1、jeesite使用shrio来进项权限和认证处理。
2、创建自己的认证系统,将cas认证加载进来
import java.net.URLDecoder;
import java.util.Collection;
import java.util.HashMap;
import java.util.List;
import java.util.Map;
import org.apache.commons.lang3.StringUtils;
import org.apache.shiro.authc.AuthenticationException;
import org.apache.shiro.authc.AuthenticationInfo;
import org.apache.shiro.authc.AuthenticationToken;
import org.apache.shiro.authc.SimpleAuthenticationInfo;
import org.apache.shiro.authz.AuthorizationInfo;
import org.apache.shiro.authz.SimpleAuthorizationInfo;
import org.apache.shiro.cas.CasAuthenticationException;
import org.apache.shiro.cas.CasRealm;
import org.apache.shiro.cas.CasToken;
import org.apache.shiro.session.Session;
import org.apache.shiro.subject.PrincipalCollection;
import org.apache.shiro.subject.SimplePrincipalCollection;
import org.jasig.cas.client.authentication.AttributePrincipal;
import org.jasig.cas.client.validation.Assertion;
import org.jasig.cas.client.validation.TicketValidationException;
import org.jasig.cas.client.validation.TicketValidator;
import org.slf4j.Logger;
import org.slf4j.LoggerFactory;
import com.thinkgem.jeesite.common.config.Global;
import com.thinkgem.jeesite.common.utils.SpringContextHolder;
import com.thinkgem.jeesite.common.web.Servlets;
import com.thinkgem.jeesite.modules.sys.entity.Menu;
import com.thinkgem.jeesite.modules.sys.entity.Role;
import com.thinkgem.jeesite.modules.sys.entity.User;
import com.thinkgem.jeesite.modules.sys.security.SystemAuthorizingRealm.Principal;
import com.thinkgem.jeesite.modules.sys.service.SystemService;
import com.thinkgem.jeesite.modules.sys.utils.LogUtils;
import com.thinkgem.jeesite.modules.sys.utils.UserUtils;
public class CasLoginRealm extends CasRealm {
private Logger logger = LoggerFactory.getLogger(getClass());
private SystemService systemService;
/**
*
* @MethodName: doGetAuthenticationInfo
* @Description: 认证
* @param @param token
* @param @return
* @param @throws AuthenticationException
* @author
*/
@Override
protected AuthenticationInfo doGetAuthenticationInfo(
AuthenticationToken token) throws AuthenticationException {
CasToken casToken = (CasToken) token;
if (token == null) {
return null;
}
String ticket = (String)casToken.getCredentials();
if (!org.apache.shiro.util.StringUtils.hasText(ticket)) {
return null;
}
TicketValidator ticketValidator = ensureTicketValidator();
try {
// contact CAS server to validate service ticket
Assertion casAssertion = ticketValidator.validate(ticket, getCasService());
// get principal, user id and attributes
AttributePrincipal casPrincipal = casAssertion.getPrincipal();
String username = casPrincipal.getName();
logger.debug("Validate ticket : {} in CAS server : {} to retrieve user : {}", new Object[]{
ticket, getCasServerUrlPrefix(), username
});
User user = getSystemService().getUserByLoginName(username);
// refresh authentication token (user id + remember me)
casToken.setUserId(username);
// create simple authentication info
// PrincipalCollection principalCollection = new SimplePrincipalCollection(new SimplePrincipalCollection(new Principal(user, false), getName()), getName());
return new SimpleAuthenticationInfo(new SimplePrincipalCollection(new Principal(user, false), getName()), ticket);
} catch (TicketValidationException e) {
throw new CasAuthenticationException("Unable to validate ticket [" + ticket + "]", e);
}
}
/**
* 授权方案
*
*
* 在验证之后的授权信息
*/
@Override
protected AuthorizationInfo doGetAuthorizationInfo(
PrincipalCollection principals) {
Principal principal = (Principal) getAvailablePrincipal(principals);
// 获取当前已登录的用户
if (!Global.TRUE.equals(Global.getConfig("user.multiAccountLogin"))){
Collection<Session> sessions = getSystemService().getSessionDao().getActiveSessions(true, principal, UserUtils.getSession());
if (sessions.size() > 0){
// 如果是登录进来的,则踢出已在线用户
if (UserUtils.getSubject().isAuthenticated()){
for (Session session : sessions){
getSystemService().getSessionDao().delete(session);
}
}
// 记住我进来的,并且当前用户已登录,则退出当前用户提示信息。
else{
UserUtils.getSubject().logout();
throw new AuthenticationException("msg:账号已在其它地方登录,请重新登录。");
}
}
}
User user = getSystemService().getUserByLoginName(principal.getLoginName());
if (user != null) {
SimpleAuthorizationInfo info = new SimpleAuthorizationInfo();
List<Menu> list = UserUtils.getMenuList();
for (Menu menu : list){
if (StringUtils.isNotBlank(menu.getPermission())){
// 添加基于Permission的权限信息
for (String permission : StringUtils.split(menu.getPermission(),",")){
info.addStringPermission(permission);
}
}
}
// 添加用户权限
info.addStringPermission("user");
// 添加用户角色信息
for (Role role : user.getRoleList()){
info.addRole(role.getEnname());
}
// 更新登录IP和时间
getSystemService().updateUserLoginInfo(user);
// 记录登录日志
LogUtils.saveLog(Servlets.getRequest(), "系统登录");
return info;
} else {
return null;
}
}
/**
* 获取系统业务对象
*/
public SystemService getSystemService() {
if (systemService == null){
systemService = SpringContextHolder.getBean(SystemService.class);
}
return systemService;
}
/**
* 未使用客户端jar包 需要手动解析
*/
public Map<String,String> getSsoUserInfo(String str){
Map<String,String> map = new HashMap<String, String>();
String str2 = str.replaceAll(" ", "").replaceAll("\t|\n", "").replace("=[",",").replace("]", "").replace("{", "").replace("}", "");
String[] strs = str2.split(",");
try {
for (String strl : strs) {
if(strl.startsWith("NAME") && strl.length()>4){
map.put("NAME", URLDecoder.decode(strl.replace("NAME", ""), "UTF-8"));
}
if(strl.startsWith("LOGINNAME") && strl.length()>9){
map.put("LOGINNAME", URLDecoder.decode(strl.replace("LOGINNAME", ""), "UTF-8"));
}
}
} catch (Exception e) {
// TODO: handle exception
}
return map;
}
}
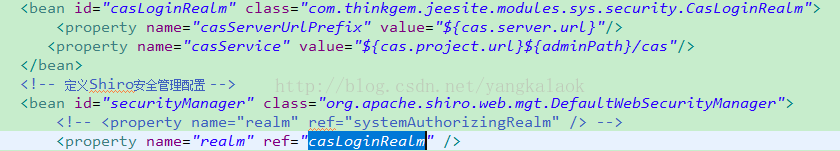
3、修改配置spring-context-shiro.xml
4、修改完成后我们直接访问项目首页,会跳转到cas登录入口,此时输入用户名和密码登录。
5、这个时候并不能完成登录,我们默认的用户名casuser,这是认证服务器的用户名,那这个用户名如何登录我们的系统呢?从代码中我们可以看到,cas认证通过的信息根据用户名,与系统中用户的登录名匹配,来加载用户信息。那么我们要改一下cas的登录名称,修改后再登录,便可使用该用户进入到系统。