邮件安全简介:
smtp pop3 imap
smtps
1. 465 (smtps)
2. Smtp+ssl (starttls)
为邮件服务器添加SMTPS 功能:
SMTPS:通过一个独立的端口向用户提供ssl/tls 加密的服务,监听端口:465。
STARTTLS:通过25 号端口同时提供加密/不加密的功能。
s/mimp gpg
pop3-àpop3s
认证:sasl
[root@mail ~]# sendmail -d0.1 –bv #查看sendmail的详细信息,查看sendmail 是否支持startls 功能(取决于二进制程序在编译的时候是否将startls 功能添加进去),若存在STARTTLS,说明支持发送加密。
NETUNIX NEWDB NIS PIPELINING SASLv2 SCANF SOCKETMAP STARTTLS
[root@mail ~]# telnet 127.0.0.1 25
Trying 127.0.0.1...
Connected to mail.bj.com (127.0.0.1).
Escape character is '^]'.
220 mail.bj.com ESMTP Sendmail 8.13.8/8.13.8; Fri, 23 Mar 2012 16:16:04 +0800
EHLO 127.0.0.1
250-mail.bj.com Hello mail.bj.com [127.0.0.1], pleased to meet you
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-8BITMIME
250-SIZE
250-DSN
250-ETRN
250-DELIVERBY
250 HELP
quit
221 2.0.0 mail.bj.com closing connection
Connection closed by foreign host.
可以看到:不存在STARTTLS选项!说明不支持加密!需要进行配置,具体参考下面的资料:
邮件系统的基本配置请参考博主文章:http://111222333.blog.51cto.com/4628697/989029
一:使sendmail与CA结合实现发送加密:
① ,为CA创建证书:
[root@ftp ~]# cd /etc/pki/
[root@ftp pki]# ll
[root@ftp pki]# vim tls/openssl.cnf
45 dir = /etc/pki/CA
88 countryName = optional
89 stateOrProvinceName = optional
90 organizationName = optional
[root@ftp pki]# cd CA/
[root@ftp CA]# mkdir certs newcerts crl
[root@ftp CA]# touch index.txt serial
[root@ftp CA]# echo "01" >serial
[root@ftp CA]# ll
[root@ftp CA]# openssl genrsa 1024 > private/cakey.pem
Generating RSA private key, 1024 bit long modulus
...........++++++
....++++++
e is 65537 (0x10001)
[root@ftp CA]# chmod 600 private/cakey.pem
[root@ftp CA]# ll private/cakey.pem
-rw------- 1 root root 887 Feb 10 23:22 private/cakey.pem
[root@ftp CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 888
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:cn
State or Province Name (full name) [Berkshire]:henan
Locality Name (eg, city) [Newbury]:zhengzhou
Organization Name (eg, company) [My Company Ltd]:junjie
Organizational Unit Name (eg, section) []:soft
Common Name (eg, your name or your server's hostname) []:ca.junjie.com
Email Address []:[email protected]
[root@ftp CA]#ll
[root@ftp CA]#chmod 600 cacert.pem
[root@ftp CA]#ll
② ,为sendmail服务器,签发证书:
[root@mail CA]# mkdir /etc/mail/certs
[root@mail CA]# cd /etc/mail/certs
[root@mail certs]# openssl genrsa 1024 >sendmail.key
Generating RSA private key, 1024 bit long modulus
.................................++++++
...........++++++
e is 65537 (0x10001)
[root@mail certs]# openssl req -new -key sendmail.key -out sendmail.csr
Country Name (2 letter code) [GB]:cn
State or Province Name (full name) [Berkshire]:henan
Locality Name (eg, city) [Newbury]:zhengzhou
Organization Name (eg, company) [My Company Ltd]:junjie
Organizational Unit Name (eg, section) []:tec
Common Name (eg, your name or your server's hostname) []:mail.bj.com
Email Address []:[email protected]
[root@mail certs]# openssl ca -in sendmail.csr -out sendmail.crt
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
[root@mail certs]# chmod 600 *
[root@mail certs]# ll
total 12
-rw------- 1 root root 3214 Mar 23 16:35 sendmail.crt
-rw------- 1 root root 688 Mar 23 16:32 sendmail.csr
-rw------- 1 root root 887 Mar 23 16:30 sendmail.key
③ :使sendmail服务使用证书功能
三个所需文件已经准备完毕,到此,证书已经申请成功,下面开始修改配置文件/etc/mail/sendmail.mc:以使sendmail服务使用证书功能
[root@mail certs]# cd /etc/mail/certs/
[root@mail certs]# cp /etc/pki/CA/cacert.pem .
[root@mail certs]# vim /etc/mail/sendmail.mc
21 define(`confLOG_LEVEL', `9')dnl
60 define(`confCACERT_PATH', `/etc/mail/certs')dnl
61 define(`confCACERT', `/etc/mail/certs/cacert.pem')dnl
62 define(`confSERVER_CERT', `/etc/mail/certs/sendmail.crt')dnl
63 define(`confSERVER_KEY', `/etc/mail/certs/sendmail.key')dnl
134 DAEMON_OPTIONS(`Port=smtps, Name=TLSMTA, M=s')dnl
保存,重启服务。line 134 监听smtps(465)端口;打开日志功能line21
[root@mail certs]# service sendmail restart
Shutting down sm-client: [ OK ]
Shutting down sendmail: [ OK ]
Starting sendmail: [ OK ]
Starting sm-client: [ OK ]
④ :使用telnet测试一下
[root@mail certs]# telnet mail.bj.com 25
Trying 127.0.0.1...
Connected to localhost.localdomain (127.0.0.1).
Escape character is '^]'.
220 mail.bj.com ESMTP Sendmail 8.13.8/8.13.8; Fri, 23 Mar 2012 16:54:22 +0800
EHLO mail.bj.com
250-mail.bj.com Hello mail.bj.com [127.0.0.1], pleased to meet you
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-8BITMIME
250-SIZE
250-DSN
250-ETRN
250-STARTTLS
250-DELIVERBY
250 HELP
quit
221 2.0.0 mail.bj.com closing connection
Connection closed by foreign host.
再次可以看到:存在有STARTTLS功能了!说明可以支持加密了!
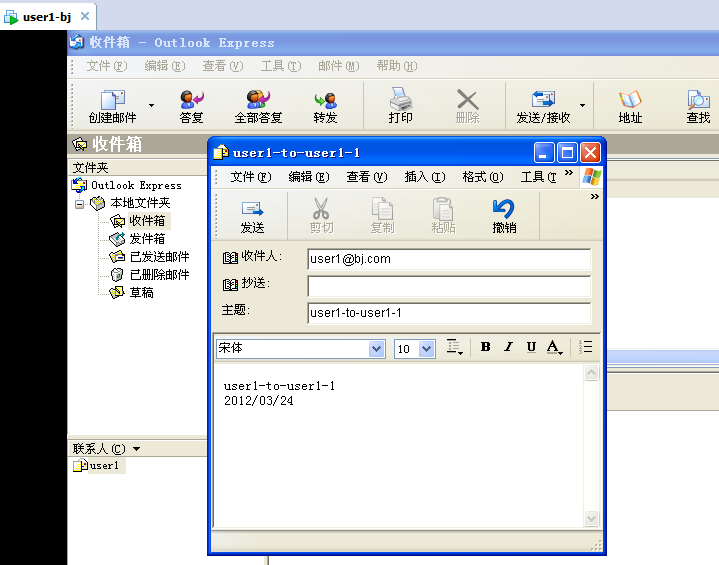
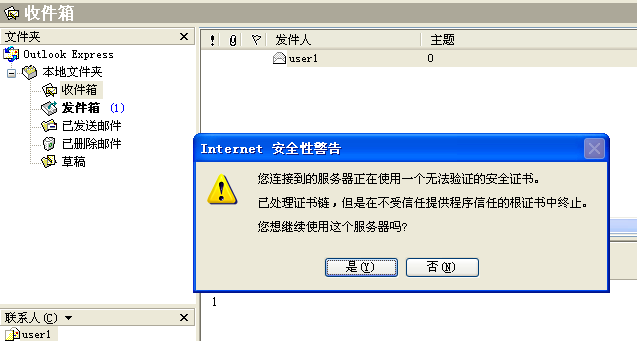
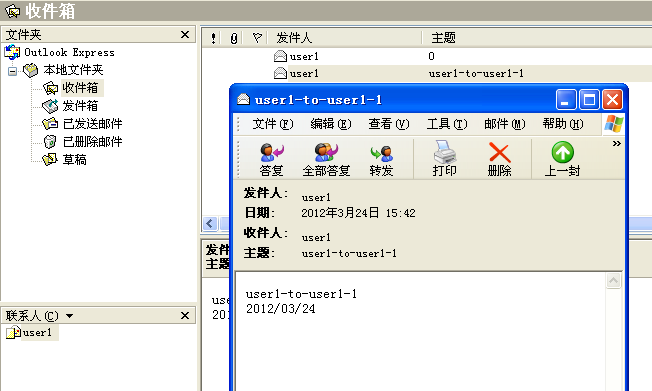
⑤ :使用windows 上的outlook Express 进行发信测试:
日志分析:
[root@mail ~]# tail -f /var/log/maillog
Mar 23 17:50:17 mail sendmail[3129]: STARTTLS=server, relay=[10.106.6.200], version=TLSv1/SSLv3, verify=NO, cipher=RC4-MD5, bits=128/128
Mar 23 17:50:57 mail sendmail[3129]: q2N9oHfJ003129: from=<[email protected]>, size=1306, class=0, nrcpts=1, msgid=<006001cd0991$d178b870$c8066a0a@hp3aea877158e2>, proto=SMTP, daemon=MTA, relay=[10.106.6.200]
Mar 23 17:50:57 mail sendmail[3132]: q2N9oHfJ003129: to=<[email protected]>, ctladdr=<[email protected]> (500/500), delay=00:00:00, xdelay=00:00:00, mailer=local, pri=31528, dsn=2.0.0, stat=Sent
Mar 23 17:51:07 mail dovecot: pop3-login: Login: user=<user1>, method=PLAIN, rip=::ffff:10.106.6.200, lip=::ffff:10.106.6.254
Mar 23 17:51:07 mail dovecot: POP3(user1): Disconnected: Logged out top=0/0, retr=1/1608, del=1/1, size=1591
二:使dovecot与CA结合实现接收加密:
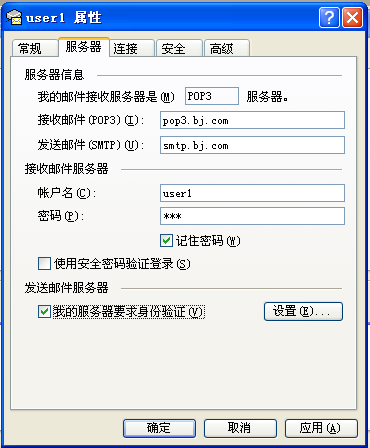
#为dovecot 增加SSL 功能:pop3---->pop3s imap-----> imaps
[root@mail ~]# yum install -y wireshark
[root@mail ~]# tshark -ni eth0 -R "tcp.dstport eq 110"
Running as user "root" and group "root". This could be dangerous.
Capturing on eth0
183.544764 10.106.6.200 -> 10.106.6.254 TCP 1116 > 110 [SYN] Seq=0 Win=64240 Len=0 MSS=1460
183.546267 10.106.6.200 -> 10.106.6.254 TCP 1116 > 110 [ACK] Seq=1 Ack=1 Win=64240 Len=0
183.548706 10.106.6.200 -> 10.106.6.254 POP Request: USER user1
183.562924 10.106.6.200 -> 10.106.6.254 POP Request: PASS 123
183.578535 10.106.6.200 -> 10.106.6.254 POP Request: STAT
183.586984 10.106.6.200 -> 10.106.6.254 POP Request: LIST
183.593295 10.106.6.200 -> 10.106.6.254 POP Request: RETR 1
183.594018 10.106.6.200 -> 10.106.6.254 TCP 1116 > 110 [ACK] Seq=43 Ack=1693 Win=64240 Len=0
183.642729 10.106.6.200 -> 10.106.6.254 POP Request: DELE 1
183.651676 10.106.6.200 -> 10.106.6.254 POP Request: QUIT
183.672294 10.106.6.200 -> 10.106.6.254 TCP 1116 > 110 [ACK] Seq=57 Ack=1757 Win=64177 Len=0
183.674327 10.106.6.200 -> 10.106.6.254 TCP 1116 > 110 [FIN, ACK] Seq=57 Ack=1757 Win=64177 Len=0
12 packets captured
① ,为dovecot服务器,签发证书:
[root@mail ~]# mkdir -pv /etc/dovecot/certs
mkdir: created directory `/etc/dovecot'
mkdir: created directory `/etc/dovecot/certs'
[root@mail ~]# cd /etc/dovecot/certs
[root@mail certs]#openssl genrsa 1024 >dovecot.key
Generating RSA private key, 1024 bit long modulus
.++++++
........................................++++++
e is 65537 (0x10001)
[root@mail certs]# openssl req -new -key dovecot.key -out dovecot.csr
Country Name (2 letter code) [GB]:cn
State or Province Name (full name) [Berkshire]:henan
Locality Name (eg, city) [Newbury]:zhengzhou
Organization Name (eg, company) [My Company Ltd]:junjie
Organizational Unit Name (eg, section) []:tec
Common Name (eg, your name or your server's hostname) []:pop3.bj.com
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@mail certs]# openssl ca -in dovecot.csr -out dovecot.crt
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
[root@mail certs]# chmod 600 *
[root@mail certs]# ll
total 12
-rw------- 1 root root 3214 Mar 23 18:02 dovecot.crt
-rw------- 1 root root 688 Mar 23 18:01 dovecot.csr
-rw------- 1 root root 887 Mar 23 17:59 dovecot.key
② ,使dovecot服务使用证书:
#修改/etc/dovecot.conf : 使dovecot服务使用证书。
[root@mail certs]# vim /etc/dovecot.conf
21 protocols = imap imaps pop3 pop3s
92 ssl_cert_file = /etc/dovecot/certs/dovecot.crt
93 ssl_key_file = /etc/dovecot/certs/dovecot.key
[root@mail certs]# service dovecot restart
Stopping Dovecot Imap: [ OK ]
Starting Dovecot Imap: [ OK ]
[root@mail certs]# netstat -tupln |grep dovecot
tcp 0 0 :::993 :::* LISTEN 3243/dovecot
tcp 0 0 :::995 :::* LISTEN 3243/dovecot
tcp 0 0 :::110 :::* LISTEN 3243/dovecot
tcp 0 0 :::143 :::* LISTEN 3243/dovecot
③ ,windows客户端使用telnet mail.bj.com 110 访问
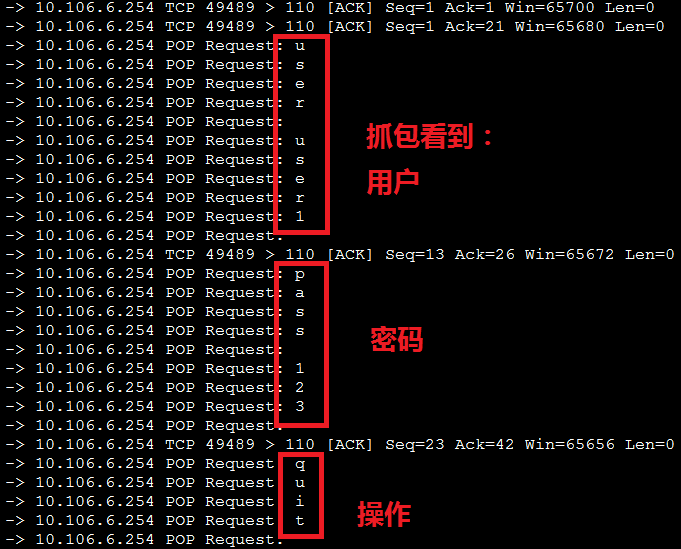
在linux下抓包分析:
[root@mail ~]# tshark -ni eth0 -R "tcp.dstport eq 110"
Running as user "root" and group "root". This could be dangerous.
Capturing on eth0
23.370858 10.106.6.190 -> 10.106.6.254 TCP 49489 > 110 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=2
23.371917 10.106.6.190 -> 10.106.6.254 TCP 49489 > 110 [ACK] Seq=1 Ack=1 Win=65700 Len=0
23.580864 10.106.6.190 -> 10.106.6.254 TCP 49489 > 110 [ACK] Seq=1 Ack=21 Win=65680 Len=0
36.262463 10.106.6.190 -> 10.106.6.254 POP Request: u
36.727270 10.106.6.190 -> 10.106.6.254 POP Request: s
37.462057 10.106.6.190 -> 10.106.6.254 POP Request: e
37.763750 10.106.6.190 -> 10.106.6.254 POP Request: r
39.832685 10.106.6.190 -> 10.106.6.254 POP Request:
40.969481 10.106.6.190 -> 10.106.6.254 POP Request: u
41.706240 10.106.6.190 -> 10.106.6.254 POP Request: s
41.979005 10.106.6.190 -> 10.106.6.254 POP Request: e
42.228525 10.106.6.190 -> 10.106.6.254 POP Request: r
44.641612 10.106.6.190 -> 10.106.6.254 POP Request: 1
45.863993 10.106.6.190 -> 10.106.6.254 POP Request:
46.063984 10.106.6.190 -> 10.106.6.254 TCP 49489 > 110 [ACK] Seq=13 Ack=26 Win=65672 Len=0
47.656999 10.106.6.190 -> 10.106.6.254 POP Request: p
48.277840 10.106.6.190 -> 10.106.6.254 POP Request: a
48.687710 10.106.6.190 -> 10.106.6.254 POP Request: s
48.903481 10.106.6.190 -> 10.106.6.254 POP Request: s
52.138586 10.106.6.190 -> 10.106.6.254 POP Request:
52.642241 10.106.6.190 -> 10.106.6.254 POP Request: 1
52.945620 10.106.6.190 -> 10.106.6.254 POP Request: 2
53.309236 10.106.6.190 -> 10.106.6.254 POP Request: 3
54.483545 10.106.6.190 -> 10.106.6.254 POP Request:
54.743086 10.106.6.190 -> 10.106.6.254 TCP 49489 > 110 [ACK] Seq=23 Ack=42 Win=65656 Len=0
61.181050 10.106.6.190 -> 10.106.6.254 POP Request: q
61.668851 10.106.6.190 -> 10.106.6.254 POP Request: u
61.743819 10.106.6.190 -> 10.106.6.254 POP Request: i
61.991869 10.106.6.190 -> 10.106.6.254 POP Request: t
62.323933 10.106.6.190 -> 10.106.6.254 POP Request:
62.326107 10.106.6.190 -> 10.106.6.254 TCP 49489 > 110 [ACK] Seq=29 Ack=61 Win=65640 Len=0
62.336106 10.106.6.190 -> 10.106.6.254 TCP 49489 > 110 [FIN, ACK] Seq=29 Ack=61 Win=65640 Len=0
32 packets captured
[root@mail ~]#
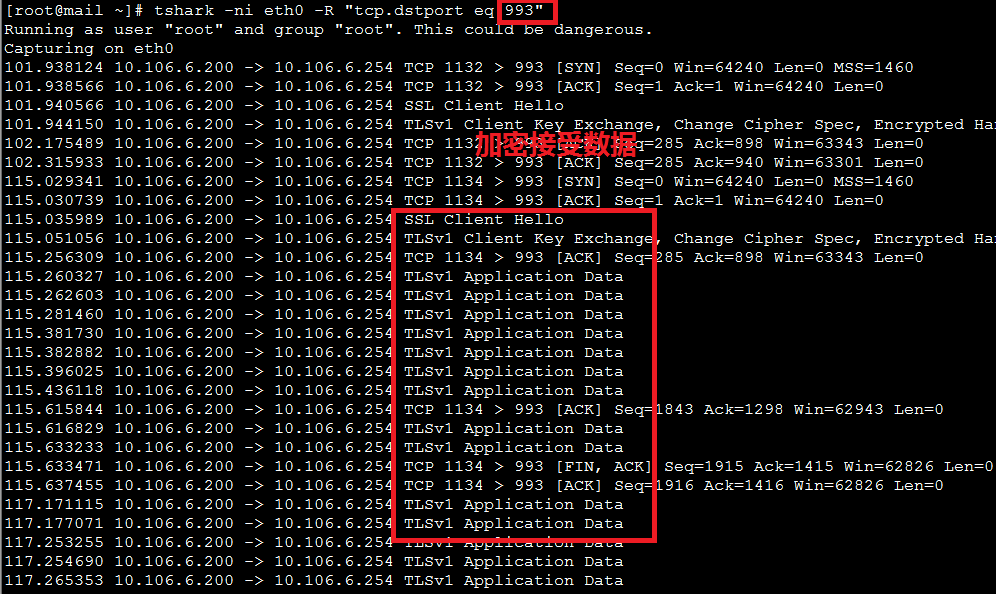
④ ,windows客户端使用telnet mail.bj.com 993 访问
在linux下抓包分析:
[root@mail ~]# tail -f /var/log/maillog
Mar 24 16:34:47 mail dovecot: imap-login: Disconnected: rip=::ffff:10.106.6.190, lip=::ffff:10.106.6.254, TLS handshake
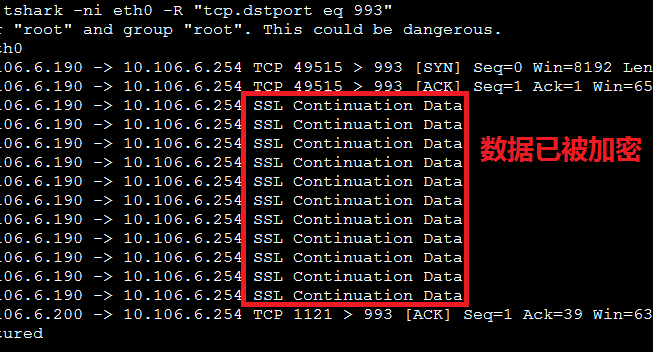
[root@mail ~]# tshark -ni eth0 -R "tcp.dstport eq 993"
Running as user "root" and group "root". This could be dangerous.
Capturing on eth0
7.758613 10.106.6.190 -> 10.106.6.254 TCP 49515 > 993 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=2
7.758832 10.106.6.190 -> 10.106.6.254 TCP 49515 > 993 [ACK] Seq=1 Ack=1 Win=65700 Len=0
78.938576 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
80.415623 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
81.063027 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
81.555095 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
82.209324 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
83.062545 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
83.561624 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
84.147630 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
84.538105 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
85.637208 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
86.519913 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
92.840161 10.106.6.200 -> 10.106.6.254 TCP 1121 > 993 [ACK] Seq=1 Ack=39 Win=63341 Len=0
⑤ ,windows客户端使用telnet mail.bj.com 995 访问
在linux下抓包分析:
[root@mail ~]# tail -f /var/log/maillog
Mar 24 16:39:36 mail dovecot: pop3-login: Disconnected: rip=::ffff:10.106.6.190, lip=::ffff:10.106.6.254, TLS handshake
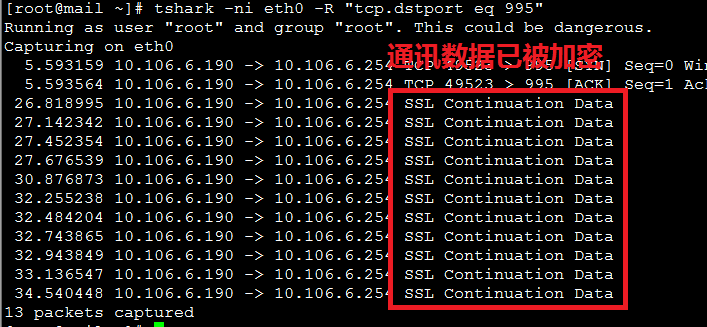
[root@mail ~]# tshark -ni eth0 -R "tcp.dstport eq 995"
Running as user "root" and group "root". This could be dangerous.
Capturing on eth0
5.593159 10.106.6.190 -> 10.106.6.254 TCP 49523 > 995 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=2
5.593564 10.106.6.190 -> 10.106.6.254 TCP 49523 > 995 [ACK] Seq=1 Ack=1 Win=65700 Len=0
26.818995 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
27.142342 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
27.452354 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
27.676539 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
30.876873 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
32.255238 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
32.484204 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
32.743865 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
32.943849 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
33.136547 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
34.540448 10.106.6.190 -> 10.106.6.254 SSL Continuation Data
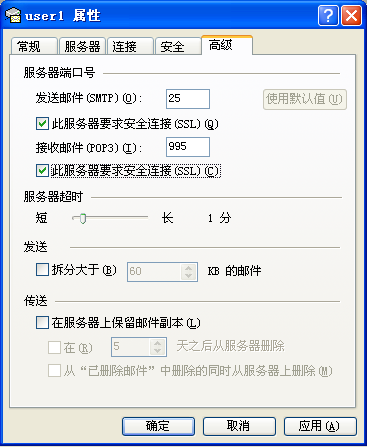
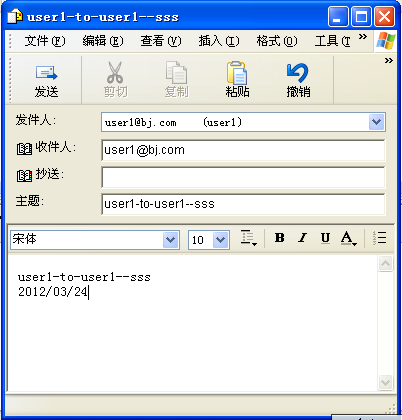
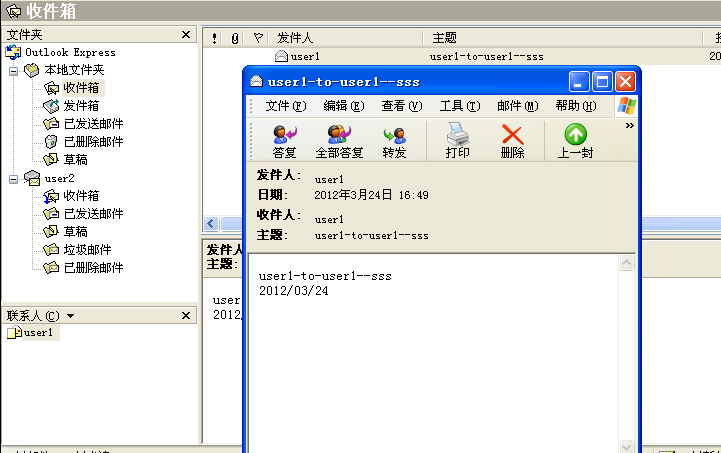
⑥ ,windows客户端使用outlook express 访问,使用995端口
[root@mail ~]# tail -f /var/log/maillog
Mar 24 16:49:51 mail sendmail[3520]: STARTTLS=server, relay=[10.106.6.200], version=TLSv1/SSLv3, verify=NO, cipher=RC4-MD5, bits=128/128
Mar 24 16:49:51 mail sendmail[3520]: q2O8npGW003520: from=<[email protected]>, size=1317, class=0, nrcpts=1, msgid=<00b001cd099b$0411aae0$c8066a0a@hp3aea877158e2>, proto=SMTP, daemon=MTA, relay=[10.106.6.200]
Mar 24 16:49:52 mail sendmail[3521]: q2O8npGW003520: to=<[email protected]>, ctladdr=<[email protected]> (500/500), delay=00:00:01, xdelay=00:00:00, mailer=local, pri=31539, dsn=2.0.0, stat=Sent
Mar 24 16:50:31 mail dovecot: pop3-login: Login: user=<user1>, method=PLAIN, rip=::ffff:10.106.6.200, lip=::ffff:10.106.6.254, TLS
Mar 24 16:50:31 mail dovecot: POP3(user1): Disconnected: Logged out top=0/0, retr=1/1619, del=1/1, size=1602
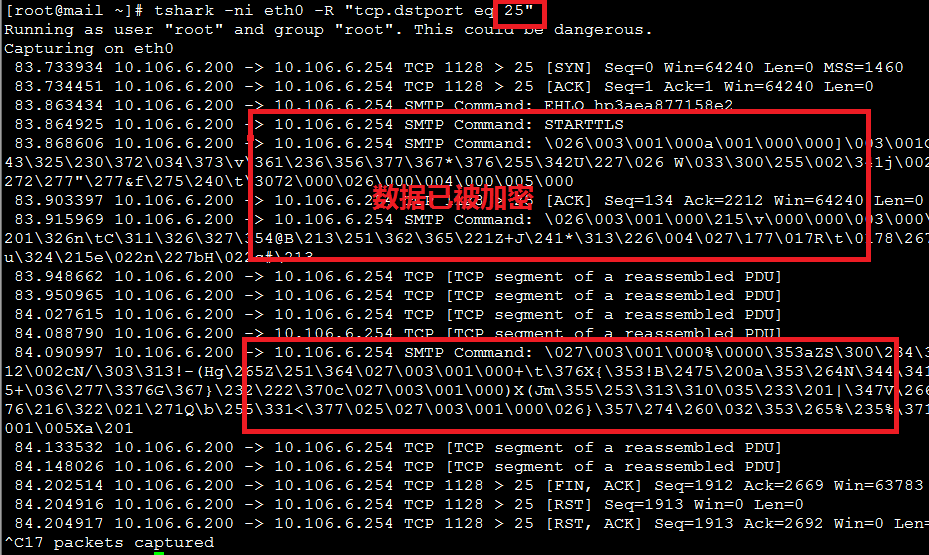
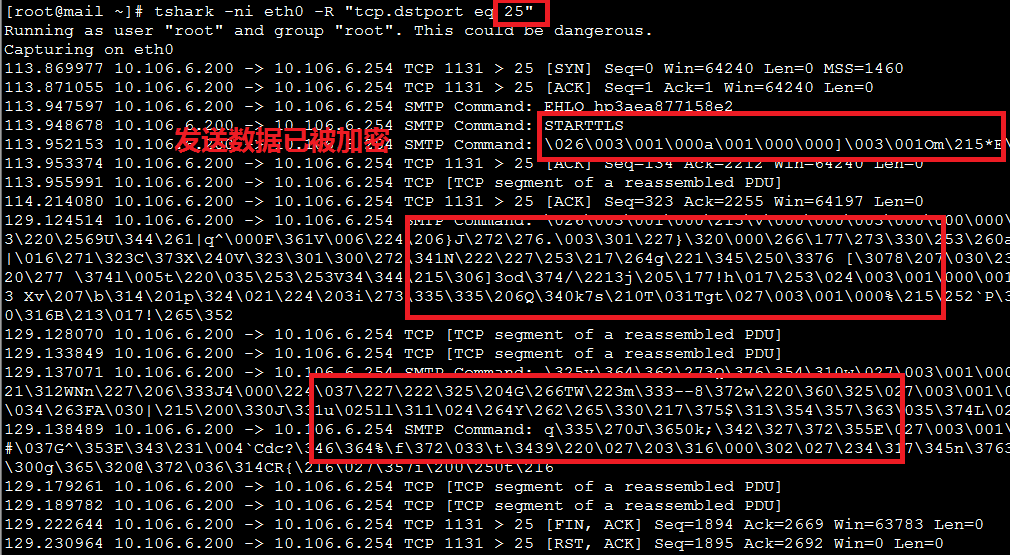
[root@mail ~]# tshark -ni eth0 -R "tcp.dstport eq 25"
Running as user "root" and group "root". This could be dangerous.
Capturing on eth0
83.733934 10.106.6.200 -> 10.106.6.254 TCP 1128 > 25 [SYN] Seq=0 Win=64240 Len=0 MSS=1460
83.734451 10.106.6.200 -> 10.106.6.254 TCP 1128 > 25 [ACK] Seq=1 Ack=1 Win=64240 Len=0
83.863434 10.106.6.200 -> 10.106.6.254 SMTP Command: EHLO hp3aea877158e2
83.864925 10.106.6.200 -> 10.106.6.254 SMTP Command: STARTTLS
83.868606 10.106.6.200 -> 10.106.6.254 SMTP Command: \026\003\001\000a\001\000\000]\003\001Om\212\225\177\2448\033\244\377\245!\336\243\325\230\372\034\373\v\361\236\356\377\367*\376\255\342U\227\026 W\033\300\255\002\341j\002\333c\232$\356\331\376\373\214\217Y{\234\272\277"\277&f\275\240\t\3072\000\026\000\004\000\005\000
83.903397 10.106.6.200 -> 10.106.6.254 TCP 1128 > 25 [ACK] Seq=134 Ack=2212 Win=64240 Len=0
83.915969 10.106.6.200 -> 10.106.6.254 SMTP Command: \026\003\001\000\215\v\000\000\003\000\000\000\020\000\000\202\000\200\276\224:\201\326n\tC\311\326\327\354@B\213\251\362\365\221Z+J\241*\313\226\004\027\177\017R\t\0178\267{\217\314O\337Q2ckX\316E\017\177\216\364&u\324\215e\022n\227bH\022c#\213
83.948662 10.106.6.200 -> 10.106.6.254 TCP [TCP segment of a reassembled PDU]
83.950965 10.106.6.200 -> 10.106.6.254 TCP [TCP segment of a reassembled PDU]
84.027615 10.106.6.200 -> 10.106.6.254 TCP [TCP segment of a reassembled PDU]
84.088790 10.106.6.200 -> 10.106.6.254 TCP [TCP segment of a reassembled PDU]
84.090997 10.106.6.200 -> 10.106.6.254 SMTP Command: \027\003\001\000%\0000\353aZS\300\234\315w\216\366y\t+\355\241\257\277\312\201\312\002cN/\303\313!-(Hg\265Z\251\364\027\003\001\000+\t\376X{\353!B\2475\200a\353\264N\344\341!\260\3061\375PS{\232\025\347\313\2601\245+\036\277\3376G\367}\232\222\370c\027\003\001\000)X(Jm\355\253\313\310\035\233\201|\347V\266\242\354^\adU\327\201\314\017\345\304.`\276\216\322\021\271Q\b\255\331<\377\025\027\003\001\000\026}\357\274\260\032\353\265%\235%\371:0_\256\222\016\352\203\036\346\\027\003\001\005Xa\201
84.133532 10.106.6.200 -> 10.106.6.254 TCP [TCP segment of a reassembled PDU]
84.148026 10.106.6.200 -> 10.106.6.254 TCP [TCP segment of a reassembled PDU]
84.202514 10.106.6.200 -> 10.106.6.254 TCP 1128 > 25 [FIN, ACK] Seq=1912 Ack=2669 Win=63783 Len=0
84.204916 10.106.6.200 -> 10.106.6.254 TCP 1128 > 25 [RST] Seq=1913 Win=0 Len=0
84.204917 10.106.6.200 -> 10.106.6.254 TCP 1128 > 25 [RST, ACK] Seq=1913 Ack=2692 Win=0 Len=0
^C17 packets captured
[root@mail ~]#
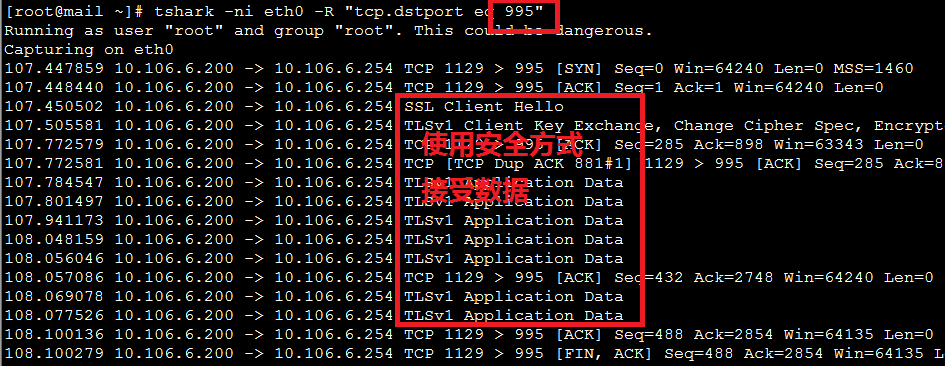
[root@mail ~]# tshark -ni eth0 -R "tcp.dstport eq 995"
Running as user "root" and group "root". This could be dangerous.
Capturing on eth0
107.447859 10.106.6.200 -> 10.106.6.254 TCP 1129 > 995 [SYN] Seq=0 Win=64240 Len=0 MSS=1460
107.448440 10.106.6.200 -> 10.106.6.254 TCP 1129 > 995 [ACK] Seq=1 Ack=1 Win=64240 Len=0
107.450502 10.106.6.200 -> 10.106.6.254 SSL Client Hello
107.505581 10.106.6.200 -> 10.106.6.254 TLSv1 Client Key Exchange, Change Cipher Spec, Encrypted Handshake Message
107.772579 10.106.6.200 -> 10.106.6.254 TCP 1129 > 995 [ACK] Seq=285 Ack=898 Win=63343 Len=0
107.772581 10.106.6.200 -> 10.106.6.254 TCP [TCP Dup ACK 881#1] 1129 > 995 [ACK] Seq=285 Ack=898 Win=63343 Len=0
107.784547 10.106.6.200 -> 10.106.6.254 TLSv1 Application Data
107.801497 10.106.6.200 -> 10.106.6.254 TLSv1 Application Data
107.941173 10.106.6.200 -> 10.106.6.254 TLSv1 Application Data
108.048159 10.106.6.200 -> 10.106.6.254 TLSv1 Application Data
108.056046 10.106.6.200 -> 10.106.6.254 TLSv1 Application Data
108.057086 10.106.6.200 -> 10.106.6.254 TCP 1129 > 995 [ACK] Seq=432 Ack=2748 Win=64240 Len=0
108.069078 10.106.6.200 -> 10.106.6.254 TLSv1 Application Data
108.077526 10.106.6.200 -> 10.106.6.254 TLSv1 Application Data
108.100136 10.106.6.200 -> 10.106.6.254 TCP 1129 > 995 [ACK] Seq=488 Ack=2854 Win=64135 Len=0
108.100279 10.106.6.200 -> 10.106.6.254 TCP 1129 > 995 [FIN, ACK] Seq=488 Ack=2854 Win=64135 Len=0
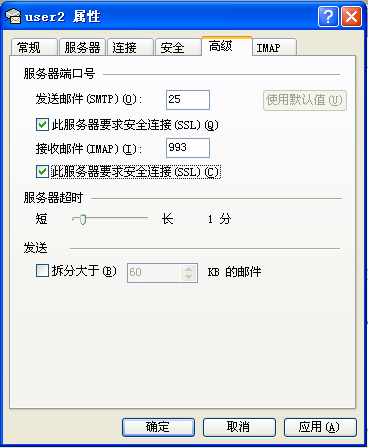
⑦ ,windows客户端使用outlook express 访问,使用993端口
三:使sendmail启用认证功能:
为邮件服务器提供SASL 功能:默认已经安装。
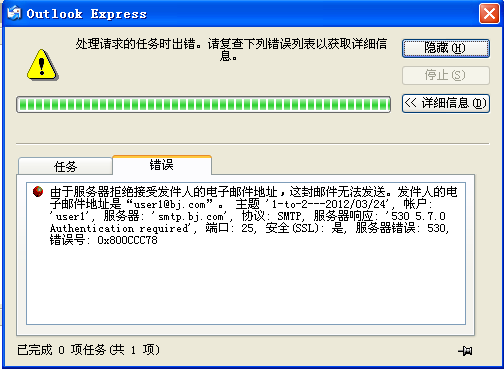
①:使用telnet 127.0.0.1 25进行简单测试:
以下:没有250认证功能
[root@mail certs]# telnet 127.0.0.1 25
EHLO 127.0.0.1
250-mail.bj.com Hello mail.bj.com [127.0.0.1], pleased to meet you
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-8BITMIME
250-SIZE
250-DSN
250-ETRN
250-STARTTLS
250-DELIVERBY
250 HELP
mail from:[email protected]
250 2.1.0 [email protected]... Sender ok
rcpt to:[email protected]
250 2.1.5 [email protected]... Recipient ok
DATA
354 Enter mail, end with "." on a line by itself
123.
.
250 2.0.0 q2O9MwGr003612 Message accepted for delivery
Quit
[root@mail certs]# su - user1
[user1@mail ~]$ mail
Mail version 8.1 6/6/93. Type ? for help.
"/var/spool/mail/user1": 2 messages 1 new
1 [email protected] Fri Mar 23 17:40 13/542 "DON'T DELETE THIS MESSAGE -- FOLDER INTERNAL DATA"
>N 2 [email protected] Sat Mar 24 17:24 11/344
& 2
Message 2:
From [email protected] Sat Mar 24 17:24:15 2012
Date: Sat, 24 Mar 2012 17:22:58 +0800
From: [email protected]
123.
日志显示发送成功:
Mar 24 17:24:15 mail sendmail[3612]: q2O9MwGr003612: [email protected], size=5, class=0, nrcpts=1, msgid=<[email protected]>, proto=ESMTP, daemon=MTA, relay=mail.bj.com [127.0.0.1]
Mar 24 17:24:15 mail sendmail[3615]: q2O9MwGr003612: [email protected], delay=00:00:29, xdelay=00:00:00, mailer=local, pri=30293, dsn=2.0.0, stat=Sent
②:安装SASL 功能:默认已经安装,并启动saslauthd服务。
SASL (简单认证安全层)服务为:saslauthd
需要安装的软件包为:
cyrus-sasl-2.1.22-4.i386.rpm
[root@mail certs]# rpm -qa |grep sasl
cyrus-sasl-plain-2.1.22-4
cyrus-sasl-2.1.22-4
cyrus-sasl-lib-2.1.22-4
cyrus-sasl-devel-2.1.22-4
#查看已经安装了相关软件包。
[root@mail certs]# chkconfig saslauthd on
[root@mail certs]# chkconfig --list saslauthd
saslauthd 0:off 1:off 2:on 3:on 4:on 5:on 6:off
[root@mail certs]# service saslauthd start
Starting saslauthd: [ OK ]
③:配置sendmail的主配置文档/etc/mail/sendmail.mc 启用认证功能。
[root@mail ~]# cd /etc/mail/
[root@mail mail]# vim sendmail.mc
39 define(`confAUTH_OPTIONS', `A y')dnl
52 TRUST_AUTH_MECH(`EXTERNAL DIGEST-MD5 CRAM-MD5 LOGIN PLAIN')dnl
53 define(`confAUTH_MECHANISMS', `EXTERNAL GSSAPI DIGEST-MD5 CRAM-MD5 LOGIN PLAIN')dnl
116DAEMON_OPTIONS(`Port=smtp,Addr=0.0.0.0, name=MTA,M=Ea')dnl
[root@mail mail]# service sendmail restart
Shutting down sm-client: [ OK ]
Shutting down sendmail: [ OK ]
Starting sendmail: [ OK ]
Starting sm-client: [ OK ]
④:在linux上使用telnet mail.bj.com 25测试认证。
[root@mail mail]# telnet mail.bj.com 25
Trying 127.0.0.1...
Connected to localhost.localdomain (127.0.0.1).
Escape character is '^]'.
220 mail.bj.com ESMTP Sendmail 8.13.8/8.13.8; Sat, 24 Mar 2012 17:50:50 +0800
EHLO mail.bj.com
250-mail.bj.com Hello mail.bj.com [127.0.0.1], pleased to meet you
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-8BITMIME
250-SIZE
250-DSN
250-AUTH LOGIN PLAIN
250-STARTTLS
250-DELIVERBY
250 HELP
mail from:[email protected]
530 5.7.0 Authentication required
在上面信息中出现250-AUTH LOGIN PLAIN表示此时以支持认证。
先对账号和密码做base64 位编码
[root@mail ~]# echo -n "[email protected]" |openssl base64
dXNlcjFAYmouY29t
[root@mail ~]# echo -n "123" |openssl base64
MTIz
再次进行测试:
[root@mail mail]# telnet mail.bj.com 25
Trying 127.0.0.1...
Connected to localhost.localdomain (127.0.0.1).
Escape character is '^]'.
220 mail.bj.com ESMTP Sendmail 8.13.8/8.13.8; Sat, 24 Mar 2012 17:50:50 +0800
EHLO mail.bj.com
250-mail.bj.com Hello mail.bj.com [127.0.0.1], pleased to meet you
250-ENHANCEDSTATUSCODES
250-PIPELINING
250-8BITMIME
250-SIZE
250-DSN
250-AUTH LOGIN PLAIN
250-STARTTLS
250-DELIVERBY
250 HELP
AUTH LOGIN dXNlcjFAYmouY29t
334 UGFzc3dvcmQ6
MTIz
235 2.0.0 OK Authenticated
mail from:[email protected]
250 2.1.0 [email protected]... Sender ok
rcpt to:[email protected]
250 2.1.5 [email protected]... Recipient ok
DATA
354 Enter mail, end with "." on a line by itself
user1-to-user1--2012/03/24.
.
250 2.0.0 q2OA2AdE003852 Message accepted for delivery
quit
221 2.0.0 mail.bj.com closing connection
Connection closed by foreign host.
[root@mail ~]# su - user1
[user1@mail ~]$ mail
Mail version 8.1 6/6/93. Type ? for help.
"/var/spool/mail/user1": 2 messages 1 new
1 [email protected] Fri Mar 23 17:40 13/542 "DON'T DELETE THIS MESSAGE -- FOLDER INTERNAL DATA"
>N 2 [email protected] Sat Mar 24 18:05 12/402
& 2
Message 2:
From [email protected] Sat Mar 24 18:05:28 2012
Date: Sat, 24 Mar 2012 18:02:10 +0800
From: [email protected]
user1-to-user1--2012/03/24.
& quit
Saved 1 message in mbox
Held 1 message in /var/spool/mail/user1
[user1@mail ~]$
日志分析:
Mar 24 18:05:28 mail sendmail[3852]: q2OA2AdE003852: [email protected], size=28, class=0, nrcpts=1, msgid=<[email protected]>, proto=ESMTP, daemon=MTA, relay=mail.bj.com [127.0.0.1]
Mar 24 18:05:28 mail sendmail[3857]: q2OA2AdE003852: [email protected], [email protected] (500/500), delay=00:00:27, xdelay=00:00:00, mailer=local, pri=30345, dsn=2.0.0, stat=Sent
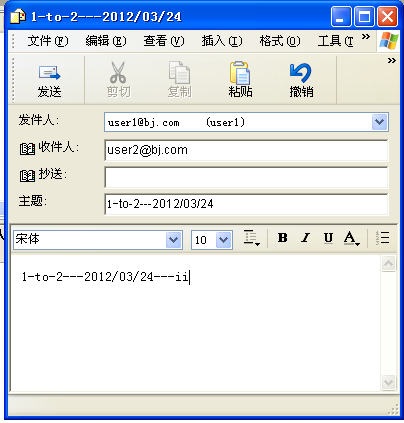
⑥ :使用outlook express测试认证。
此时已经可以用OE 通过验证身份的方式发送邮件了。
在启用sasl 功能之后,access 的设置就不起效,因为所有的认证都是通过sasl 来实现了。此时,smtp 就不再基于IP 地址来认证,只需提供账户密码即可。
日志文件如下所示:
[root@mail ~]# tail -f /var/log/maillog
Mar 24 18:22:58 mail sendmail[3927]: STARTTLS=server, relay=[10.106.6.200], version=TLSv1/SSLv3, verify=NO, cipher=RC4-MD5, bits=128/128
Mar 24 18:22:58 mail sendmail[3927]: AUTH=server, relay=[10.106.6.200], authid=user1, mech=LOGIN, bits=0
Mar 24 18:22:58 mail sendmail[3927]: q2OAMwNU003927: from=<[email protected]>, size=1244, class=0, nrcpts=1, msgid=<00e901cd09a7$f3aa8700$c8066a0a@hp3aea877158e2>, proto=ESMTP, daemon=MTA, relay=[10.106.6.200]
Mar 24 18:22:58 mail sendmail[3928]: q2OAMwNU003927: to=<[email protected]>, ctladdr=<[email protected]> (500/500), delay=00:00:00, xdelay=00:00:00, mailer=local, pri=31491, dsn=2.0.0, stat=Sent
Mar 24 18:23:26 mail dovecot: imap-login: Login: user=<user2>, method=PLAIN, rip=::ffff:10.106.6.200, lip=::ffff:10.106.6.254, TLS
Mar 24 18:23:26 mail dovecot: IMAP(user2): Disconnected in IDLE
Mar 24 18:23:29 mail dovecot: pop3-login: Login: user=<user1>, method=PLAIN, rip=::ffff:10.106.6.200, lip=::ffff:10.106.6.254, TLS
Mar 24 18:23:29 mail dovecot: POP3(user1): Disconnected: Logged out top=0/0, retr=0/0, del=0/0, size=0
Mar 24 18:23:29 mail dovecot: imap-login: Login: user=<user2>, method=PLAIN, rip=::ffff:10.106.6.200, lip=::ffff:10.106.6.254, TLS
Mar 24 18:23:29 mail dovecot: IMAP(user2): Connection closed
转载于:https://blog.51cto.com/jinjianping/996913