一、抓包分析
Flutter应用是内置进行ssl证书校验的,无法通过常规方法抓到包,需要通过frida把它内置的ssl校验hook掉。
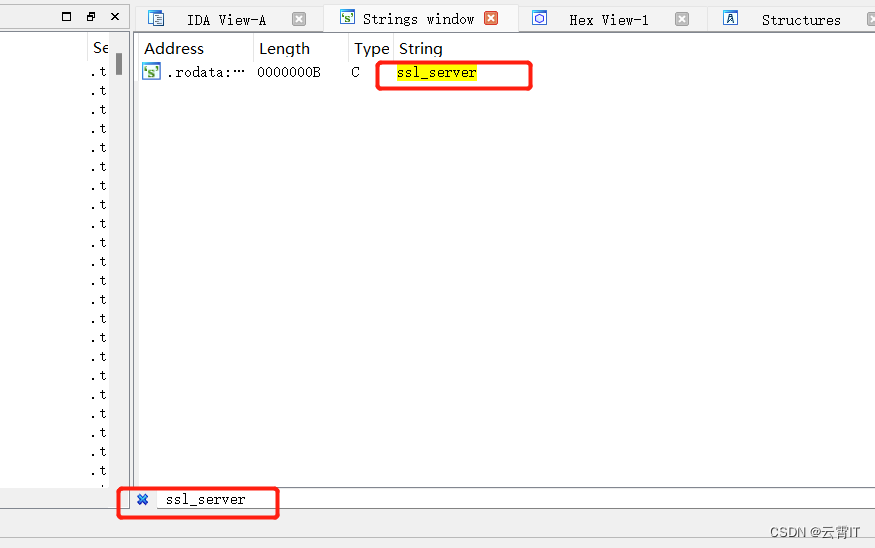
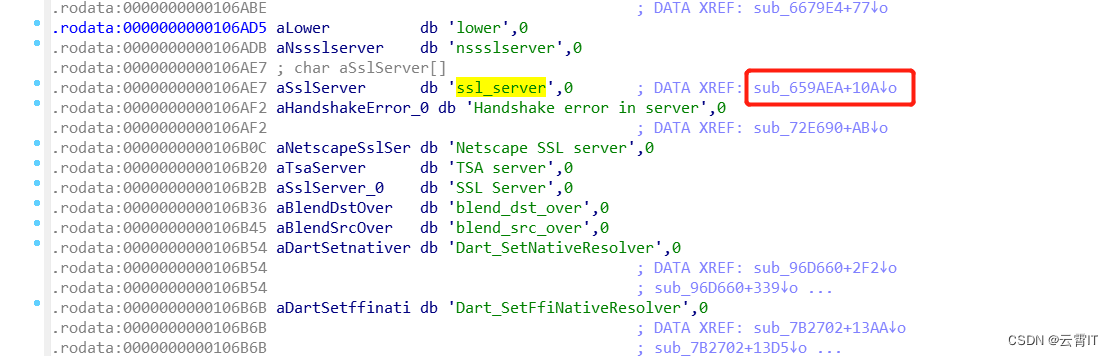
ssl证书校验在
libflutter.so中,拖进ide搜索字符串ssl_server,双击进去找到ssl_crypto_x509_session_verify_cert_chain函数的偏移地址进行hook掉;
hook代码如下:
function hook_ssl() {
Java.perform(function () {
var base = Module.findBaseAddress("libflutter.so");
var ssl_crypto_x509_session_verify_cert_chain = base.add(0x659AEA);
console.log("找到函数偏移地址:",ssl_crypto_x509_session_verify_cert_chain)
Interceptor.attach(ssl_crypto_x509_session_verify_cert_chain, {
onEnter: function(args) {
console.log("hook 开始!")
},
onLeave: function(retval) {
console.log("返回值: " + retval);
retval.replace(0x1);
console.log("解除ssl验证成功\n---------------------");
}
});
}
)};
setTimeout(hook_ssl,1690) // 设置延时找对hook时机(太快函数还没加载出来,太慢app已经发起请求了)
hook后,配合 Charles+Postern 即可抓到包。
二、dump出dart文件分析
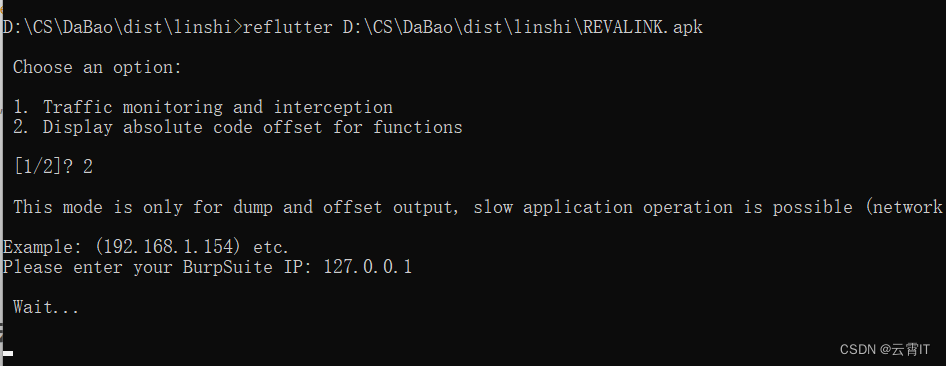
1、reflutter 工具
使用 reflutter 工具进行dump,解出dart文件
pip install reflutter==0.7.7
当前目录cmd运行以下代码,等待10几分钟重构apk
reflutter app.apk
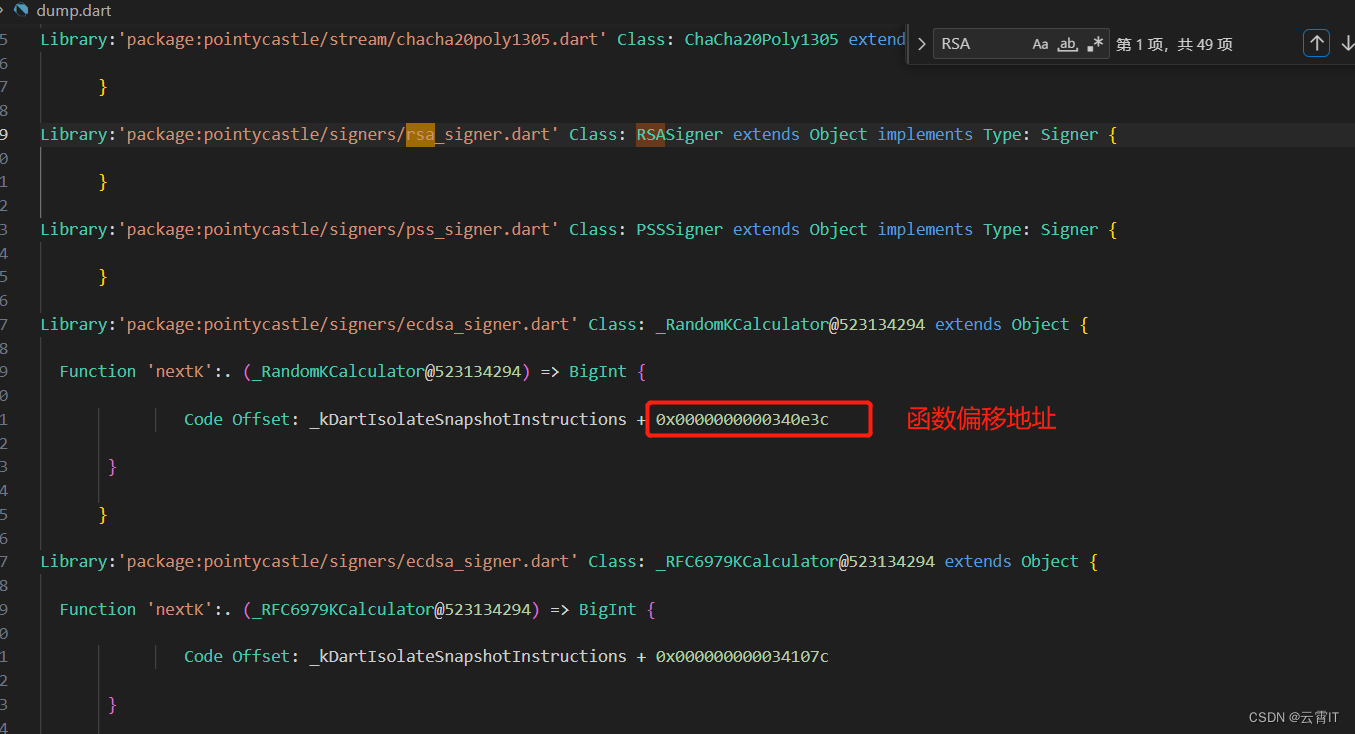
重构完成后会生成新的apk,把它安装到模拟器或者真机中并打开运行,此时系统会在
/data/data/包名/路径中生成dump.dart文件。使用下面语句把该文件提取到电脑当前目录
adb pull /data/data/包名/dump.dart
搜索md5、rsa、aes等关键字分析要破解的加密算法,使用frida进行hook可疑函数的偏移地址。搜索加密算法关键字没有头绪,可搜索含有
=> String关键字的函数进行hook(因为其返回的是字符串类型)
如果dart文件太长用python进行清洗,只保留方法(方便查看研究)
line_list = open('dump.dart','r').readlines()
result = ''
flag = False
for line in line_list:
if 'Function ' in line:
flag = True
if '}' in line:
flag = False
if flag == True:
result += line
if 'Code Offset' in line:
result += "}\n"
open('func.dart','w',encoding='utf-8').write(result)
print(result)
2、B(l)utter 工具
借助开源框架B(l)utter (https://github.com/worawit/blutter)进行dump出dart文件进行分析hook
,推荐使用Linux系统
git clone https://github.com/worawit/blutter --depth=1 # clone 下 blutter 的项目
sudo apt install python3-pyelftools python3-requests git cmake ninja-build \
build-essential pkg-config libicu-dev libcapstone-dev
执行下面之前把apk的arm64-v8a的所有文件复制到linux的/home/ubuntu/mydir/arm64-v8a目录下
python3 blutter.py /home/ubuntu/mydir/arm64-v8a out_dir
三、hook方法
hook可疑函数,打印输出调用栈,使用ide进行研究
var app = Module.findExportByName("libapp.so","_kDartIsolateSnapshotInstructions");
var Func = app.add(0x000000000000d2b0)
console.log("找到函数偏移地址:",Func)
Interceptor.attach(Func, {
onEnter: function(args) {
console.log('输出调用栈:\n' + Thread.backtrace(this.context, Backtracer.ACCURATE).map(DebugSymbol.fromAddress).join('\n') + '\n');
console.log("============================= 输入 ===============================","\n")
for(let i = 0; i < 8; i++) {
console.log("arg",i,": ", "\n");
try {
console.log(hexdump(args[i],{length: 0x130}), "\r\n");
} catch (error) {
console.log((args[i]), "\r\n");
}
}
},
onLeave: function(retval) {
console.log('输出调用栈:\n' + Thread.backtrace(this.context, Backtracer.ACCURATE).map(DebugSymbol.fromAddress).join('\n') + '\n');
console.log("============================= 结果 ===============================","\n")
try {
console.log(hexdump(retval,{length: 0x130}), "\r\n");
console.log("result:",ptr(retval).readCString());
} catch (error) {
console.log((retval), "\r\n");
}
}
});
四、Cheat Engine窥看(技巧篇)
如果上面方法还没能研究出啥,可试试这个办法。
Cheat Engine下载官网:https://cheatengine.org/downloads.php
待更新…
五、dart-sdk版本对照表
| version | Snapshot_Hash |
|---|---|
| 3.12.0 | 16ad76edd19b537bf6ea64fdd31977a7 |
| 3.11.0-0.1.pre | 36b0375d284ee2af0d0fffc6e6e48fde |
| 3.10.4 | 90b56a561f70cd55e972cb49b79b3d8b |
| 3.10.0 | aa64af18e7d086041ac127cc4bc50c5e |
| 3.7.12 | adb4292f3ec25074ca70abcd2d5c7251 |
| 3.7.0 | 501ef5cbd64ca70b6b42672346af6a8a |
| 3.3.10 | b6d0a1f034d158b0d37b51d559379697 |
| 3.3.0‑0.1.pre | b0e899ec5a90e4661501f0b69e9dd70f |
| 2.18.0.165 | 8e50e448b241be23b9e990094f4dca39 |
| 2.18.0.44 | 6a9b5a03a7e784a4558b10c769f188d9 |
| 2.17.0.stable | 1441d6b13b8623fa7fbf61433abebd31 |
| 2.17.0-182.2.beta | a0cb0c928b23bc17a26e062b351dc44d |
| 2.17.0-69.2.beta | ded6ef11c73fdc638d6ff6d3ad22a67b |
| 2.16.0-134.1.beta | d56742caf7b3b3f4bd2df93a9bbb5503 |
| 2.16.0-80.1.beta | 3318fe66091c0ffbb64faec39976cb7d |
| 2.8.0-3.1.pre | adf563436d12ba0d50ea5beb7f3be1bb |
| 2.7.0-3.0.pre | 24d9d411c2f90c8fbe8907f99e89d4b0 |
| 2.6.0-5.2.pre | f10776149bf76be288def3c2ca73bdc1 |
| 2.5.0 | 9cf77f4405212c45daf608e1cd646852 |
| 2.4.0 | 659a72e41e3276e882709901c27de33d |
| 2.3.0 | 7a5b240780941844bae88eca5dbaa7b8 |
| 2.2.0 | e4a09dbf2bb120fe4674e0576617a0dc |
| 2.2.0-10.1.pre | 34f6eec64e9371856eaaa278ccf56538 |
| 2.1.0-12.2.pre | 39a9141bbcc3cae43e6f9f6b7fbaafe3 |
| 2.0.6 | 5b97292b25f0a715613b7a28e0734f77 |
| 1.25.0-8.3.pre | 9e2165577cef0f0f70f9ff072107920c |
| 1.24.0-10.2.pre | a2bdb58c7edf9471da9180bf8185e7f7 |
| 1.23.0-18.1.pre | 953aa80d78c4d8886e3e4d784fd9d95f |
| 1.22.6 | 8ee4ef7a67df9845fba331734198a953 |
| 1.21.0-9.2.pre | 5f40b0a9f04b5018fa08a9b67fd316cd |
| 1.20.4 | 04645b6182fad3d68350d84669869ce5 |
| 1.20.0-7.2.pre | 8b2ca977d1d2920b9839d1b60eade6a7 |
| 1.19.0-4.3.pre | 59da07d9da5a83be4ce75b7913b63dbd |
| 1.18.0-11.1.pre | b58ead73b2c5dfec69565df469bba387 |
| 1.17.5 | be7d304ff826e2dfac63538e227c3cc5 |
| 1.17.1 | 74edb834fac3fcea79d7ac2d1d6f1fb2 |
| 1.17.0-dev.3.1 | 9e7cb7c9394c24c2398410b902673e13 |
| v1.15.17 | ee91a9191a5286c31d91a89754ba36af |
| v1.14.6 | e739779cc1d28f0f697a92f2daf5f10f |
| v1.13.6 | 81662522448cdd4d02eb060669e5d48b |
| v1.12.13+hotfix.9 | 20e5c4f7dc44368ac5a17643b93665f6 |
| v1.11.0 | 2fb364d659ea53f7892be9ba5e036047 |
| v1.10.7 | c3bbfe8f226120ad0569d7b78ed2d9ef |
| v1.9.1+hotfix.6 | c8562f0ee0ebc38ba217c7955956d1cb |
| v1.8.3 | 34948253b59d5a56b2ec161e17975a4e |
| v1.7.8+hotfix.4 | 1d7acad1540192ac459cf60344efb7c1 |
| v1.6.3 | c89592e3e4956c33956c8ba0f691dbd0 |
| v1.5.4-hotfix.2 | eed485c757fba5d731e4054412c99f2e |
| v1.4.9-hotfix.1 | f630ecdf457e27dd24d3b9e0a6bc1c13 |
| v1.3.8 | 9a66dcb2da955dffdbdb0eafa0288784 |
| v1.2.1 | 0c73eb70aa4d30f450273cb424be8c62 |
| v1.1.8 | 317d4c7e607b1fd7d682c0010aadf1d0 |
| v1.0.0 | 8343f188ada07642f47c56e518f1307c |