Tryhackerme Investigating Windows
前言
这个靶场主要还是应急响应部分的,Windows系统排查,调查windows方面的
简介
This is a challenge that is exactly what is says on the tin, there are a few challenges around investigating a windows machine that has been previously compromised.
这是一个挑战,正如罐头上所说的那样,在调查以前被入侵的 Windows 机器方面存在一些挑战。
Connect to the machine using RDP. The credentials the machine are as follows:
使用 RDP 连接到计算机。计算机的凭据如下:
Username: Administrator 用户名:管理员
Password: letmein123! 密码:letmein123!
Please note that this machine does not respond to ping (ICMP) and may take a few minutes to boot up.
请注意,此计算机不响应 ping (ICMP),可能需要几分钟才能启动。
文章目录
- Tryhackerme Investigating Windows
- 前言
- 简介
- Whats the version and year of the windows machine?
- Windows机器的版本和年份是什么?
- Which user logged in last?
- 哪个用户最后登录?
- When did John log onto the system last?
- John 上次登录系统是什么时候?
- What IP does the system connect to when it first starts?
- 系统首次启动时连接到哪个 IP?
- What two accounts had administrative privileges (other than the Administrator user)?
- 哪两个帐户具有管理权限(管理员用户除外)?
- Whats the name of the scheduled task that is malicous.
- 恶意计划任务的名称是什么。
- What file was the task trying to run daily?
- 任务每天尝试运行哪个文件?
- What port did this file listen locally for?
- 此文件在本地侦听了哪个端口?
- When did Jenny last logon?
- 珍妮上次登录是什么时候?
- At what date did the compromise take place?
- 妥协发生在哪一天?
- During the compromise, at what time did Windows first assign special privileges to a new logon?
- 在入侵期间,Windows 何时首次为新登录分配特殊权限?
- What tool was used to get Windows passwords?
- 使用什么工具获取 Windows 密码?
- What was the attackers external control and command servers IP?
- 攻击者的外部控制和命令服务器IP是什么?
- What was the extension name of the shell uploaded via the servers website?
- 通过服务器网站上传的 shell 的扩展名称是什么?
- What was the last port the attacker opened?
- 攻击者打开的最后一个端口是什么?
- Check for DNS poisoning, what site was targeted?
- 检查DNS中毒,针对哪个站点?
Whats the version and year of the windows machine?
Windows机器的版本和年份是什么?
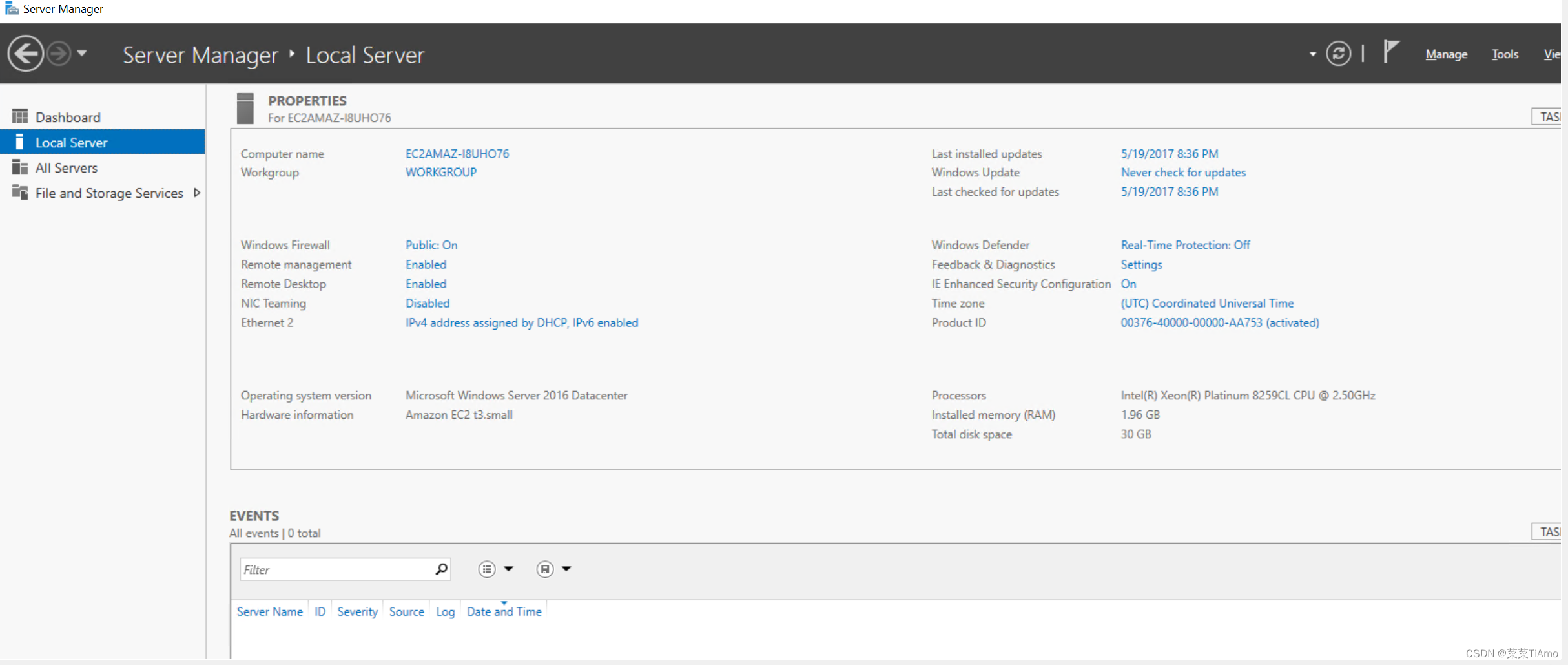
一打眼我们发现这个靶机是windows server 但是不知道是什么版本,windwosw server有一个管理的平台
server manager
在管理平台可以看到windows版本信息
windows server 2016
Which user logged in last?
哪个用户最后登录?
那个用户最后登录,最后登录图形化界面可以通过事件管理器去查看
Event viewer
1.打开 Event Viewer。
2.在左侧导航栏中,依次展开 “Windows Logs” > “Security” 看里面的内容
3.在右侧窗格中,会列出安全事件。你可以在其中查找 ID 为 4624 的事件,这是登录成功的事件。这些事件将显示用户的登录时间和其他相关信息。
cmd查看
C:\Users\Administrator>net user
User accounts for \\EC2AMAZ-I8UHO76
-------------------------------------------------------------------------------
Administrator DefaultAccount Guest
Jenny John
The command completed successfully.
C:\Users\Administrator>net user Administrator
User name Administrator
Full Name
Comment Built-in account for administering the computer/domain
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 3/2/2019 5:46:03 PM
Password expires Never
Password changeable 3/2/2019 5:46:03 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 6/12/2024 10:44:00 AM
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *None
The command completed successfully
C:\Users\Administrator>net user Jenny
User name Jenny
Full Name Jenny
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 3/2/2019 4:52:25 PM
Password expires Never
Password changeable 3/2/2019 4:52:25 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Administrators *Users
Global Group memberships *None
The command completed successfully.
.......
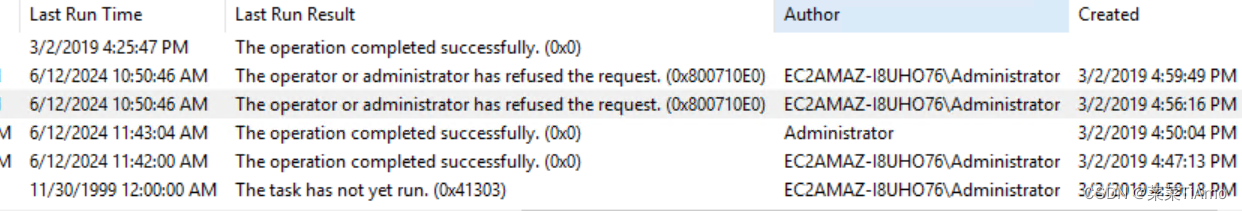
列出所有用户后,一个一个去查看last logon通过对比Administrator是最近的
When did John log onto the system last?
John 上次登录系统是什么时候?
可以和第二题使用一样的代码去查看.
C:\Users\Administrator>net user john
User name John
Full Name John
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 3/2/2019 5:48:19 PM
Password expires Never
Password changeable 3/2/2019 5:48:19 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 3/2/2019 5:48:32 PM
Logon hours allowed All
Local Group Memberships *Users
Global Group memberships *None
The command completed successfully.
答案 : 03/02/2019 5:48:32 PM
What IP does the system connect to when it first starts?
系统首次启动时连接到哪个 IP?
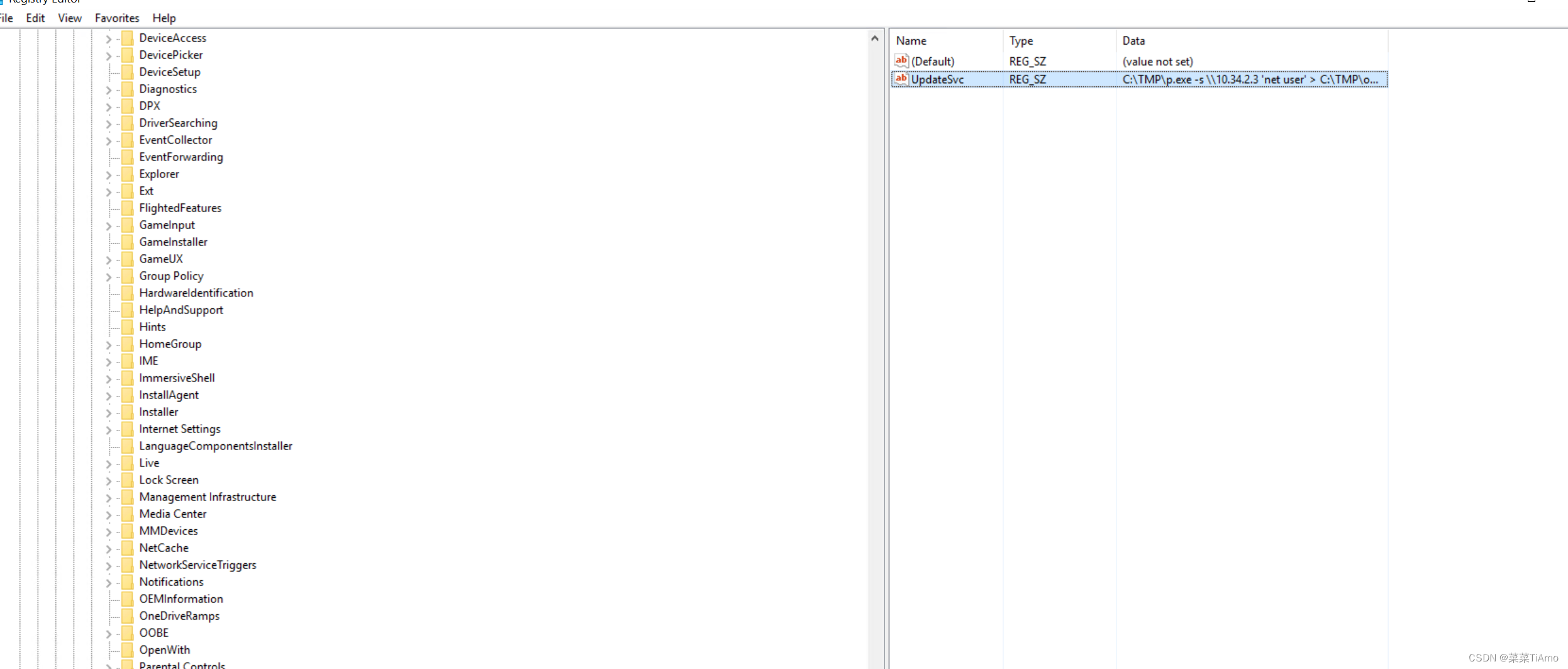
在启动系统的时候我们看到了,但是我们不能清除的记得,只记得是p.exe的文件执行的,但是没有在事件管理器中找到,
我们看一下注册表中有没有,一般系统开机启动的都是可以在注册表找到的为了防止有些小伙伴在英文中迷了眼,可以在cmd中输入 regedit来打开注册表
进入注册表我们也不知道到底是啥在哪我们直接一点ctrl+f查找C:\TMP\p.exe,我们在执行命令的时候有一个mim.exe反复执行我们大概猜到TMP是攻击者创建的文件夹存放攻击工具的地方
答案: 10.34.2.3
What two accounts had administrative privileges (other than the Administrator user)?
哪两个帐户具有管理权限(管理员用户除外)?
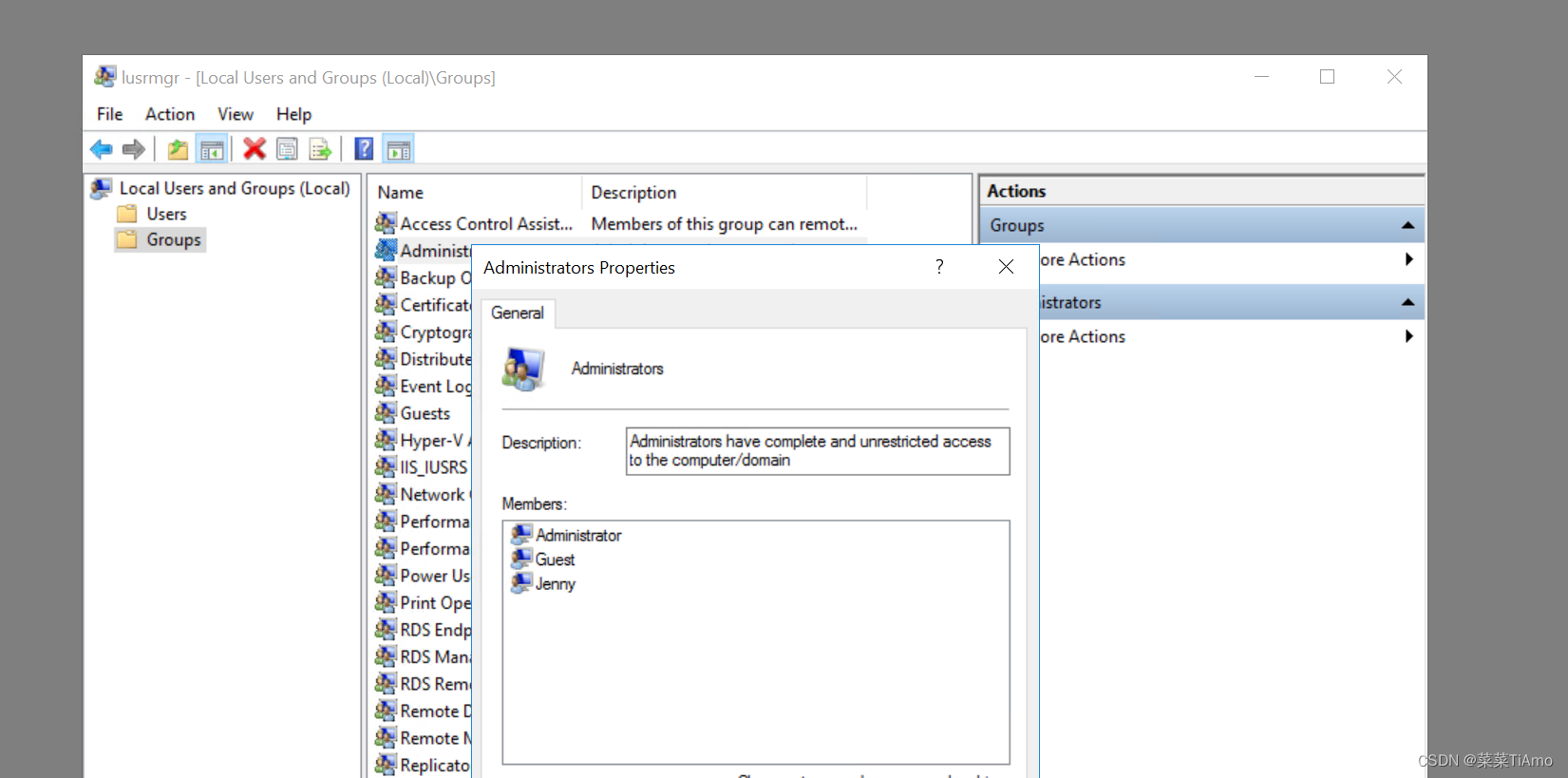
图形化界面我们可以查看本地用户和组,来查看本地的Administrator 组中有那些用户
由于TiAmo我也看着英文就晕所以我直接使用Cmd代劳 win+R 输入 lusrmgr.msc打开本地用户和组
查看groups(组) administrators 组 发现三个用户具有管理员权限
答案:Jenny, Guest
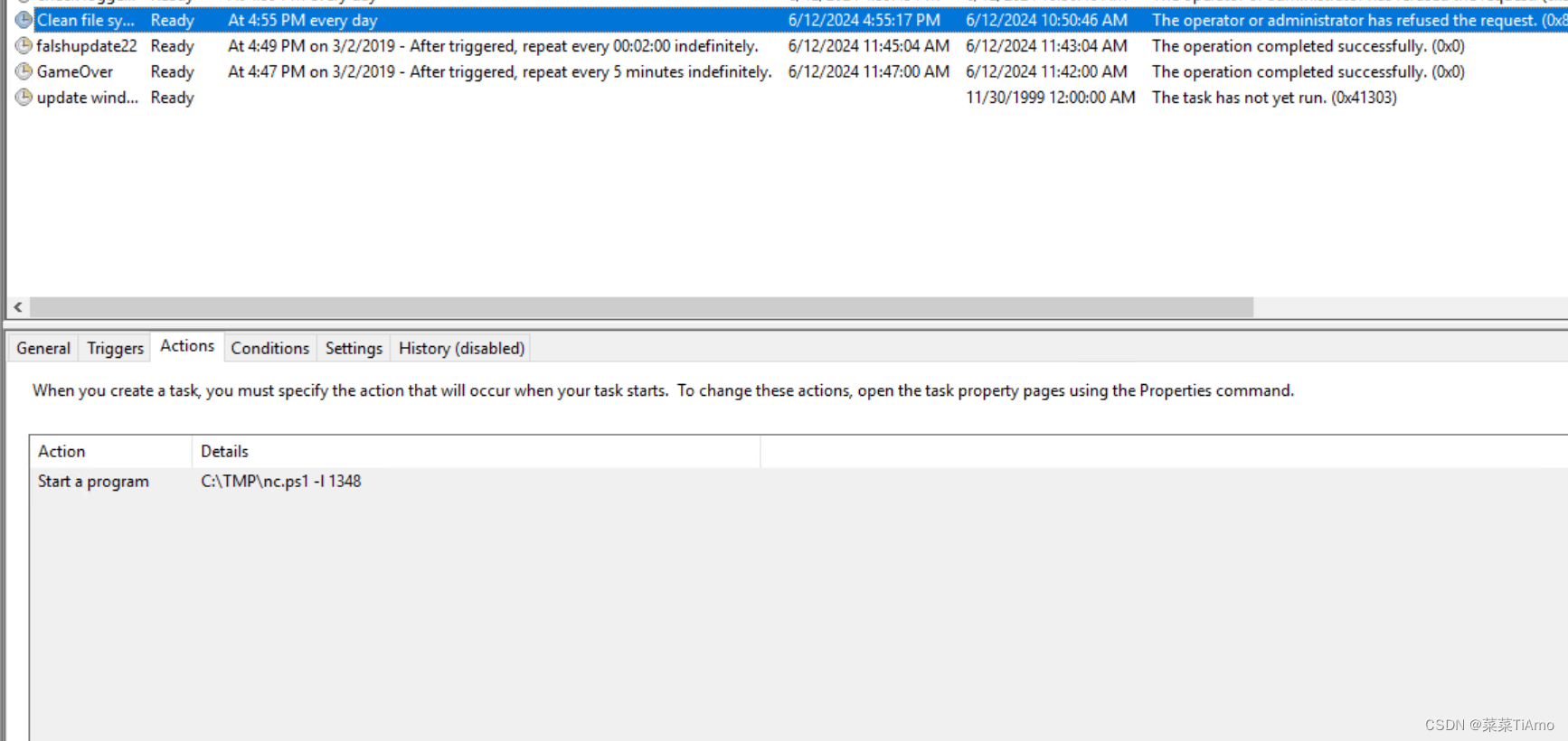
Whats the name of the scheduled task that is malicous.
恶意计划任务的名称是什么。
这个我们要在任务计划管理器中去查看也可以在cmd中输入命令查看
任务计划管理器
win+r
taskschd.msc
打开任务计划管理器
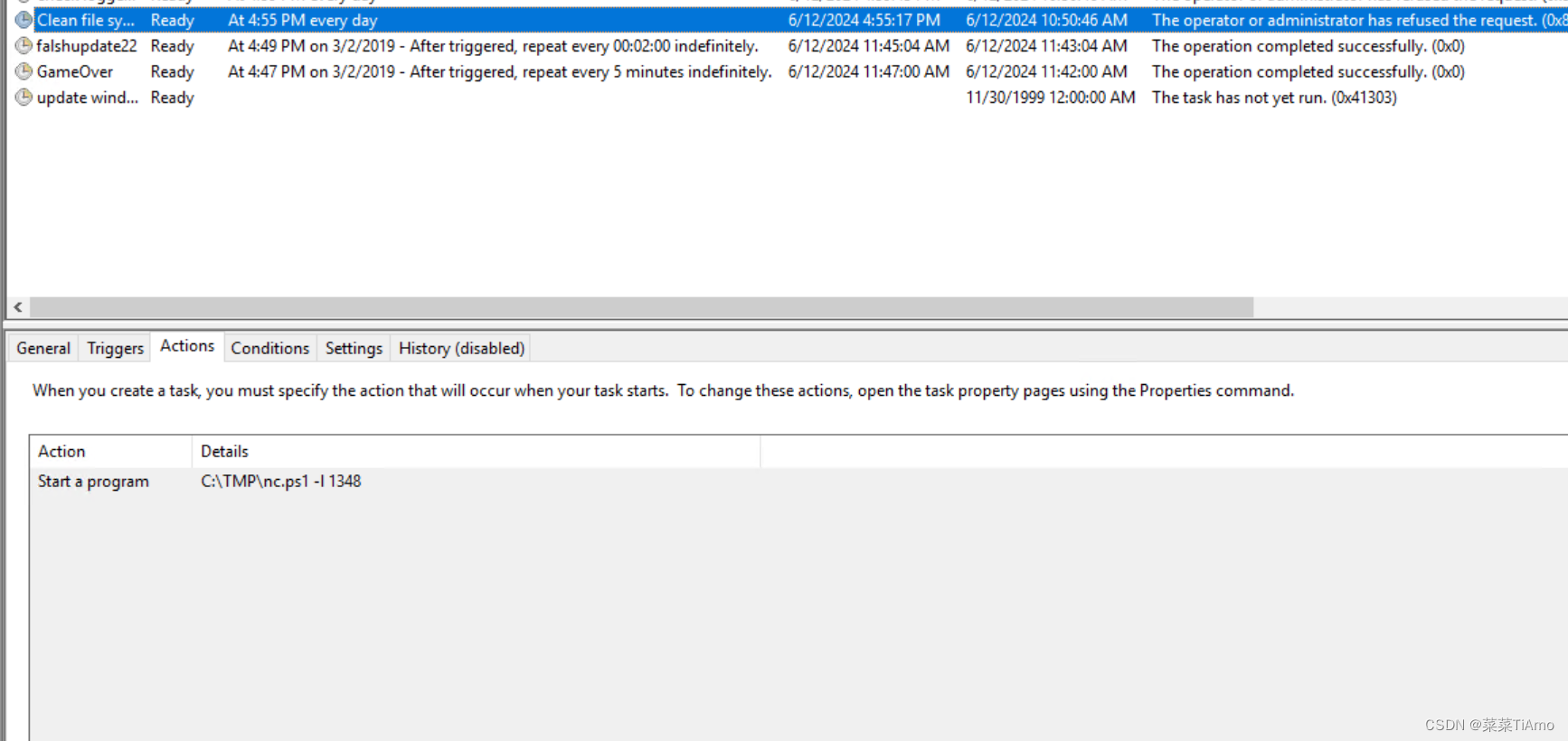
因为我们前边推断C://TMP目录是攻击者的存放攻击工具的目录所以我们看它调用了那个文件夹的那个程序
一共是发现两个可疑的程序
clean file system
A task to clean old files of the system
清理系统旧文件的任务
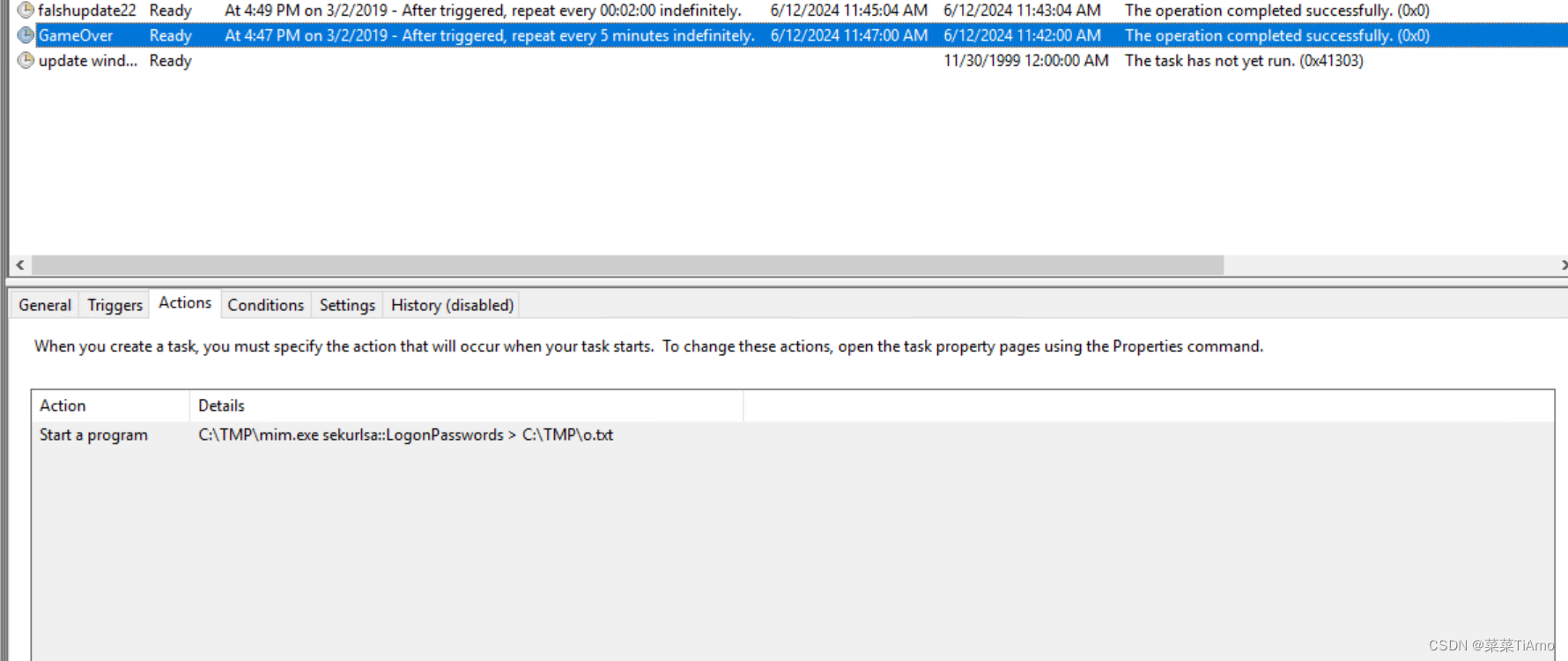
gameover
看他执行的命令应该是使用mim.exe将windows的密码写道C:/TMP\的o.txt中
答案:clean file system
What file was the task trying to run daily?
任务每天尝试运行哪个文件?
查看Triggers就可以看到是否是每日执行,结合Actions就不难看出是nc.ps1 而 -l 1348就是参数和参数值
答案: ns.ps1
What port did this file listen locally for?
此文件在本地侦听了哪个端口?
根据参数值就不难发现是1348
答案:1348
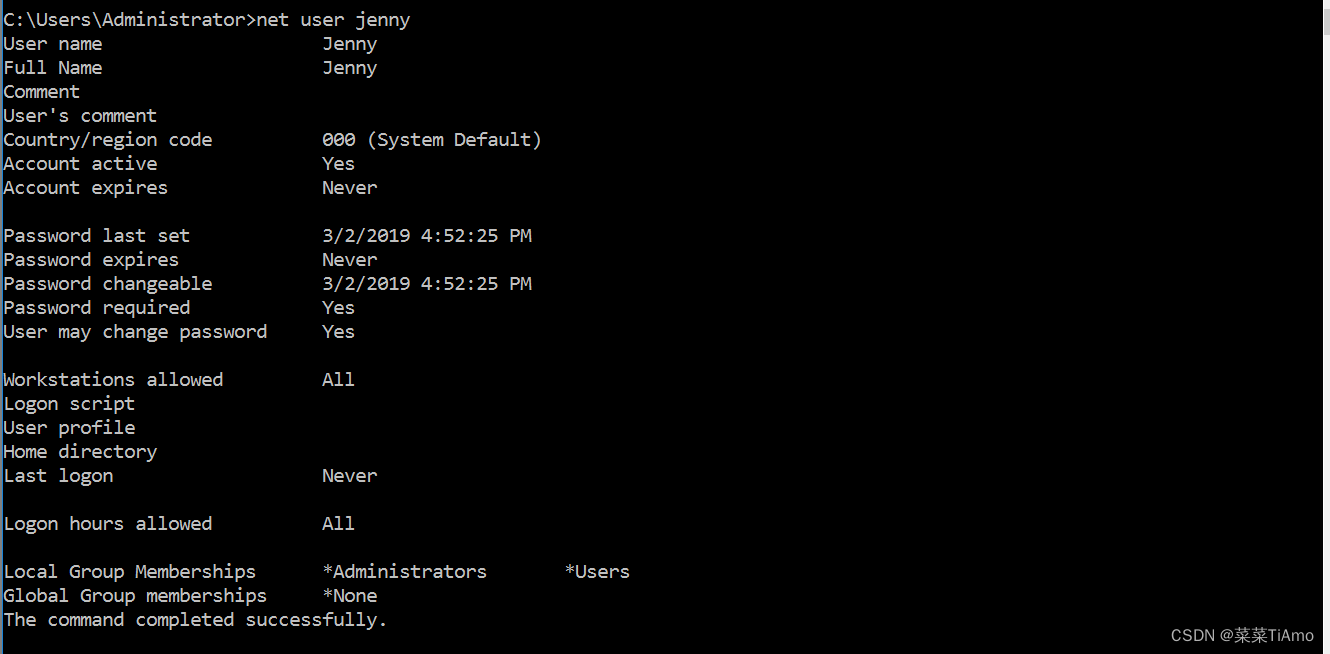
When did Jenny last logon?
珍妮上次登录是什么时候?
net user jenny 就可以查看了
答案:never
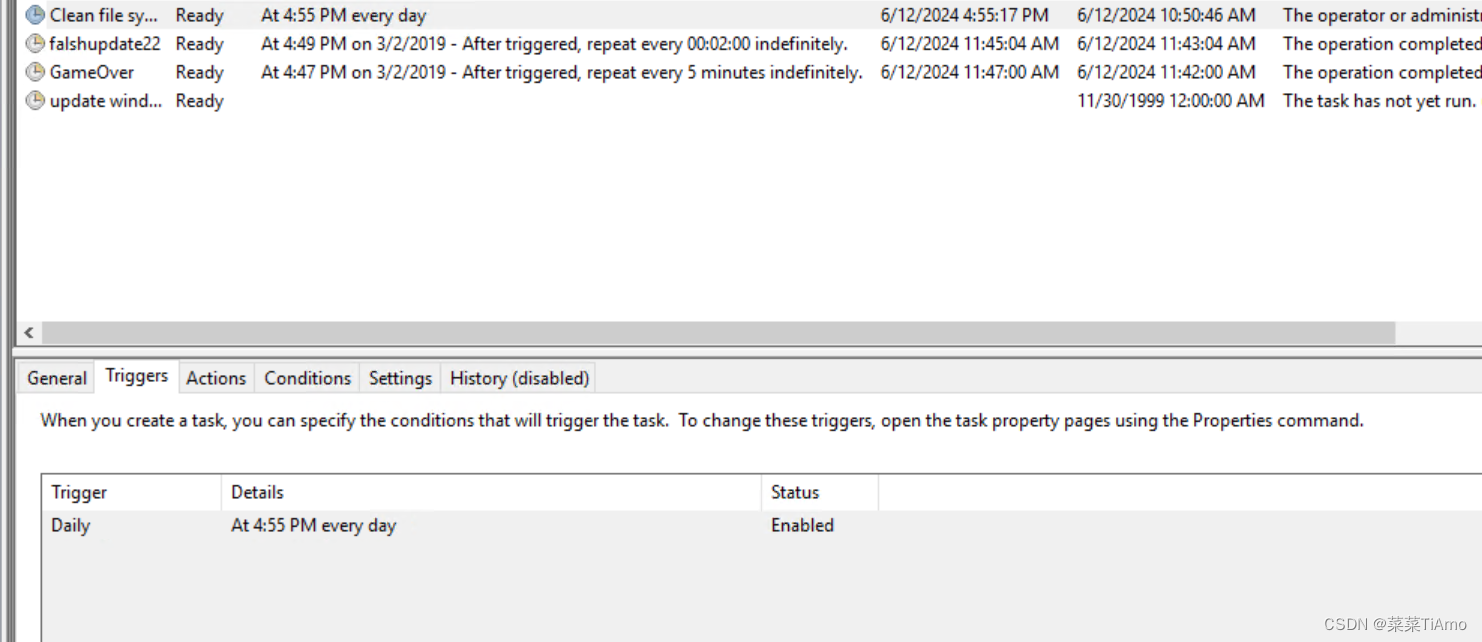
At what date did the compromise take place?
妥协发生在哪一天?
这个题目是没看明白的,应该说的是服务器是什么时候被RCE的
由于攻击者已经将日志清理干净了,而且入侵完服务器的第一件事就是清除日志文件所以应该就是clean file system创建的那一天
拖到后面就是创建的时间
答案:03/02/2019
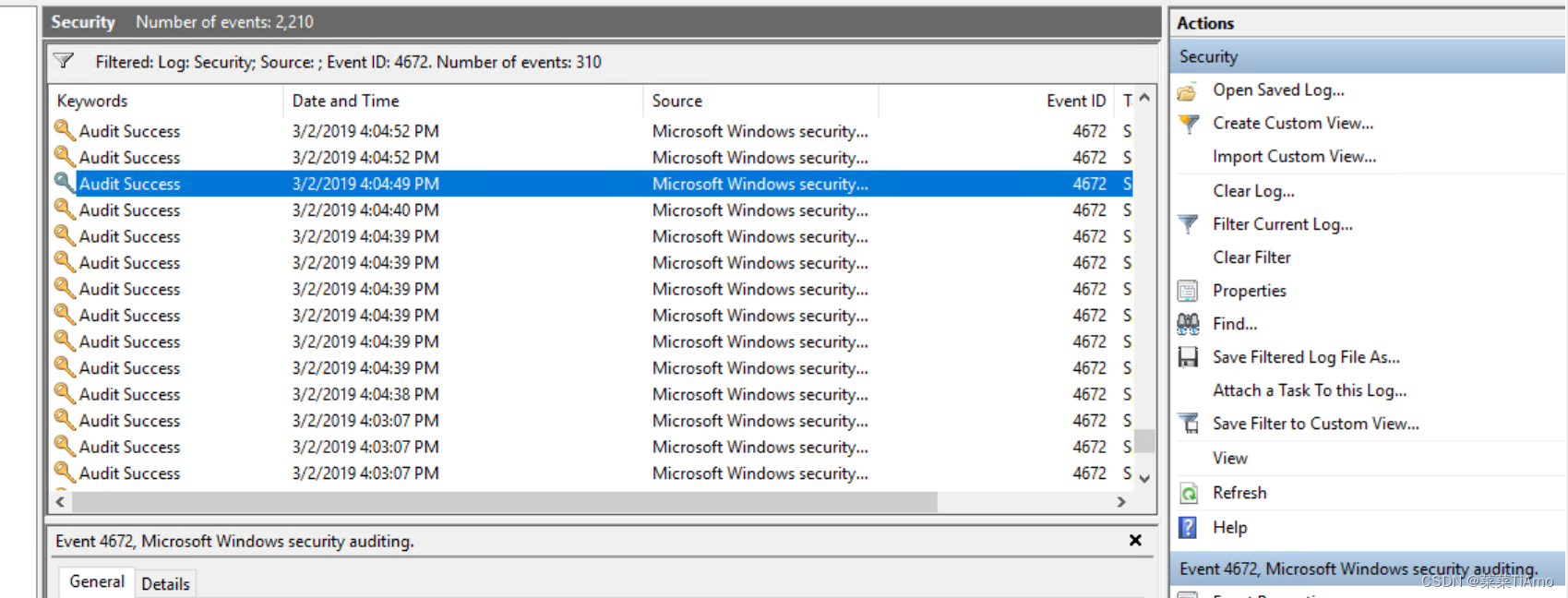
During the compromise, at what time did Windows first assign special privileges to a new logon?
在入侵期间,Windows 何时首次为新登录分配特殊权限?
这个题我也做了半天最后看提示找到的答案,这个题的思路还是进入事件查看器中查看,windows logs —secuity 筛选进程ID为4672的进程,提示说是49秒,我们看看哪一个是49秒
唯一的49秒所以
答案:03/02/2019 04:04:49 PM
What tool was used to get Windows passwords?
使用什么工具获取 Windows 密码?
相信从每次运行也知道了差不多了
mim.exe在内网运行能在内存中获取账号密码,必然是内网渗透神器(Mimikatz)
答案:Mimikatz
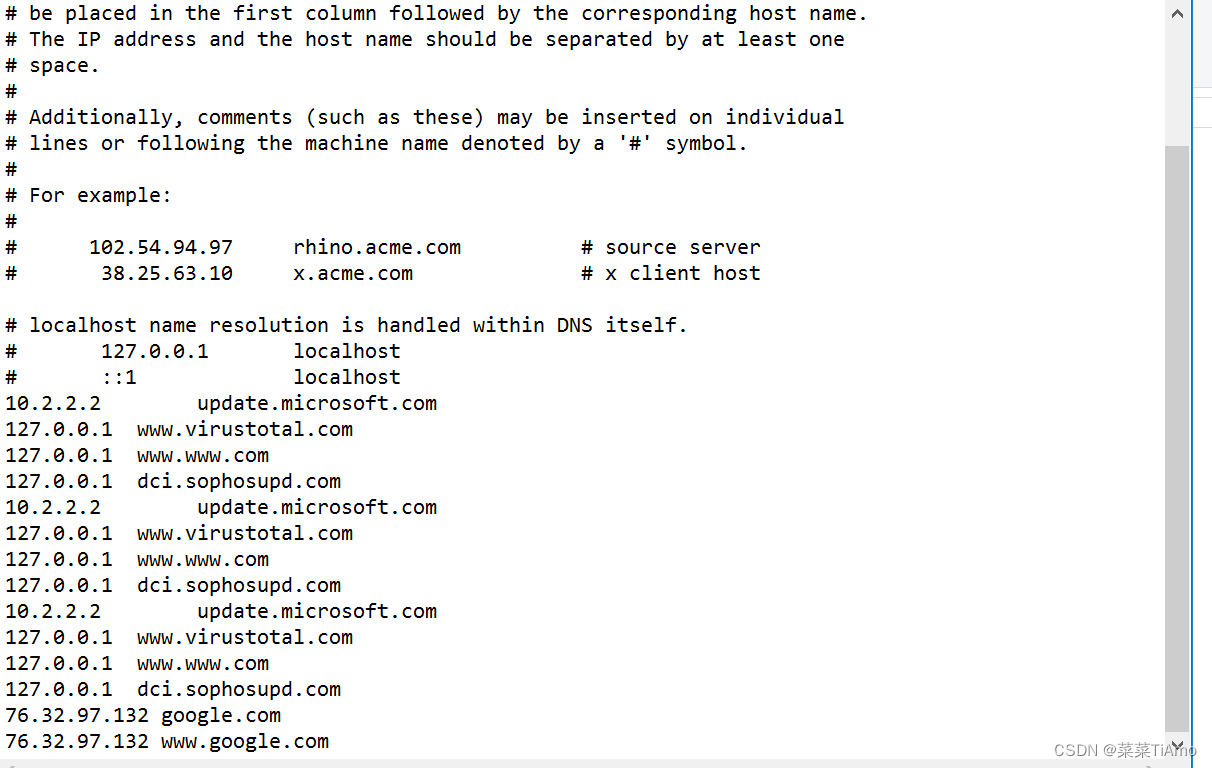
What was the attackers external control and command servers IP?
攻击者的外部控制和命令服务器IP是什么?
这个我们要去看hosts文件
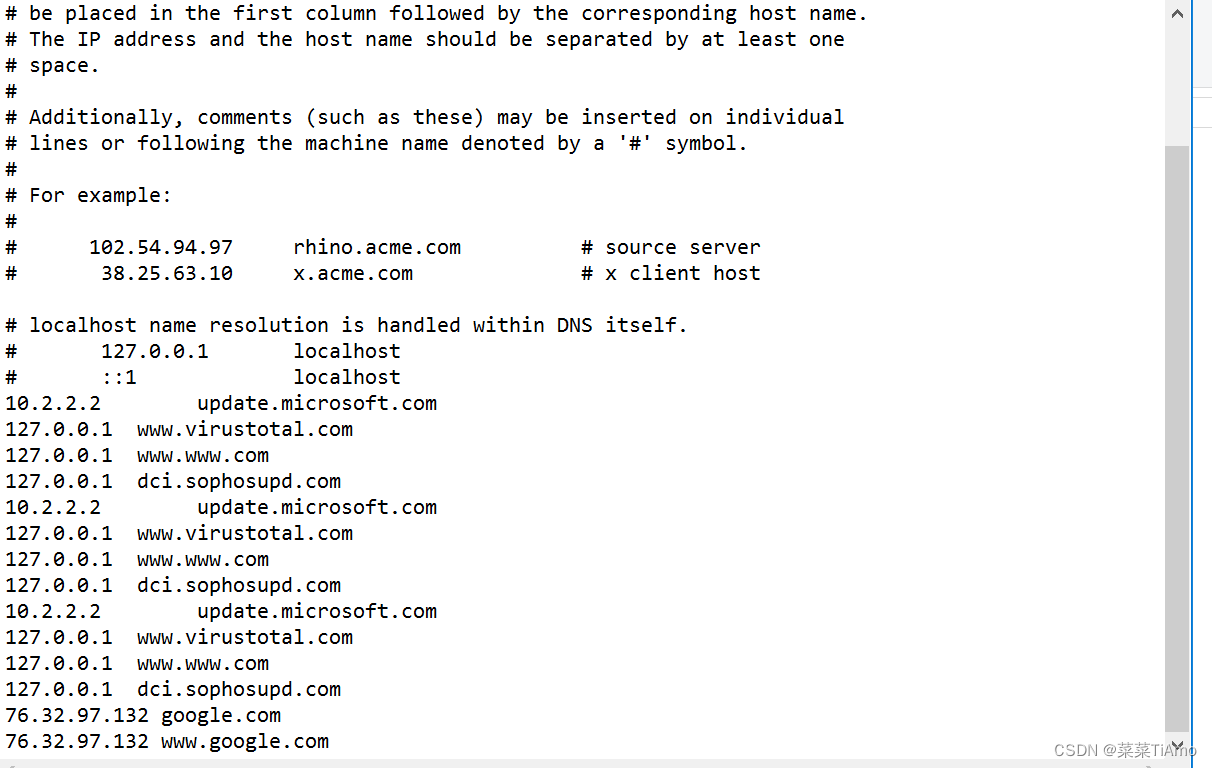
唯一的外来IP 76.32.97.132
答案:76.32.97.132
What was the extension name of the shell uploaded via the servers website?
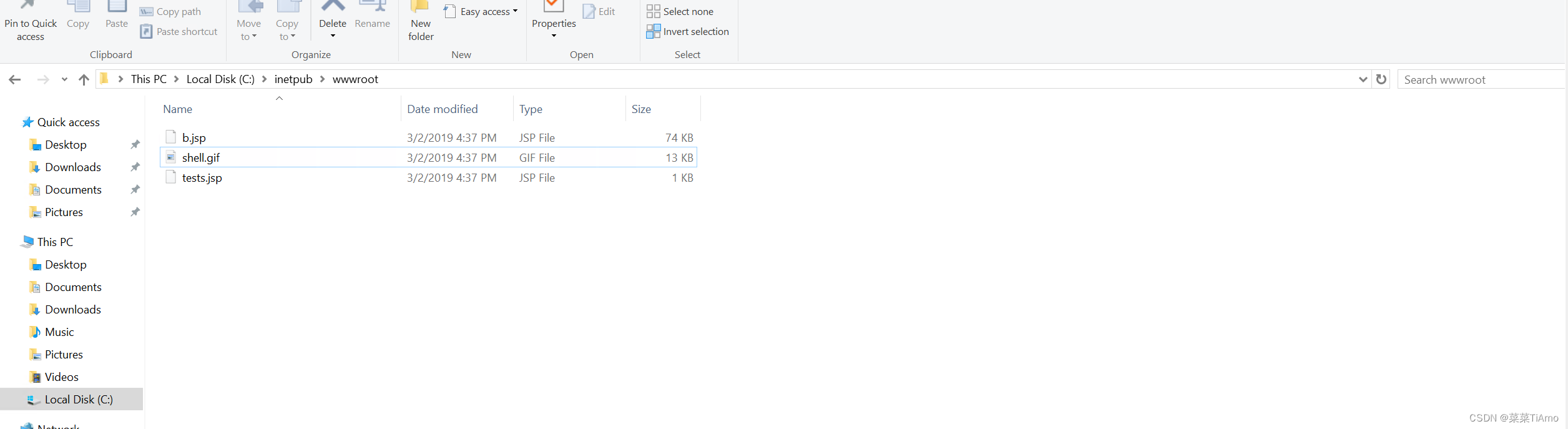
通过服务器网站上传的 shell 的扩展名称是什么?
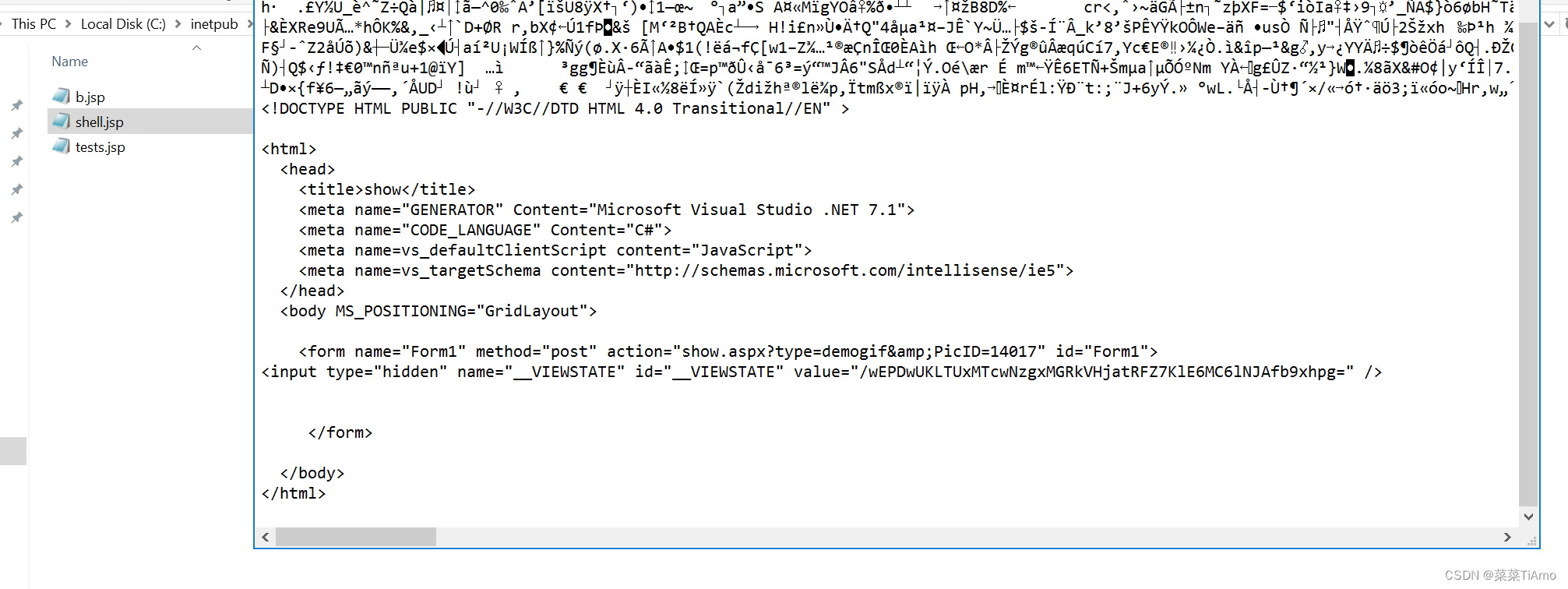
服务器网站,那我们就找一下网站根目录,wwwroot,发现shell是gif格式的但是其他的都是jsp,gif是图片格式但是可以进行隐写在gif中我们改一下后缀来看一下
发现可以执行但是上面是乱码,上面的乱码是gif图片的
答案:.jsp
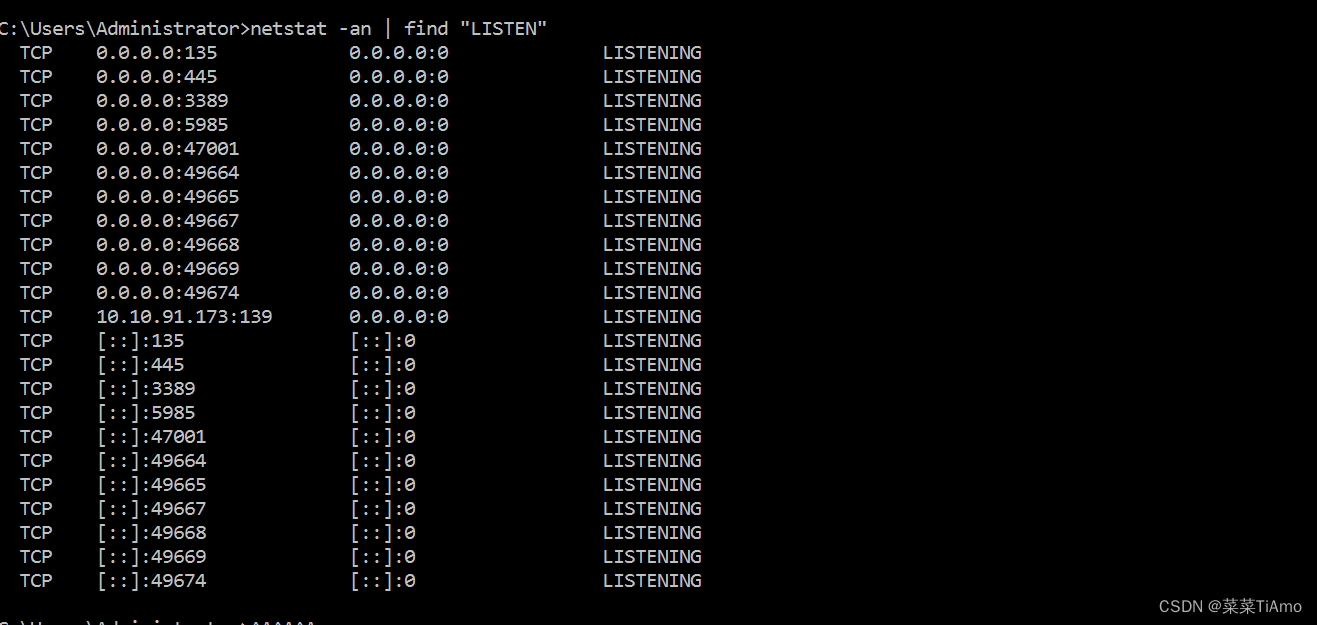
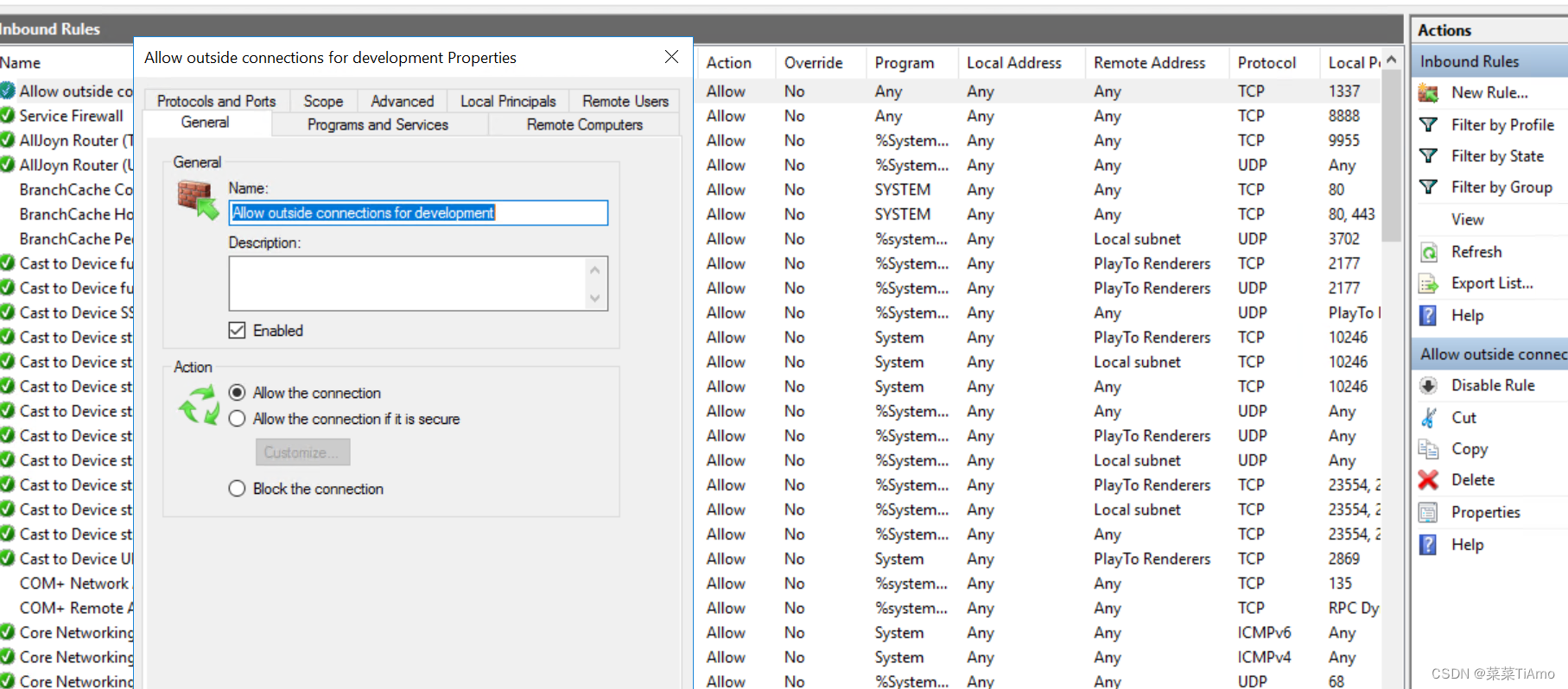
What was the last port the attacker opened?
攻击者打开的最后一个端口是什么?
在处于监听状态的端口的中没看到奇怪的端口
看一下防火墙的入站规则
Allow outside connections for development
允许外部连接进行开发
感觉就不想好货
答案:1337
Check for DNS poisoning, what site was targeted?
检查DNS中毒,针对哪个站点?
这个在上面有提到hosts文件中写了
hosts文件在本地优先于DNS解析域名,提供手动映射域名到IP地址的功能。
答案:google.com