
Name: www.a.shifen.com
Address: 110.242.68.3
Name: www.a.shifen.com
Address: 2408:871a:2100:2:0:ff:b09f:237
Name: www.a.shifen.com
Address: 2408:871a:2100:3:0:ff:b025:348d
[root@vm2 ~]#1.8 DNS分离解析
什么是分离解析
当收到客户机的DNS查询请求的时候
能够区分客户机的来源地址
为不同类别的客户机提供不同的解析结果(IP地址)
根据客户端的不同,解析同一个域名,得到的解析结果不同
目的:为客户端提供网络最近的服务器资源
实验:
解析www.a.com:
vm1:192.168.99.100解析结果为1.1.1.1
vm2: 192.168.99.129 解析结果为2.2.2.2
windows: 作为其他主机,解析结果为3.3.3.3
通过视图实现:view
-
由上到下依次匹配, 匹配及停止
-
使用view时,所有的客户端都必须在分类中
-
所有的zone都必须在view中
-
每一个view中的zone必须相同
[root@vm1 ~]# cat /etc/named.conf
options {
listen-on port 53 { any; };
directory "/var/named";
allow-query { any; };
recursion yes;
};
view "tj" {
match-clients { 192.168.99.100; };
zone "." IN {
type hint;
file "named.ca";
};
zone "a.com" IN {
type master;
file "a.com.zone.tj";
};
};
view "bj" {
match-clients { 192.168.99.129; };
zone "." IN {
type hint;
file "named.ca";
};
zone "a.com" IN {
type master;
file "a.com.zone.bj";
};
};
view "other" {
match-clients { any; };
zone "." IN {
type hint;
file "named.ca";
};
zone "a.com" IN {
type master;
file "a.com.zone.other";
};
};
[root@vm1 ~]# named-checkconf /etc/named.conf
[root@vm1 ~]# cp -p /var/named/a.com.zone /var/named/a.com.zone.tj
[root@vm1 ~]# cp -p /var/named/a.com.zone /var/named/a.com.zone.bj
[root@vm1 ~]# cp -p /var/named/a.com.zone /var/named/a.com.zone.other
[root@vm1 ~]# cat /var/named/a.com.zone.tj
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 1.1.1.1
[root@vm1 ~]# vim /var/named/a.com.zone.bj
[root@vm1 ~]# cat /var/named/a.com.zone.bj
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 2.2.2.2
[root@vm1 ~]#
[root@vm1 ~]# vim /var/named/a.com.zone.other
[root@vm1 ~]# cat /var/named/a.com.zone.other
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 3.3.3.3
[root@vm1 ~]# named-checkzone a.com /var/named/a.com.zone.tj
zone a.com/IN: loaded serial 0
OK
[root@vm1 ~]# named-checkzone a.com /var/named/a.com.zone.bj
zone a.com/IN: loaded serial 0
OK
[root@vm1 ~]# named-checkzone a.com /var/named/a.com.zone.other
zone a.com/IN: loaded serial 0
OK
[root@vm1 ~]#重启验证
[root@vm1 ~]# systemctl restart named
[root@vm1 ~]# nslookup www.a.com 192.168.99.100
Server: 192.168.99.100
Address: 192.168.99.100#53
Name: www.a.com
Address: 1.1.1.1
[root@vm1 ~]#
[root@vm2 ~]# nslookup www.a.com 192.168.99.100
Server: 192.168.99.100
Address: 192.168.99.100#53
Name: www.a.com
Address: 2.2.2.2
[root@vm2 ~]#
# Windows测试:
PS C:\Users\hehe> nslookup www.a.com 192.168.99.100
服务器: UnKnown
Address: 192.168.99.100
名称: www.a.com
Address: 3.3.3.3
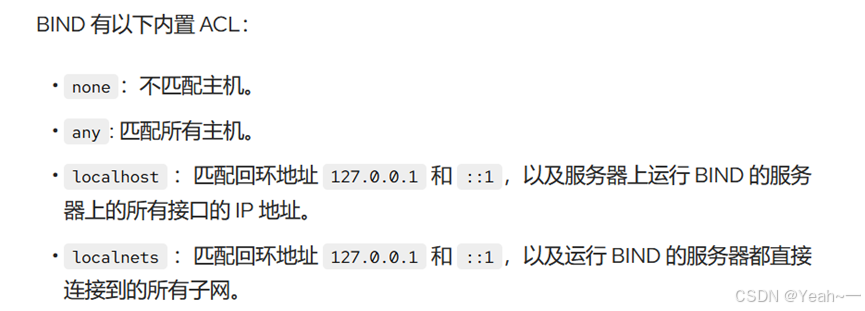
PS C:\Users\hehe>ACL
练习
现在有三个区域:和平、西青、滨海
有两个zone:a.com和b.com
-
www.a.com:分别解析为11.11.11.11,22.22.22.22,33.33.33.33
-
www.b.com:分别解析为11.11.11.12,22.22.22.23,33.33.33.34
和平区包含vm1的所有网卡ip(192.x.x.x,127.0.0.1,192.168.122.1)
西青区包含vm2的所有网卡ip(192.x.x.x,172.16.16.100)
滨海区包含所有其他ip
所有被匹配的ip,使用ACL的形式表示
[root@vm1 ~]# cat /etc/named.conf
options {
listen-on port 53 { any; };
directory "/var/named";
allow-query { any; };
recursion yes;
};
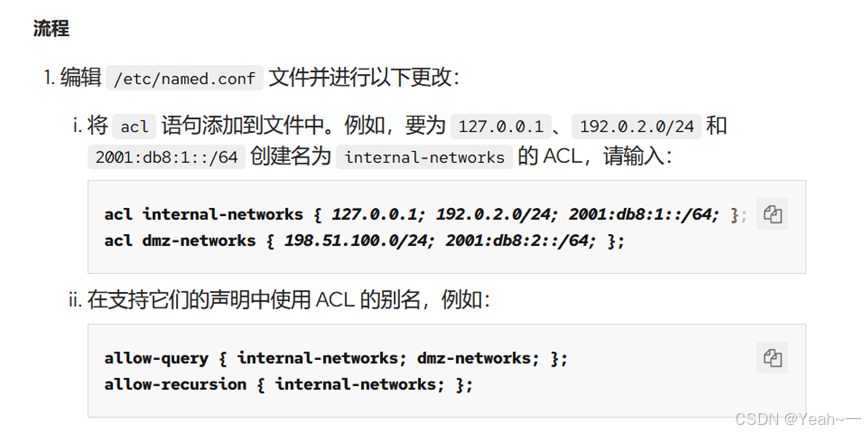
acl hp-net { 192.168.99.100;192.168.122.1;127.0.0.1; };
acl xq-net { 192.168.99.129;172.16.16.100; };
view "hp" {
match-clients { hp-net; };
zone "." IN {
type hint;
file "named.ca";
};
zone "a.com" IN {
type master;
file "a.com.zone.hp";
};
zone "b.com" IN {
type master;
file "b.com.zone.hp";
};
};
view "xq" {
match-clients { xq-net; };
zone "." IN {
type hint;
file "named.ca";
};
zone "a.com" IN {
type master;
file "a.com.zone.xq";
};
zone "b.com" IN {
type master;
file "b.com.zone.xq";
};
};
view "bh" {
match-clients { any; };
zone "." IN {
type hint;
file "named.ca";
};
zone "a.com" IN {
type master;
file "a.com.zone.bh";
};
zone "b.com" IN {
type master;
file "b.com.zone.bh";
};
};
[root@vm1 ~]# named-checkconf /etc/named.conf
[root@vm1 ~]# cp -p /var/named/a.com.zone.tj /var/named/a.com.zone.hp
[root@vm1 ~]# cp -p /var/named/a.com.zone.tj /var/named/a.com.zone.xq
[root@vm1 ~]# cp -p /var/named/a.com.zone.tj /var/named/a.com.zone.bh
[root@vm1 ~]# cp -p /var/named/a.com.zone.tj /var/named/b.com.zone.bh
[root@vm1 ~]# cp -p /var/named/a.com.zone.tj /var/named/b.com.zone.xq
[root@vm1 ~]# cp -p /var/named/a.com.zone.tj /var/named/b.com.zone.hp
[root@vm1 ~]# cat /var/named/a.com.zone.hp
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 11.11.11.11
[root@vm1 ~]# cat /var/named/a.com.zone.xq
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 22.22.22.22
[root@vm1 ~]# cat /var/named/a.com.zone.bh
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 33.33.33.33
[root@vm1 ~]# cat /var/named/b.com.zone.hp
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
b.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 11.11.11.12
[root@vm1 ~]# cat /var/named/b.com.zone.xq
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
b.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 22.22.22.23
[root@vm1 ~]# cat /var/named/b.com.zone.bh
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
b.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 33.33.33.34
[root@vm1 ~]# named-checkzone a.com /var/named/a.com.zone.hp
zone a.com/IN: loaded serial 0
OK
[root@vm1 ~]# named-checkzone a.com /var/named/a.com.zone.xq
zone a.com/IN: loaded serial 0
OK
[root@vm1 ~]# named-checkzone a.com /var/named/a.com.zone.bh
zone a.com/IN: loaded serial 0
OK
[root@vm1 ~]#
[root@vm1 ~]# named-checkzone b.com /var/named/b.com.zone.hp
zone b.com/IN: loaded serial 0
OK
[root@vm1 ~]# named-checkzone b.com /var/named/b.com.zone.xq
zone b.com/IN: loaded serial 0
OK
[root@vm1 ~]# named-checkzone b.com /var/named/b.com.zone.bh
zone b.com/IN: loaded serial 0
OK
[root@vm1 ~]#重启验证
[root@vm1 ~]# systemctl restart named
[root@vm1 ~]# nslookup www.a.com 192.168.99.100
Server: 192.168.99.100
Address: 192.168.99.100#53
Name: www.a.com
Address: 11.11.11.11
[root@vm1 ~]# nslookup www.b.com 192.168.99.100
Server: 192.168.99.100
Address: 192.168.99.100#53
Name: www.b.com
Address: 11.11.11.12
[root@vm1 ~]#
[root@vm2 ~]# nslookup www.a.com 192.168.99.100
Server: 192.168.99.100
Address: 192.168.99.100#53
Name: www.a.com
Address: 22.22.22.22
[root@vm2 ~]# nslookup www.b.com 192.168.99.100
Server: 192.168.99.100
Address: 192.168.99.100#53
Name: www.b.com
Address: 22.22.22.23
[root@vm2 ~]#
# Windows测试:
PS C:\Users\hehe> nslookup www.a.com 192.168.99.100
服务器: UnKnown
Address: 192.168.99.100
名称: www.a.com
Address: 33.33.33.33
PS C:\Users\hehe> nslookup www.b.com 192.168.99.100
服务器: UnKnown
Address: 192.168.99.100
名称: www.b.com
Address: 33.33.33.34
PS C:\Users\hehe>1.9 DNS主从
作为重要的互联网基础设施服务,保证DNS域名解析服务的正常运转至关重要,只有这样才能提供稳定、快速且不间断的域名查询服务。在DNS域名解析服务中,从服务器可以从主服务器上获取指定的区域数据文件,从而起到备份解析记录与负载均衡的作用。因此,通过部署从服务器不仅可以减轻主服务器的负载压力,还可以提升用户的查询效率。
# vm1:主(192.168.99.100) vm2:从(192.168.99.129)
[root@vm1 ~]# cat /etc/named.conf
options {
listen-on port 53 { any; };
directory "/var/named";
allow-query { any; };
recursion yes;
};
zone "." IN {
type hint;
file "named.ca";
};
zone "a.com" IN {
type master;
file "a.com.zone";
allow-update { 192.168.99.129;};
};
[root@vm1 ~]# named-checkconf /etc/named.conf
[root@vm1 ~]# cat /var/named/a.com.zone
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 1.1.1.1
[root@vm1 ~]# named-checkzone a.com /var/named/a.com.zone
zone a.com/IN: loaded serial 0
OK
[root@vm1 ~]# systemctl restart named
[root@vm1 ~]# host www.a.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
www.a.com has address 1.1.1.1
[root@vm1 ~]#
# vm2中配置
[root@vm2 ~]# cat /etc/named.conf
options {
listen-on port 53 { any; };
directory "/var/named";
allow-query { any; };
recursion yes;
};
zone "." IN {
type hint;
file "named.ca";
};
zone "a.com" IN {
type slave;
masters { 192.168.99.100; };
file "slaves/a.com.zone.slave";
};
[root@vm2 ~]# named-checkconf /etc/named.conf
[root@vm2 ~]# systemctl restart named
# 注:slaves目录自动创建,区域文件自动同步
[root@vm2 ~]# ll /var/named/slaves/
total 4
-rw-r--r--. 1 named named 232 Apr 24 11:19 a.com.zone.slave
[root@vm2 ~]# ll /var/named/slaves/ -d
drwxrwx---. 2 named named 30 Apr 24 11:19 /var/named/slaves/
[root@vm2 ~]# cat /var/named/slaves/a.com.zone.slave 输出略,非正常文本
[root@vm1 ~]# host www.a.com 192.168.99.129
Using domain server:
Name: 192.168.99.129
Address: 192.168.99.129#53
Aliases:
www.a.com has address 1.1.1.1
[root@vm1 ~]#配置防火墙和selinux,放行相应服务、端口
[root@vm1 ~]# setenforce 1
[root@vm1 ~]# firewall-cmd --set-default-zone=public
success
[root@vm1 ~]# firewall-cmd --add-port=53/tcp
success
[root@vm1 ~]# firewall-cmd --add-port=53/udp
success
[root@vm1 ~]# firewall-cmd --add-port=53/udp --permanent
success
[root@vm1 ~]# firewall-cmd --add-port=53/tcp --permanent
success
[root@vm1 ~]#
[root@vm2 ~]# setenforce 1
[root@vm2 ~]# firewall-cmd --set-default-zone=public
success
[root@vm2 ~]# firewall-cmd --add-port=53/tcp
success
[root@vm2 ~]# firewall-cmd --add-port=53/udp
success
[root@vm2 ~]# firewall-cmd --add-port=53/udp --permanent
success
[root@vm2 ~]# firewall-cmd --add-port=53/tcp --permanent
success
[root@vm2 ~]#验证
[root@vm1 ~]# host www.a.com 192.168.99.129
Using domain server:
Name: 192.168.99.129
Address: 192.168.99.129#53
Aliases:
www.a.com has address 1.1.1.1
[root@vm1 ~]#
[root@vm2 ~]# host www.a.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
www.a.com has address 1.1.1.1
[root@vm2 ~]#1.10 bind-chroot
在 change-root 环境中运行 named-chroot 服务
-
利用 change-root 功能,管理员可以定义进程的根目录及其子进程与
/目录不同。当您启动named-chroot服务时,BIND 将其根目录切换到/var/named/chroot/。因此,服务使用mount --bind命令使/etc/named-chroot.files中列出的文件和目录保存在/var/named/chroot/中,并且进程无法访问/var/named/chroot/以外的文件。
[root@vm1 ~]# systemctl stop named
[root@vm1 ~]# ps aux | grep named
root 7463 0.0 0.0 221940 1140 pts/0 S+ 11:32 0:00 grep --color=auto named
[root@vm1 ~]# ls /var/named/chroot/
dev etc proc run usr var
[root@vm1 ~]# ls /var/named/chroot/etc/
crypto-policies named pki
[root@vm1 ~]# ls /var/named/chroot/var/
log named run tmp
[root@vm1 ~]# ls /var/named/chroot/var/named/
[root@vm1 ~]# cp -p /etc/named.conf /var/named/chroot/etc/named.conf
[root@vm1 ~]# cat /var/named/chroot/etc/named.conf
options {
listen-on port 53 { any; };
directory "/var/named"; #(此时的根是/var/named/chroot)
allow-query { any; };
recursion yes;
};
zone "." IN {
type hint;
file "named.ca";
};
zone "a.com" IN {
type master;
file "a.com.zone";
};
[root@vm1 ~]#
[root@vm1 ~]# cp -p /var/named/a.com.zone /var/named/chroot/var/named/a.com.zone
[root@vm1 ~]# cp -p /var/named/named.ca /var/named/chroot/var/named/named.ca
[root@vm1 ~]# vim /var/named/chroot/var/named/a.com.zone
[root@vm1 ~]# cat /var/named/chroot/var/named/a.com.zone
$TTL 1D
@ IN SOA vm1.a.com root.localhost.localdomain. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
a.com. NS vm1.a.com.
vm1 A 192.168.99.100
www A 1.1.1.11
[root@vm1 ~]#
# 验证:
[root@vm1 ~]# systemctl restart named-chroot
[root@vm1 ~]# host www.a.com 192.168.99.100
Using domain server:
Name: 192.168.99.100
Address: 192.168.99.100#53
Aliases:
www.a.com has address 1.1.1.11
[root@vm1 ~]#二、unbound DNS服务器
unbound DNS 服务器是一个验证、递归并进行缓存的 DNS 解析器。此外,unbound 侧重于安全性,例如,它会默认启用域名系统安全扩展 (DNSSEC)。
2.1 将 Unbound 配置为缓存 DNS 服务器
清理之前的实验环境,并安装unbound包
[root@vm1 ~]# systemctl stop named
[root@vm1 ~]# systemctl stop named-chroot
[root@vm1 ~]# yum -y install unbound编辑 /etc/unbound/unbound.conf 文件,并在 server 子句中进行以下更改
# 添加 interface 参数来配置 unbound 服务侦听查询的 IP 地址
[root@vm1 ~]# cat /etc/unbound/unbound.conf | grep 192.168.99
interface: 192.168.99.100
access-control: 192.168.99.0/24 allow
[root@vm1 ~]#创建用于远程管理 unbound 服务的私钥和证书
[root@vm1 ~]# systemctl restart unbound-keygen
[root@vm1 ~]# unbound-checkconf #检查配置文件语法
unbound-checkconf: no errors in /etc/unbound/unbound.conf
[root@vm1 ~]#放行防火墙规则并启动服务验证
[root@vm1 ~]# firewall-cmd --permanent --add-service=dns
success
[root@vm1 ~]# firewall-cmd --reload
success
[root@vm1 ~]# systemctl start unbound
[root@vm1 ~]# dig @192.168.99.100 www.redhat.com
; <<>> DiG 9.11.36-RedHat-9.11.36-13.el8 <<>> @192.168.99.100 www.redhat.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 28263
;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;www.redhat.com. IN A
;; ANSWER SECTION:
www.redhat.com. 3598 IN CNAME ds-www.redhat.com.edgekey.net.
ds-www.redhat.com.edgekey.net. 21599 IN CNAME ds-www.redhat.com.edgekey.net.globalredir.akadns.net.
ds-www.redhat.com.edgekey.net.globalredir.akadns.net. 3600 IN CNAME e3396.ca2.s.tl88.net.
e3396.ca2.s.tl88.net. 20 IN A 222.138.4.220
;; Query time: 2866 msec #########第一次查询时间长
;; SERVER: 192.168.99.100#53(192.168.99.100)
;; WHEN: Wed Apr 24 16:38:19 CST 2024
;; MSG SIZE rcvd: 196
[root@vm1 ~]# dig @192.168.99.100 www.redhat.com
; <<>> DiG 9.11.36-RedHat-9.11.36-13.el8 <<>> @192.168.99.100 www.redhat.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 1620
;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;www.redhat.com. IN A
;; ANSWER SECTION:
www.redhat.com. 3580 IN CNAME ds-www.redhat.com.edgekey.net.
ds-www.redhat.com.edgekey.net. 21581 IN CNAME ds-www.redhat.com.edgekey.net.globalredir.akadns.net.
ds-www.redhat.com.edgekey.net.globalredir.akadns.net. 3582 IN CNAME e3396.ca2.s.tl88.net.
e3396.ca2.s.tl88.net. 2 IN A 222.138.4.220
;; Query time: 0 msec ########第二次有缓存,时间短
;; SERVER: 192.168.99.100#53(192.168.99.100)
;; WHEN: Wed Apr 24 16:38:37 CST 2024
;; MSG SIZE rcvd: 196
[root@vm1 ~]#附
CDN 内容分发网络
CDN的全称是Content Delivery Network,即内容分发网络。其基本思路是尽可能避开互联网上有可能影响数据传输速度和稳定性的瓶颈和环节,使内容传输得更快、更稳定。通过在网络各处放置节点服务器所构成的在现有的互联网基础之上的一层智能虚拟网络,CDN系统能够实时地根据网络流量和各节点的连接、负载状况以及到用户的距离和响应时间等综合信息将用户的请求重新导向离用户最近的服务节点上。其目的是使用户可就近取得所需内容,解决 Internet网络拥挤的状况,提高用户访问网站的响应速度。
根服务器
根服务器主要用来管理互联网的主目录,全世界只有13台(这13台根域名服务器名字分别为“A”至“M”),1个为主根服务器在美国。其余12个均为辅根服务器,其中9个在美国,欧洲2个,位于英国和瑞典,亚洲1个位于日本。
ipv6的主根服务器一共有3台,分别设立在了三个国家,分别是中国、美国和日本。中国一共部署了4台ipv6根服务器,其中1台主根、3台辅根。中国四台IPV6根服务器,主机在北京,三副分别在上海、成都和广州。