有道翻译
Part01:加密解析
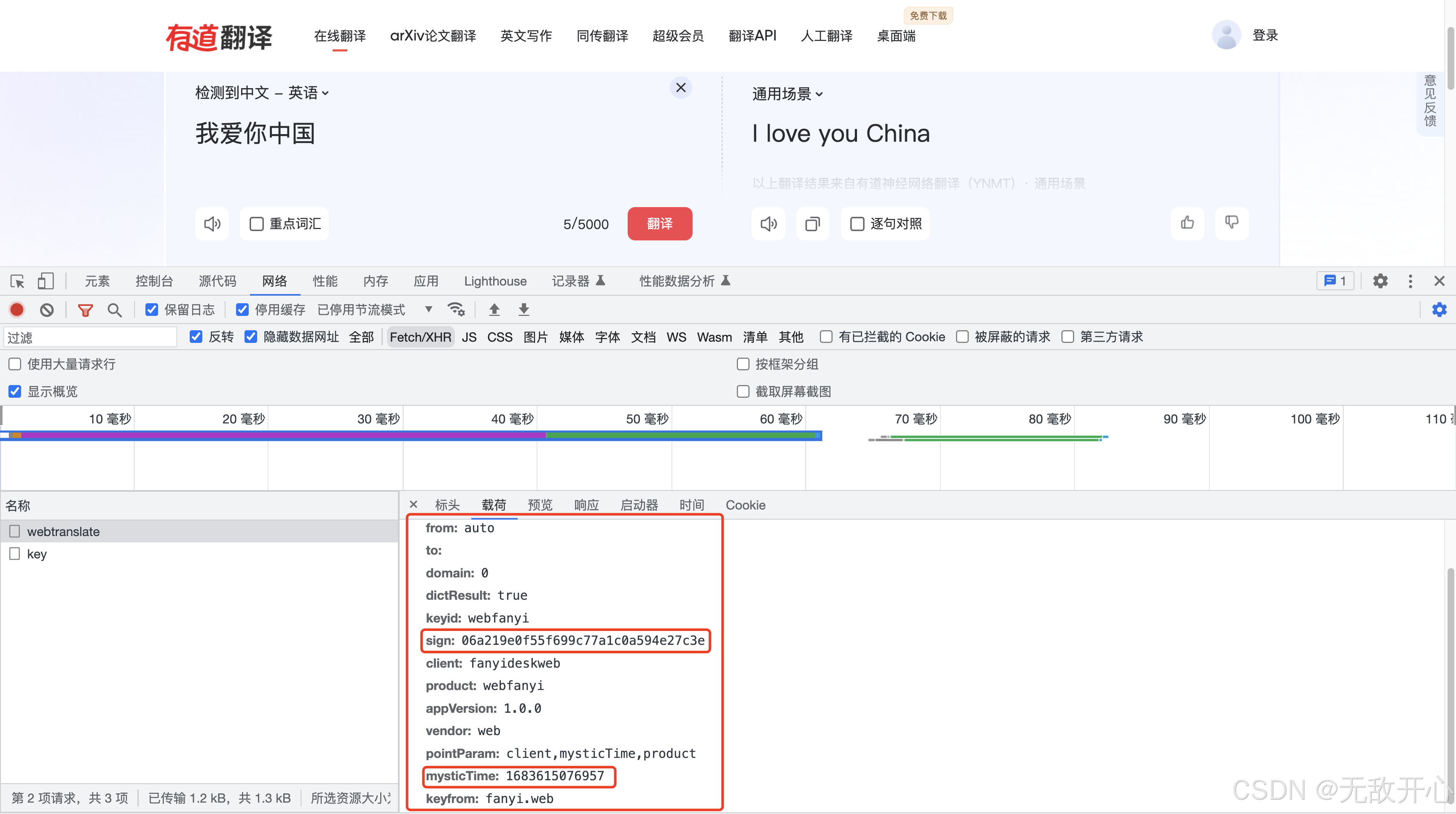
(1)抓包解析
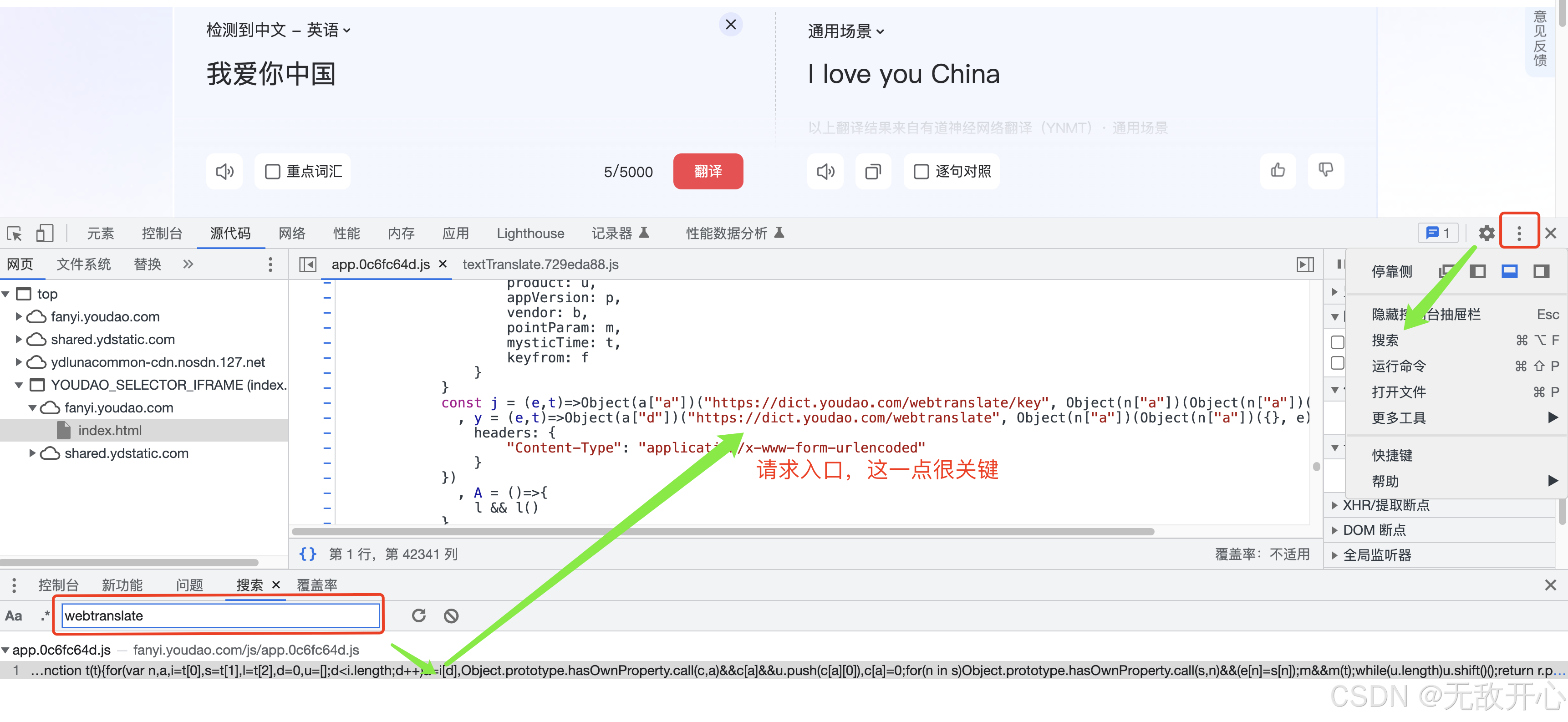
(2)定位JS的请求入口
获取请求入口:搜索关键字,比如sign(有时候太多不好用),比如请求路径
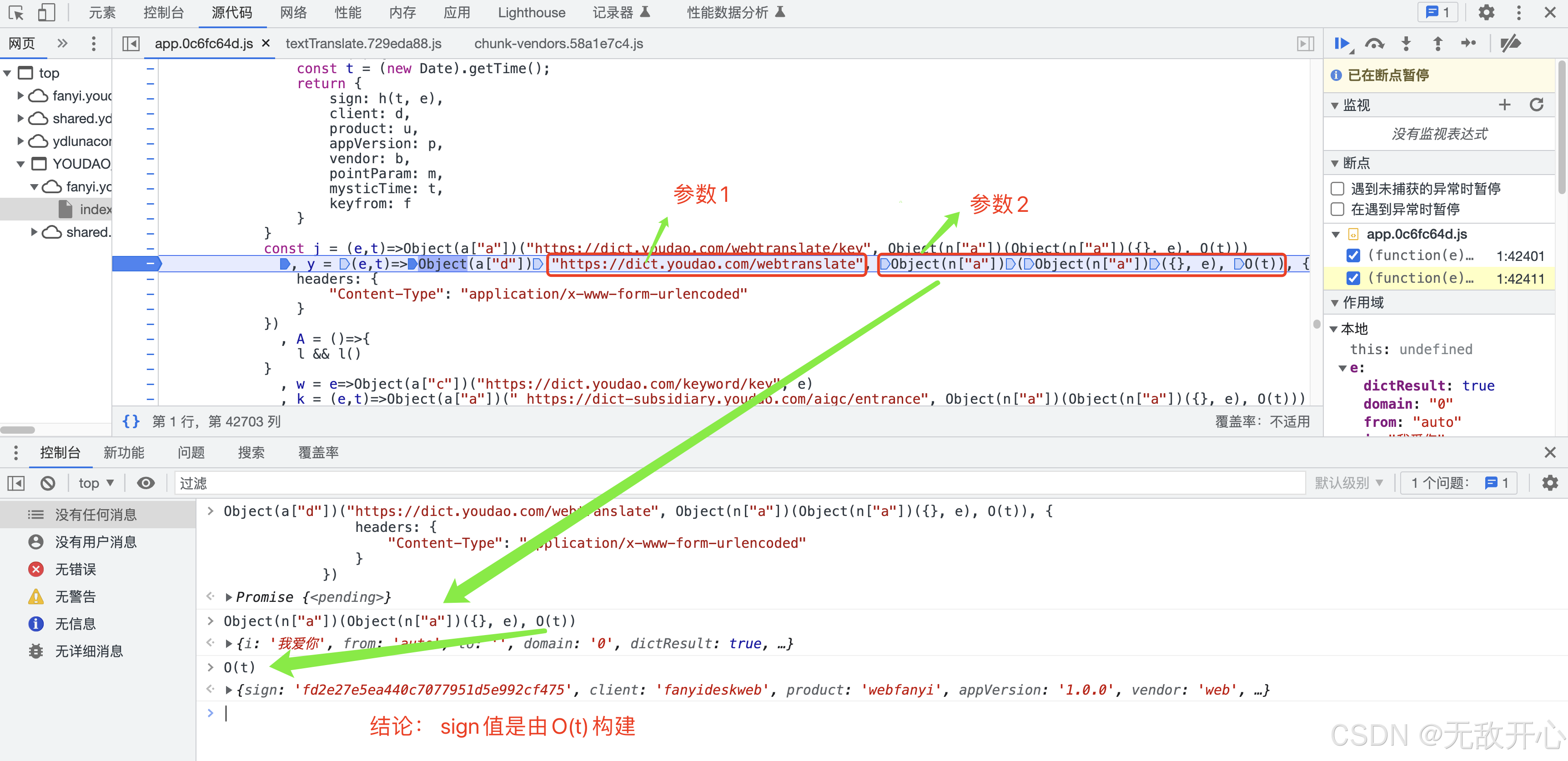
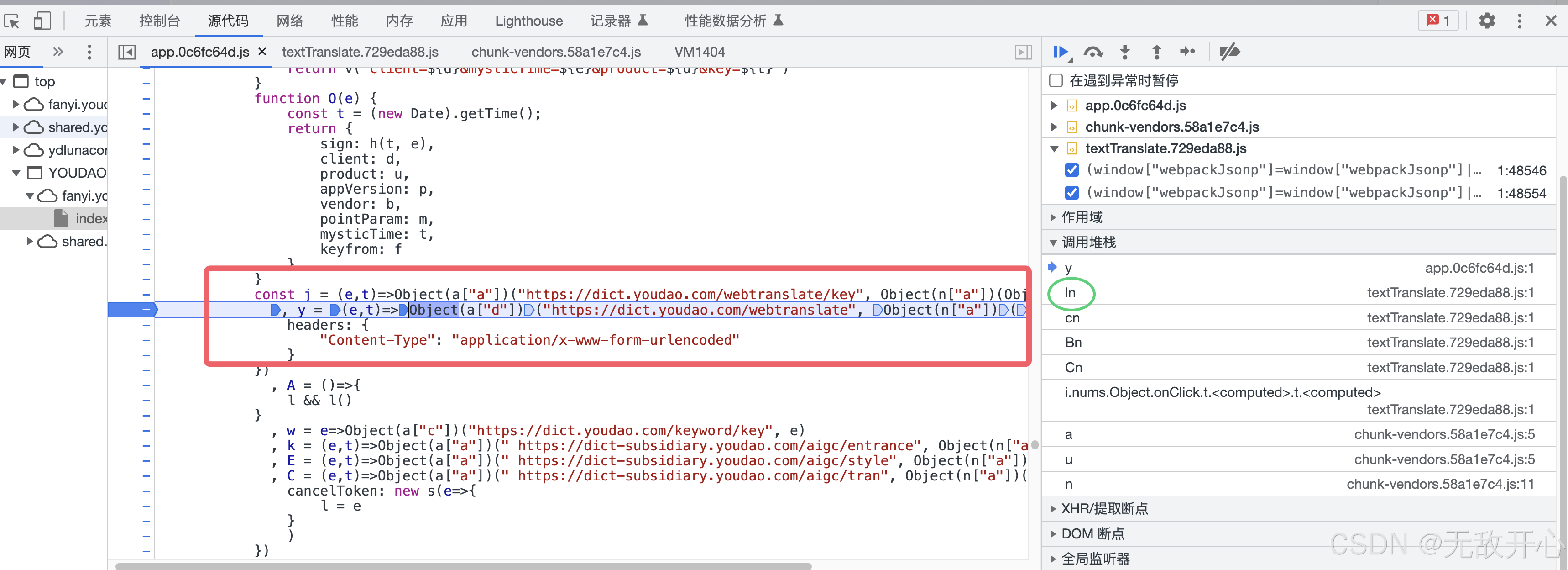
(3)获取构建数据的目标函数
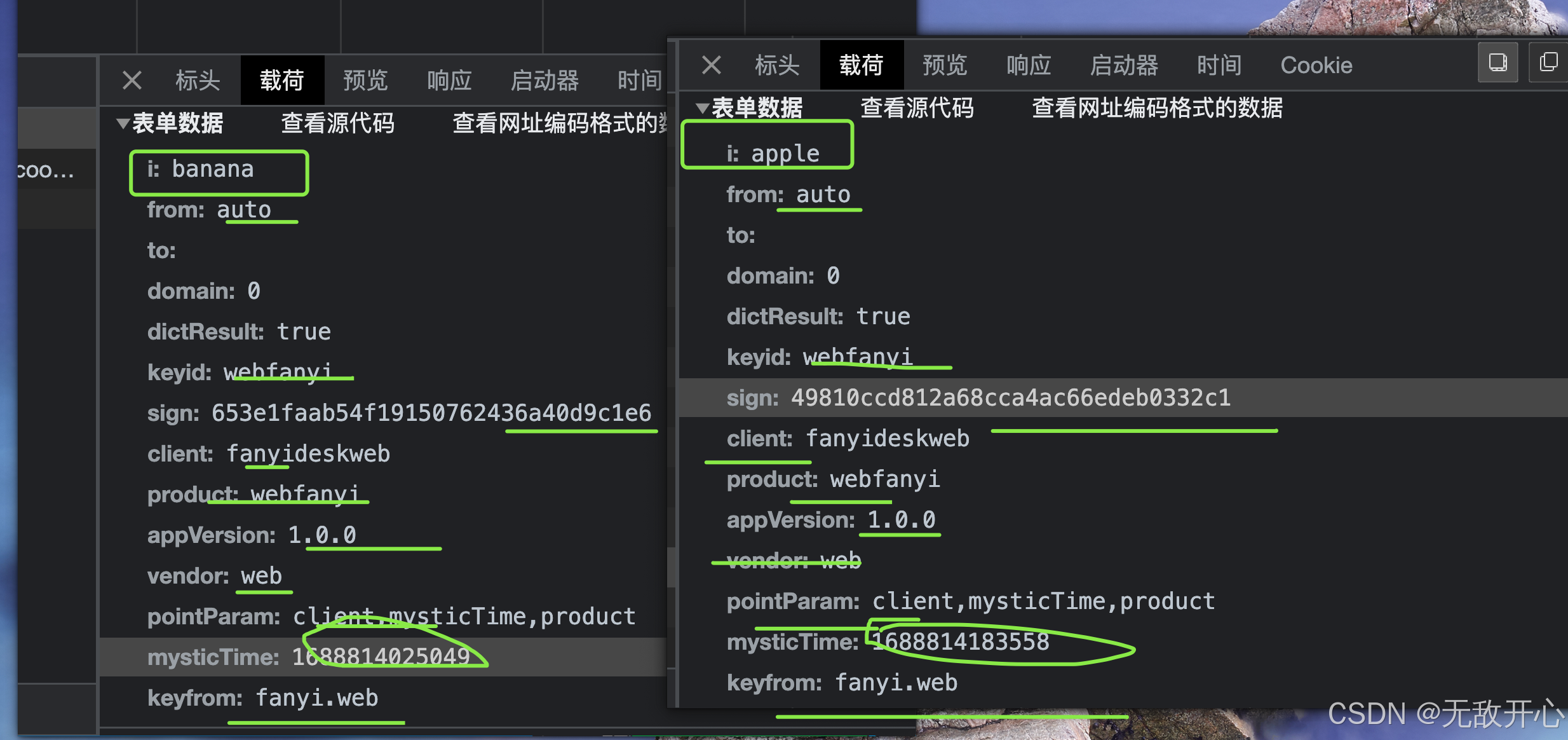
分析请求参数
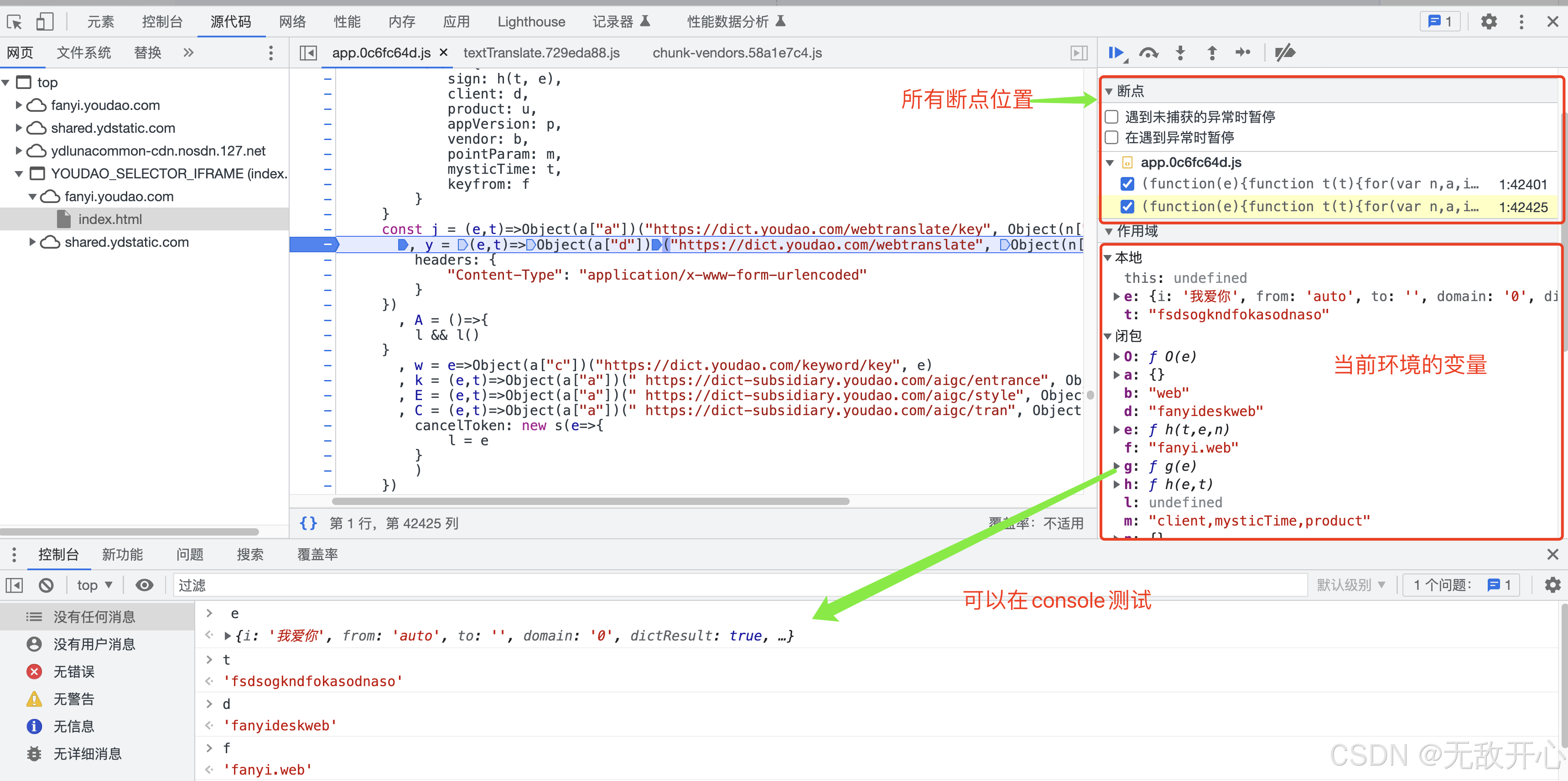
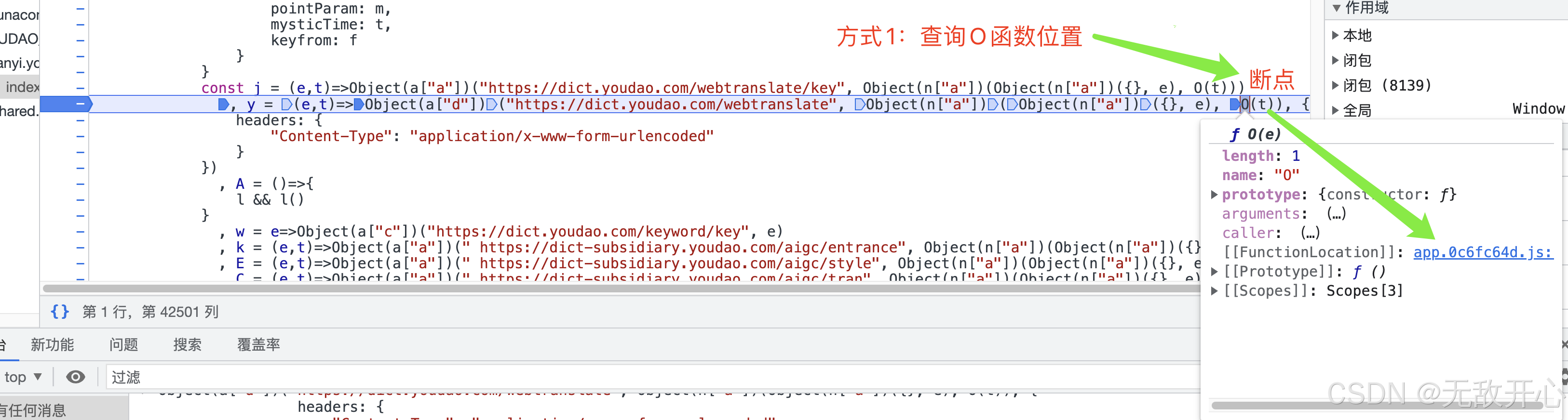
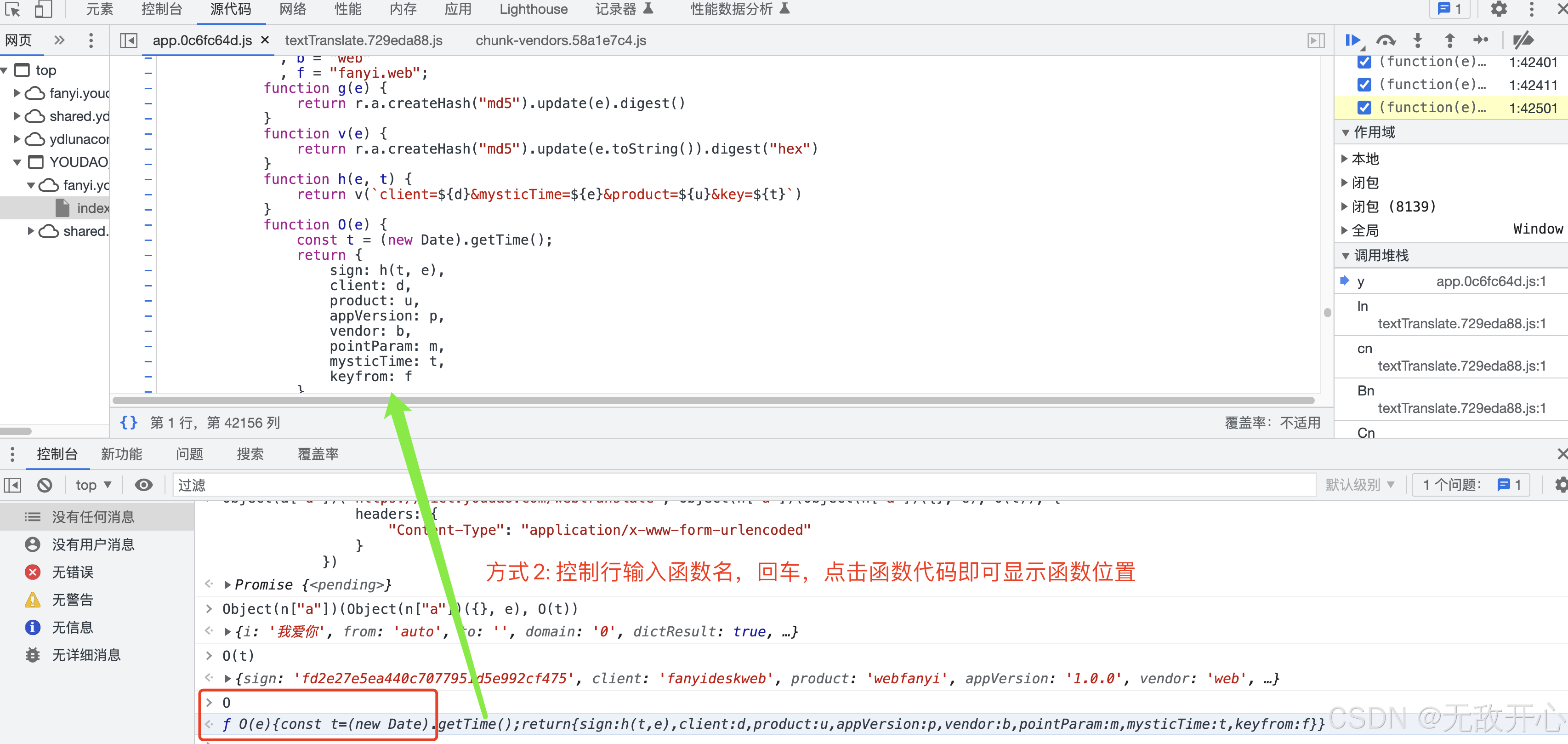
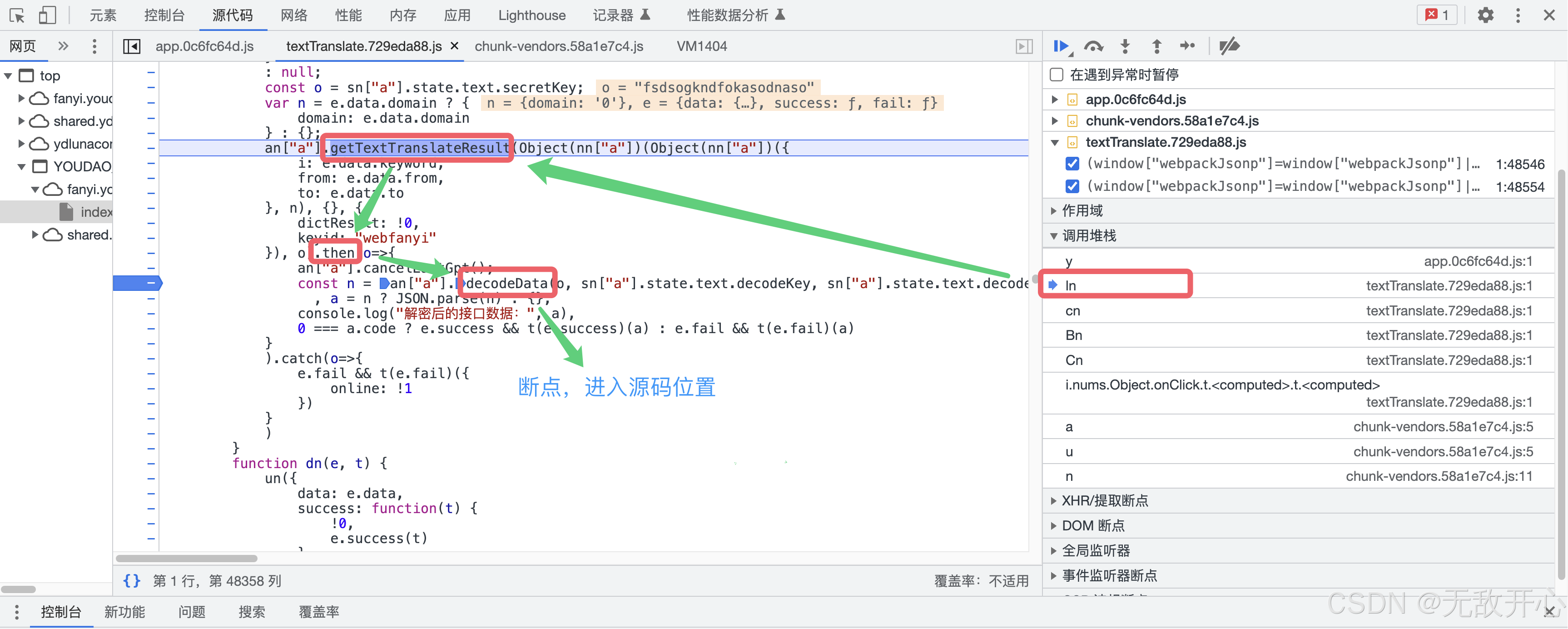
(4)获取目标函数源码位置
方式2:
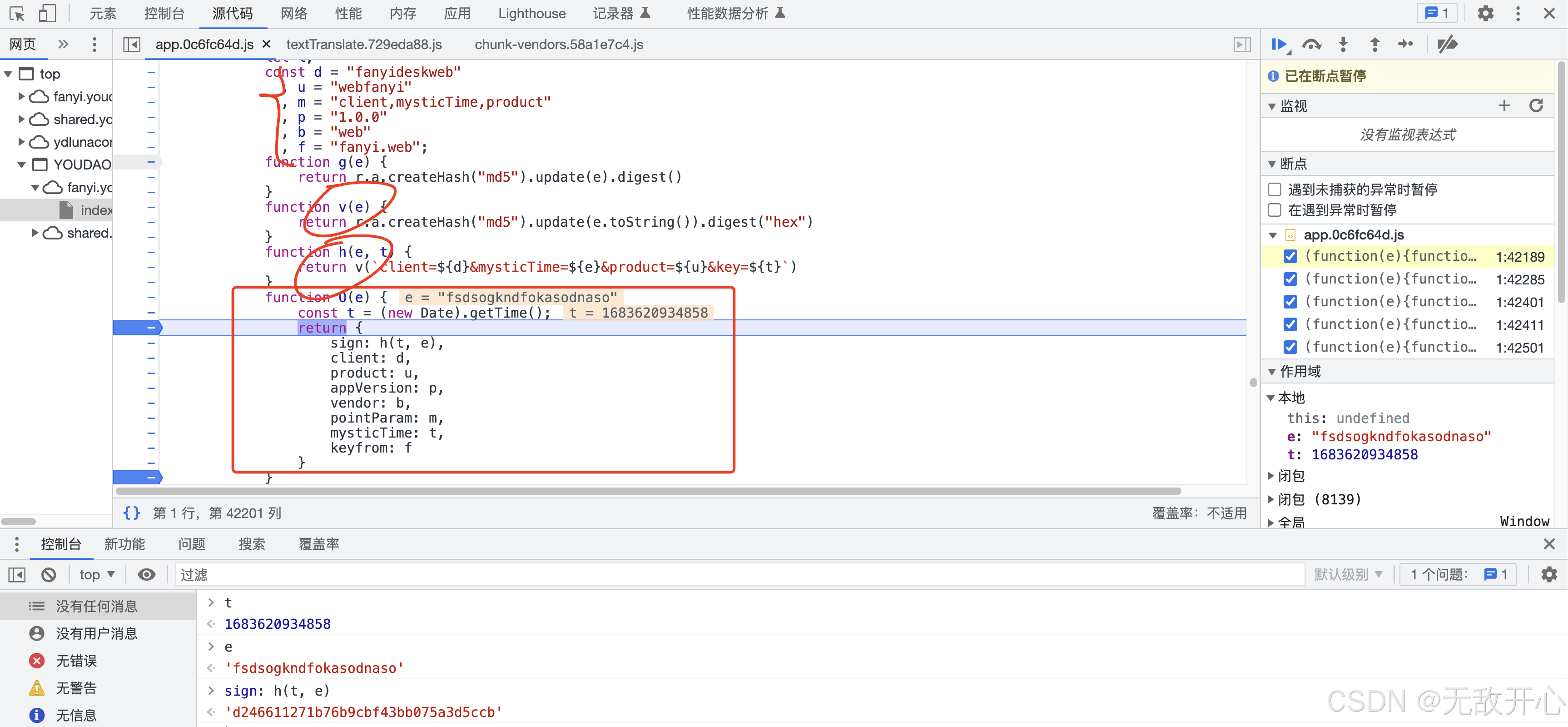
(5) 逆向实现
# Python逆向模拟:
import time
import hashlib
import requests
session = requests.session()
session.get("https://fanyi.youdao.com/")
word = "apple"
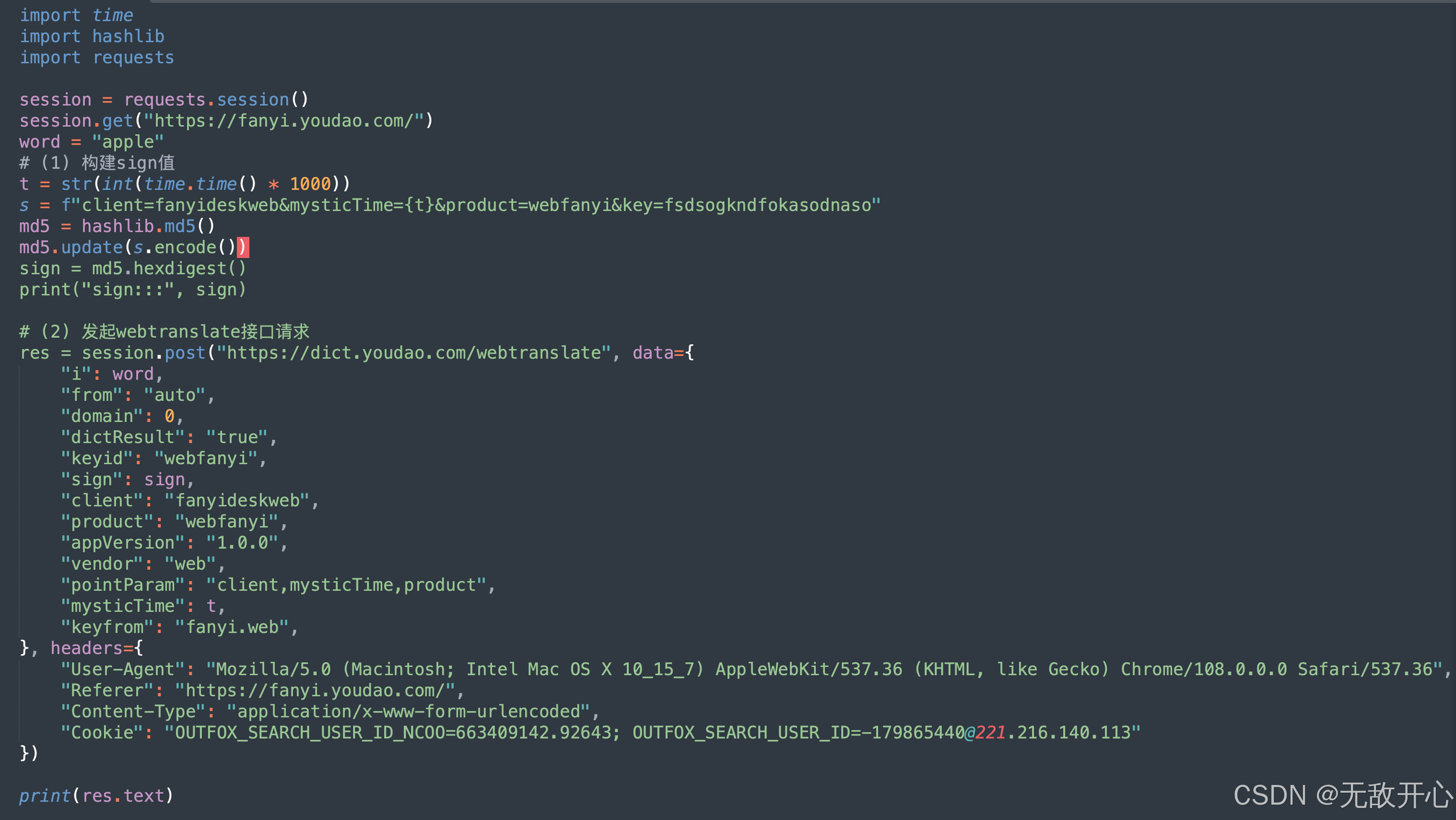
# (1) 构建sign值
t = str(1683620934858)
s = f"client=fanyideskweb&mysticTime={t}&product=webfanyi&key=fsdsogkndfokasodnaso"
md5 = hashlib.md5()
md5.update(s.encode())
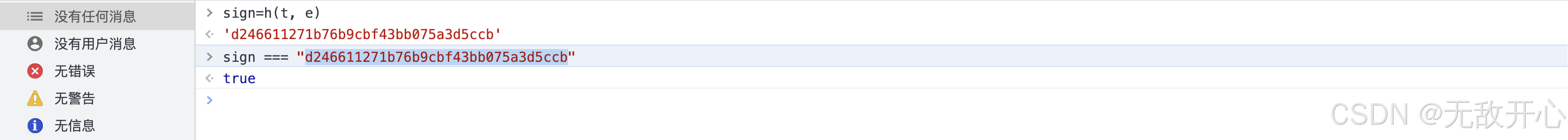
sign = md5.hexdigest()
print("sign:::", sign)
# sign::: d246611271b76b9cbf43bb075a3d5ccb
md5是标准的,没有魔改,程序员是个好人!
完整的逆向代码也就出来了:
res = session.post("https://dict.youdao.com/webtranslate", data={
"i": word,
"from": "auto",
"to": "",
"domain": "0",
"dictResult": "true",
"keyid": "webfanyi",
"sign": sign,
"client": "fanyideskweb",
"product": "webfanyi",
"appVersion": "1.0.0",
"vendor": "web",
"pointParam": "client,mysticTime,product",
"mysticTime": mysticTime,
"keyfrom": "fanyi.web",
}
结果为:
Z21kD9ZK1ke6ugku2ccWu-MeDWh3z252xRTQv-wZ6jddVo3tJLe7gIXz4PyxGl73nSfLAADyElSjjvrYdCvEP4pfohVVEX1DxoI0yhm36ytQNvu-WLU94qULZQ72aml6JKK7ArS9fJXAcsG7ufBIE0gd6fbnhFcsGmdXspZe-8whVFbRB_8Fc9JlMHh8DDXnskDhGfEscN_rfi-A-AHB3F9Vets82vIYpkGNaJOft_JA-m5cGEjo-UNRDDpkTz_NIAvo5PbATpkh7PSna2tHcE6Hou9GBtPLB67vjScwplB96-zqZKXJJEzU5HGF0oPDY_weAkXArzXyGLBPXFCnn_IWJDkGD4vqBQQAh2n52f48GD_cb-PSCT_8b-ESsKUI9NJa11XsdaUZxAc8TzrYnXwdcQbtl_kZGKhS6_rCtuNEBouA_lvM2CbS7TTtV2U4zVmJKpp-c6nt3yZePK3Av01GWn1pH_3sZbaPEx8DUjSbdp4i4iK-Mj4p2HPoph67DR7B9MFETYku_28SgP9xsKRRvFH4aHBHESWX4FDbwaU=
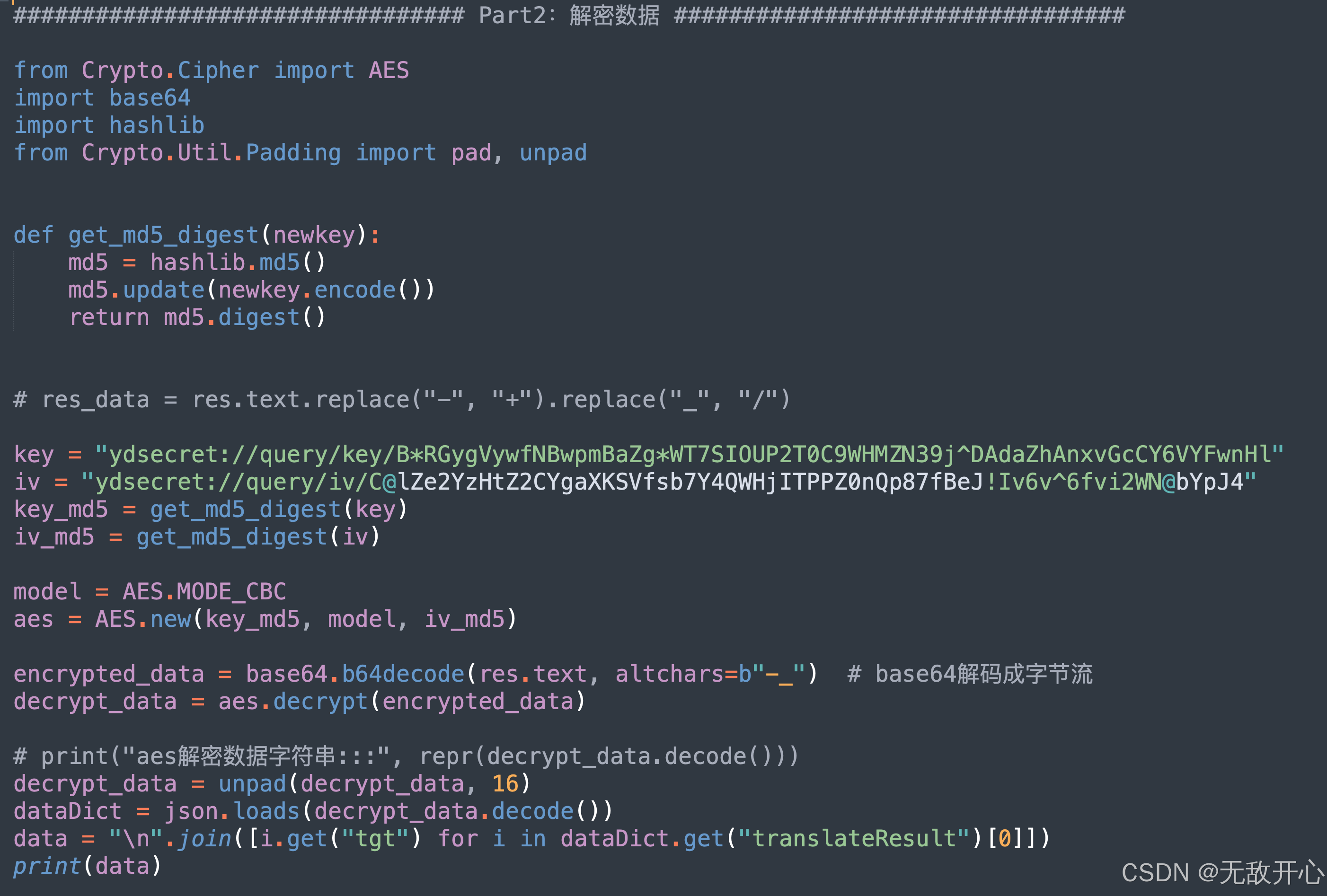
Part02:解密数据
(1)解密入口
(2)查找解密函数
import hashlib
def get_md5_digest(newkey):
md5 = hashlib.md5()
md5.update(newkey.encode())
return md5.digest()
key = "ydsecret://query/key/B*RGygVywfNBwpmBaZg*WT7SIOUP2T0C9WHMZN39j^DAdaZhAnxvGcCY6VYFwnHl"
iv = "ydsecret://query/iv/C@lZe2YzHtZ2CYgaXKSVfsb7Y4QWHjITPPZ0nQp87fBeJ!Iv6v^6fvi2WN@bYpJ4"
key_md5 = get_md5_digest(key)
iv_md5 = get_md5_digest(iv)
基于Python的完整解密:
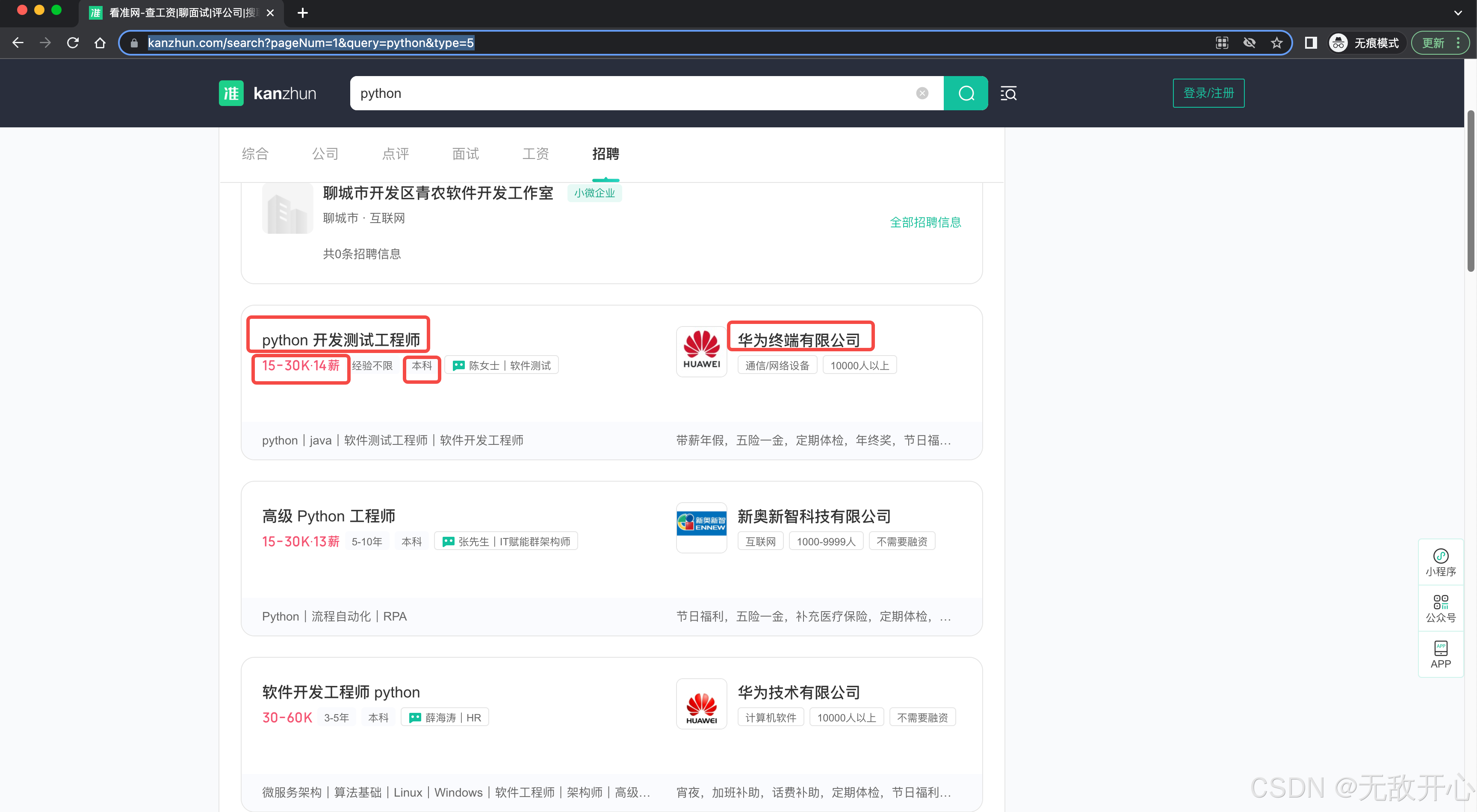
今日作业
网页地址:https://www.kanzhun.com/search?pageNum=1&query=python&type=5
要求:爬虫岗位信息,实现请求信息逆向过程,标好思路和过程的注释。